Authenticated Received Chain (ARC)
Hi All,
Did you come across “Authenticated Received Chain (ARC)”?
Authenticated Received Chain (ARC) is an email authentication system designed to allow an intermediate mail server like a mailing list or forwarding service to sign an email’s original authentication results. This allows a receiving service to validate an email when the email’s SPF and DKIM records are rendered invalid by an intermediate server’s processing.
ARC is defined in RFC 8617, published in July 2019, as “Experimental”
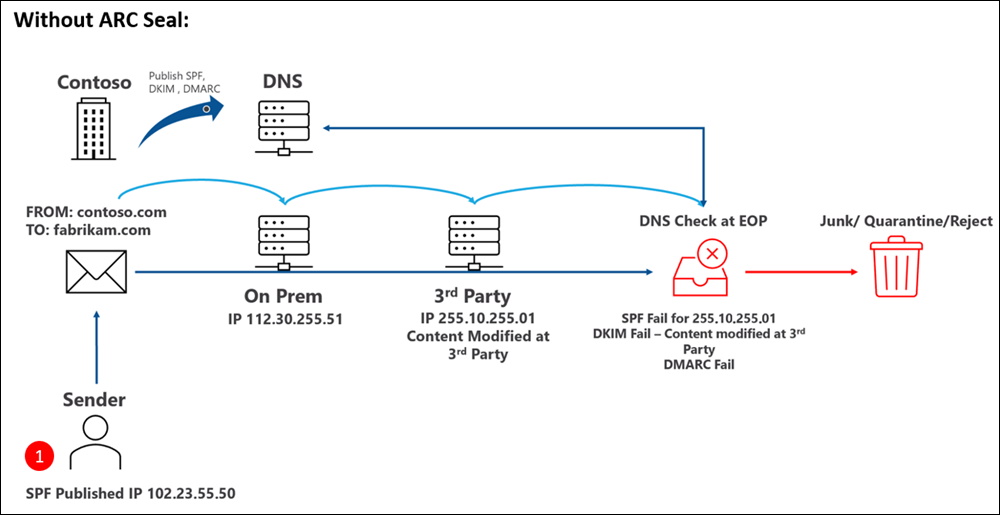
If a Mail is sent via a 3rd Party Server, then SPF, DKIM and DMARC might fail on the Recipient Mailserver.
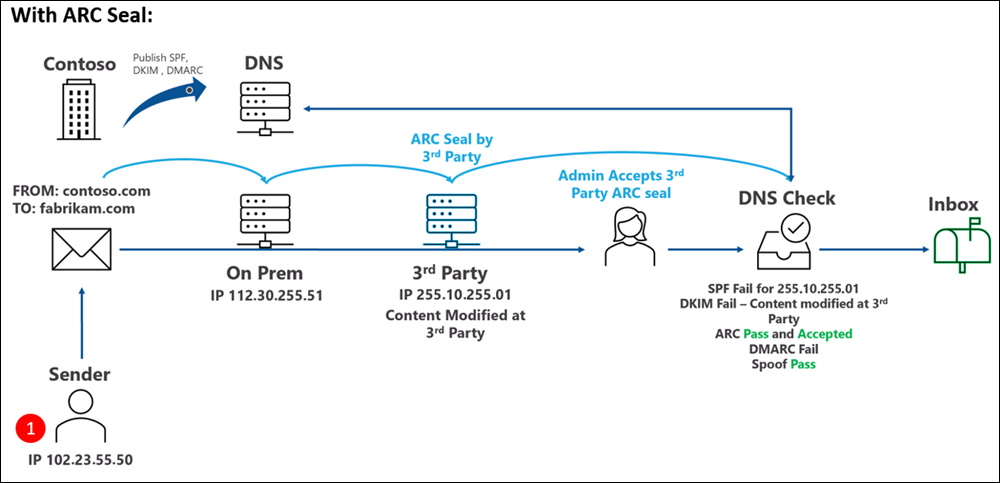
With ARC, the 3rd Party Server can add a ARC Seal with the the original Message SPF and DKIM Checks. On the Receiver Side you can now add trust that ARC Domain. But i suggest to do that only if they do it right and have good practices and procedures in place.
ARC defines three new mail headers:
- ARC-Authentication-Results (abbreviated AAR) - A combination of an instance number (i) and the results of the SPF, DKIM, and DMARC validation
- ARC-Seal (abbreviated AS) - A combination of an instance number (i), a DKIM-like signature of the previous ARC-Seal headers, and the validity of the prior ARC entries.
- ARC-Message-Signature (abbreviated AMS) - A combination of an instance number (i) and a DKIM-like signature of the entire message except for the ARC-Seal headers
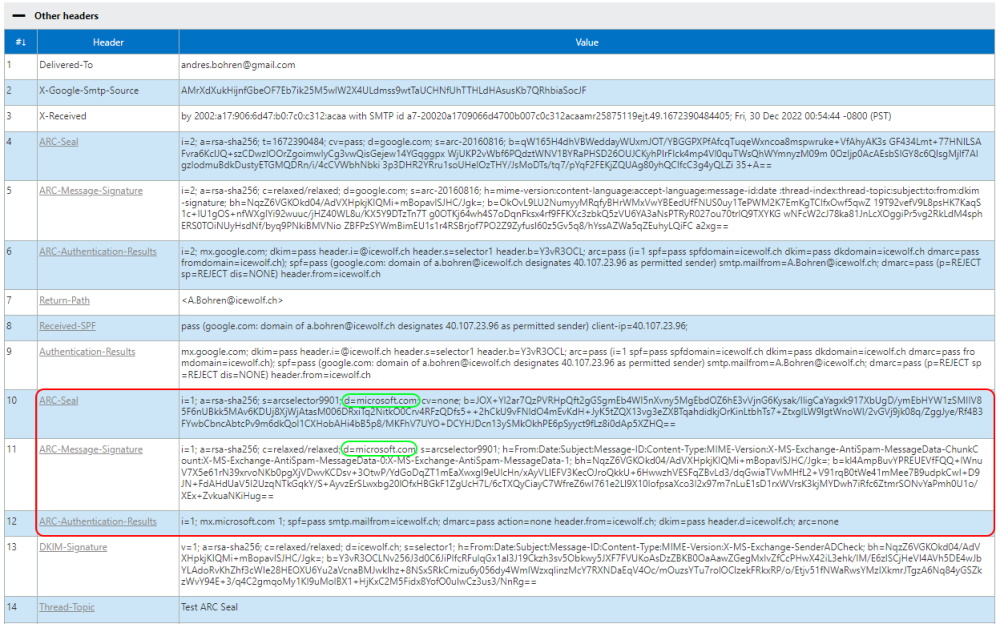
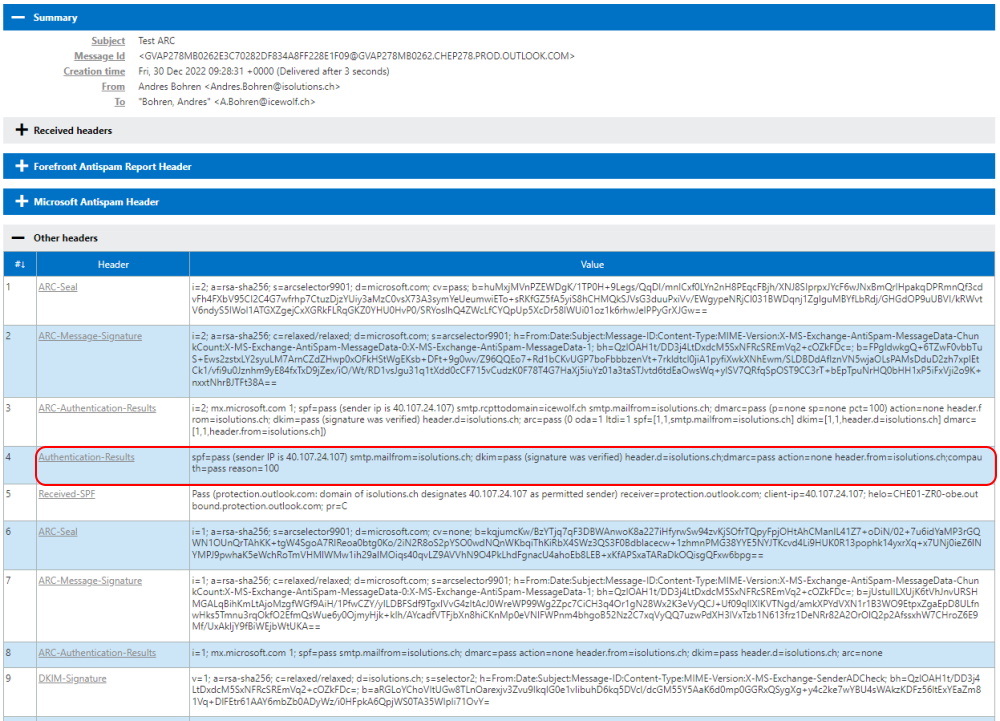
I’ve sent an Email to my Gmail Account. As you can see Outgoing Messages from Exchange Online already have an ARC Seal. Please note the Domain Tag “d=domain.tld”
Exchange Online Supports ARC since Summer 2022.
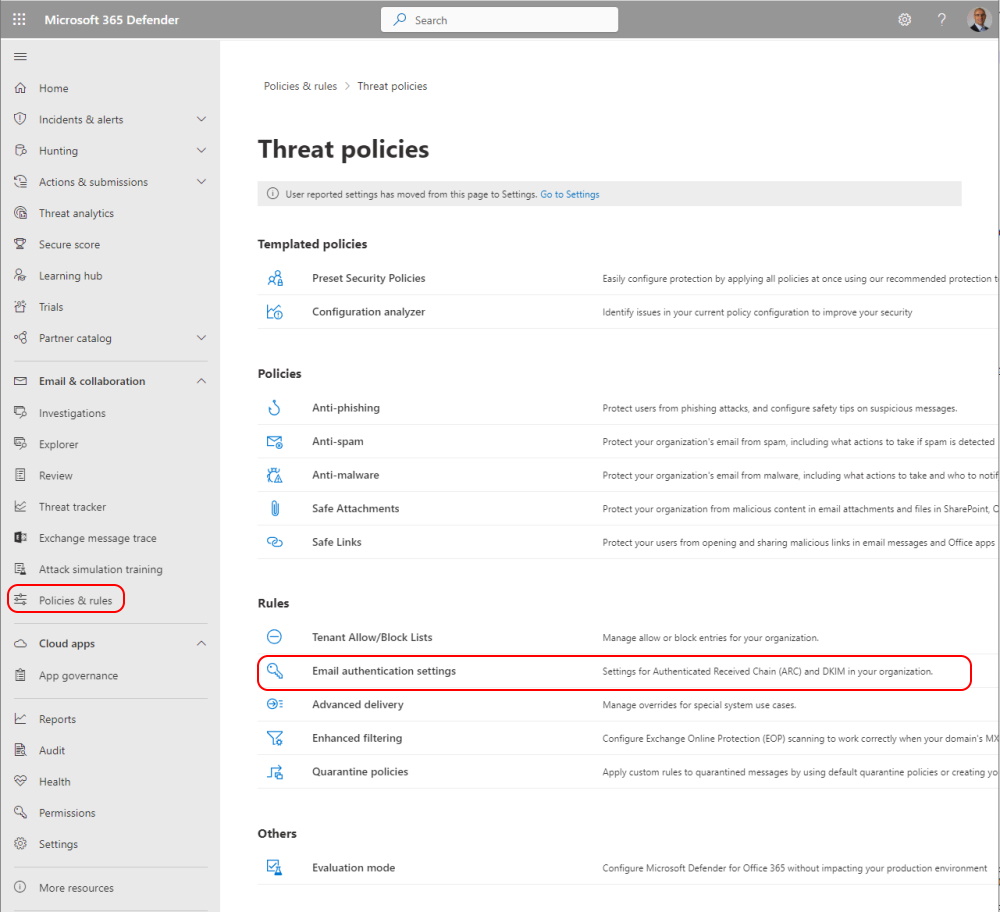
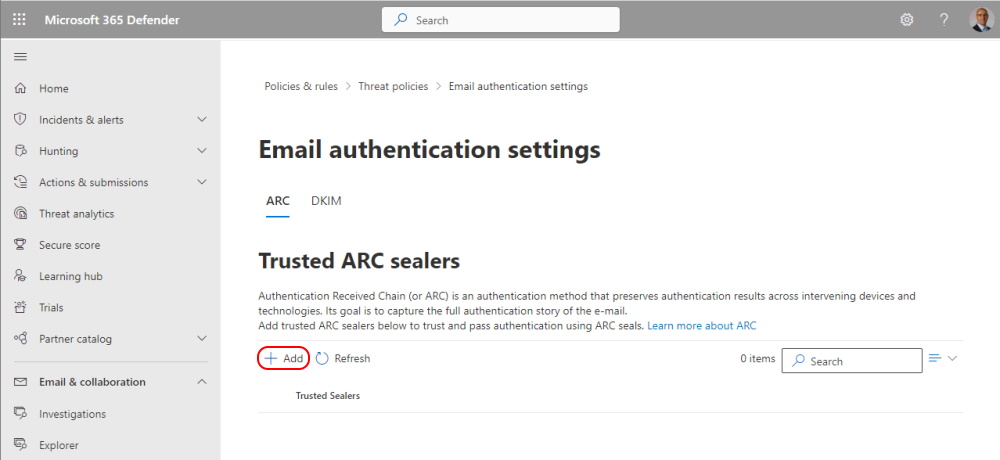
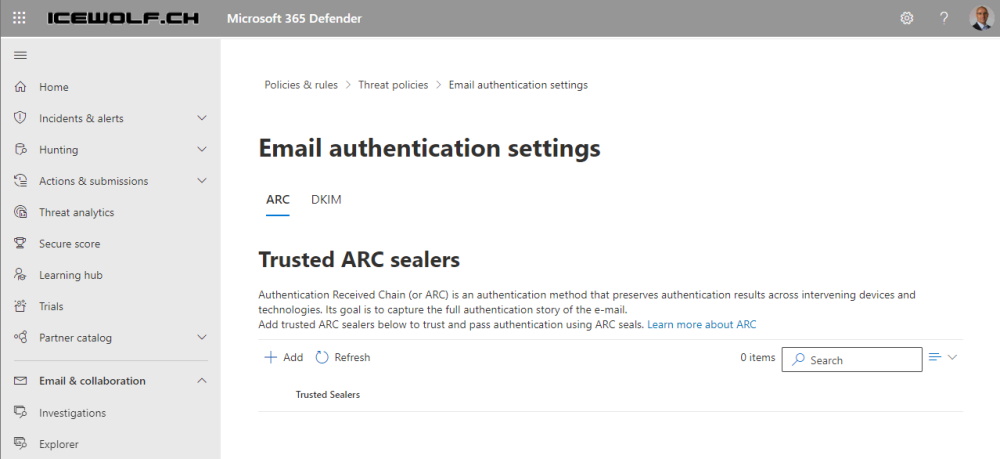
Make a list of trusted ARC Senders to trust legitimate indirect mailflows
You can add ARC Trusts in the Microsoft 365 Defender Portal under Email authentication settings
You can add a Trusted ARC Sealer
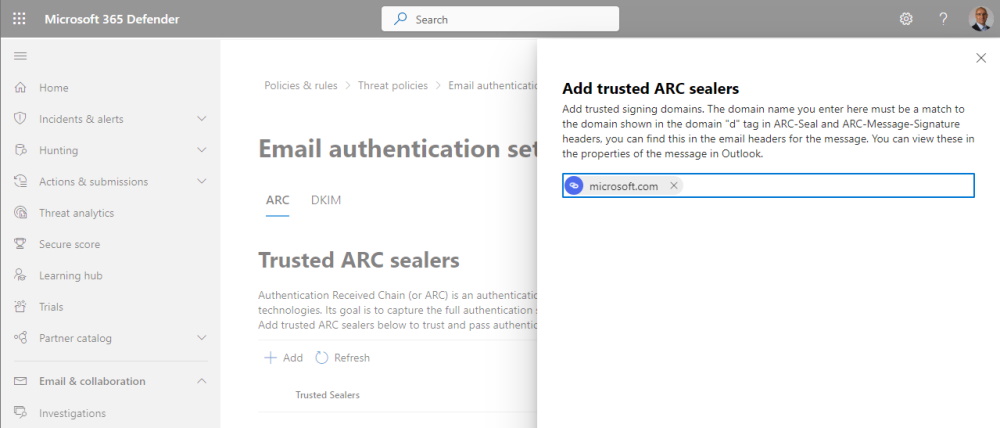
Now you add the Domain of the Sealer (remember the “d=domain.tld”)
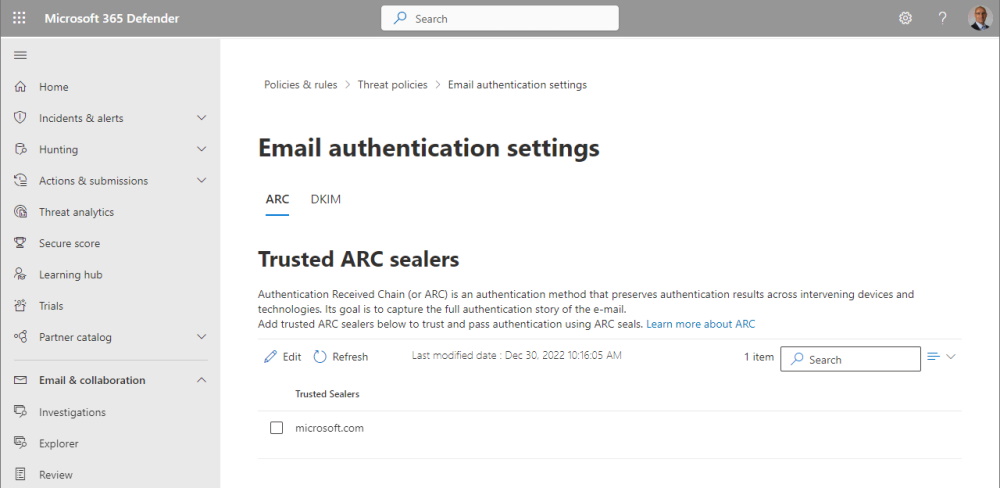
That’s how it looks then
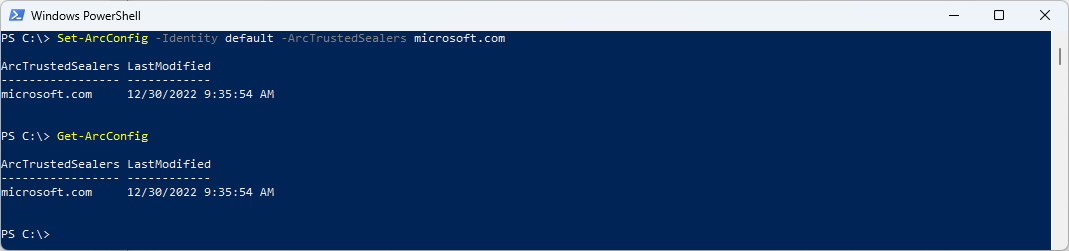
If you like to do that with the ExchangeOnlineManagement PowerShell Module. Here you go:
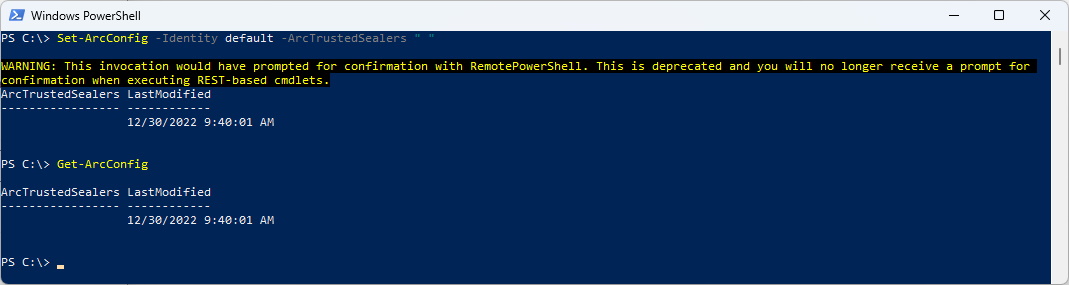
Set-ArcConfig -Identity default -ArcTrustedSealers microsoft.com
Get-ArcConfig
To delete the Entry is a little bit odd in my Opinion. I’ve tried to set it to $Null and pass an empty Array. But instead you have to set a Space to delete the List.
Set-ArcConfig -Identity default -ArcTrustedSealers " "
Get-ArcConfig
That will result in an Empty ARC Sealers list
Now i’ve tried to send a Mail from another Exchange Online Organization.
Microsoft states: To check whether the ARC result was used to override a DMARC failure, look for compauth result and a reason of code(130) in the header. I don’t see that here. Probably because SPF, DKIM and DMARC have already passed and there is no need of evaluating ARC to override DMARC.
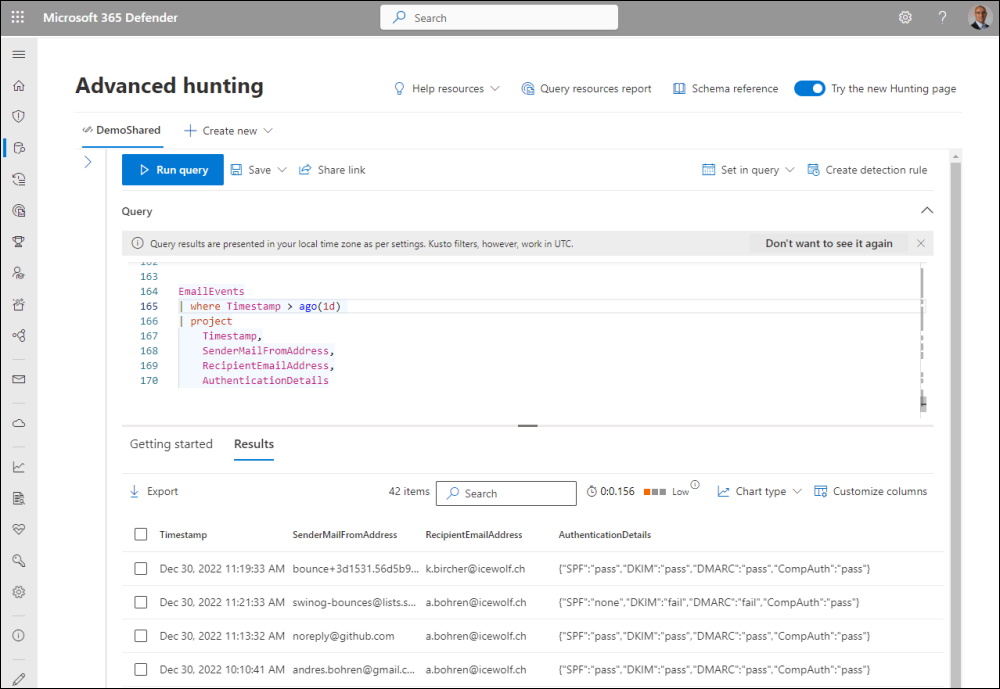
I’ve tried to see if i can see that in Advanced Hunting https://security.microsoft.com/v2/advanced-hunting
But you cant’s see the reason code there
//Authentication Details
EmailEvents
| where Timestamp > ago(1d)
| project
Timestamp,
SenderMailFromAddress,
RecipientEmailAddress,
AuthenticationDetails
Now you now how Authenticated Received Chain (ARC) works and can add Trusted ARC Sealers if you need to.
Regards
Andres Bohren