Exchange Online legacy TLS Endpoints for POP3 IMAP and SMTP
Hi All,
New opt-in endpoint for POP3/IMAP4 clients that need legacy TLS
- Exchange Online ended support for TLS1.0 and TLS1.1 in October 2020.
- This year, we plan to disable these older TLS versions for POP3/IMAP4 clients to secure our customers and meet compliance requirements.
- However, we know that there is still significant usage of POP3/IMAP4 clients that don�t support TLS 1.2, so we�ve created an opt-in endpoint for these clients so they can use TLS1.0 and TLS1.1.
- This way, an organization is secured with TLS1.2 unless they specifically decide to opt for a less secure posture.
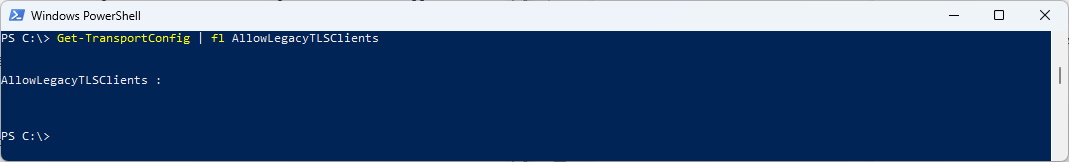
The Setting for legacy TLS Protocols (TLS1.0 and TLS 1.1) for POP3 / IMAP and SMTP is controlled by this setting. The Default is $Null and means disabled.
Get-TransportConfig | fl AllowLegacyTLSClients
- pop-legacy.office365.com
- imap-legacy.office365.com
Customers who use Microsoft 365 operated by 21 Vianet need to configure their clients to use
- pop-legacy.partner.outlook.cn
- imap-legacy.partner.outlook.cn
Opt in to the Exchange Online endpoint for legacy TLS clients using SMTP AUTH
- smtp-legacy.office365.com
Customers who use Microsoft 365 operated by 21 Vianet need to configure their clients to use the endpoint
- smtp-legacy.partner.outlook.cn
The most known SSL/TLS Attacks:
- 2011 BEAST (Browser Exploit Against SSL/TLS)
- 2012 CRIME (Compression Ratio Info-leak Made Easy)
- 2013 BREACH (Browser Reconnaissance and Exfiltration via Adaptive Compression of Hypertext)
- 2014 POODLE-Angriff (Padding Oracle On Downgraded Legacy Encryption)
- 2014 Heartbleed-Bug in OpenSSL.
- 2015 FREAK-Angriff (Factoring RSA Export Keys)
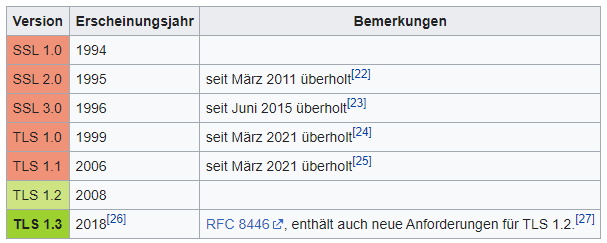
As you can see TLS 1.2 exists since 2008
Let’s have a look at the TLS Configuration in Exchange Server.
-
TLS 1.2 support was added with Cumulative Update (CU) 19 to Exchange Server 2013 and CU 8 to Exchange Server 2016. Exchange Server 2019 supports TLS 1.2 out of the box.
-
It is possible to disable TLS 1.0 and 1.1 on Exchange Server 2013 with CU 20 and later or on Exchange Server 2016 with CU 9 and later. It is also required to have the latest version of .NET Framework and associated patches supported by your CU in place.
-
Exchange Server 2016 CU9 March 20, 2018
-
Exchange Server 2013 CU20 March 20, 2018
Conclusion: It’s almost 5 Years since you can use Exchange on TLS 1.2 only.
My recommendation would be to seek for a Solution that Supports TLS 1.2 in before you enable “AllowLegacyTLSClients”. You will decrease your Security Posture. Now is the Time to do it right!
Regards
Andres Bohren