Microsoft Outlook Elevation of Privilege Vulnerability (CVE-2023-23397)
Hi All,
There is a Outlook Escalation of Privilege Vulnerability in Outlook. Tony Redmond has explained that very well
- Outlook Elevation of Privilege Vulnerability Leaks Credentials via NTLM
- Microsoft Outlook Elevation of Privilege Vulnerability
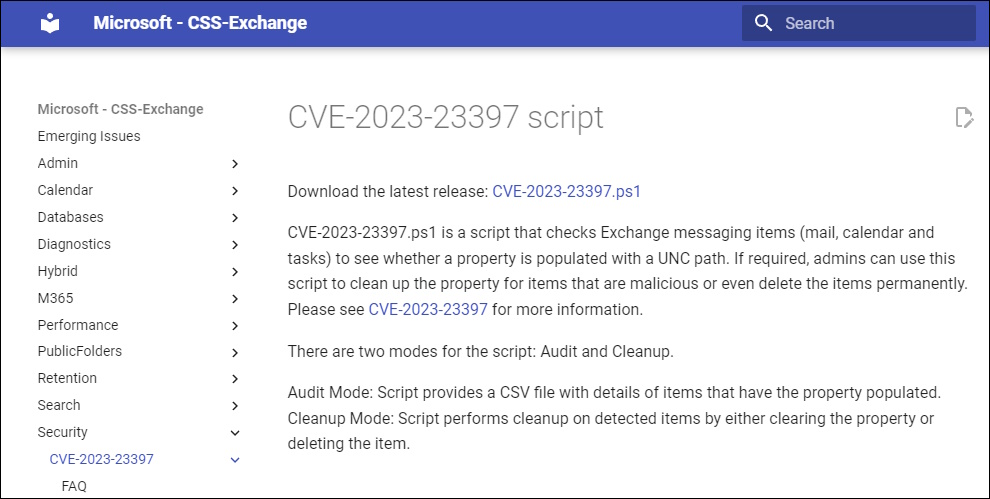
Exchange CSS has released a Script to test and mitigate
Exchange On Prem
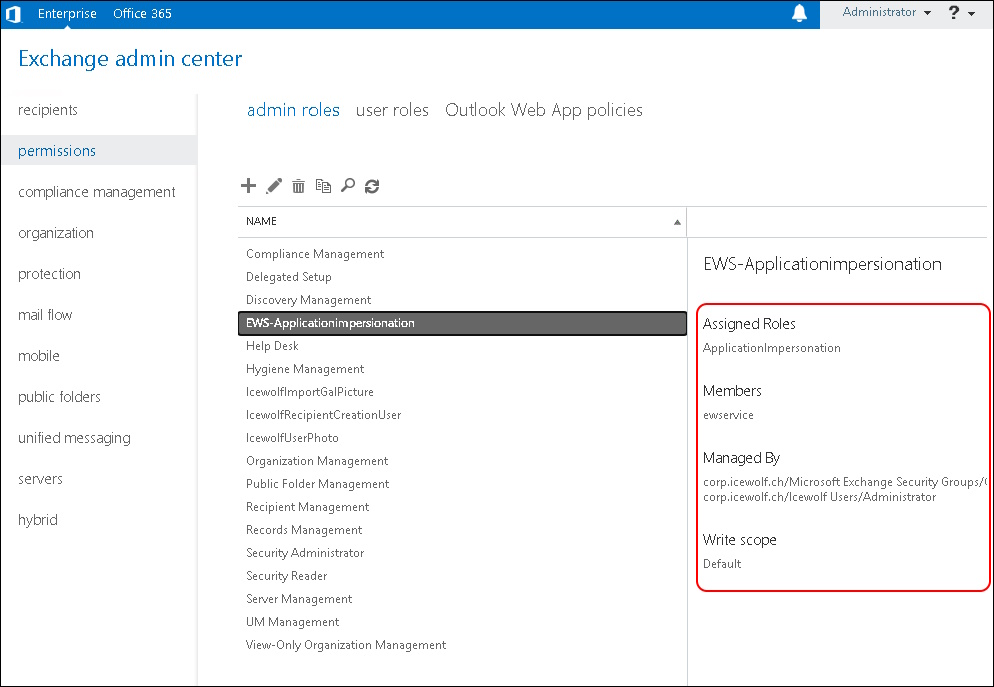
You need to have an RBAC Admin Role that allows Application Impersonation and assign an Account.
If you don’t have that Role you can create it
New-RoleGroup -Name "CVE-2023-23397-Script" -Roles "ApplicationImpersonation" -Description "Permission to run the CVE-2023-23397 script
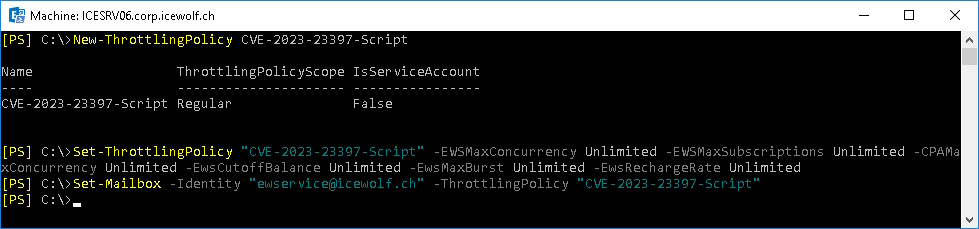
You can also create a Throttling Policy
New-ThrottlingPolicy CVE-2023-23397-Script
Set-ThrottlingPolicy "CVE-2023-23397-Script" -EWSMaxConcurrency Unlimited -EWSMaxSubscriptions Unlimited -CPAMaxConcurrency Unlimited -EwsCutoffBalance Unlimited -EwsMaxBurst Unlimited -EwsRechargeRate Unlimited
Set-Mailbox -Identity "ewservice@icewolf.ch" -ThrottlingPolicy "CVE-2023-23397-Script"
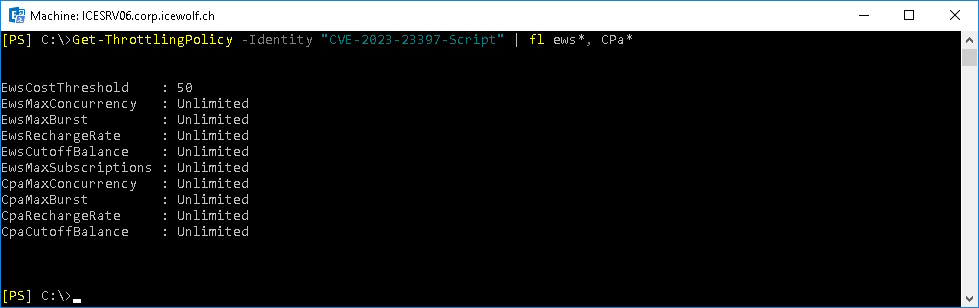
Let’s check that Throttling Policy
Get-ThrottlingPolicy -Identity CVE-2023-23397-Script | fl ews*, cpa*
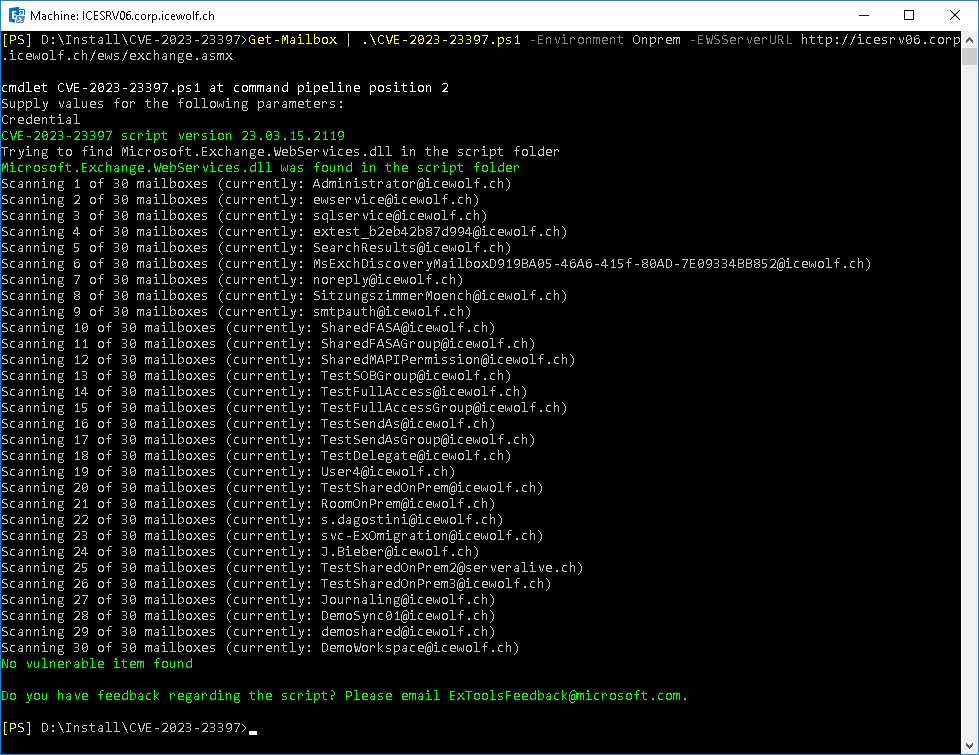
Download the Script and run it in a Exchange Management Shell
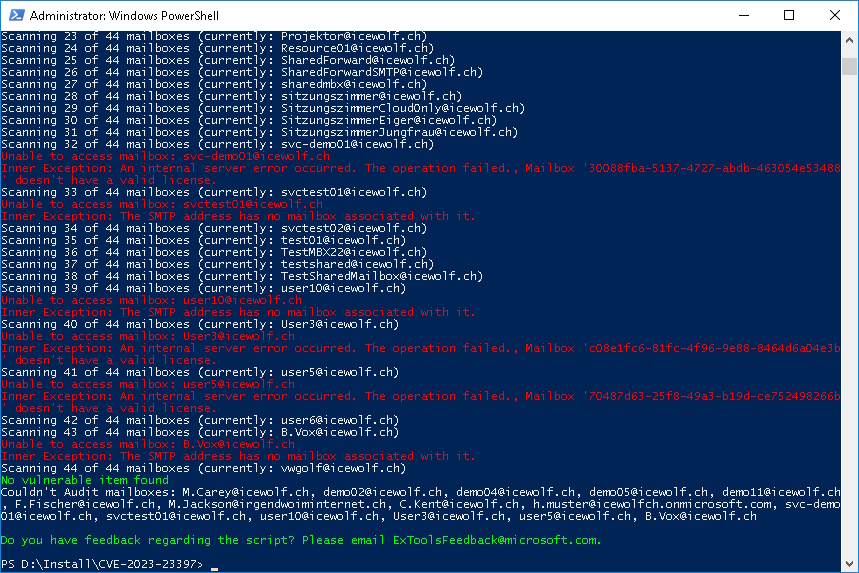
Get-Mailbox | .\CVE-2023-23397.ps1 -Environment Onprem -EWSServerURL http://ExchangeServerName/ews/exchange.asmx
You will need to provide the Credentials of the Account you are using to connect to EWS
No Mailbox with a vulnerability found
Exchange Online
You will need to have the AzureAD PowerShell Module installed
Install-Module AzureAD
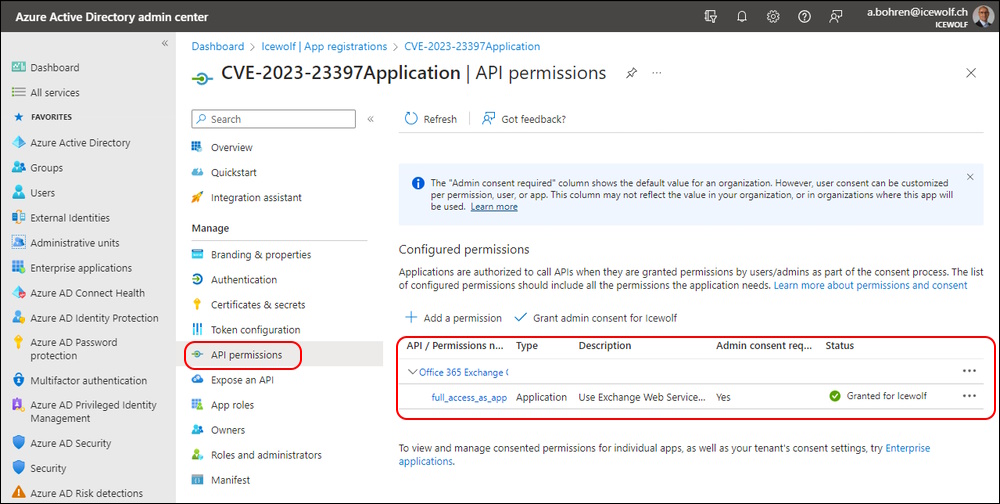
Now you need to create the AzureAD Application and you need to have the Global Administrator or an Application Administrator Role.
.\CVE-2023-23397.ps1 -CreateAzureApplication
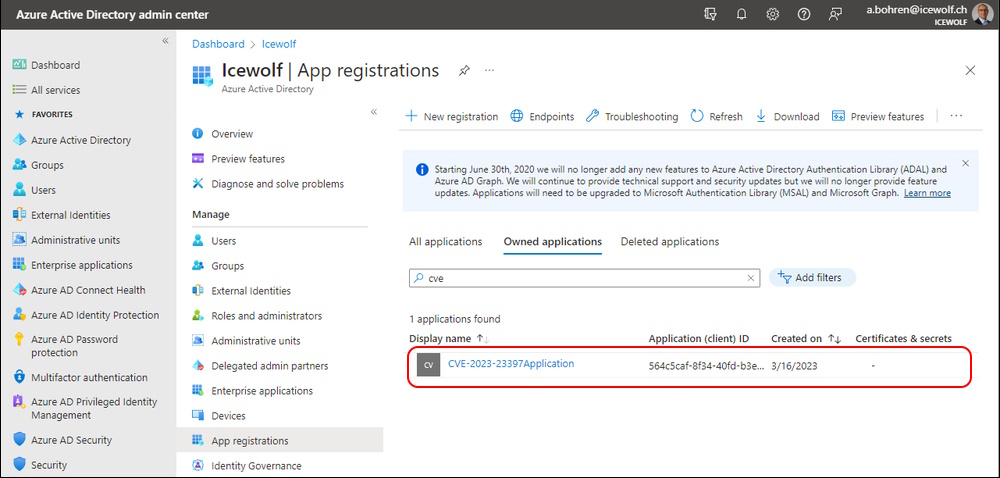
This will Create an AzureAD Application
And set the Permission “full_access_as_app” which is like Impersonation.
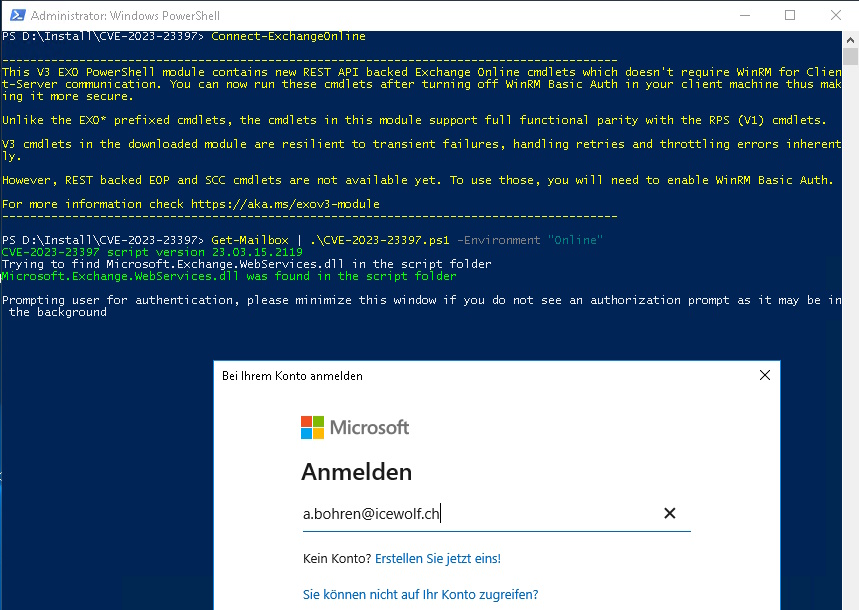
Now you need to connect to Exchange Online
Connect-ExchangeOnline
Now you can scan your environement
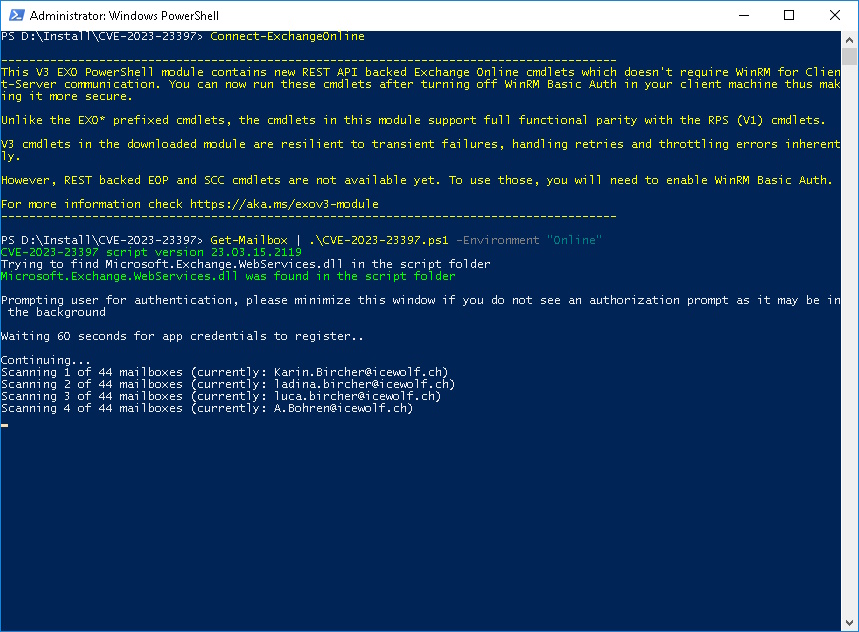
Get-Mailbox | .\CVE-2023-23397.ps1 -Environment "Online"
You need to Authenticate to register a new Client Secret. That’s why the Script has to wait for 60 Seconds
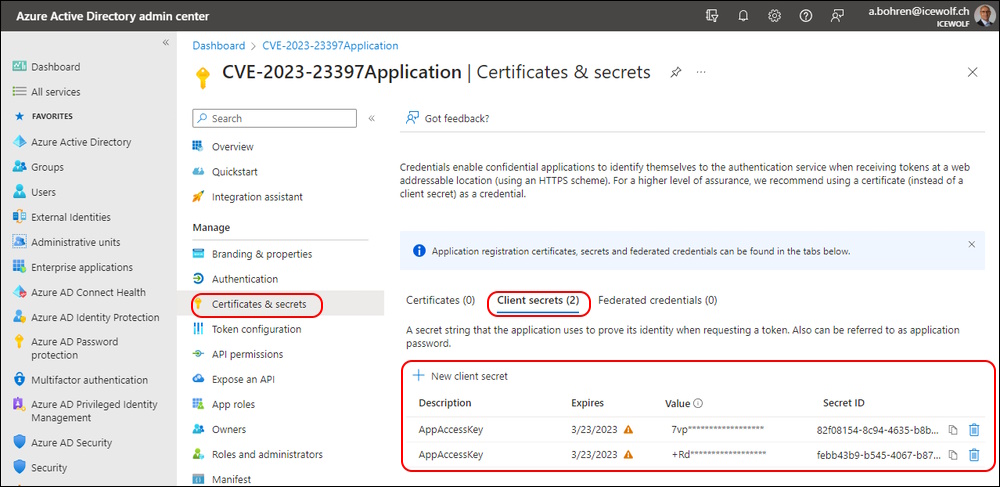
Every time you run the Script it will register a new Client Secret
I have a lot of Test Mailboxes with no Licenses assigned.
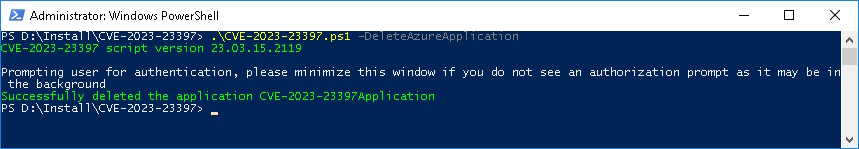
If no vulnerable Items are found the Azure AD Application can be deletet
.\CVE-2023-23397.ps1 -DeleteAzureApplication
Regards
Andres Bohren