Windows Hello for Business - Hybrid Cloud Kerberos trust
Hi All,
In this Blog Article i show you how you can enable Hybrid Cloud Kerberos Trust. So you can use Windows Hello for Business (WHfB) to authenticate with Kerberos to your OnPremise Active Directory Resources.
Overview
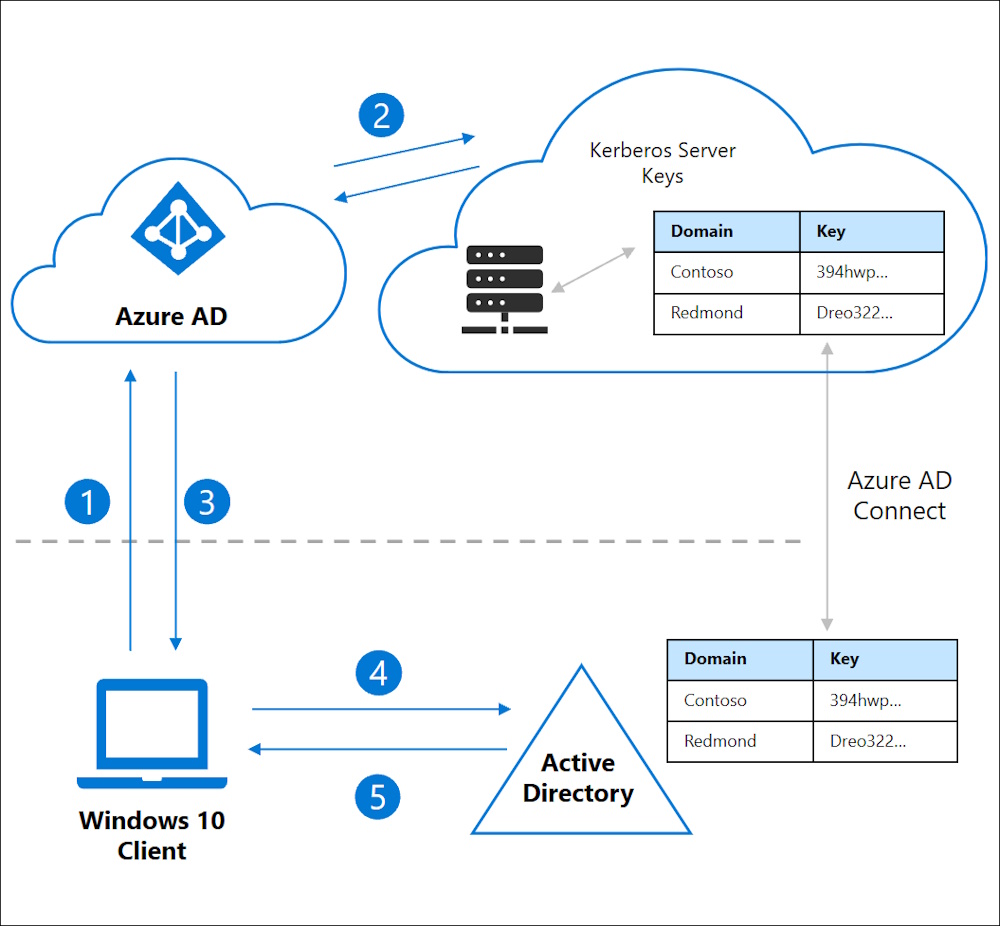
An Architectual Overview can be found Here Enable passwordless security key sign-in to on-premises resources by using Azure AD
Enable Cloud Kerberos Trust
How SSO to on-premises resources works on Azure AD joined devices
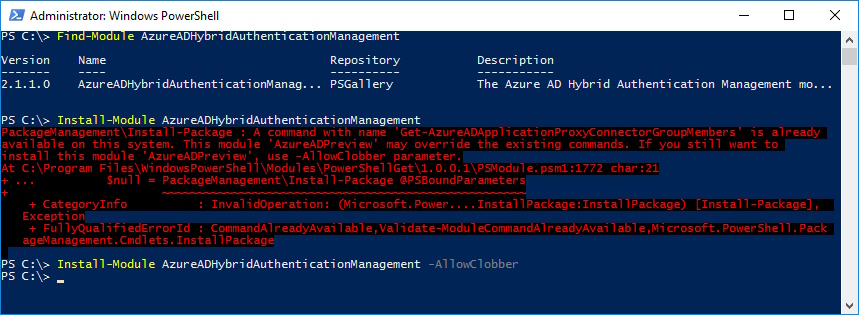
Find-Module AzureADHybridAuthenticationManagement
Install-Module AzureADHybridAuthenticationManagement
Install-Module AzureADHybridAuthenticationManagement -AllowClobber
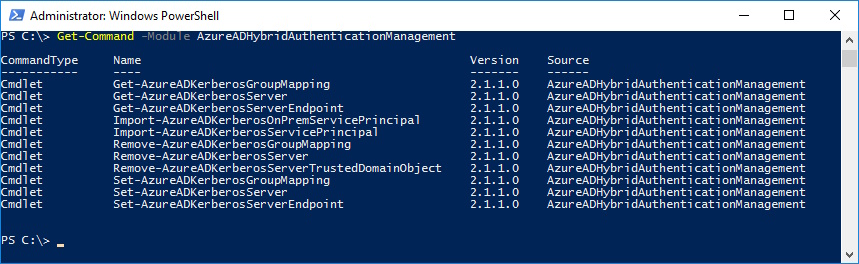
Let’s see what commandlets are available
Get-Command -Module AzureADHybridAuthenticationManagement
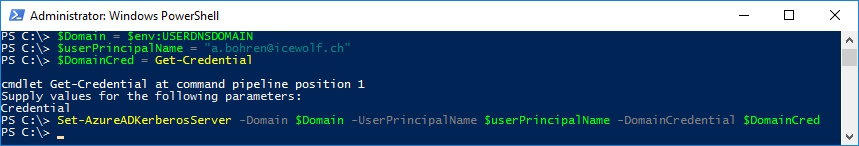
Now we need to create the Objects in Active Directory
# Specify the on-premises Active Directory domain. A new Azure AD
# Kerberos Server object will be created in this Active Directory domain.
$domain = $env:USERDNSDOMAIN
# Enter a UPN of an Azure Active Directory global administrator
$userPrincipalName = "administrator@contoso.onmicrosoft.com"
# Enter a domain administrator username and password.
$domainCred = Get-Credential
# Create the new Azure AD Kerberos Server object in Active Directory
# and then publish it to Azure Active Directory.
# Open an interactive sign-in prompt with given username to access the Azure AD.
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential $domainCred
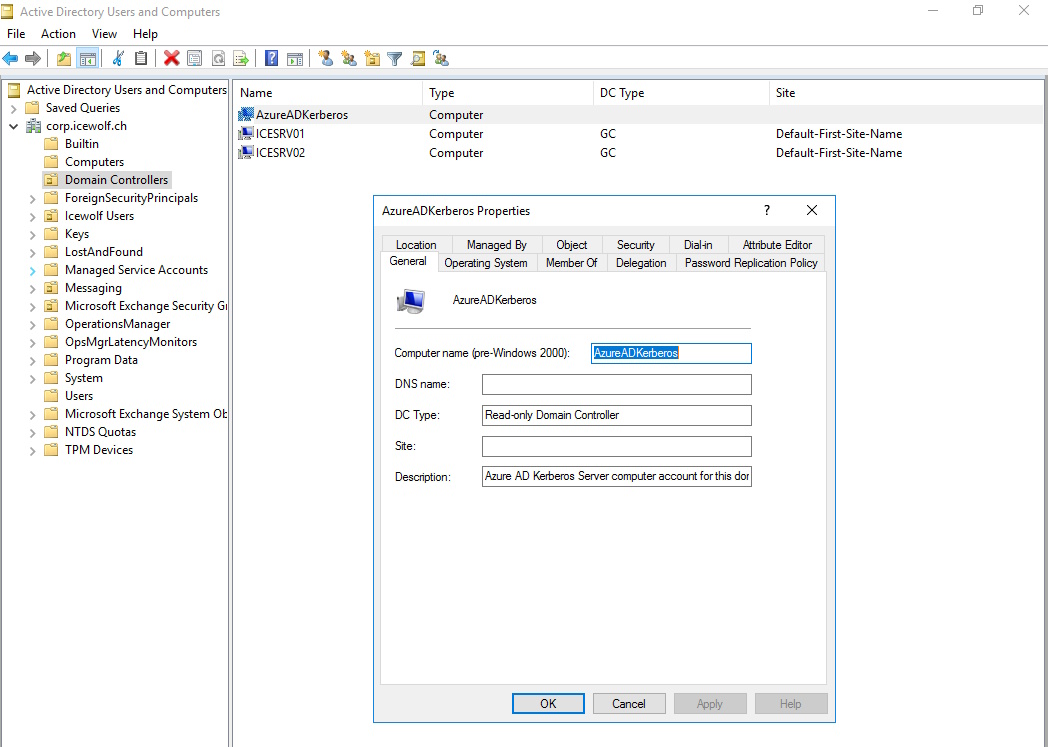
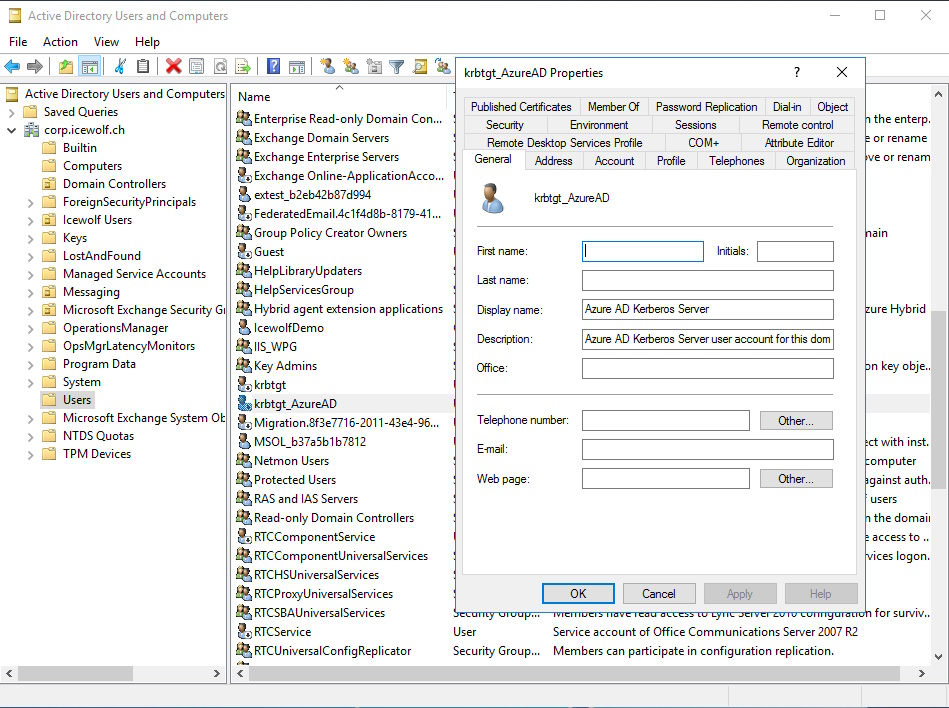
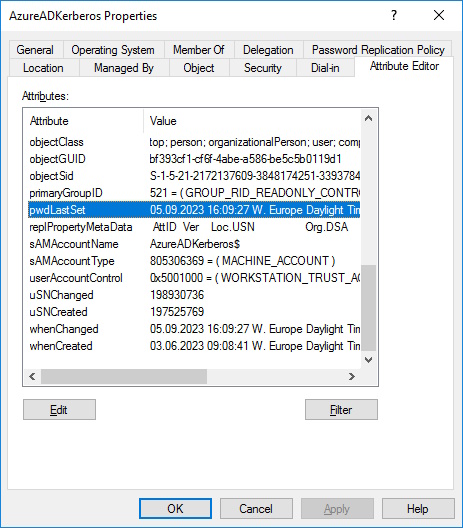
The Script will create an “AzureADKerberos” Computer Object in the “Domain Controllers” Organizational Unit of Active Directory.
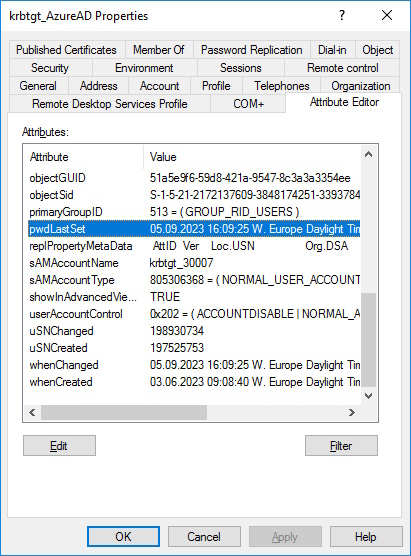
Ans also an Account “krbtgt_AzureAD” in the “Users” Organizational Unit
Windows Hello for Business
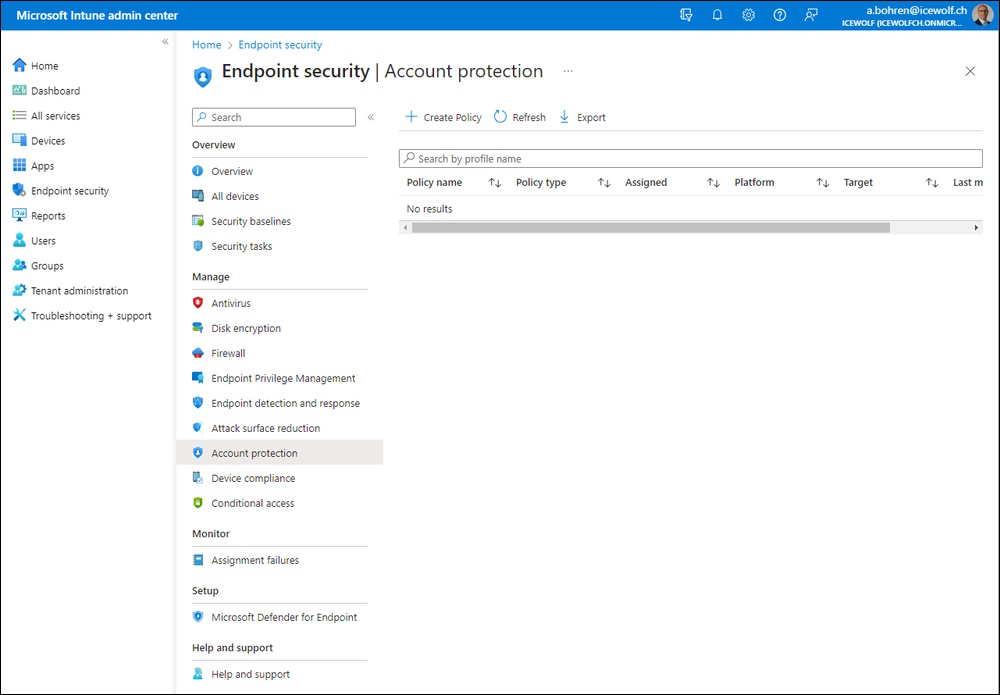
The Configuration in Intune for Windows Hello for Business (WHfB) is documented here Configure and provision Windows Hello for Business - cloud Kerberos trust
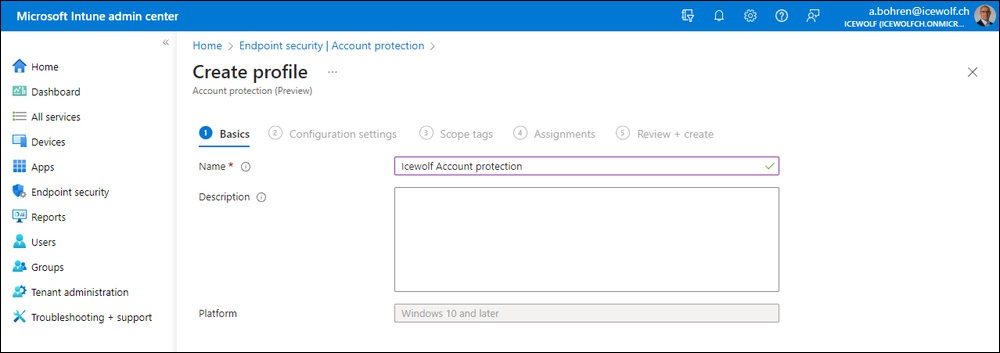
Intune Admin Center > Endpoint Security > Account Protection > Create Policy
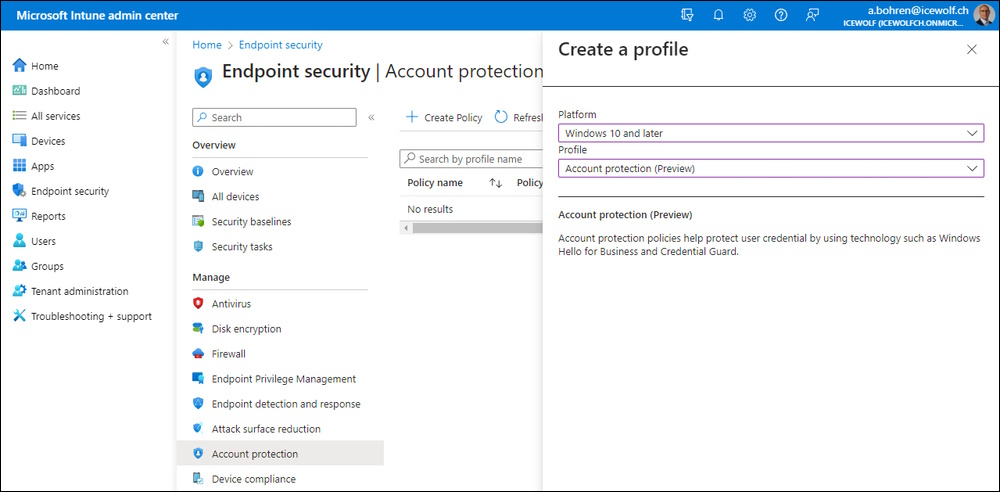
Add a new Profile
- Windows 10 and later
- Account Protection (Preview)
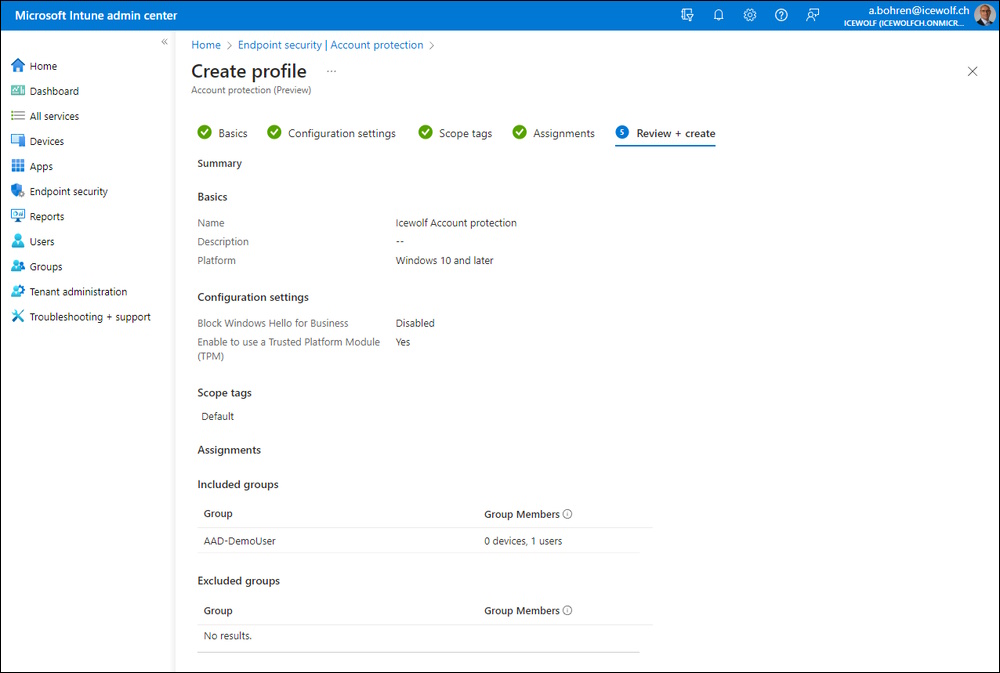
Give it a Name and Description
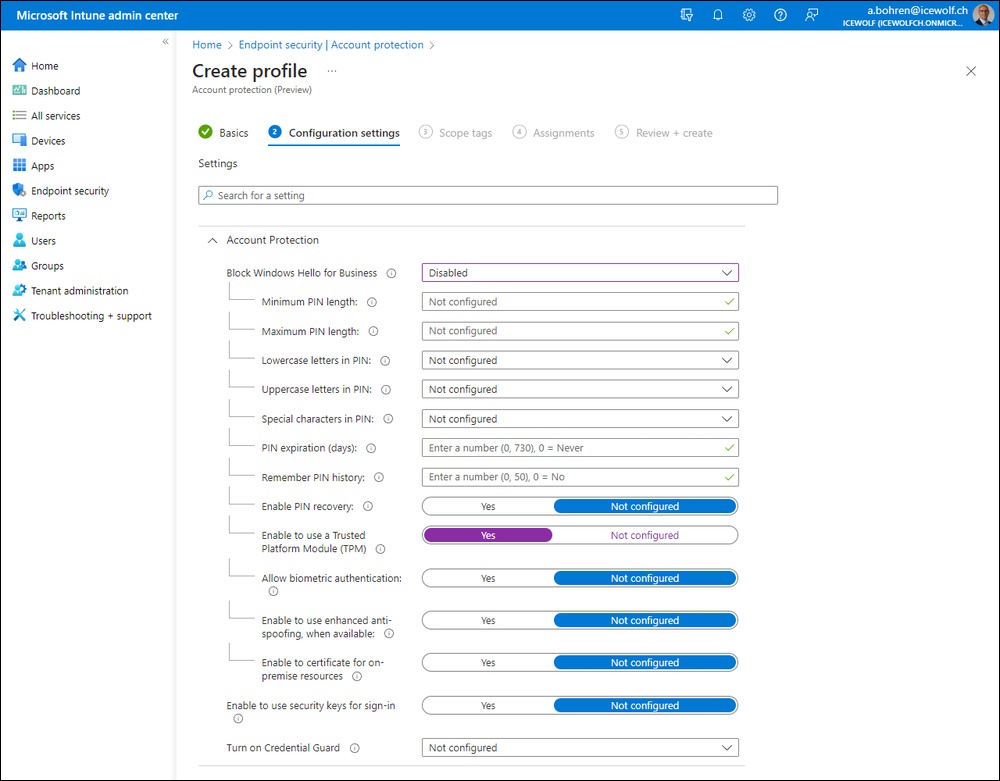
Enable this setting
- Enable to use a Trusted Platform Module (TPM)
Use Scope tags if you need
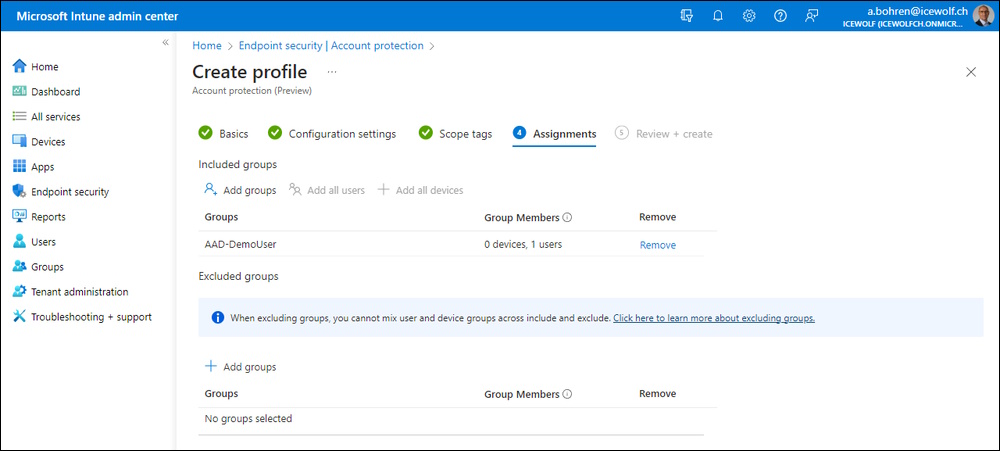
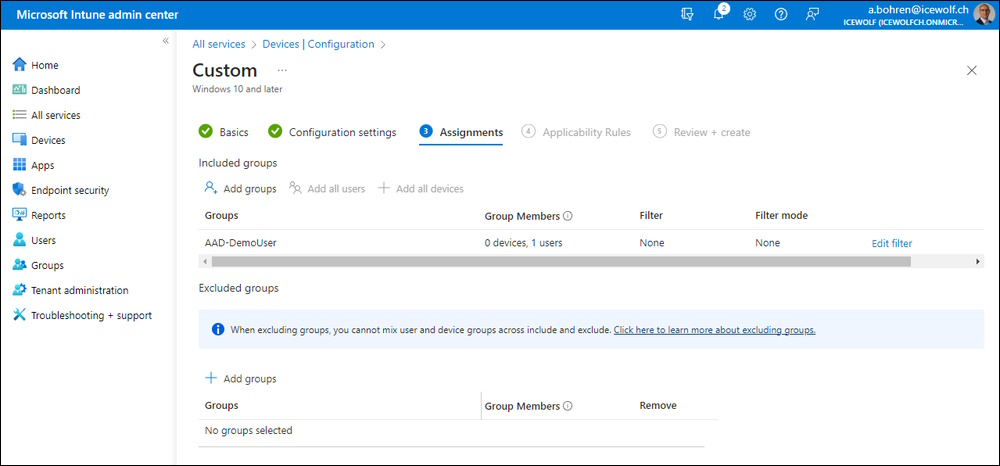
Assign it to the User Group
Review Screen
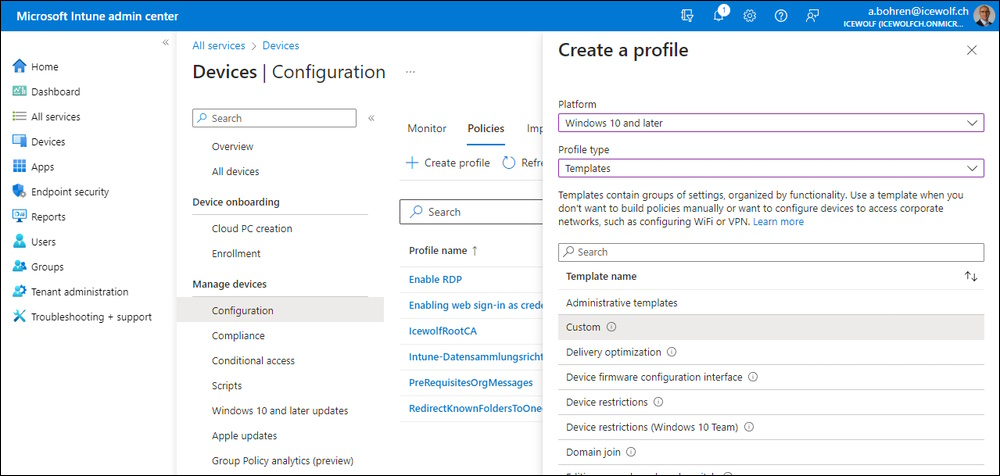
Intune Admin Center > Devices > Windows > Configuration Profiles > Create Profile
For Profile Type, select Templates and select the Custom Template.
- Windows 10 and later
- Templates > Custom
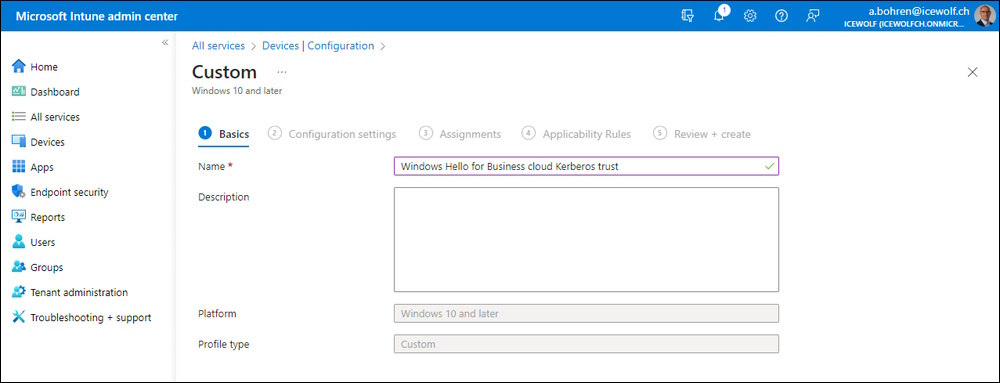
Give it a Name
Fill out these Fields:
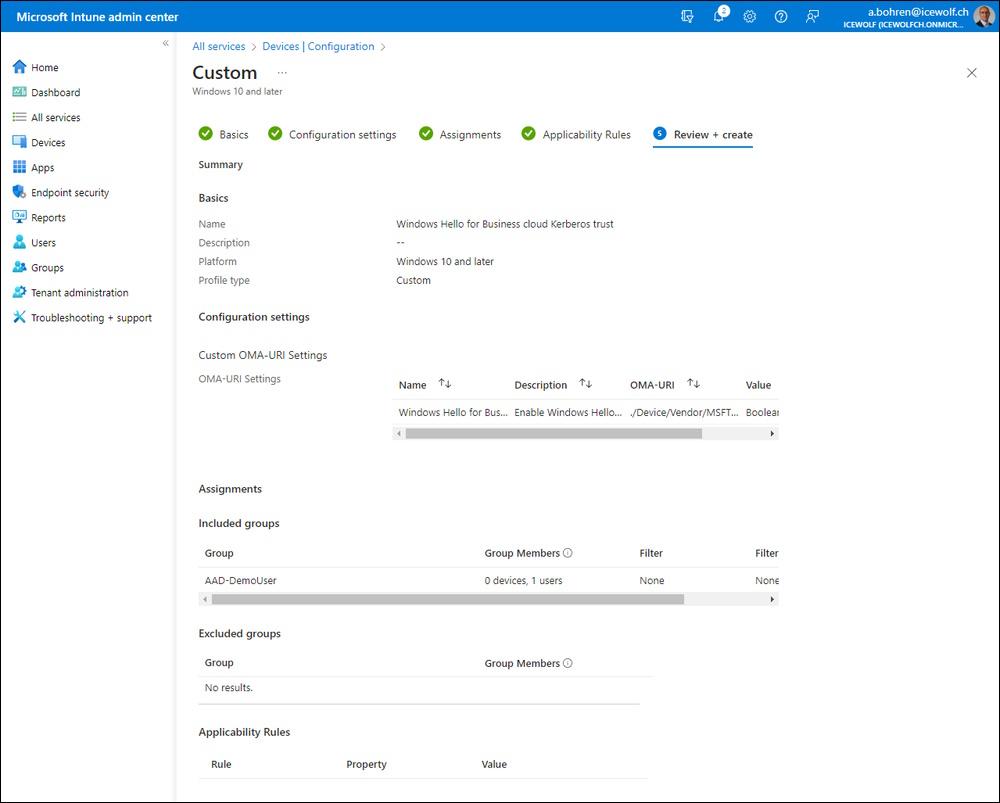
- Name = “Windows Hello for Business cloud Kerberos trust”.
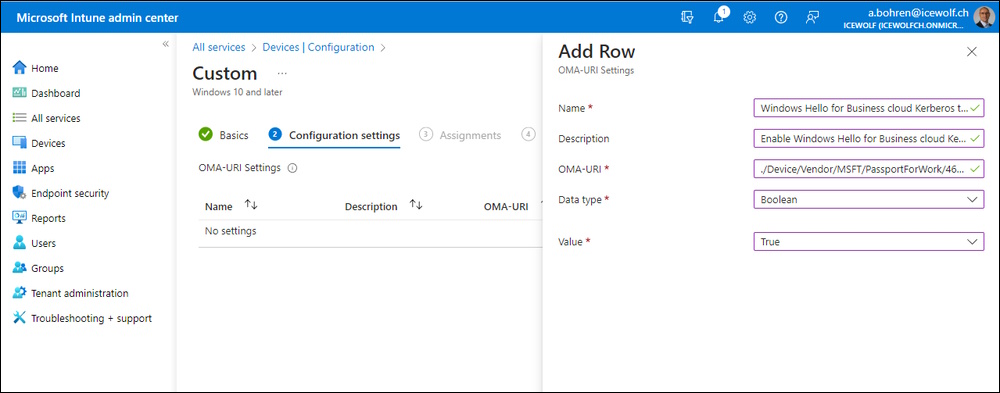
- Description (optional): Enable Windows Hello for Business cloud Kerberos trust for sign-in and on-premises SSO
- OMA-URI: ./Device/Vendor/MSFT/PassportForWork/TenantID/Policies/UseCloudTrustForOnPremAuth
- Data type: Boolean
- Value: True
Assign it to a User Group
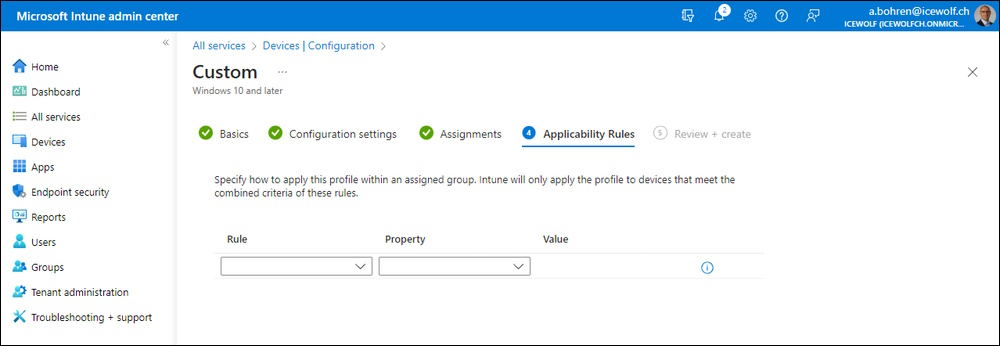
Use Applicability Rules if you want to
Review Screen
Testing
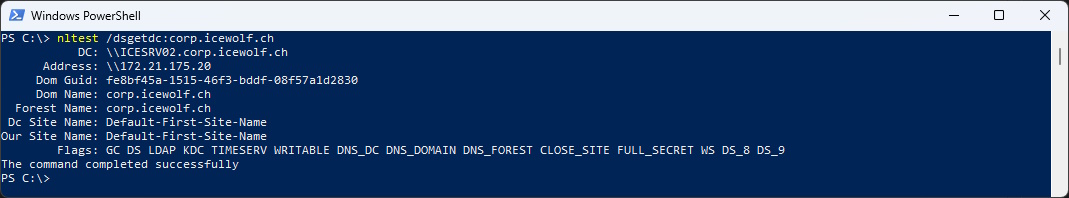
Queriy the Domain Name System (DNS) server for a list of domain controllers and their corresponding IP addresses
nltest /dsgetdc:corp.icewolf.ch
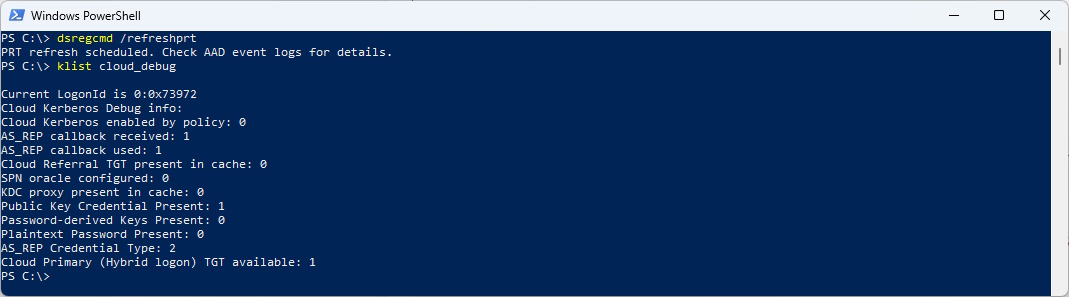
Refresh the Primary Primary Refresh Token (PRT) and check the Kerberos Tokens.
The “Cloud Primary (Hybrid logon) TGT available” count must be 1 or greater.
dsregcmd /refreshprt
klist cloud_debug
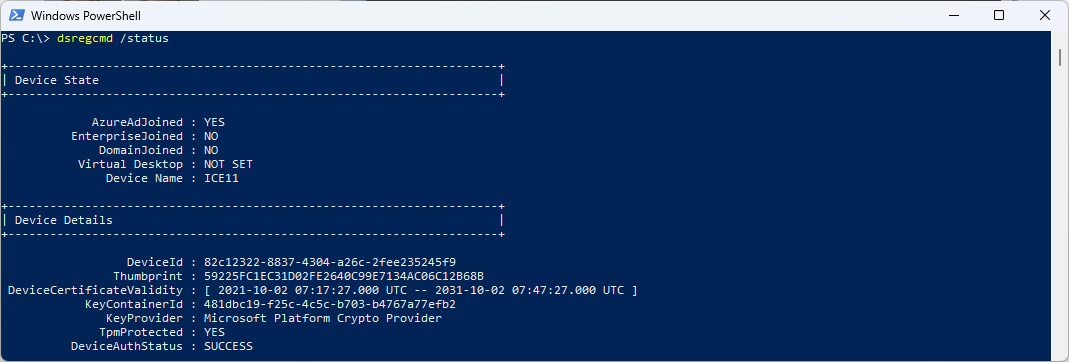
As you can see, my computer is Azure AD Joined. Not Domain or Hybrid Joined.
dsregcmd /status
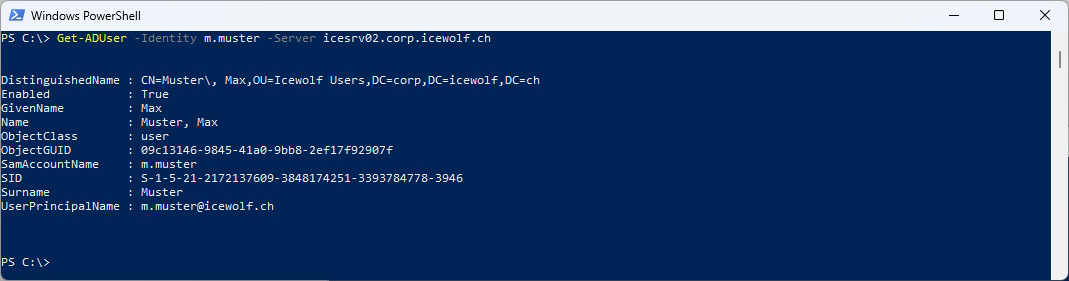
I am able to query Active Directory without Credentials but have to specify a Domain Controller
Get-ADUser -Identity m.muster -Server icesrv02.corp.icewolf.ch
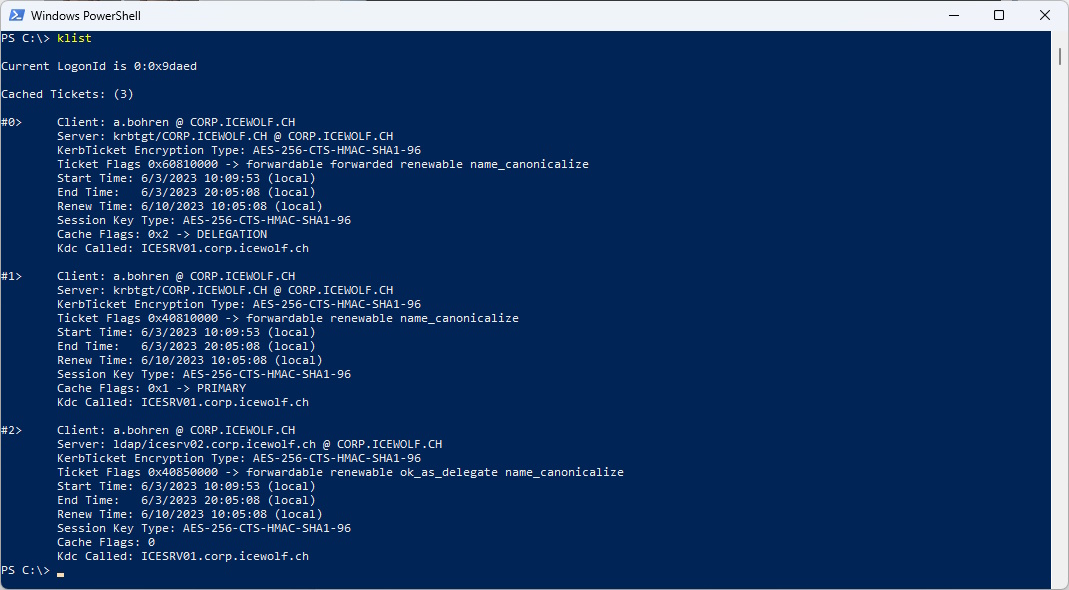
Let’s check the Kerberos Tickets
klist
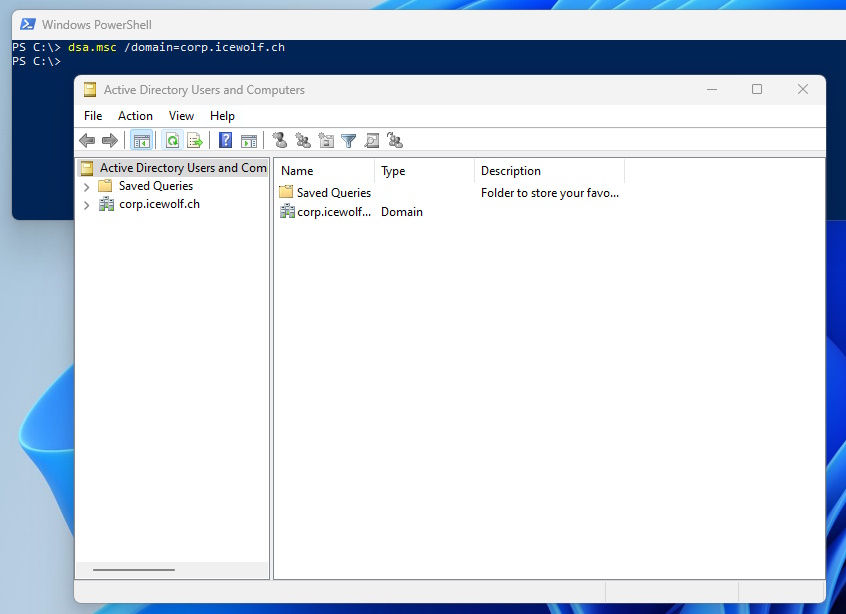
It’s even possible to use the Active Directory users and Computers when you specify the Domain
dsa.msc /domain=corp.icewolf.ch
Rotate the Azure AD Kerberos Server key
The Azure AD Kerberos Server encryption krbtgt keys should be rotated on a regular basis. We recommend that you follow the same schedule you use to rotate all other Active Directory DC krbtgt keys.
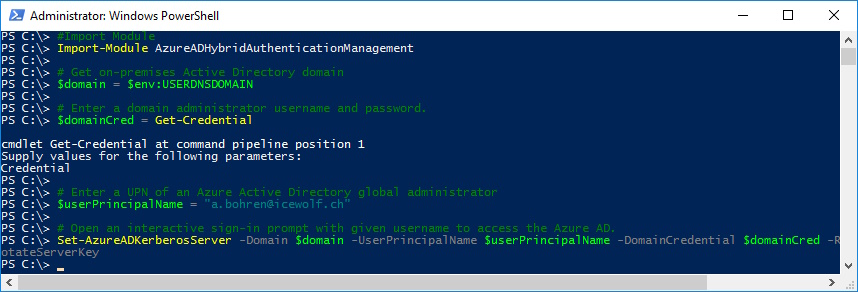
This is how you do it Interactively
#Import Module
Import-Module AzureADHybridAuthenticationManagement
# Get on-premises Active Directory domain
$domain = $env:USERDNSDOMAIN
# Enter a domain administrator username and password.
$domainCred = Get-Credential
# Enter a UPN of an Azure Active Directory global administrator
$userPrincipalName = "a.bohren@icewolf.ch"
# Open an interactive sign-in prompt with given username to access the Azure AD.
Set-AzureADKerberosServer -Domain $domain -UserPrincipalName $userPrincipalName -DomainCredential $domainCred -RotateServerKey
As you can see the “pwdLastSet” on the “krbtgt_AzureAD” and “AzureADKerberos” Account are updated.
Additional Information:
- https://msendpointmgr.com/2023/03/04/cloud-kerberos-trust-part-1/
- https://msendpointmgr.com/2023/03/04/cloud-kerberos-trust-part-2/
- https://cloudbrothers.info/en/windows-business-cloud-trust-kdc-proxy/
Regards
Andres Bohren