Mail Transfer Agent Strict Transport Security (MTA-STS)

Hi All,
What is MTA-STS
Mail Transfer Agent Strict Transport Security (MTA-STS) makes sure that Emails are Transfered over a secured TLS Connection but has lower requirements than DNS based Authentification of Named Entities (DANE).
“Mail Transfer Agent Strict Transport Security (MTA-STS)” has been defined in 2018 in the following RFC
MTA-STS benefits:
- Emails are transfered over a secure TLS connection
- Must use TLS-Version 1.2 or higher
- For the TLS Certificates they need to:
- Certificate Subject needs to match the MX-Entry
- They need to be signed and issued by a public trusthworthy CA
- They need to be valid (valid from / valid until)
MTA-STS protects against:
- Downgrade-Attacks to lower TLS Versions
- Man-In-The-Middle (MITM) Attacks
- Solves multiple SMTP-Security Issues, including expired TLS certificates and lack of support for secure protocols.
MTA-STS consists of:
- MTA STS DNS TXT Record (_mta-sts.domain.tld)
- MTA-STS Policy (https://mta-sts.domain.tld/.well-known/mta-sts.txt)
- SMTP TLS Reporting DNS TXT Record (_smtp._tls.domain.tld)
Like DANE the Sender must support MTA-STS and query the MTA-STS TXT Record as well as get the MTA-STS Policy. If the Sender does not support MTA-STS it is still allowed to send Mails without TLS1.2 - as long as the Receiving Mailserver supports that.
MTS-STS DNS TXT Record
The MTA-STS DNS TXT Record basically tells a Sending Server that this Domain does support MTA-STS
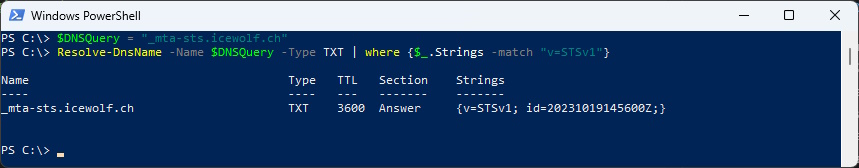
The DNS Query is for a TXT Record in “_mta-sts.domain.tld”
_mta-sts.domain.tld IN TXT “v=STSv1; id=20231019145600Z;”
Example Record
v=STSv1; id=20231019145600Z;
$DNSQuery = "_mta-sts.icewolf.ch"
Resolve-DnsName -Name $DNSQuery -Type TXT | where {$_.Strings -match "v=STSv1"}
MTA-STS Policy
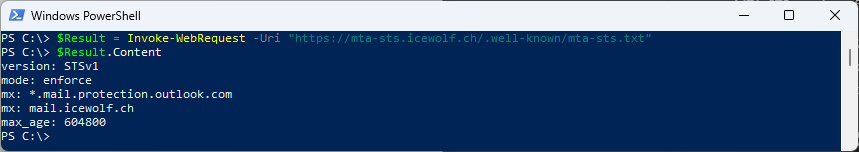
The MTA-STS Policy is a simple Text File that contains a Version, Mode, the MX Certificate Subjects and max Age for caching.
Mode:
-
“enforce”: In this mode, Sending MTAs MUST NOT deliver the message to hosts that fail MX matching or certificate validation or that do not support STARTTLS.
-
“testing”: In this mode, Sending MTAs that also implement the TLSRPT (TLS Reporting) specification [RFC8460] send a report indicating policy application failures (as long as TLSRPT is also implemented by the recipient domain); in any case, messages may be delivered as though there were no MTA-STS validation failure.
-
“none”: In this mode, Sending MTAs should treat the Policy Domain as though it does not have any active policy
The MTA-STS Policy for Exchange Online has been provided here
- Exchange Team Blog Introducing MTA-STS for Exchange Online
version: STSv1
mode: enforce
mx: *.mail.protection.outlook.com
max_age: 604800
To query the MTA-STS Policy you can use this PowerShell Code
$Result = Invoke-WebRequest -Uri "https://mta-sts.icewolf.ch/.well-known/mta-sts.txt"
$Result.Content
As you can see the Policy can contain mutliple MX Records
version: STSv1
mode: enforce
mx: *.mail.protection.outlook.com
mx: mail.icewolf.ch
max_age: 604800
SMTP TLS Reporting
TLS Reporting provides a way to report if the TLS connection could not be established.
- rfc8460 SMTP TLS Reporting
The Reprorting can be eighter a Mailbox or a HTTP POST to an URL.
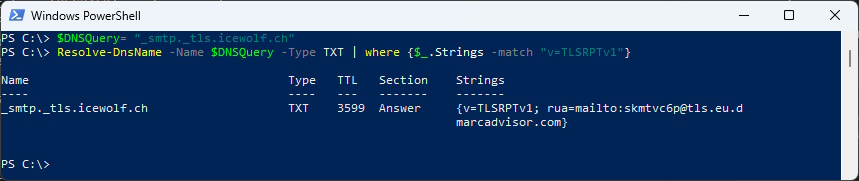
Example for RUA to Mailbox
_smtp._tls.icewolf.ch IN TXT “v=TLSRPTv1; rua=mailto:mailbox@domain.tld”
Examle for RUA to HTTP POST
_smtp._tls.example.com. IN TXT “v=TLSRPTv1; rua=https://reporting.domain.tld/v1/tlsrpt”
Example Record
v=TLSRPTv1; rua=mailto:mailbox@domain.tld
$DNSQuery= "_smtp._tls.icewolf.ch"
Resolve-DnsName -Name $DNSQuery -Type TXT | where {$_.Strings -match "v=TLSRPTv1"}
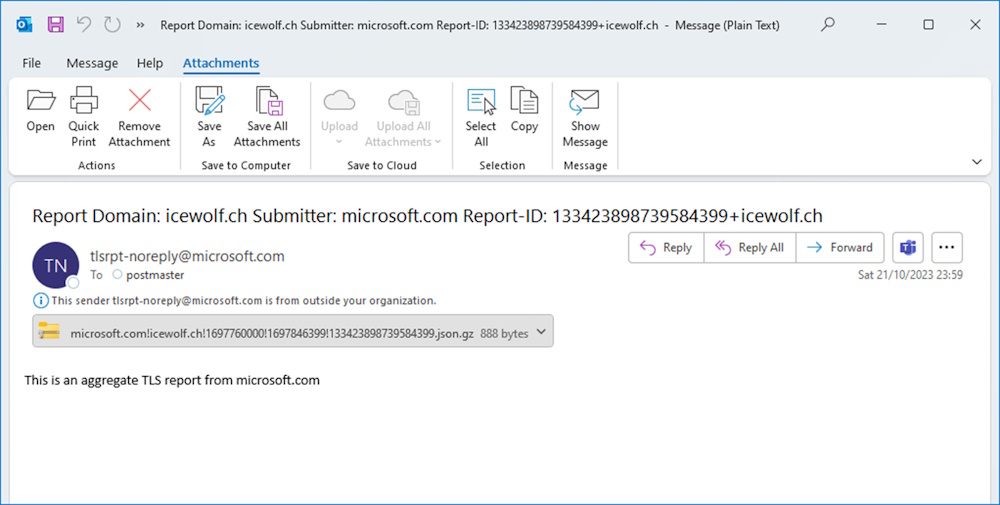
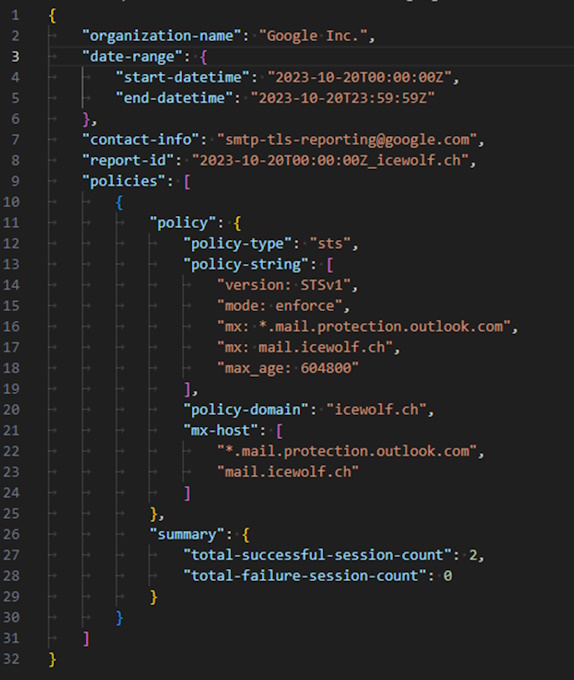
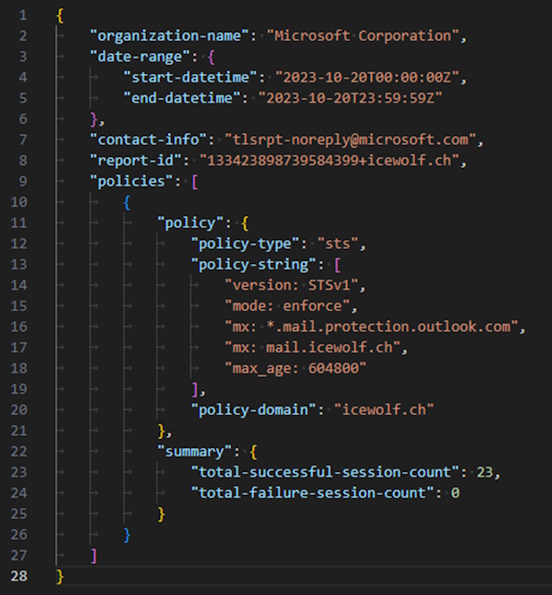
A TLSRPT Email looks quite similar to DMARC Reports. I has an *.gz Attachment that contains a JSON File
Here are two Examples of such JSON Files
Google:
Microsoft:
Exchange Online Report
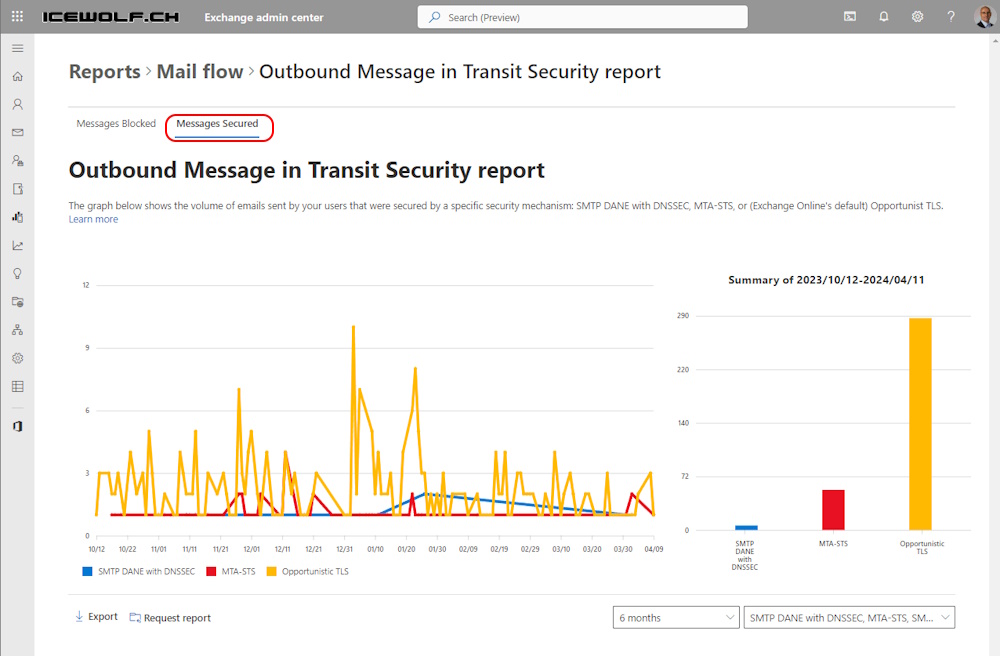
In Exchange Online Admin Center there is a Outbound Message in Transit Security report
As you can see MTA-STS
Regards
Andres Bohren