Entra ID Microsoft Authenticator Registration campain

Hi All,
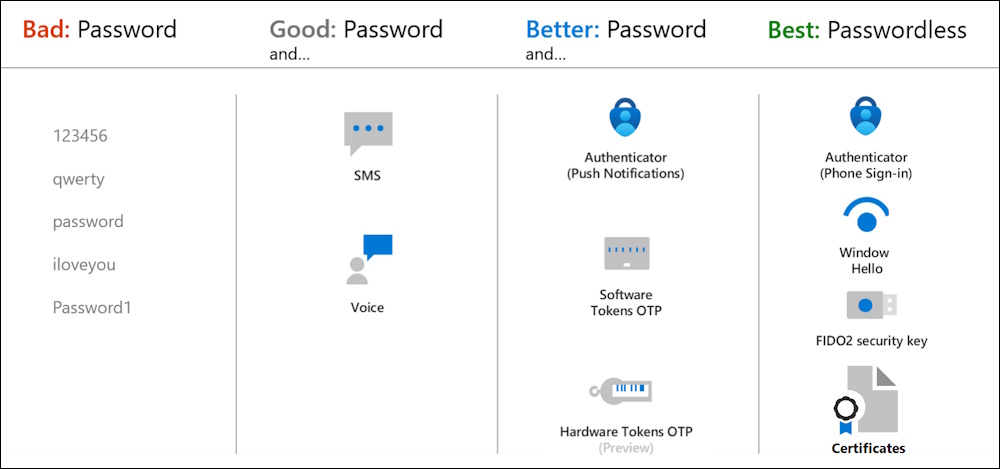
I recently had a customer that still allows SMS for MFA Authentication on theyr Entra ID Tenant.
We all know, that SMS and Voice, should not be used anymore for MFA Authentication.
In addition, i would point out, that can lead to a very bad situation, when using Teams Phone as your Voice destination. Think of how you want to authenticate to Teams, when receiving the MFA Voice call there 😂
Preparation of Showcase
I had to Showcase the Microsoft Authenticator Registration Campain.
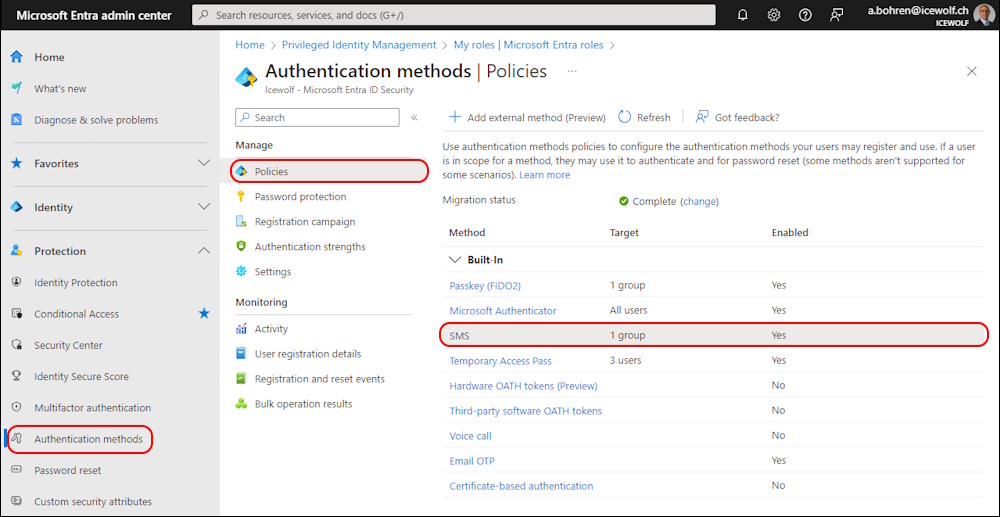
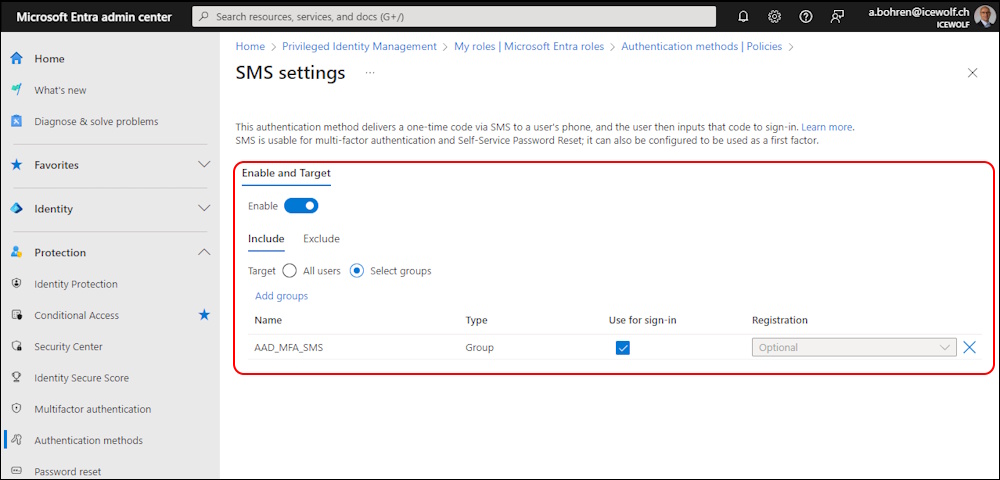
For that purpose, i had to enable SMS Authentication in my Tenant again
But made sure, it’s only available for a Group (that contains our Testuser)
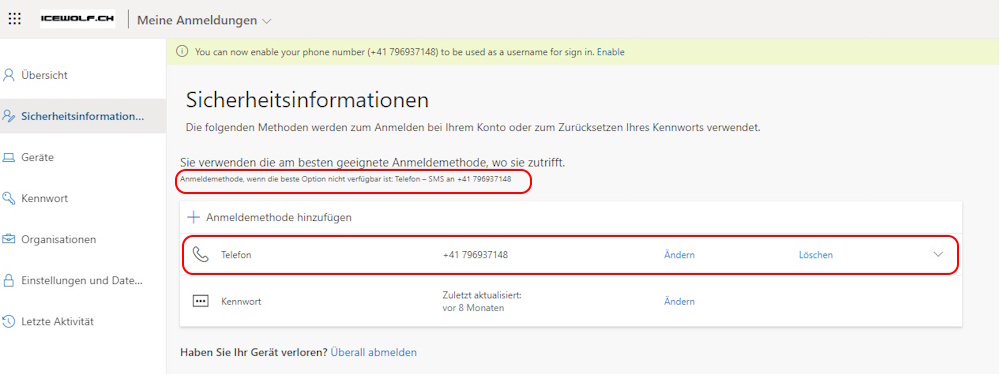
Now im am able to register my MobilePhone for SMS under SecurityInfo
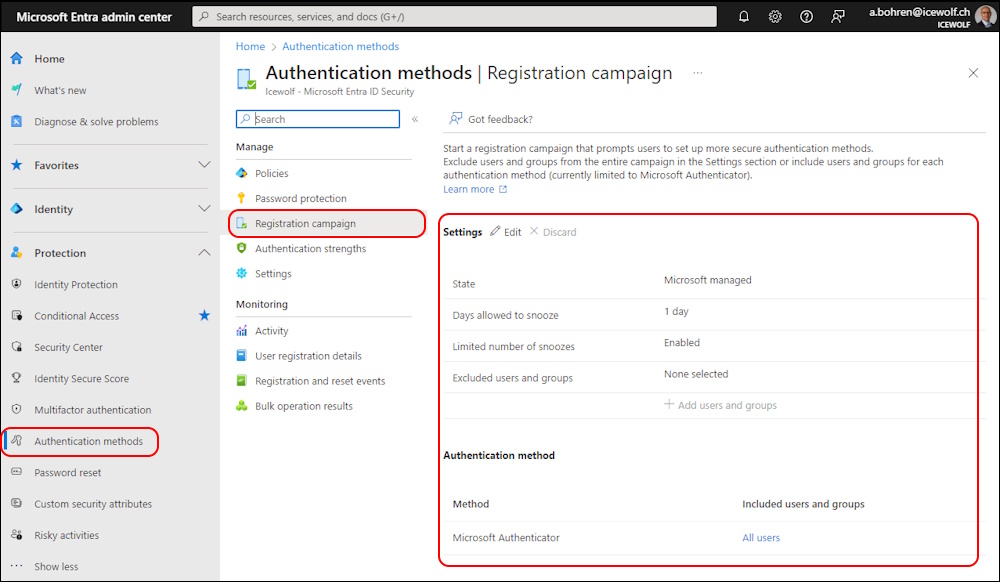
Registration campain
Now let’s activate the Registration campain for Microsoft Authenticator. It’s assigned to all Users with no Exclusion Group. For the purpose of teh Test i limited the Snooze to 1 Day.
Enduser experience
The following Screenshots simulate the Enduser experience.
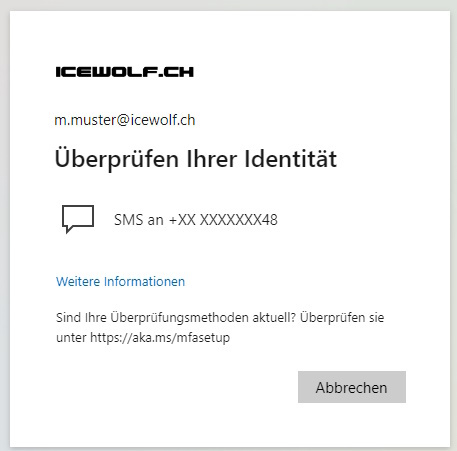
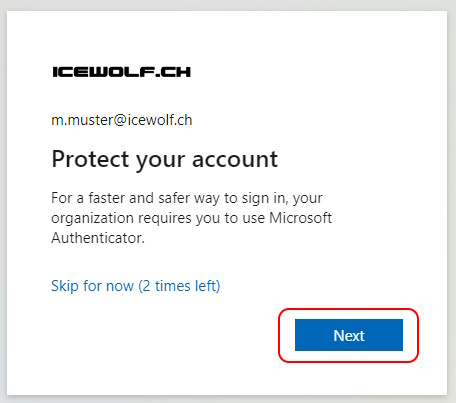
First Login after enabling the Authenticator registration campain with SMS as MFA Factor
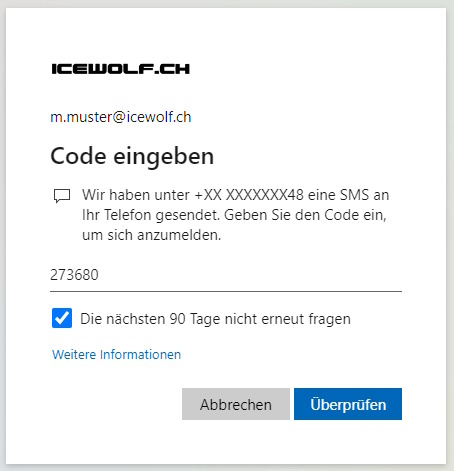
Enter the Code received by SMS
Now i am presented with the Registration - skipped here
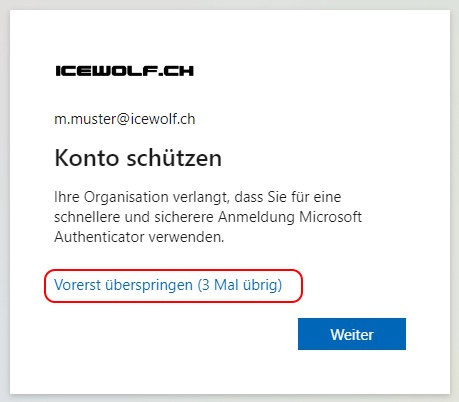
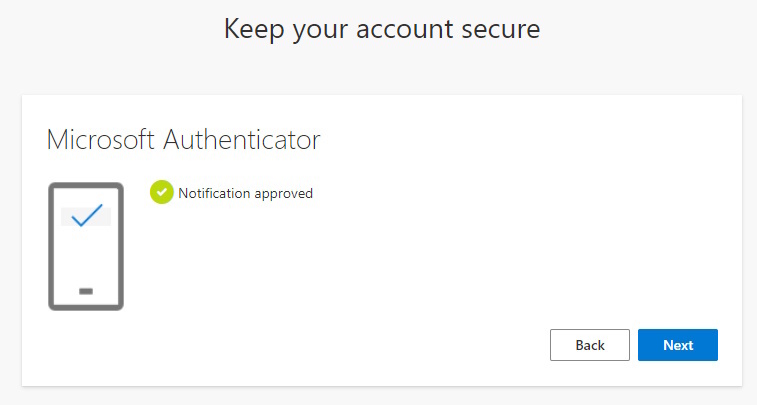
The next time, i clicked on “Next”
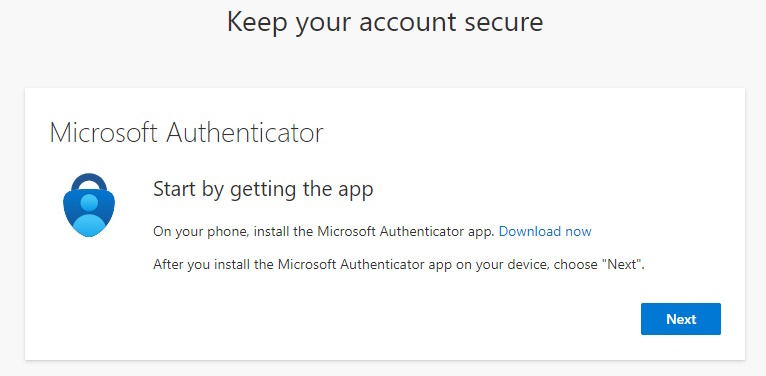
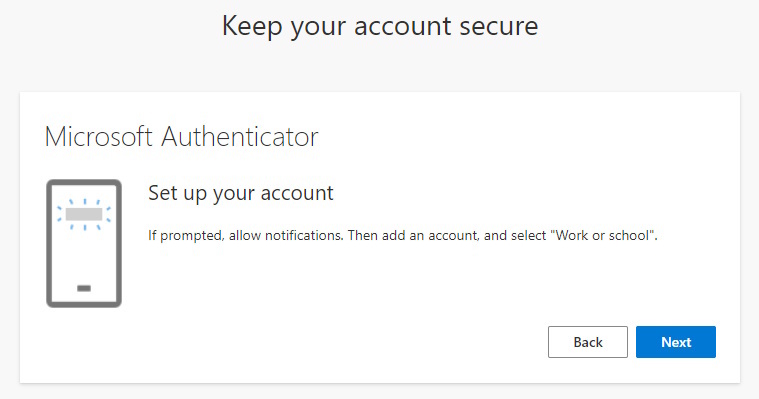
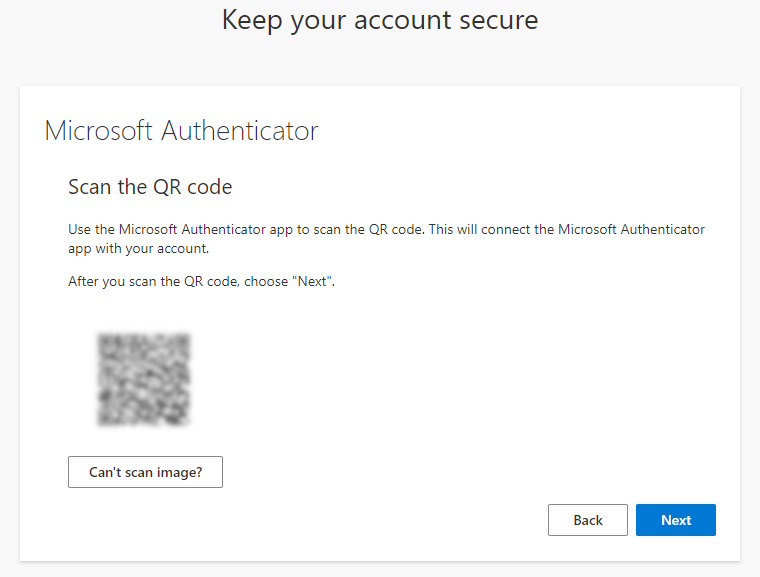
Here starts the Wizard for the Microsoft Authenticator App registration
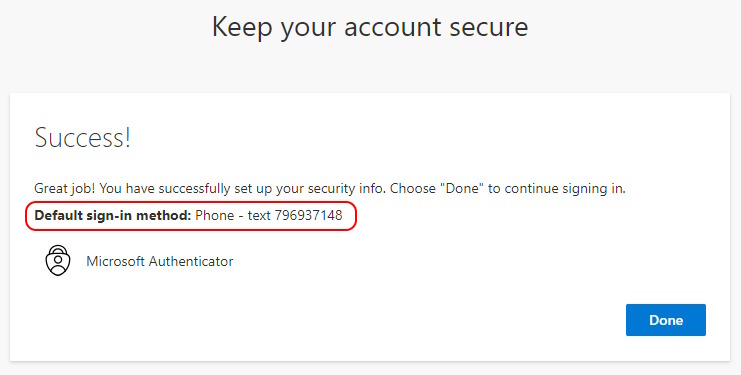
It’s done - Microsoft Authenticator is registered. Sadly the Default sign-in Method is still SMS
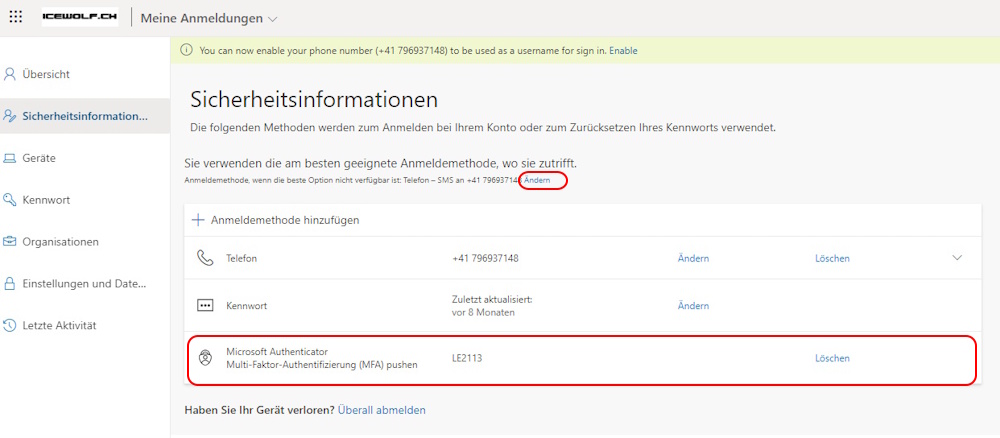
The user can check the Registered Methods in SecurityInfo and also change the default sign-in Method.
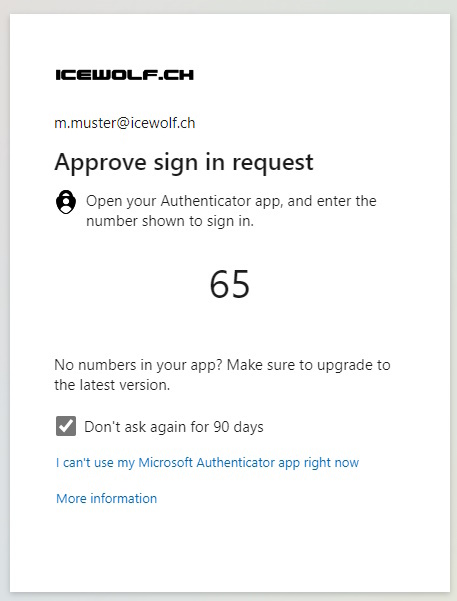
At the next Login with MFA the Authenticator App was used
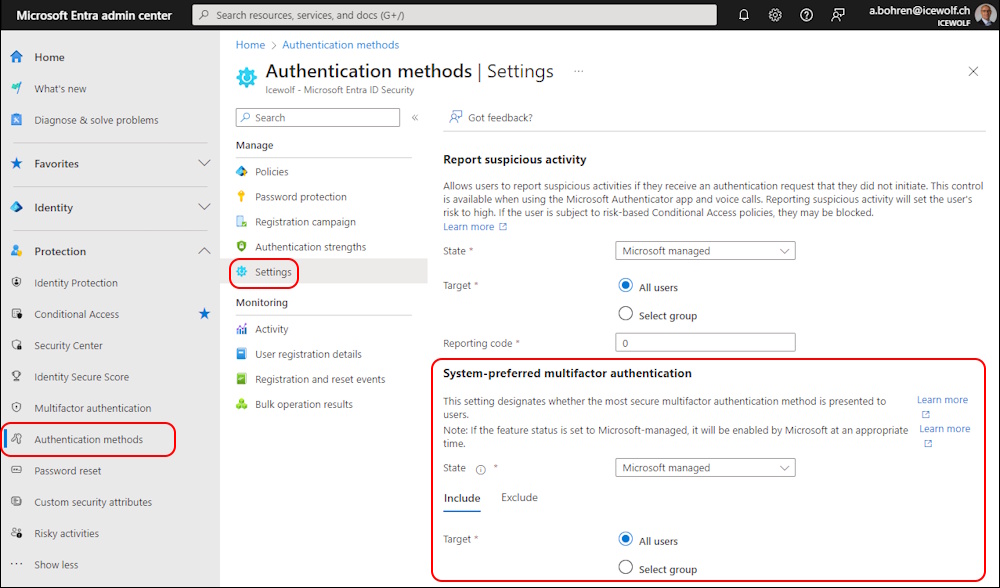
This is because in the Settings the System-preffered multifactor Authentication tries to use the most secure Authentication Method, even the default sign-in Method is set to SMS.
Regards
Andres Bohren