Exchange Server use ADFS for OWA and ECP

Hi All,
A few days ago, i did publish the Article Installing ADFS on Windows Server 2025. That gave me the opportunity, to test some scenarios with Exchange and Active Directory Federation Services (ADFS).
ADFS Server
Let’s start the ADFS MMC
C:\Windows\ADFS\Microsoft.IdentityServer.msc
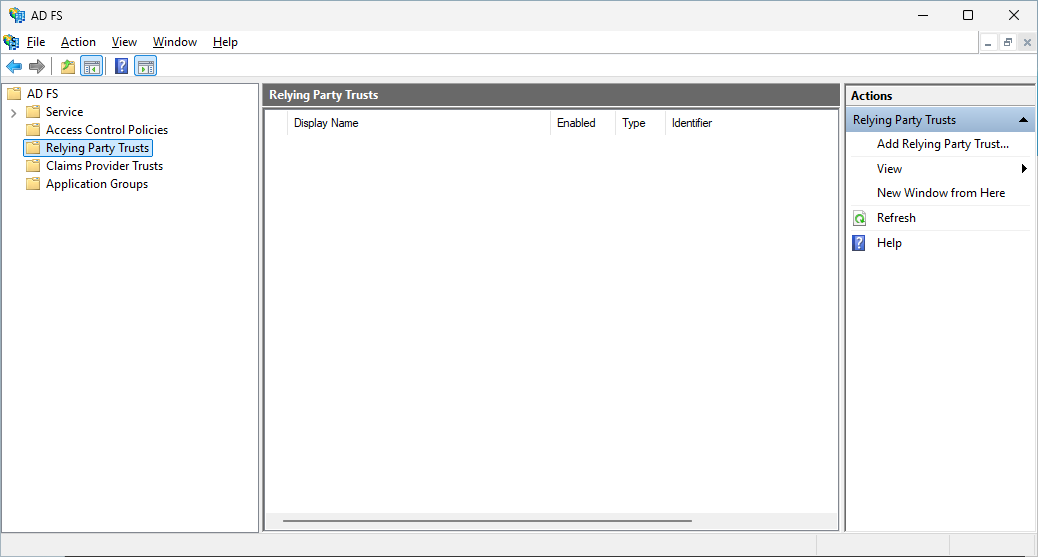
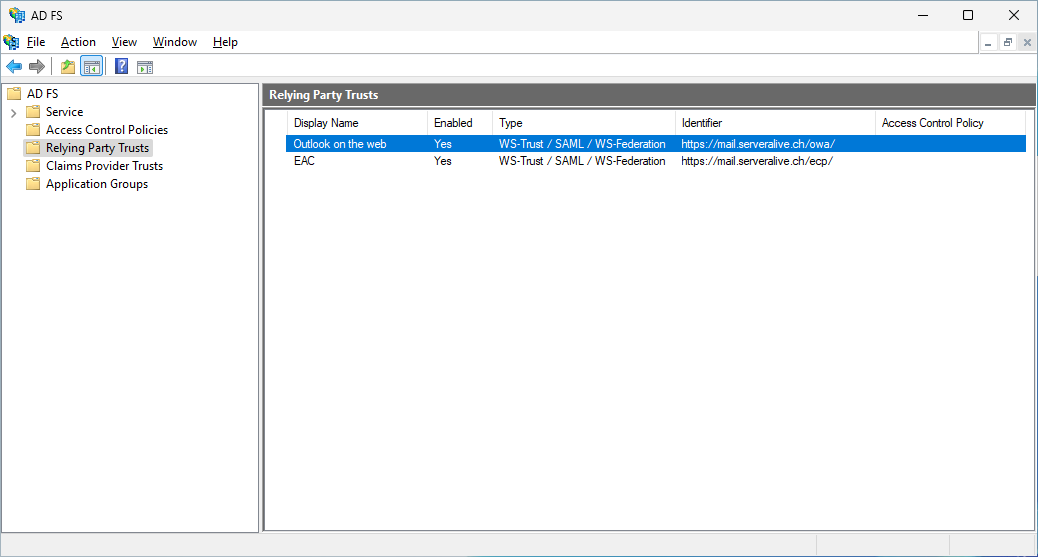
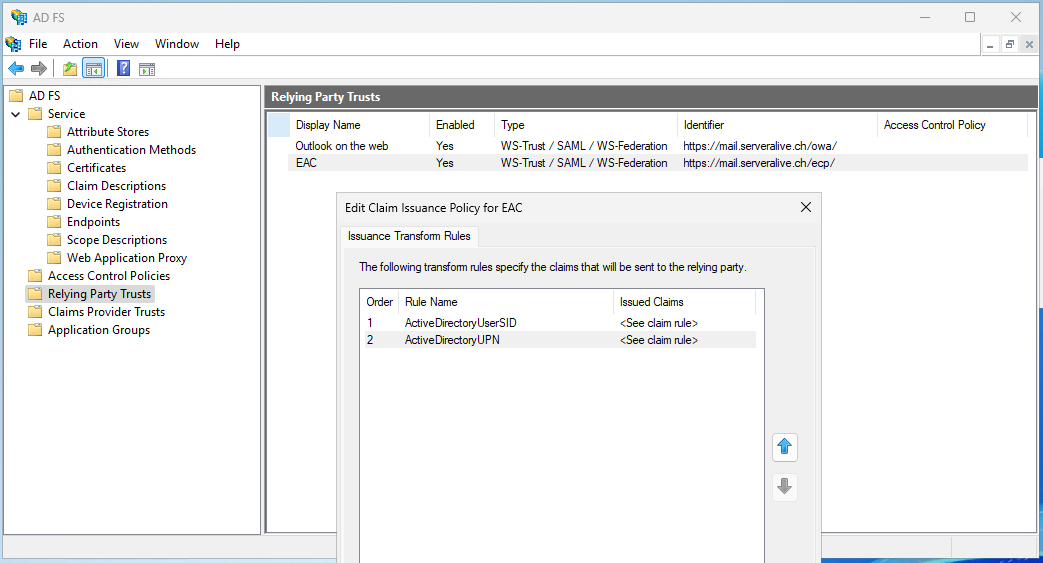
Create relying party trusts in AD FS for Outlook on the web and the EAC
As you can see, the Relying Party Trusts are empty
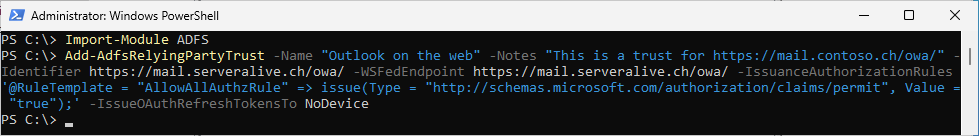
Create Relying Party Trust for Outlook on the Web (owa)
Import-Module ADFS
Add-AdfsRelyingPartyTrust -Name "Outlook on the web" -Notes "This is a trust for https://mail.contoso.ch/owa/" -Identifier https://mail.serveralive.ch/owa/ -WSFedEndpoint https://mail.serveralive.ch/owa/ -IssuanceAuthorizationRules '@RuleTemplate = "AllowAllAuthzRule" => issue(Type = "http://schemas.microsoft.com/authorization/claims/permit", Value = "true");' -IssueOAuthRefreshTokensTo NoDevice
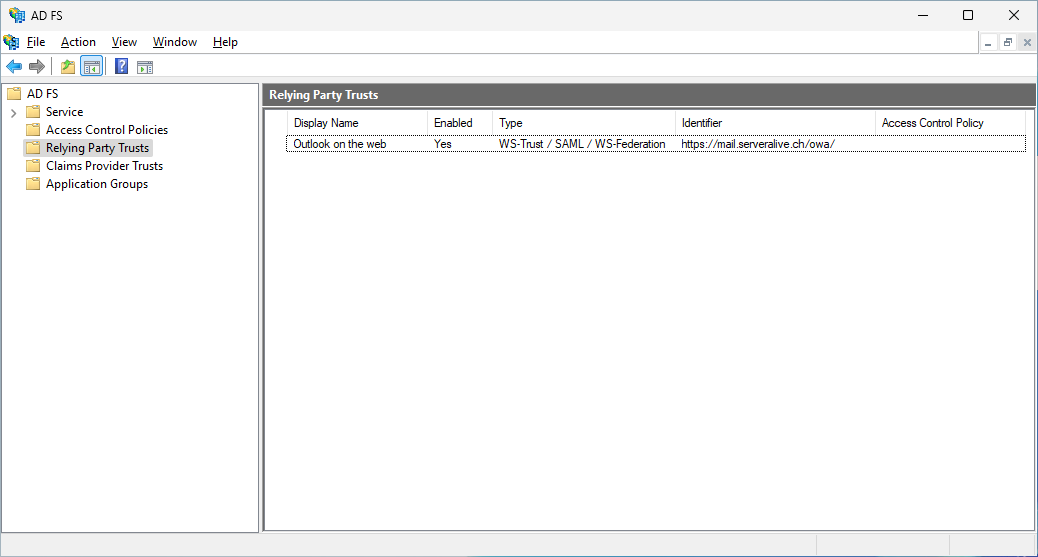
Relying Party Trust for OWA now there
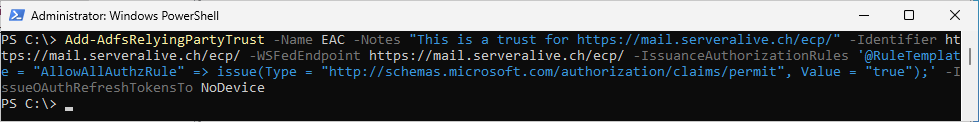
Create Relying Party Trust for Exchange Control Panel (ecp)
Add-AdfsRelyingPartyTrust -Name EAC -Notes "This is a trust for https://mail.serveralive.ch/ecp/" -Identifier https://mail.serveralive.ch/ecp/ -WSFedEndpoint https://mail.serveralive.ch/ecp/ -IssuanceAuthorizationRules '@RuleTemplate = "AllowAllAuthzRule" => issue(Type = "http://schemas.microsoft.com/authorization/claims/permit", Value = "true");' -IssueOAuthRefreshTokensTo NoDevice
Relying Party Trust for ECP now there
Create custom claim rules in AD FS for Outlook on the web and the EAC
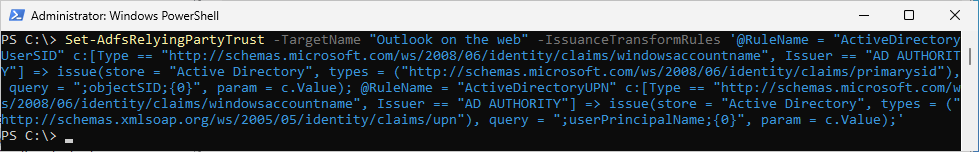
Now let’s create the Relying Party Trust for OWA
Set-AdfsRelyingPartyTrust -TargetName "Outlook on the web" -IssuanceTransformRules '@RuleName = "ActiveDirectoryUserSID" c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"] => issue(store = "Active Directory", types = ("http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid"), query = ";objectSID;{0}", param = c.Value); @RuleName = "ActiveDirectoryUPN" c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"] => issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"), query = ";userPrincipalName;{0}", param = c.Value);'
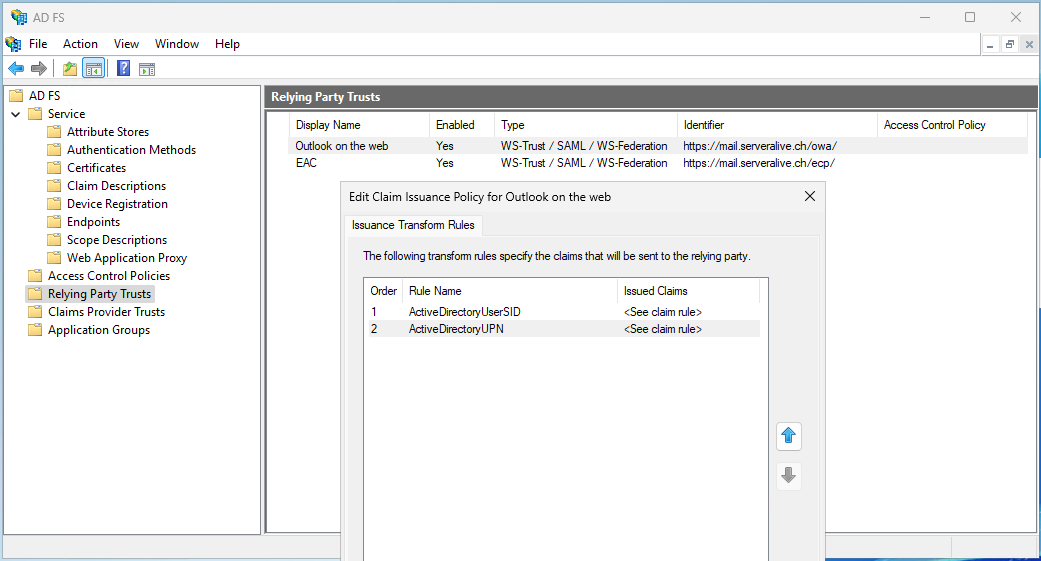
Now you can see the Issuance Transform Rules for OWA
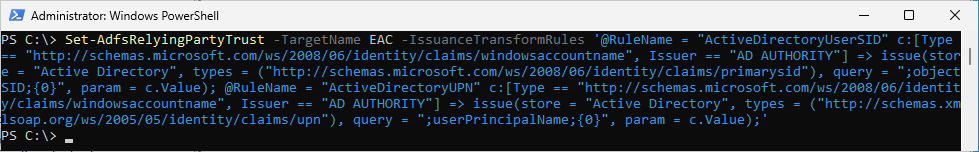
Now let’s create the Relying Party Trust for ECP
Set-AdfsRelyingPartyTrust -TargetName EAC -IssuanceTransformRules '@RuleName = "ActiveDirectoryUserSID" c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"] => issue(store = "Active Directory", types = ("http://schemas.microsoft.com/ws/2008/06/identity/claims/primarysid"), query = ";objectSID;{0}", param = c.Value); @RuleName = "ActiveDirectoryUPN" c:[Type == "http://schemas.microsoft.com/ws/2008/06/identity/claims/windowsaccountname", Issuer == "AD AUTHORITY"] => issue(store = "Active Directory", types = ("http://schemas.xmlsoap.org/ws/2005/05/identity/claims/upn"), query = ";userPrincipalName;{0}", param = c.Value);'
Now you can see the Issuance Transform Rules for ECP
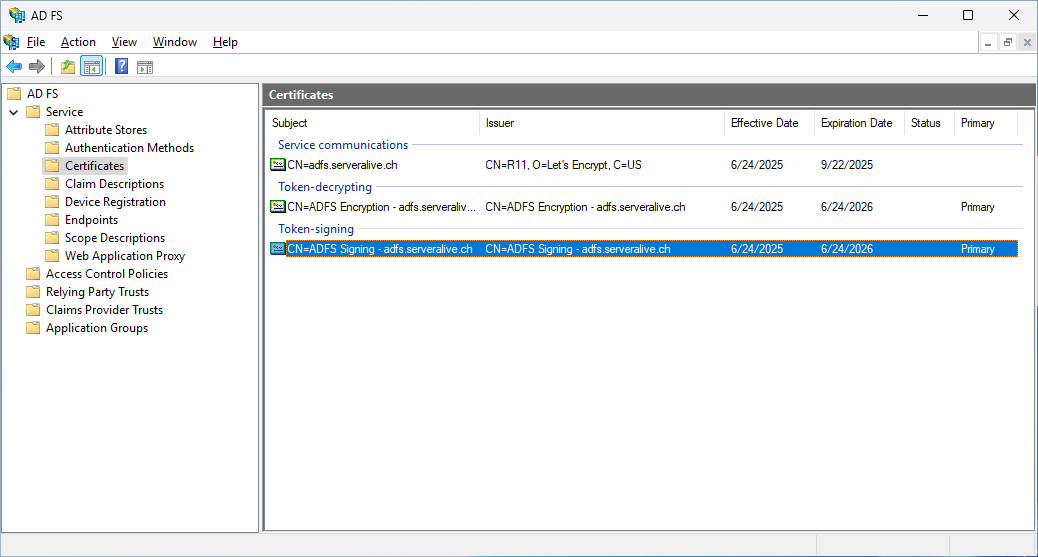
Export Token Signin Certificate on ADFS
Now we need to Export the ADFS Token Signin Certificate
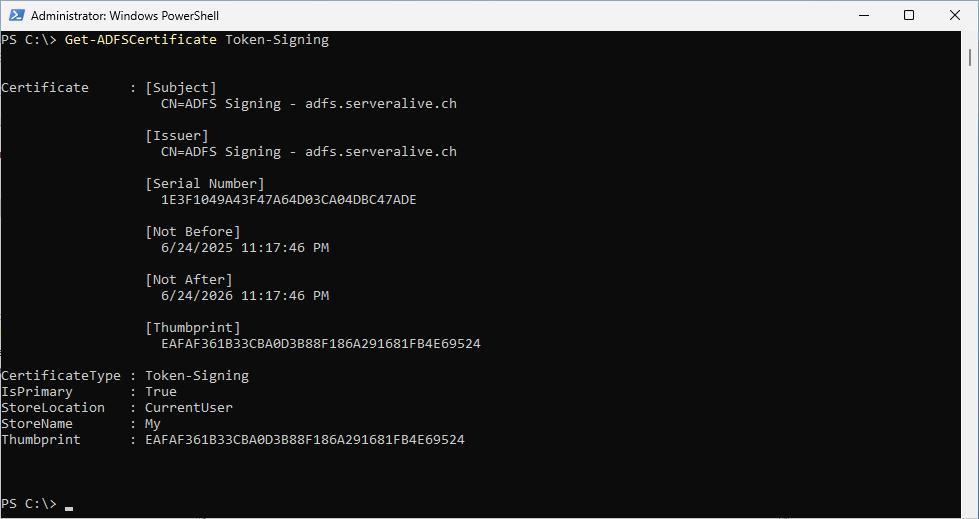
Show the ADFS oken Signin Certificate
Get-ADFSCertificate Token-Signing
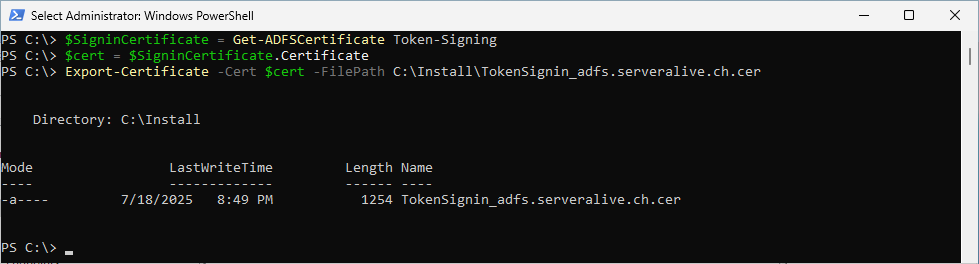
Export the Certificate
$SigninCertificate = Get-ADFSCertificate Token-Signing
$cert = $SigninCertificate.Certificate
Export-Certificate -Cert $cert -FilePath C:\Install\TokenSignin_adfs.serveralive.ch.cer
File has been exportet to a *.CER File
Import Signing Certificate in Exchange
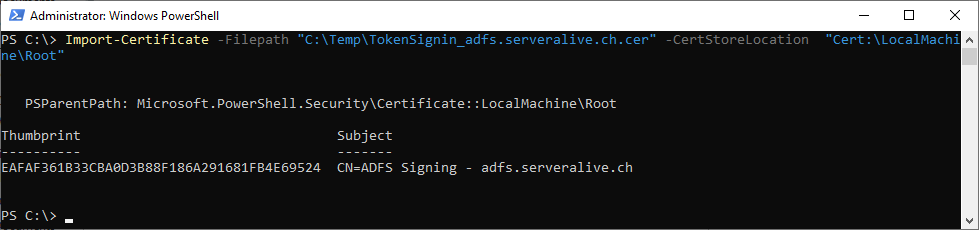
Now you need to import the ADFS Token SignIn Certificate to the Exchange Server LocalMachine Certificate Store under Root
Import-Certificate -Filepath "C:\Temp\TokenSignin_adfs.serveralive.ch.cer" -CertStoreLocation "Cert:\LocalMachine\Root"
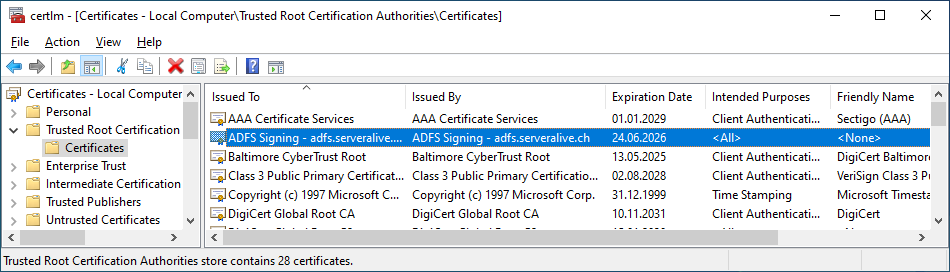
Here you can see the imported Certificate
Configure the Exchange organization to use AD FS authentication
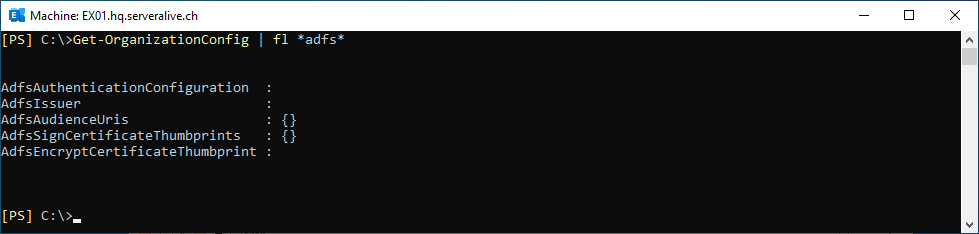
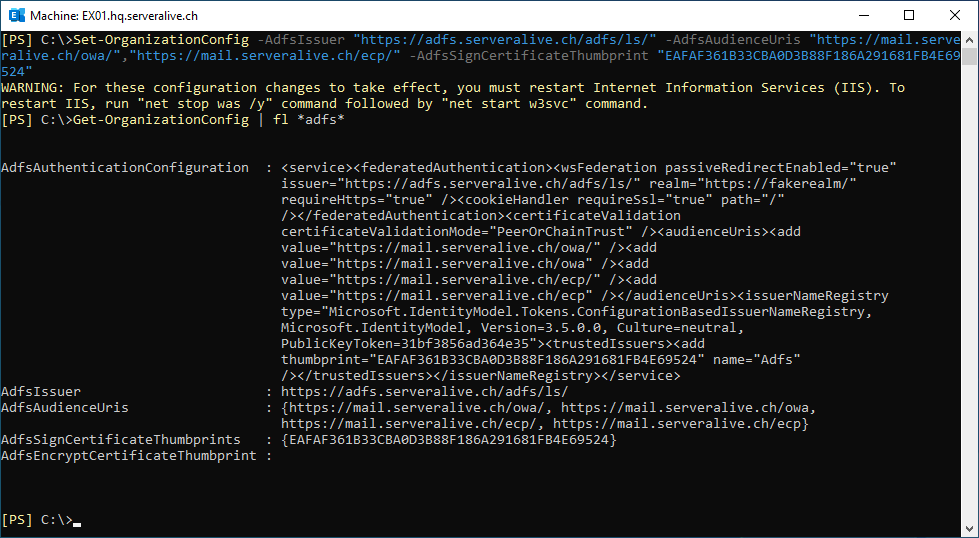
Before we change any Exchange Configuration, let’s check the Exchange Settings
Get-OrganizationConfig | fl *adfs*
Now, let’s create the ADFS Settings in Exchange by using the ADFS Token Signing Thumbprint
Set-OrganizationConfig -AdfsIssuer "https://adfs.serveralive.ch/adfs/ls/" -AdfsAudienceUris "https://mail.serveralive.ch/owa/","https://mail.serveralive.ch/ecp/" -AdfsSignCertificateThumbprint "EAFAF361B33CBA0D3B88F186A291681FB4E69524"
Get-OrganizationConfig | fl *adfs*
Configure AD FS authentication on the Outlook on the web and EAC virtual directories
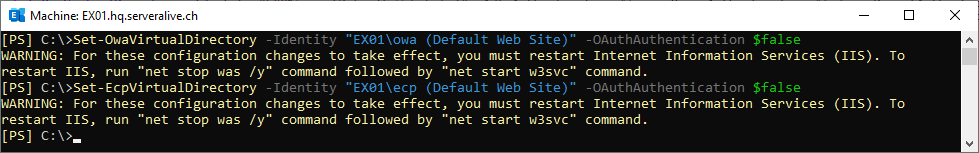
I had OAuth Authentication Enabled on OWA and ECP. I will disable this first.
Set-OwaVirtualDirectory -Identity "EX01\owa (Default Web Site)" -OAuthAuthentication $false
Set-EcpVirtualDirectory -Identity "EX01\ecp (Default Web Site)" -OAuthAuthentication $false
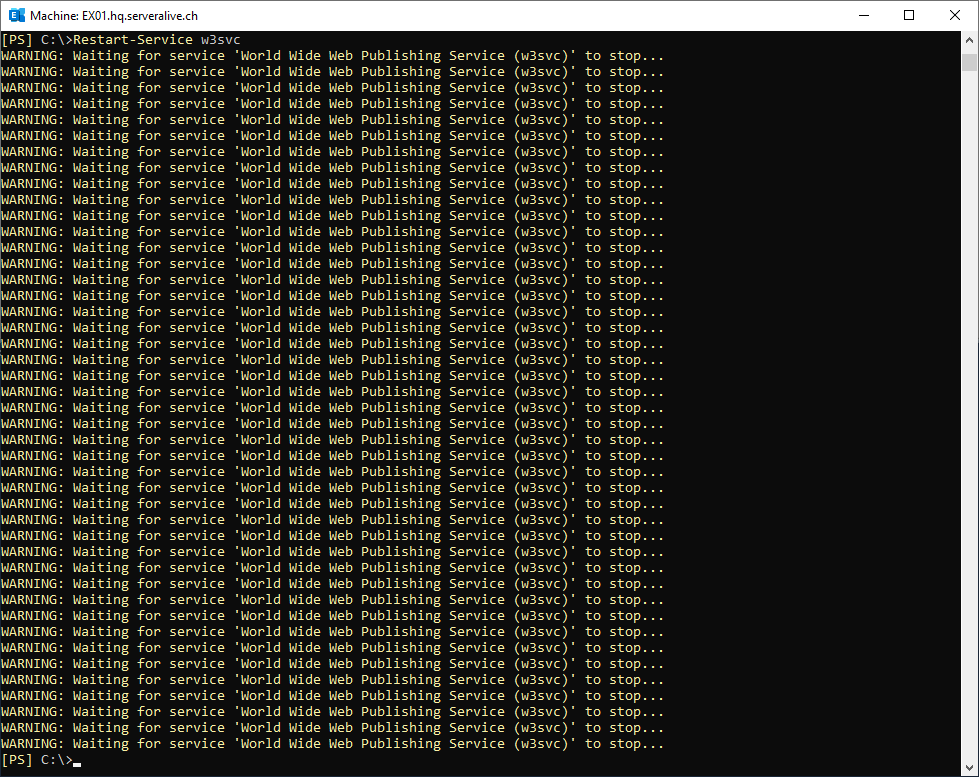
Restart IIS
Restart-Service w3svc
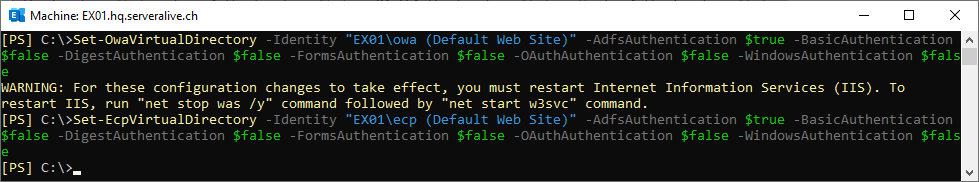
Enable ADFSAuthentication on OWA and ECP
Set-EcpVirtualDirectory -Identity "EX01\ecp (Default Web Site)" -AdfsAuthentication $true -BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $false -OAuthAuthentication $false -WindowsAuthentication $false
Set-OwaVirtualDirectory -Identity "EX01\owa (Default Web Site)" -AdfsAuthentication $true -BasicAuthentication $false -DigestAuthentication $false -FormsAuthentication $false -OAuthAuthentication $false -WindowsAuthentication $false
Restart IIs
Restart-Service w3svc
OWA Tests
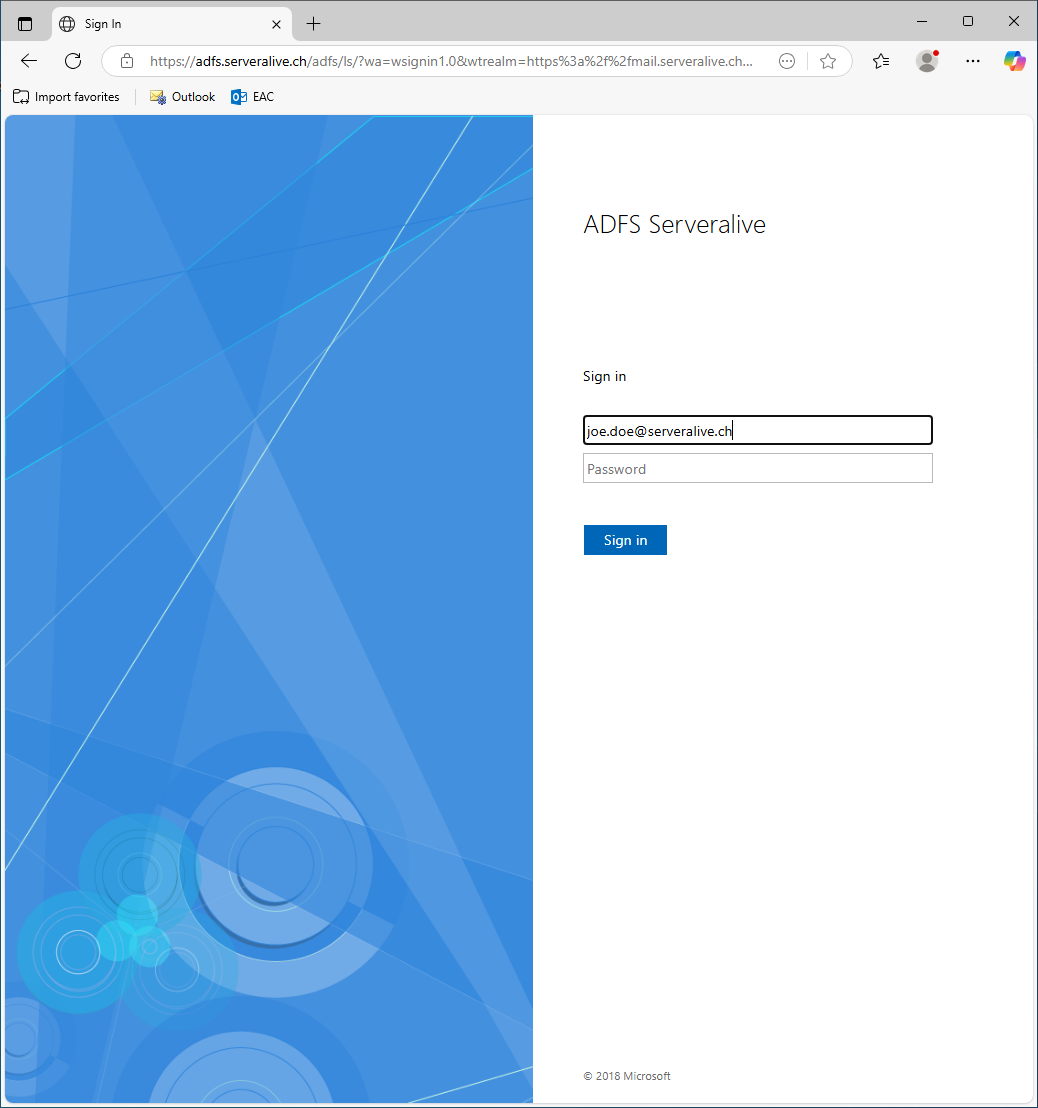
When i open the Browser and navigate to https://mail.serveralive.ch/owa i will be redirected automatically to ADFS
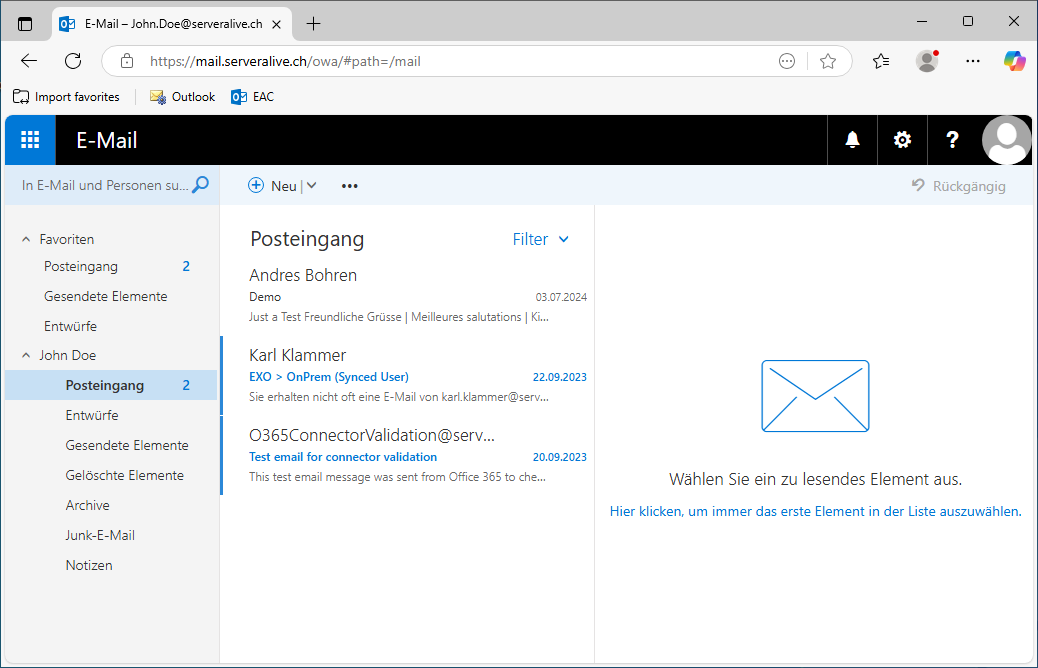
After successful Authentication i will be redirected to OWA and get the Contents of the Mailbox
Details
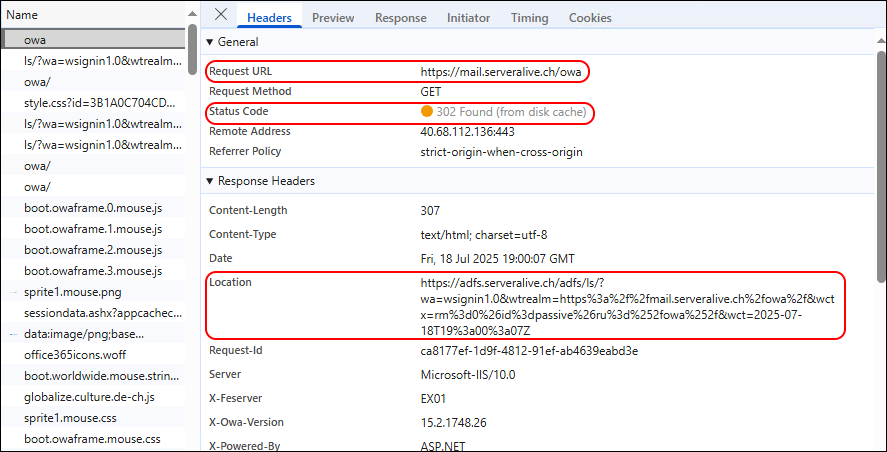
Made some Network Trace with the Browser Development Tools.
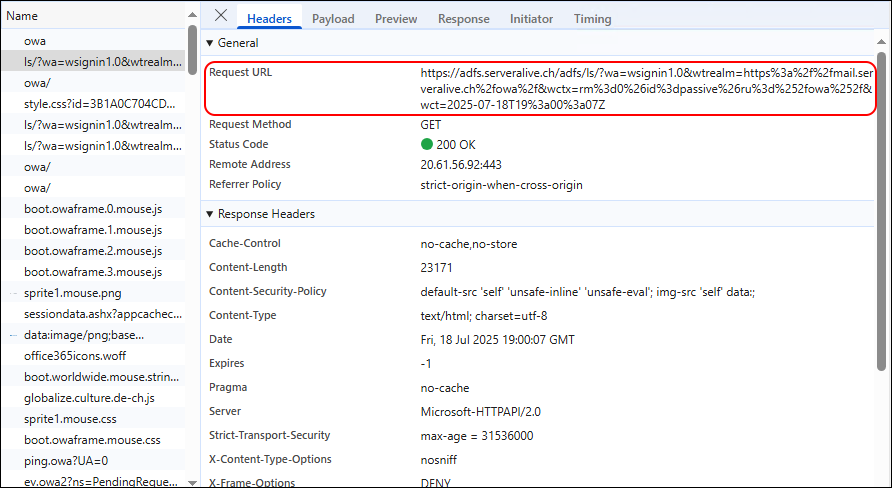
You can see the Redirect to ADFS when navigation to the OWA URL
Getting the ADFS Signin Page
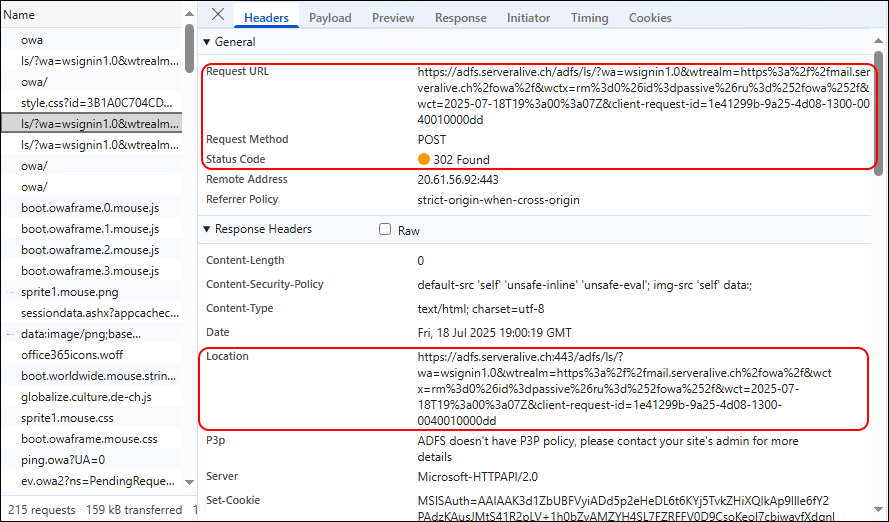
Username and Password are sent via POST and get a redirect to another ADFS URL
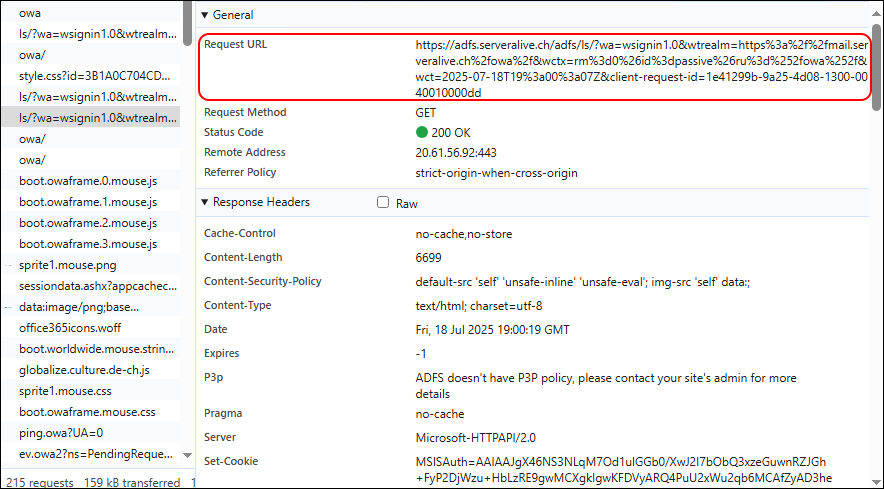
Here i don’t know how the Redirect back to OWA works
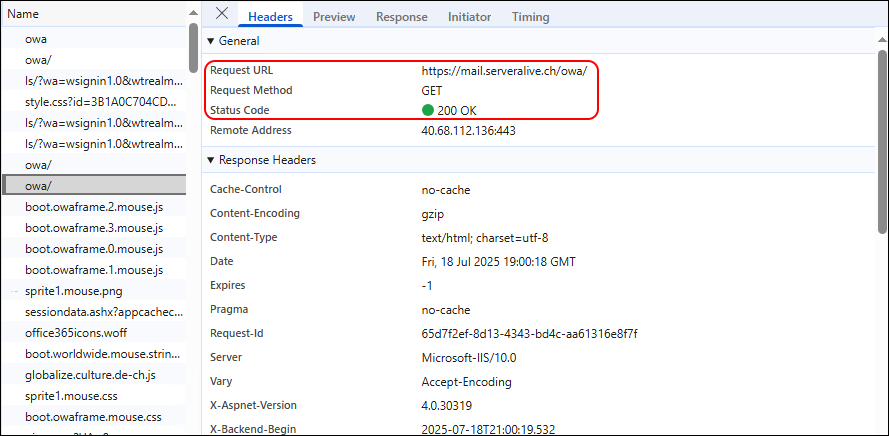
But we land back on OWA and are Authenticated
Summary
I followed this Article Use AD FS claims-based authentication with Outlook on the web and added some clarifications and some additional PowerShell Commands.
I plan to document also this in one of the future Blog Articles Enabling Modern Auth in Exchange on-premises
Regards
Andres Bohren