Change source of authority (SOA) for Groups (Preview)

Hi All,
Recently i published an Article about the Preview of the Change of authority for the Exchange Attributes Change source of authority (SOA) for Exchange Attributes (Preview)
In this Article i will show you the Preview for changing the source of authority (SOA) for Groups.
- Configure Group Source of Authority (SOA) (Preview)
- Embrace cloud-first posture: Convert Group Source of Authority to the cloud (Preview)
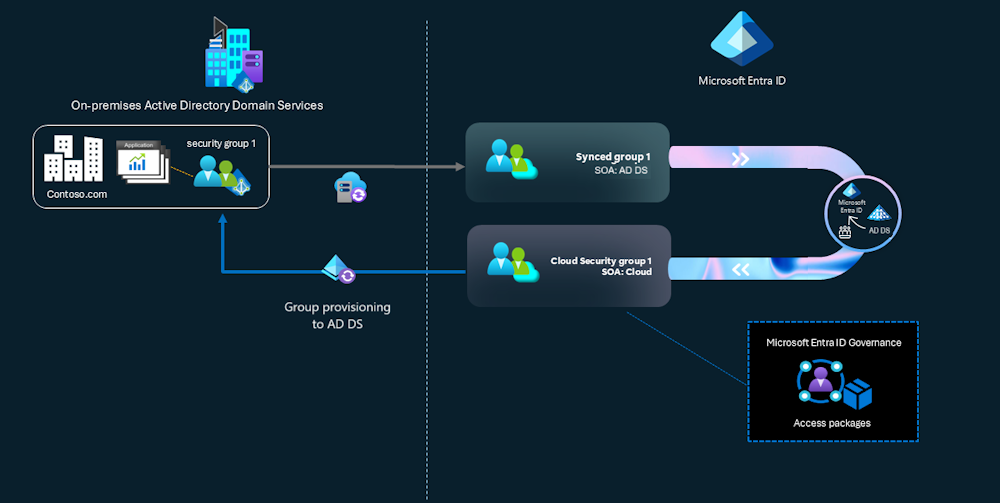
In an Enterprise Evironement, typically Users and Groups are Synced with Entra Connect or Cloud Sync to Entra ID.
Now you are able to convert syched Active Directory Groups to Cloud Security Groups. And with Cloud Sync back to Active Directory.
Prerequisits
- Entra Connect Sync build version 2.5.76.0 or later
- Entra Cloud Sync client build version 1.1.1370.0 or later
Limitations
No reconciliation support for AD DS groups: An AD DS admin (or an application with sufficient permissions) can directly modify an AD DS group. If Group SOA is converted for the group, or if cloud security group provisioning to AD DS is enabled, those local AD changes aren’t reflected in Microsoft Entra ID. When a change to the cloud security group is made, any local AD DS changes are overwritten when group provisioning to AD DS runs.
No dual write allowed: After you start to manage the memberships for the converted group (say cloud group A) from Microsoft Entra ID, and you provision this group to AD as a nested group under another AD DS group (OnPremGroupB) that’s in scope for sync to Microsoft Entra ID, the membership references of group A aren’t synced when sync happens for OnPremGroupB. The membership references aren’t synced because the sync client doesn’t know the cloud group membership references. This behavior is by design.
No SOA conversion of nested groups: If there are nested groups in AD DS, and you want to convert the SOA of the parent group or top group to Microsoft Entra ID, only the parent group SOA is converted. Nested groups in the parent group continue to be AD DS groups. You need to convert the SOA of any nested groups one-by-one. We recommend you start with the group that is lowest in the hierarchy, and move up the tree.
No support for extension attributes (1-15): Extension attributes 1–15 aren’t supported on cloud security groups and aren’t supported after SOA is converted.
Cloud Sync
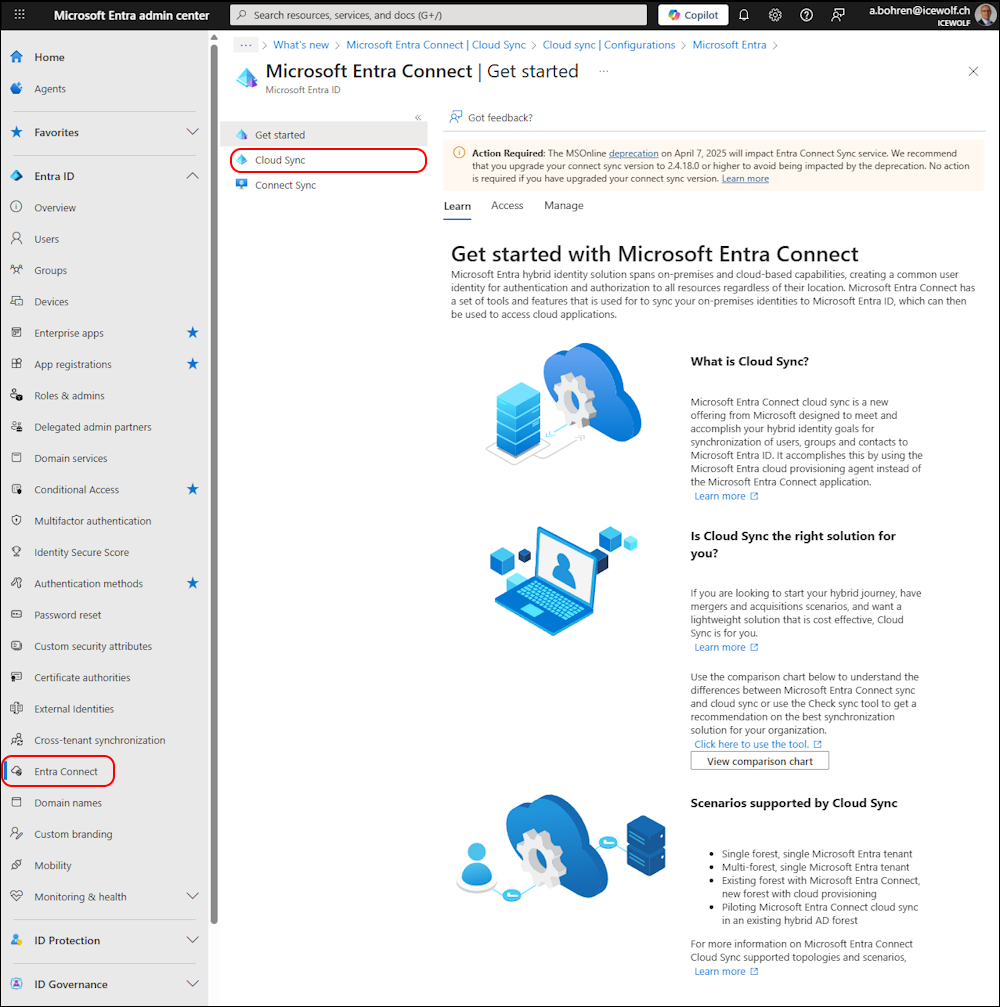
Let’s set up Cloud Sync to sync the Groups from Entra ID back to Active Directory.
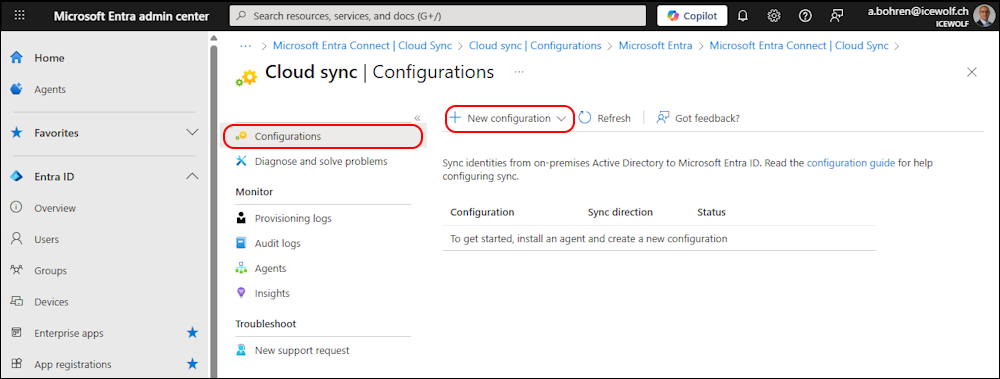
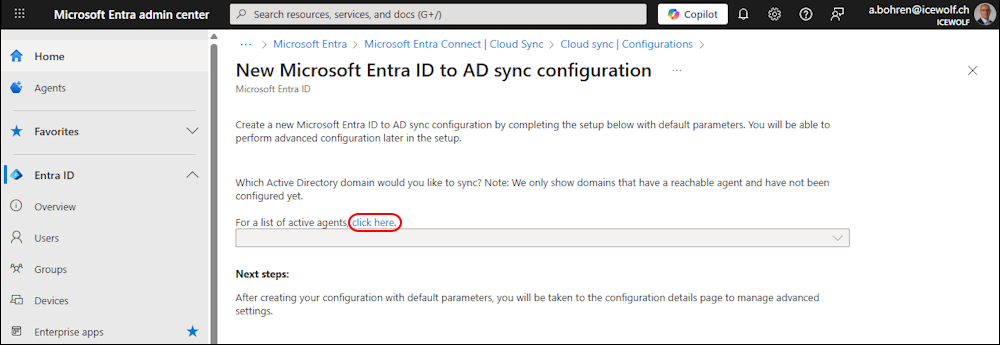
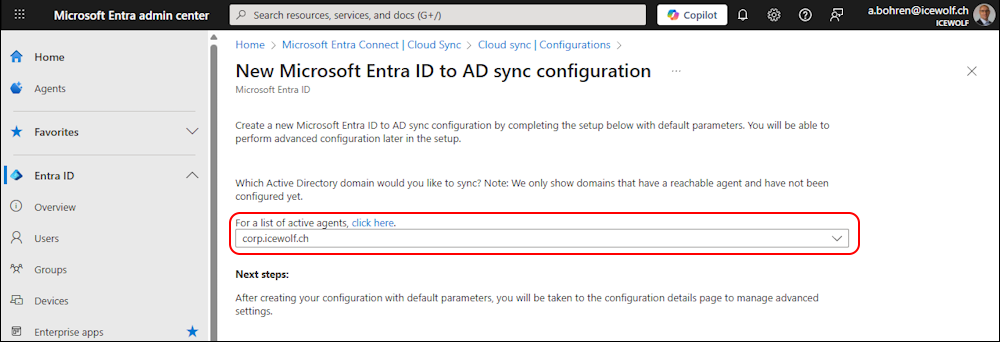
In Entra Admin Center go to Entra ID > Entra Connect > Cloud Sync
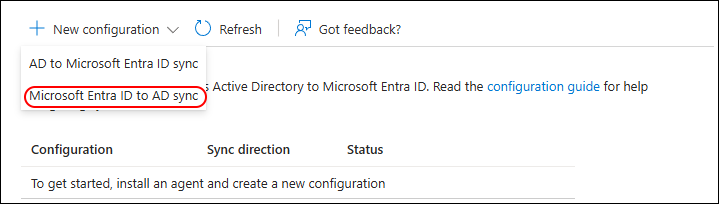
In the Configurations click on “+ New configuration”
Select “Microsoft Entra ID to AD Sync”
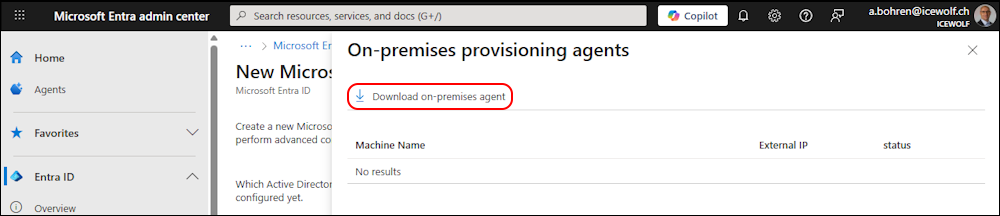
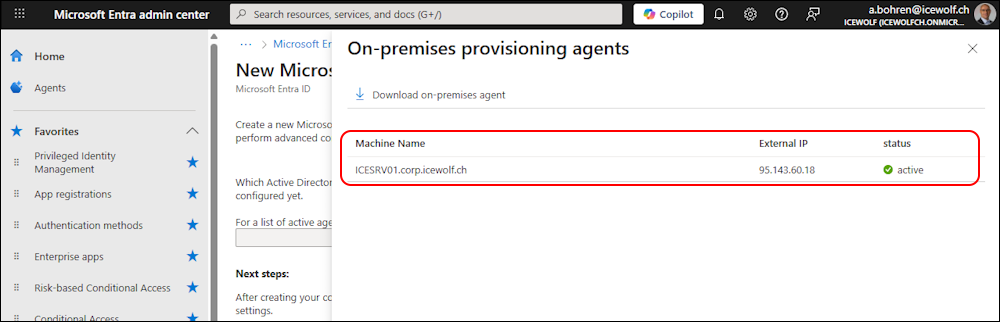
Click on the Link for the Agents
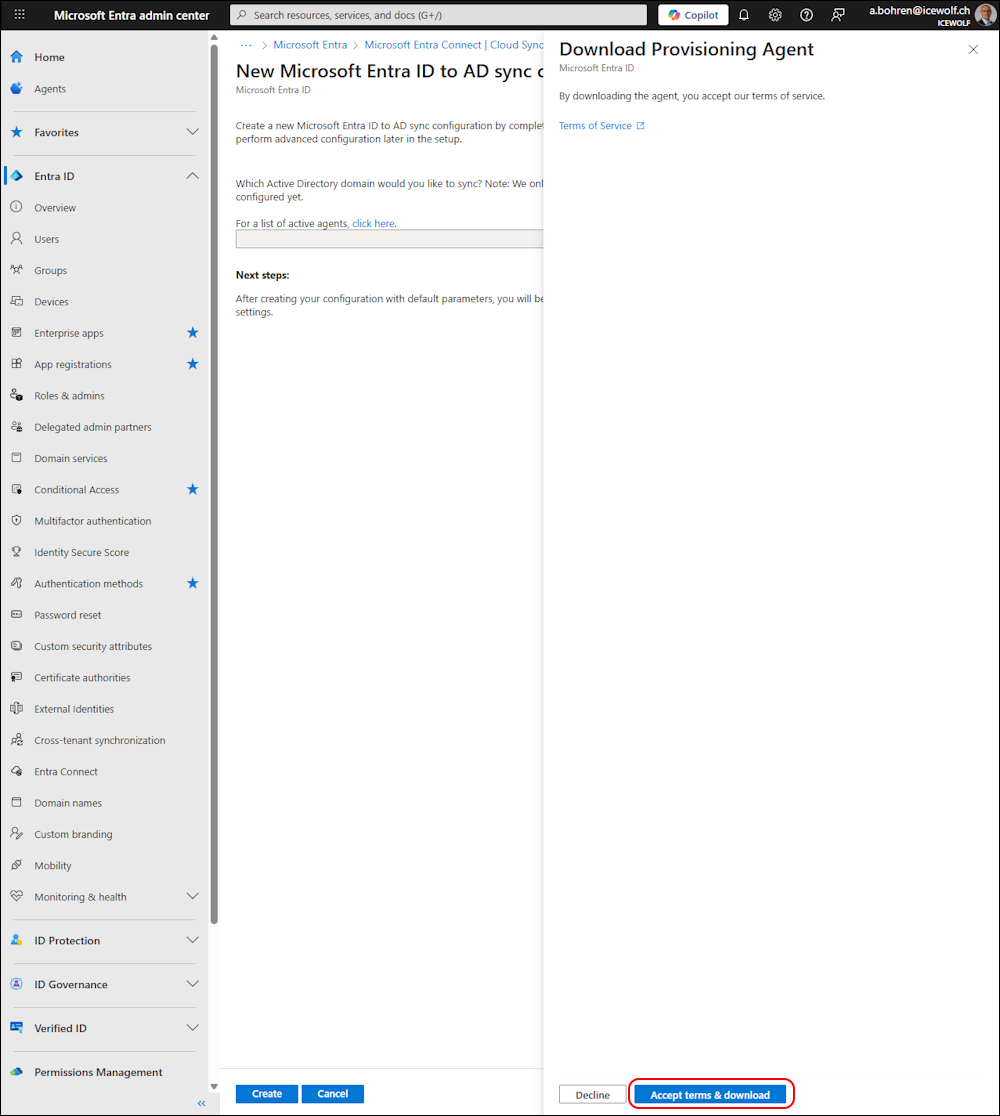
Now you can download the Agent
Accept Terms and download
Cloud Sync Client
I have a very small Test Environment. So i will install the Cloud Sync Client on the Domain Controller where also Entra Connect Sync is installed.
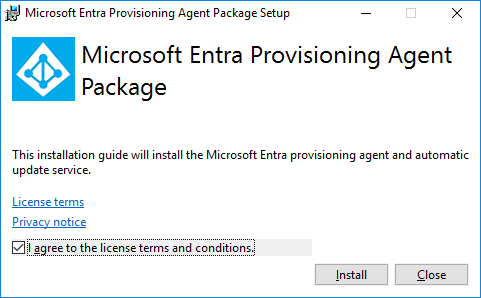
Installing
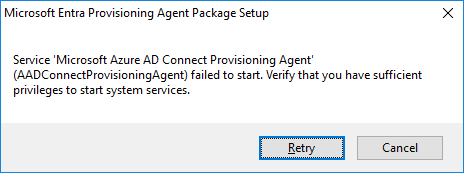
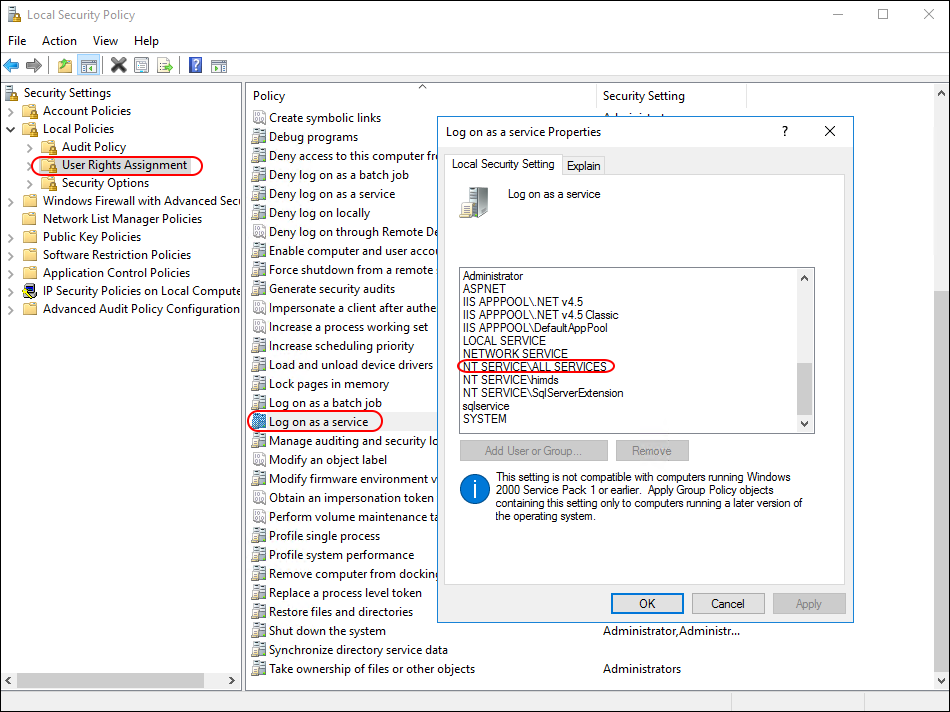
I am logged in as Domain Administrator but still did get this Message. Several Retrys did not work.
I’ve ended up with a failure
Finally i found the following Article: Microsoft Entra Hybrid Sync Agent Installation Issues - No privileges to install MSI
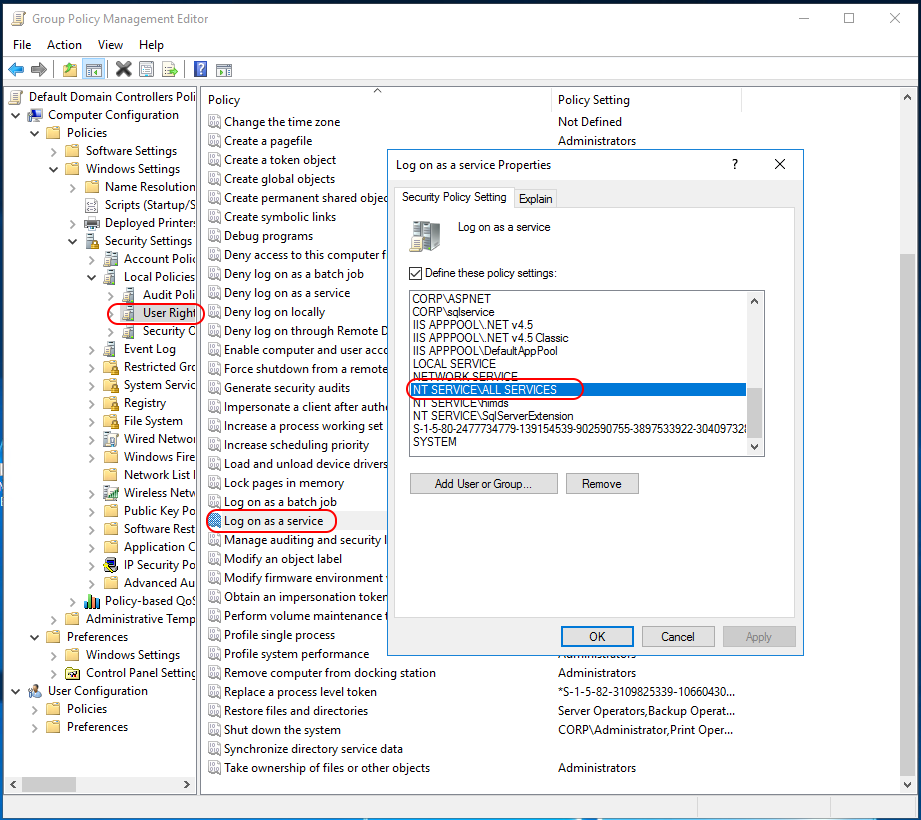
I’ve changed the Group Policy. Windows Settings > Security Settings > Local Policies > User Rights Assignment > Log on as a service > “NT SERVICE\ALL SERVICES”
Ran a Group Policy Update
gpupdate /force
and then checked the Group Policy to see if the Setting was applied
secpol.msc
Now i was able to install the Cloud Sync Client
Cloud Sync Client Configuration
Immediately after the Installation succeedet. The Configuration Wizard of Cloud Sync Client startet.
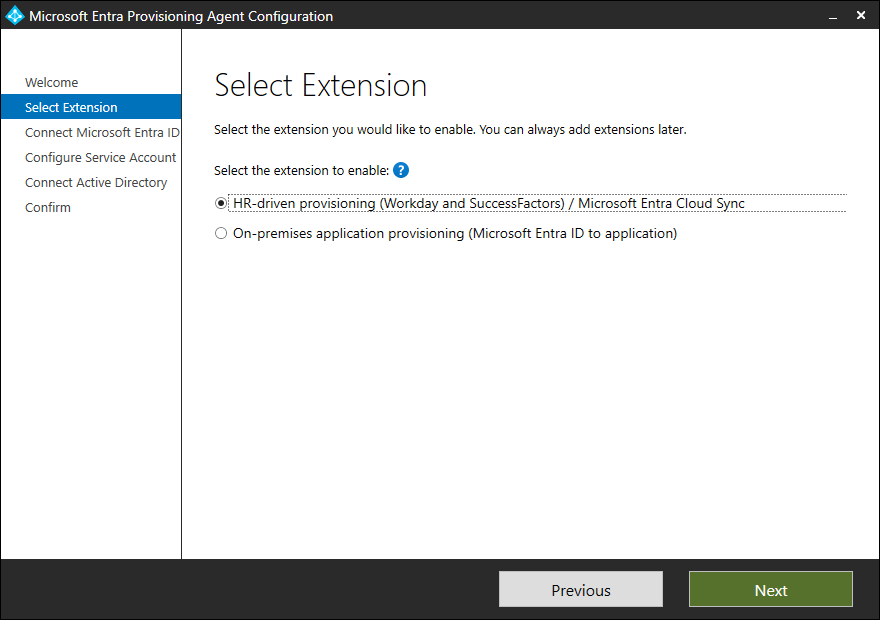
I’ve selected “HR-driven provisioning”
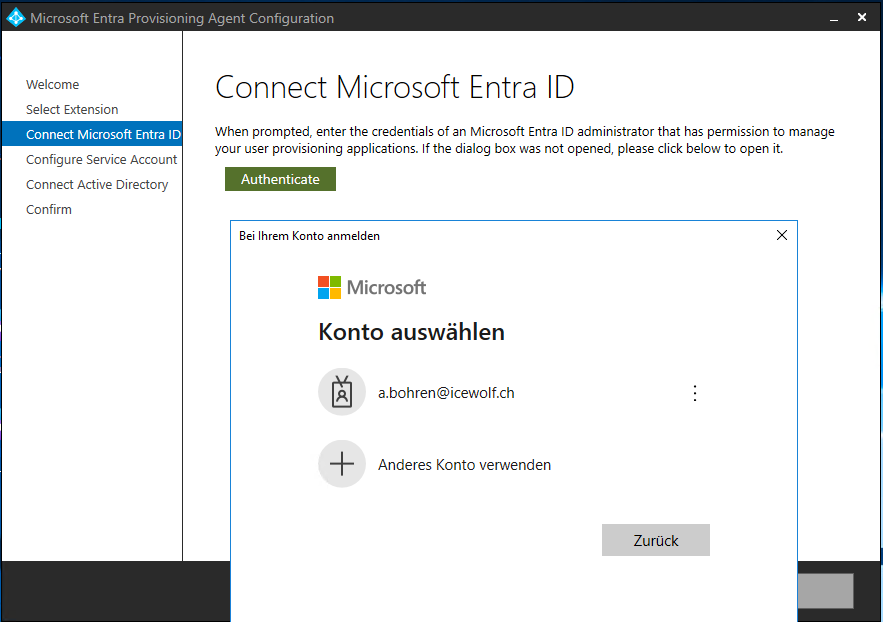
Now you need to Authenticate probably as Global Admin or Hybrid Identity Admin
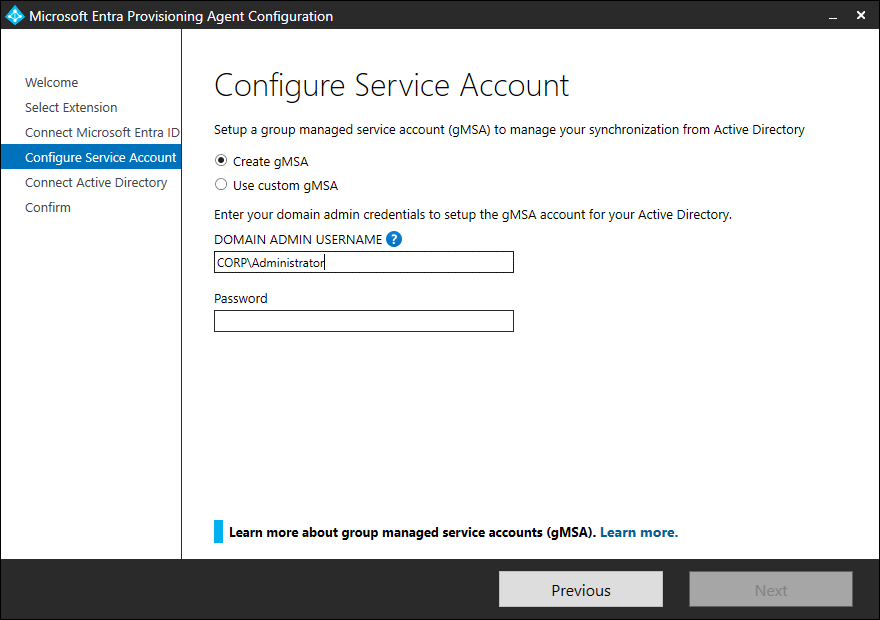
Let’s create a gMSA Account. Had to provide Domain Administrator Credentials to create a gMSA Account
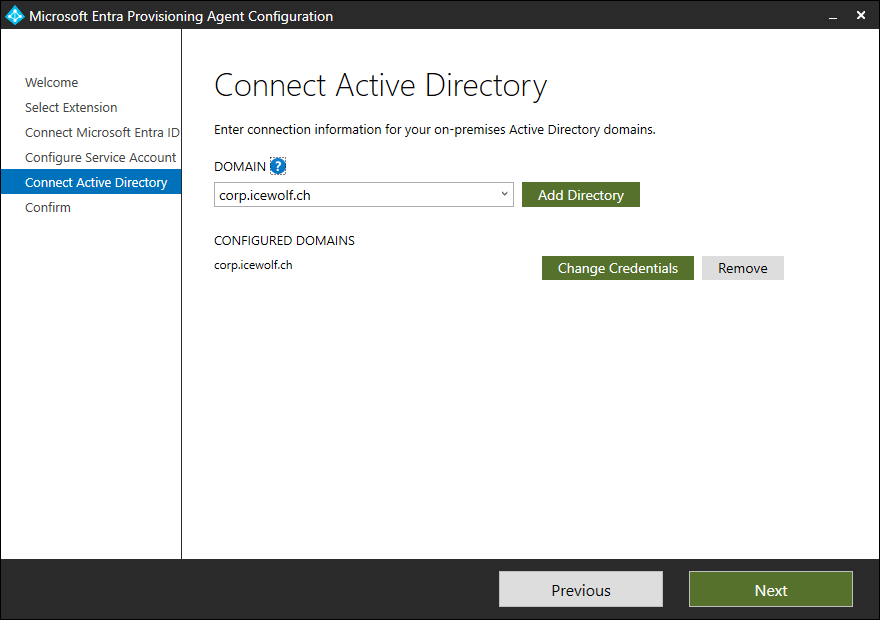
Directory was already populated - so nothing to do here
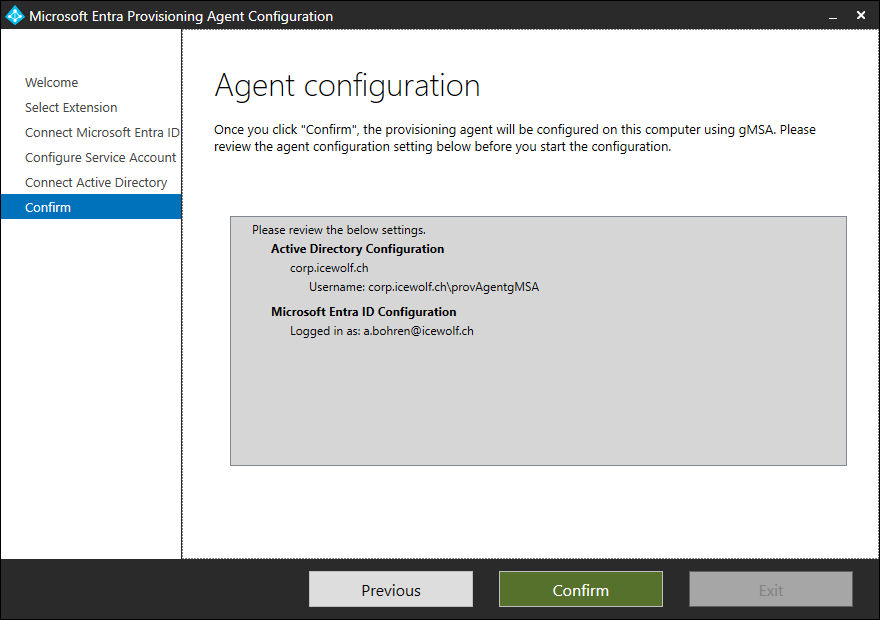
Summary dialog
Now everything will be configured
Agent will be restarted
Configuration is completed
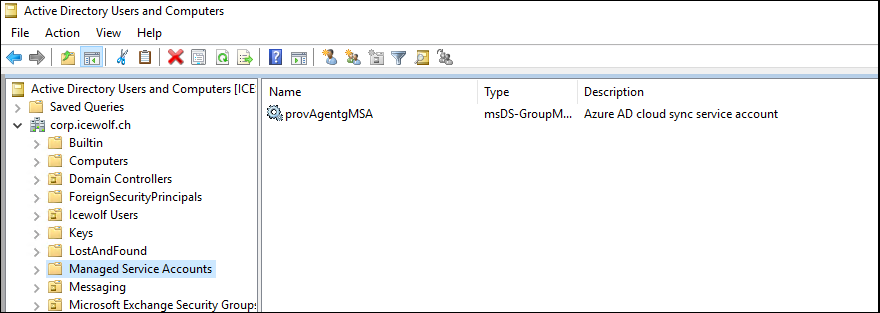
The gMSA Account can be found under “Managed Service Accounts” OU in your Active Directory Domain
Finish Configuration in Entra ID
To finish the Configuration, we need to go back to Entra ID
We can now find an active Agent
In the dropdown we can find our Active Directory Domain
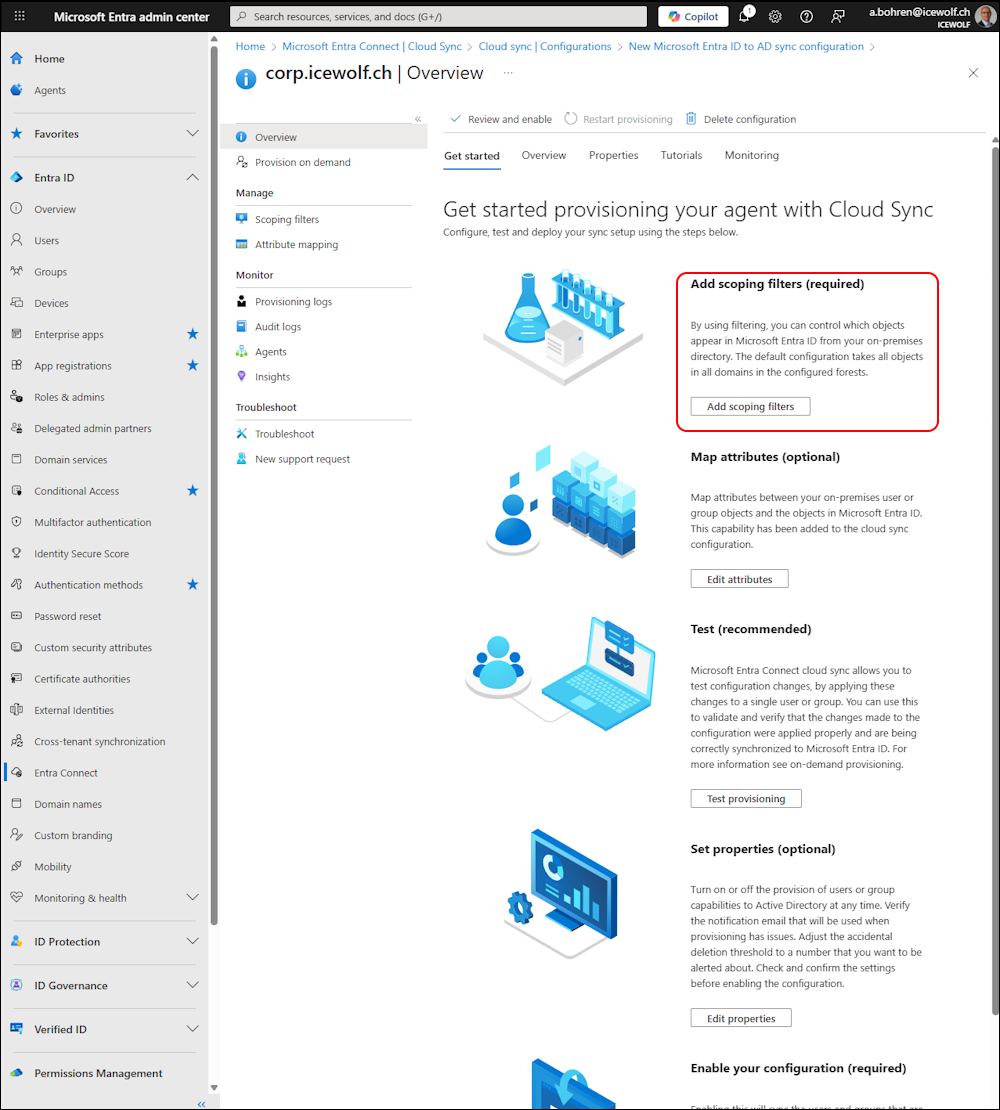
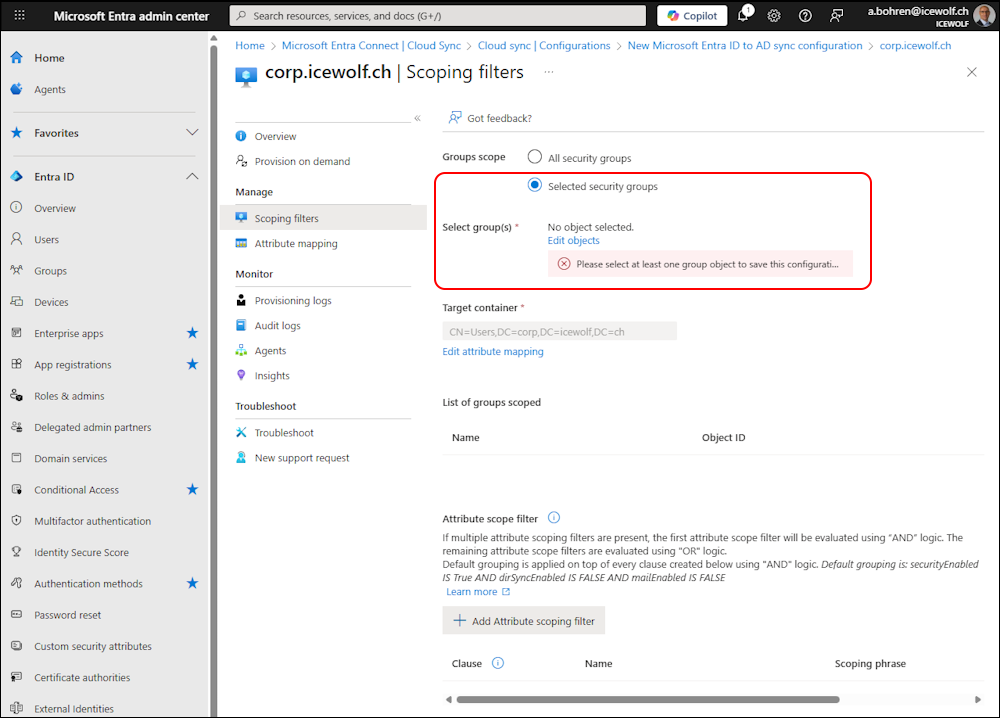
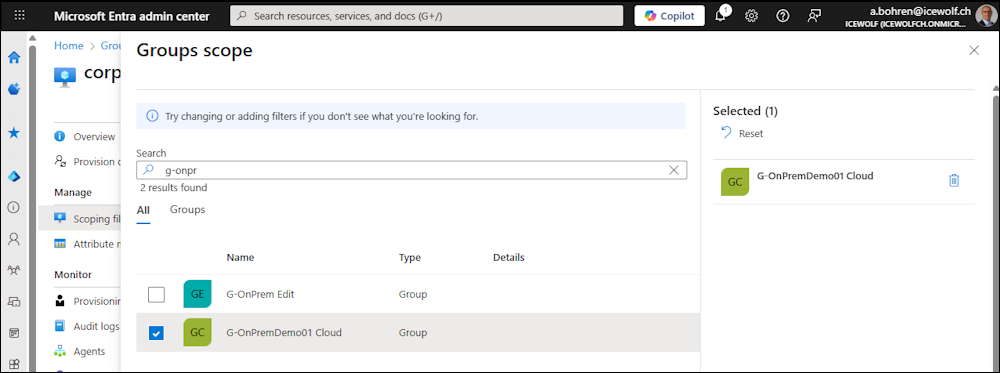
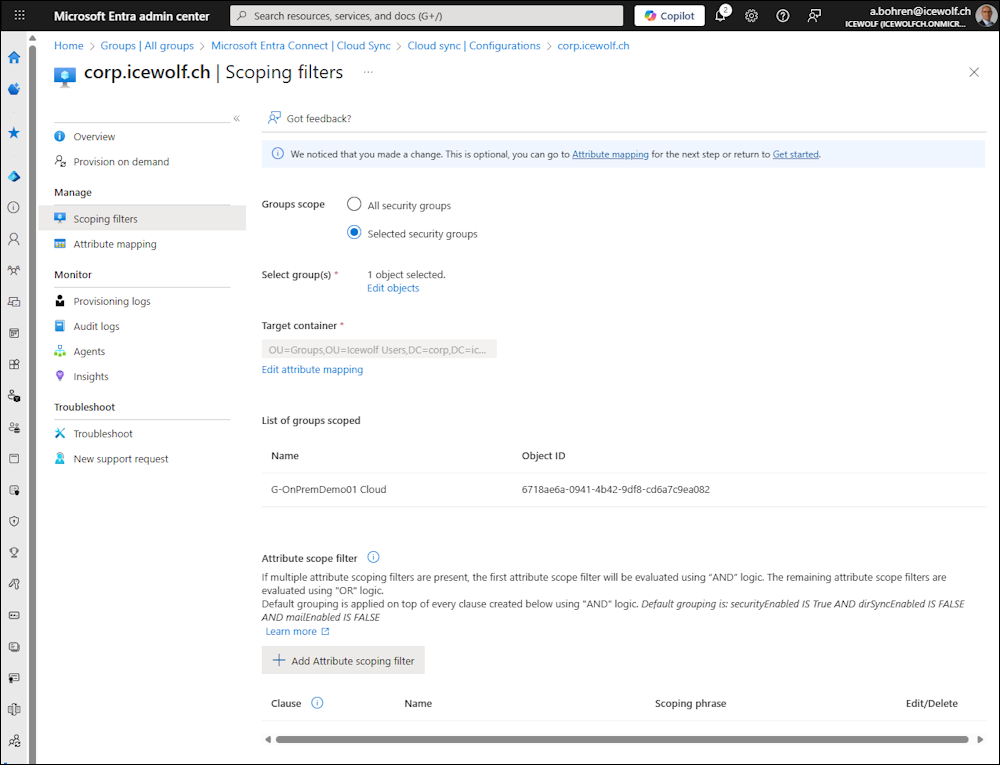
Now we need to add the Scoping Filters - it’s the only one that is required
Scoping Filter
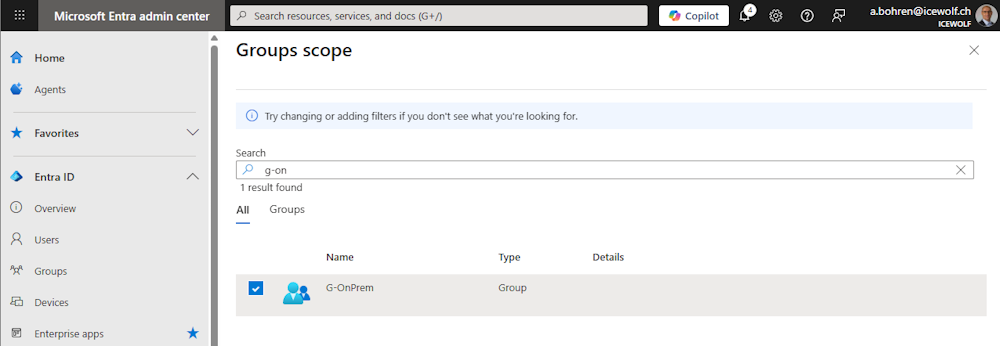
I select “Selected security Groups”
Select one of the from Active Directory synced Groups
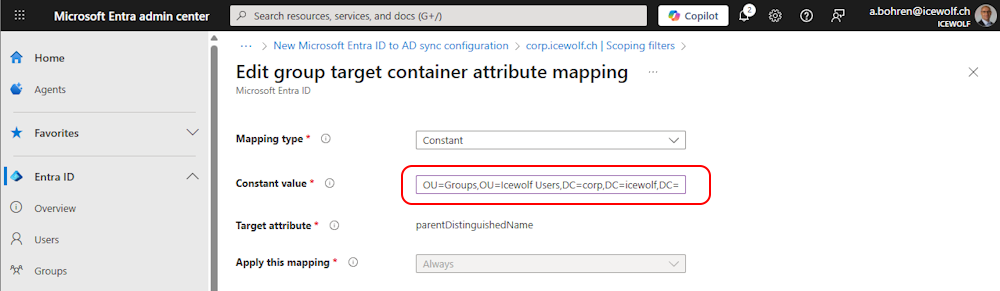
Changed the DN of the OU where the Object should be created
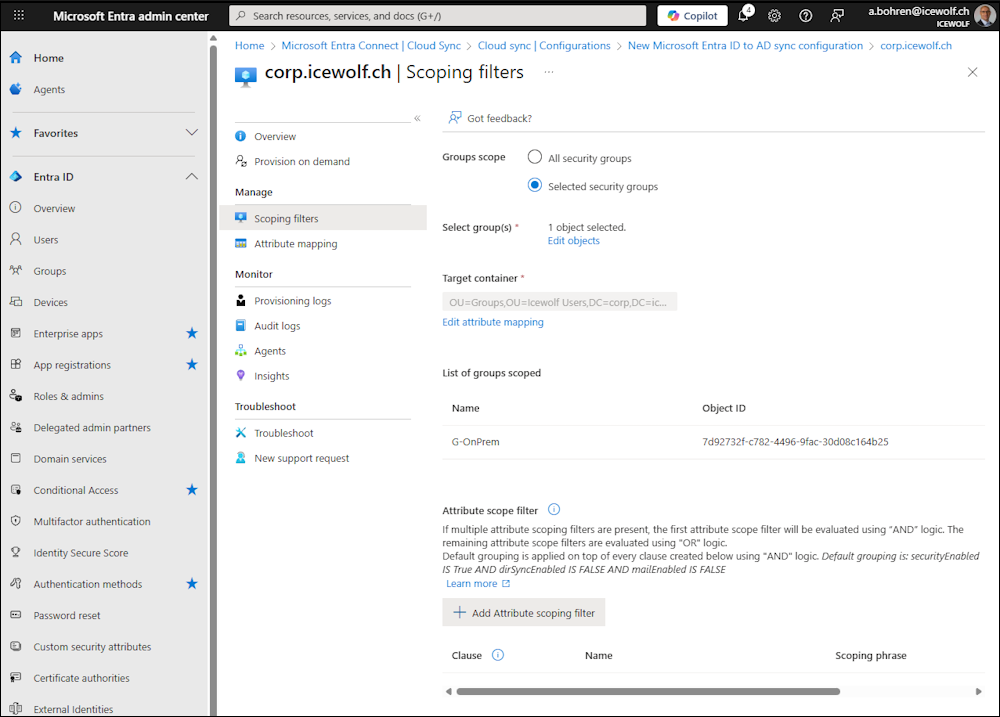
That’s how it looks now
Change Group SOA with Graph Explorer
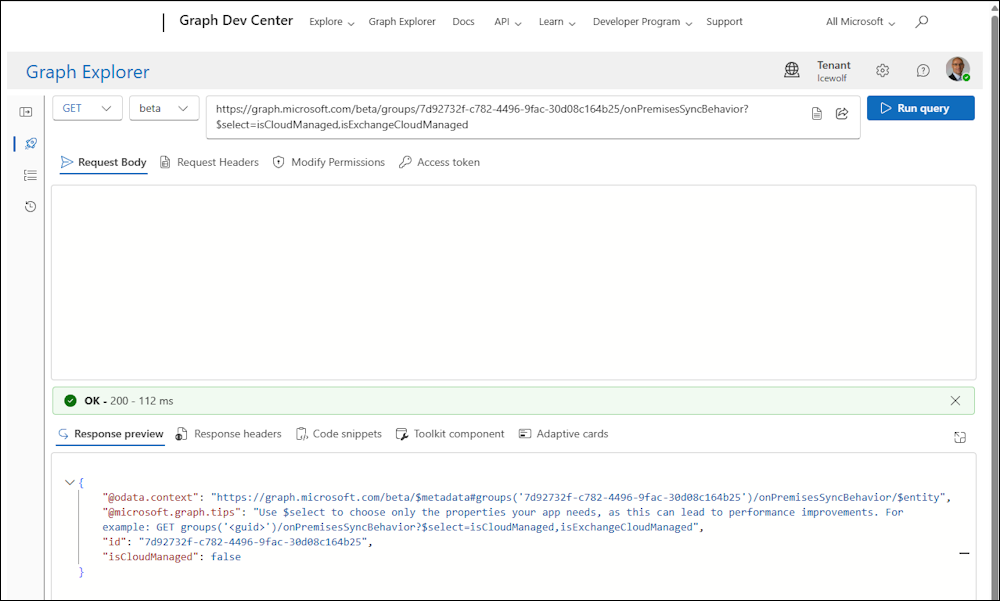
Browse to Graph Explorer and sign in on the top left
GET https://graph.microsoft.com/Beta/groups/7d92732f-c782-4496-9fac-30d08c164b25/onPremisesSyncBehaviour?$select=isCloudManaged,isExchangeCloudManaged
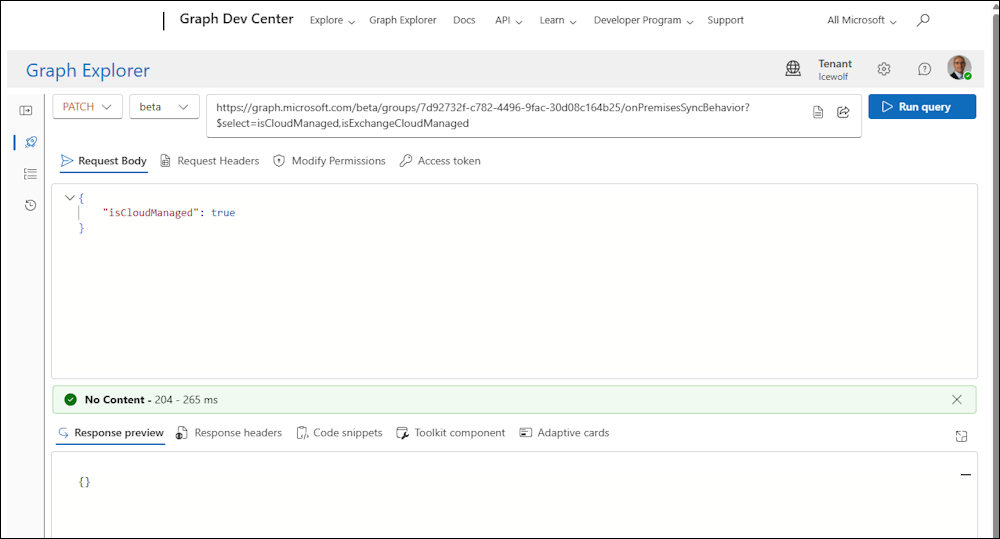
PATCH https://graph.microsoft.com/Beta/groups/7d92732f-c782-4496-9fac-30d08c164b25/onPremisesSyncBehaviour?$select=isCloudManaged,isExchangeCloudManaged
Request Body:
{
"isCloudManaged": true
}
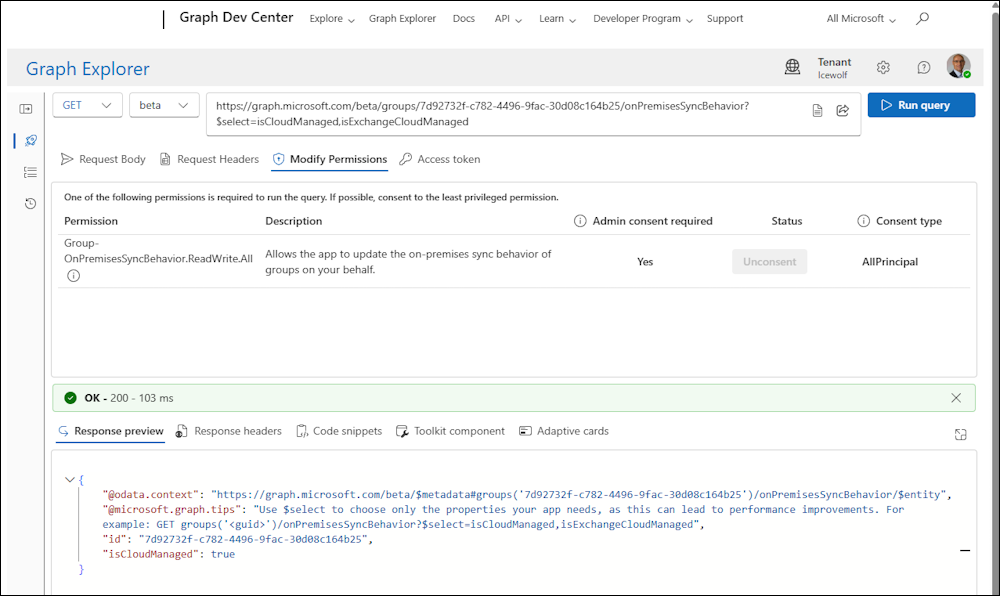
If you check the “Modify Permissions” Tab you see that you will need the “Group-OnPremisesSyncBehavior.ReadWrite.All” Permission for that
Change Group SOA with PowerShell
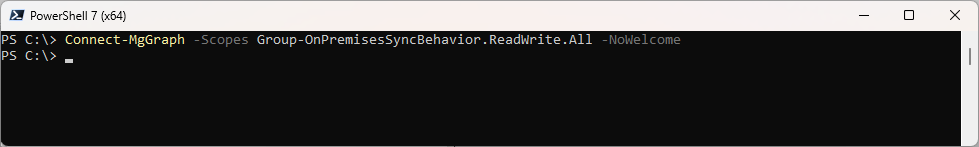
Connect-MgGraph -Scopes Group-OnPremisesSyncBehavior.ReadWrite.All -NoWelcome
You get the Permission Dialog if you never used that Scope before
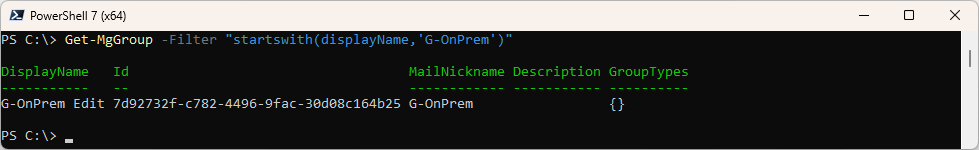
Get the Group to get the ID of the Entra Group
Get-MgGroup -Filter "startswith(displayName,'G-OnPrem')"
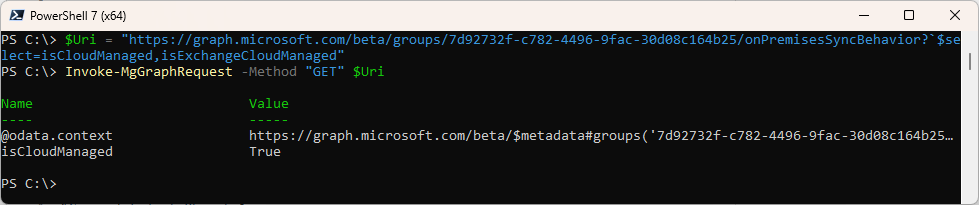
Get the Status of “isCloudManagement”
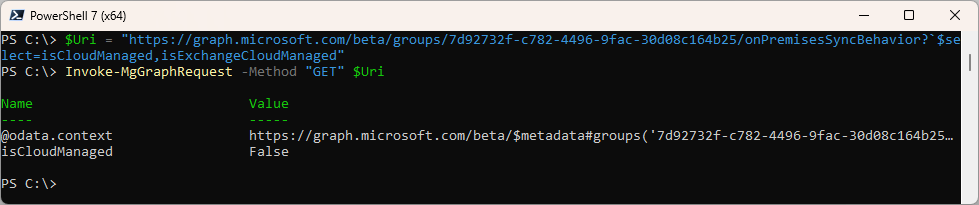
#GET
$Uri = "https://graph.microsoft.com/beta/groups/7d92732f-c782-4496-9fac-30d08c164b25/onPremisesSyncBehavior?`$select=isCloudManaged,isExchangeCloudManaged"
Invoke-MgGraphRequest -Method "GET" $Uri
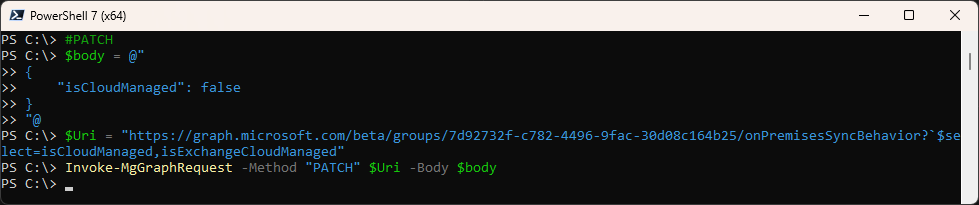
Change the Status of “isCloudManagement”
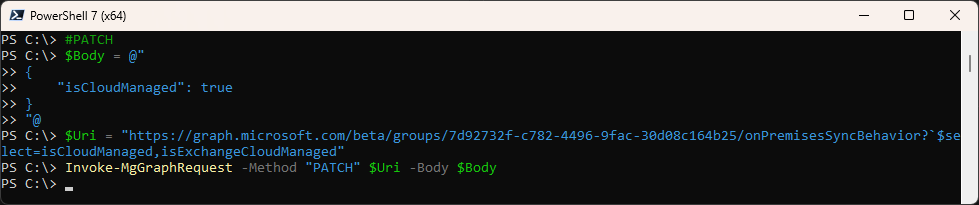
#PATCH
$Body = @"
{
"isCloudManaged": false
}
"@
$Uri = "https://graph.microsoft.com/beta/groups/7d92732f-c782-4496-9fac-30d08c164b25/onPremisesSyncBehavior"
Invoke-MgGraphRequest -Method "PATCH" $Uri -Body $Body
Get the Status of “isCloudManagement”
#GET
$Uri = "https://graph.microsoft.com/beta/groups/7d92732f-c782-4496-9fac-30d08c164b25/onPremisesSyncBehavior?`$select=isCloudManaged,isExchangeCloudManaged"
Invoke-MgGraphRequest -Method "GET" $Uri
How can you identify in Entra Admin Center
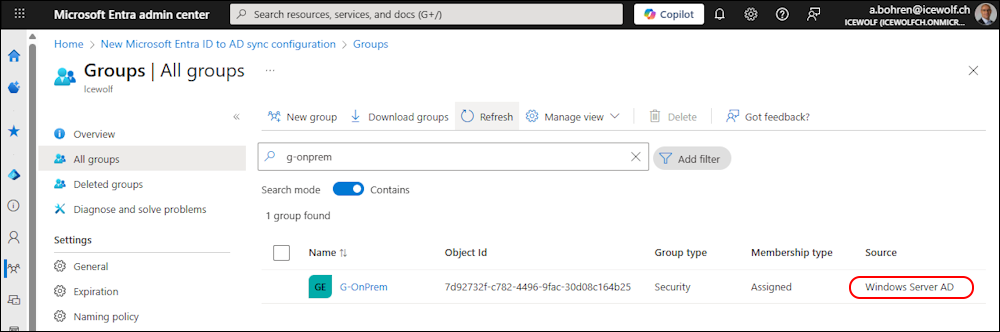
In the Entra Admin Center you can see the Source (of Authority) in the List for groups
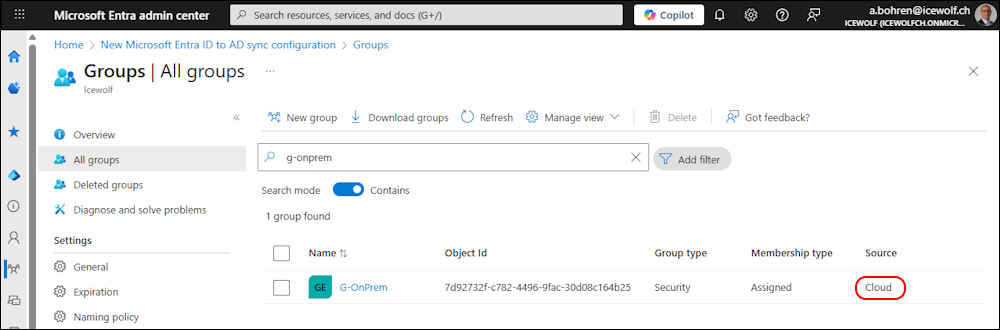
If you change the “IsCloudManaged” Attribute
The Source changes to Cloud
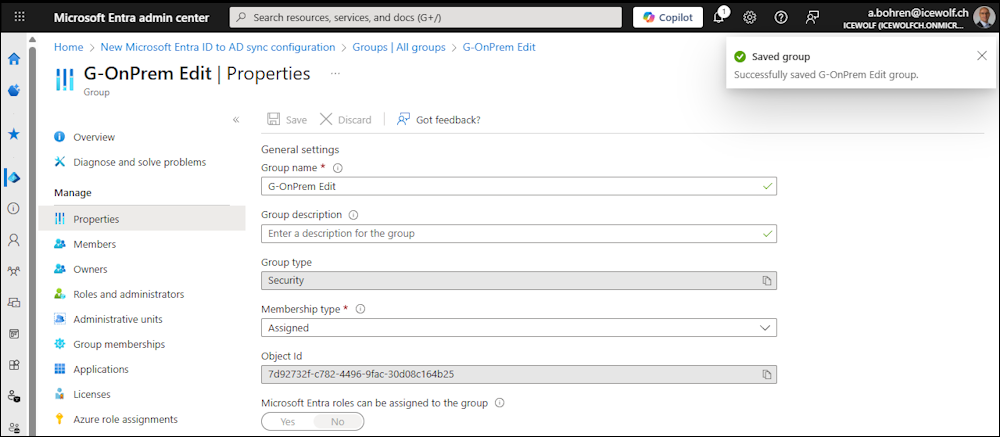
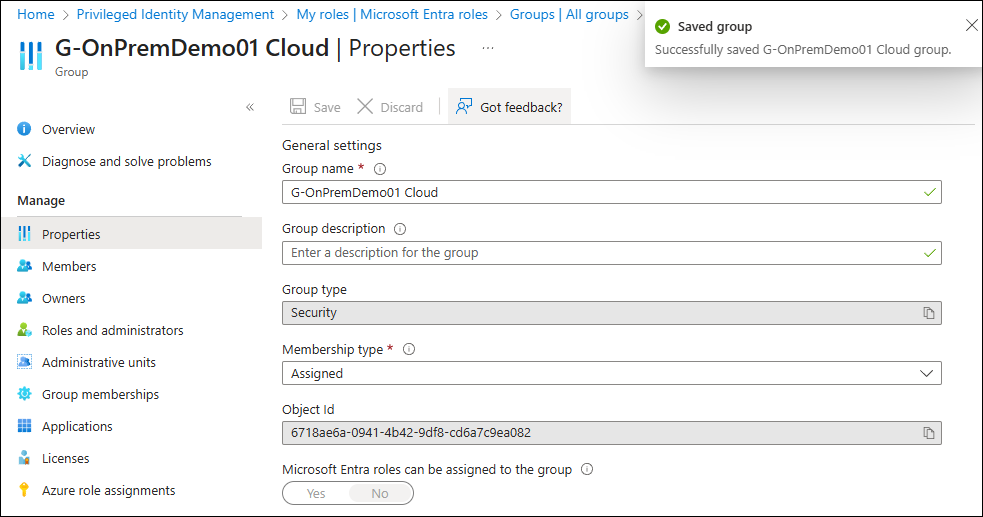
Now you are able to Change the “Group Name” witch changes the “Display Name” in the background.
Let’s do that from Scratch
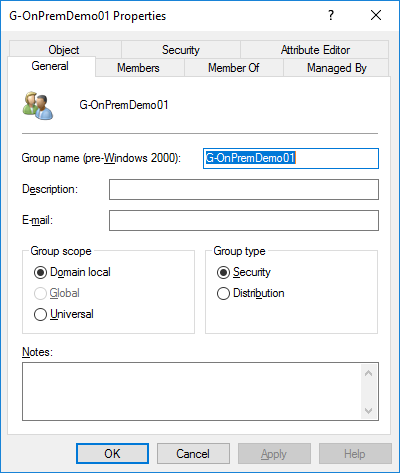
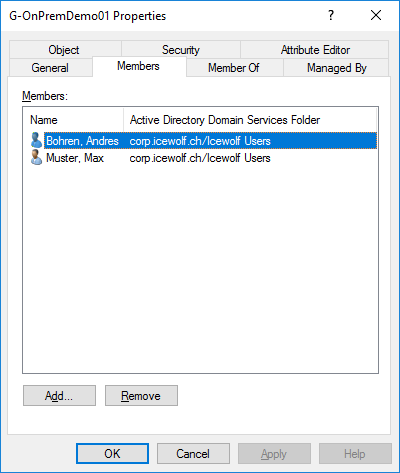
I have a Domain Local Group called “G-OnPremDemo01” with two Members
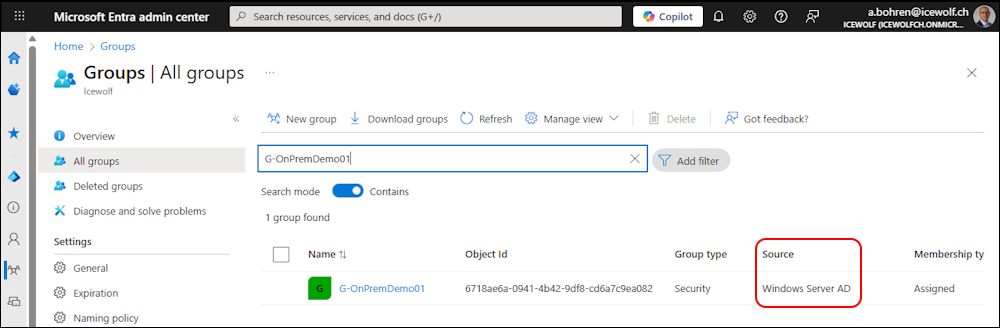
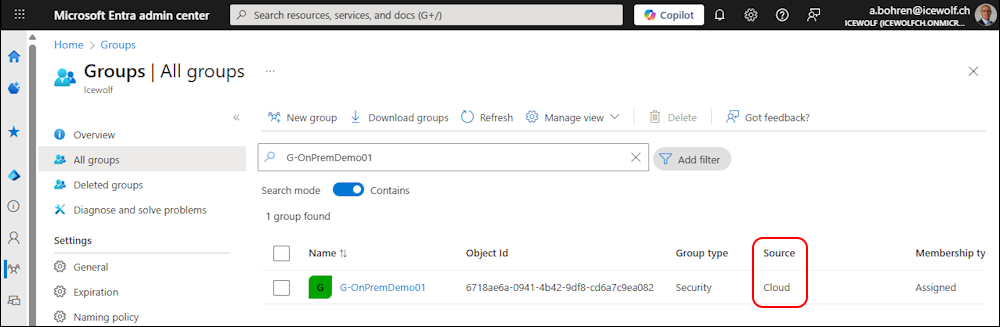
In Entra Admin Center the Group has the Source “Windows Server AD”
Now let’s change the Group to “IsCloudManaged = True”
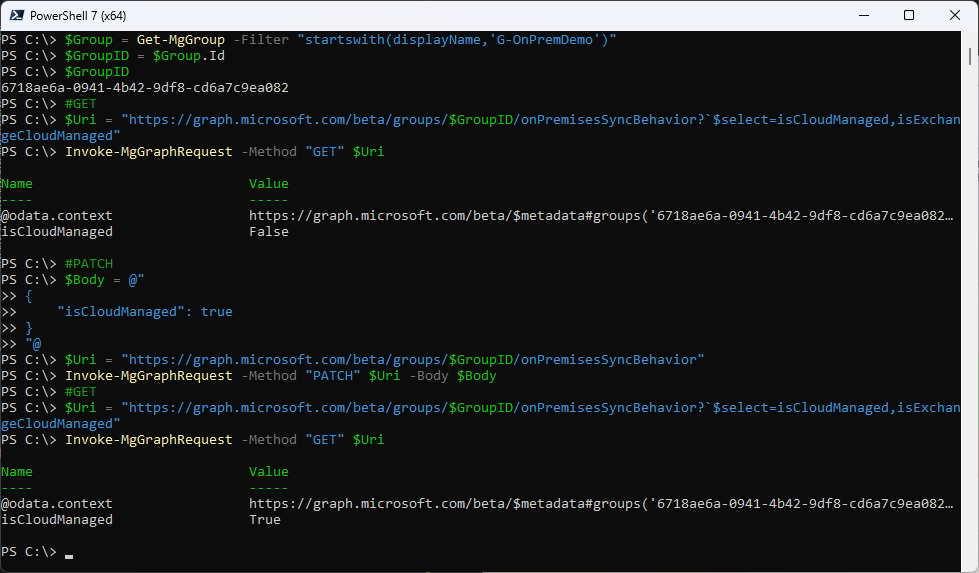
$Group = Get-MgGroup -Filter "startswith(displayName,'G-OnPremDemo')"
$GroupID = $Group.Id
$GroupID
#GET
$Uri = "https://graph.microsoft.com/beta/groups/$GroupID/onPremisesSyncBehavior?`$select=isCloudManaged,isExchangeCloudManaged"
Invoke-MgGraphRequest -Method "GET" $Uri
#PATCH
$Body = @"
{
"isCloudManaged": true
}
"@
$Uri = "https://graph.microsoft.com/beta/groups/$GroupID/onPremisesSyncBehavior"
Invoke-MgGraphRequest -Method "PATCH" $Uri -Body $Body
In Entra Admin Center the Group has now the Source “Cloud”
Entra Connect Sync
On the Entra ID Connect Server let’s start a Delta Sync
Start-ADSyncSyncCycle -PolicyType Delta
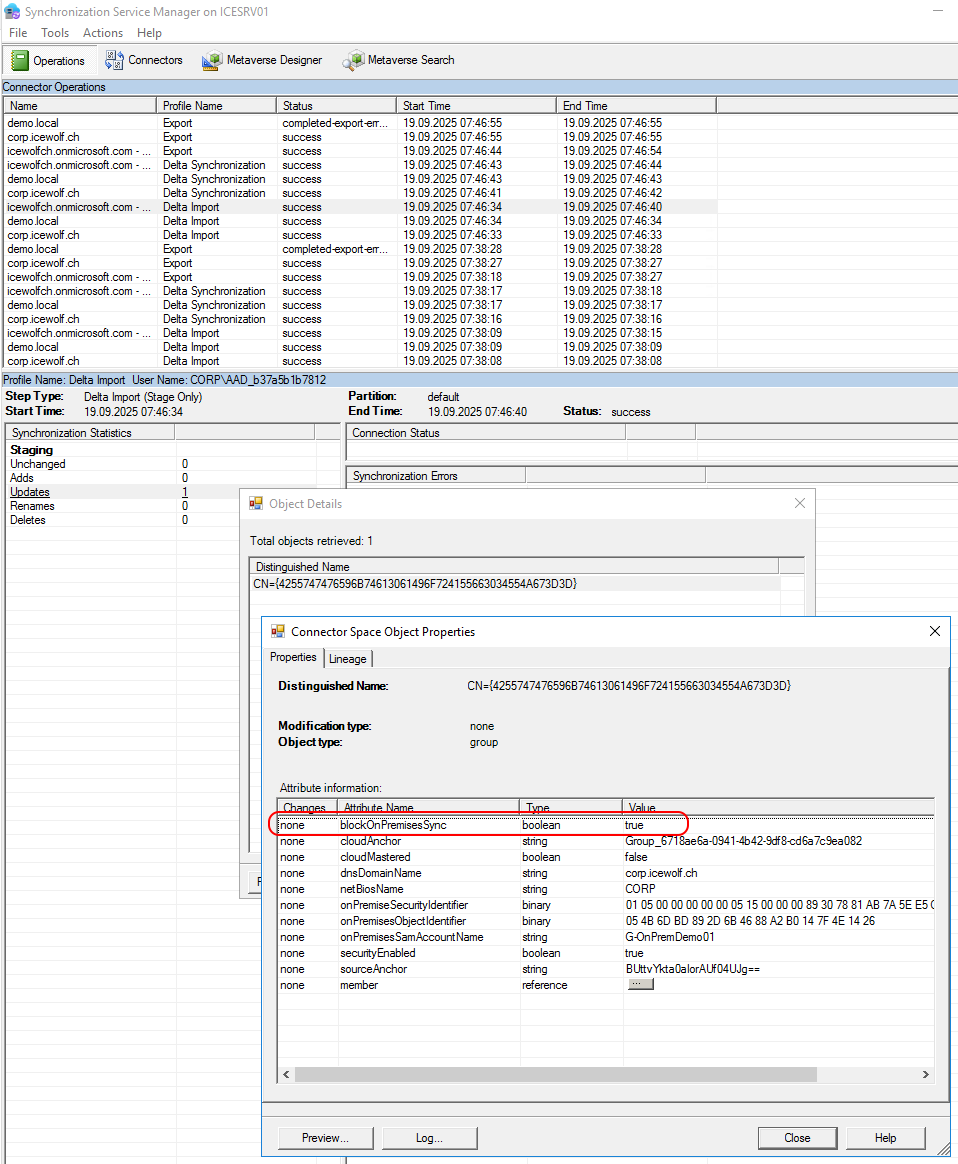
On the “Delta Import” the “blockOInPremisesSync” fo the Group is set to “true”
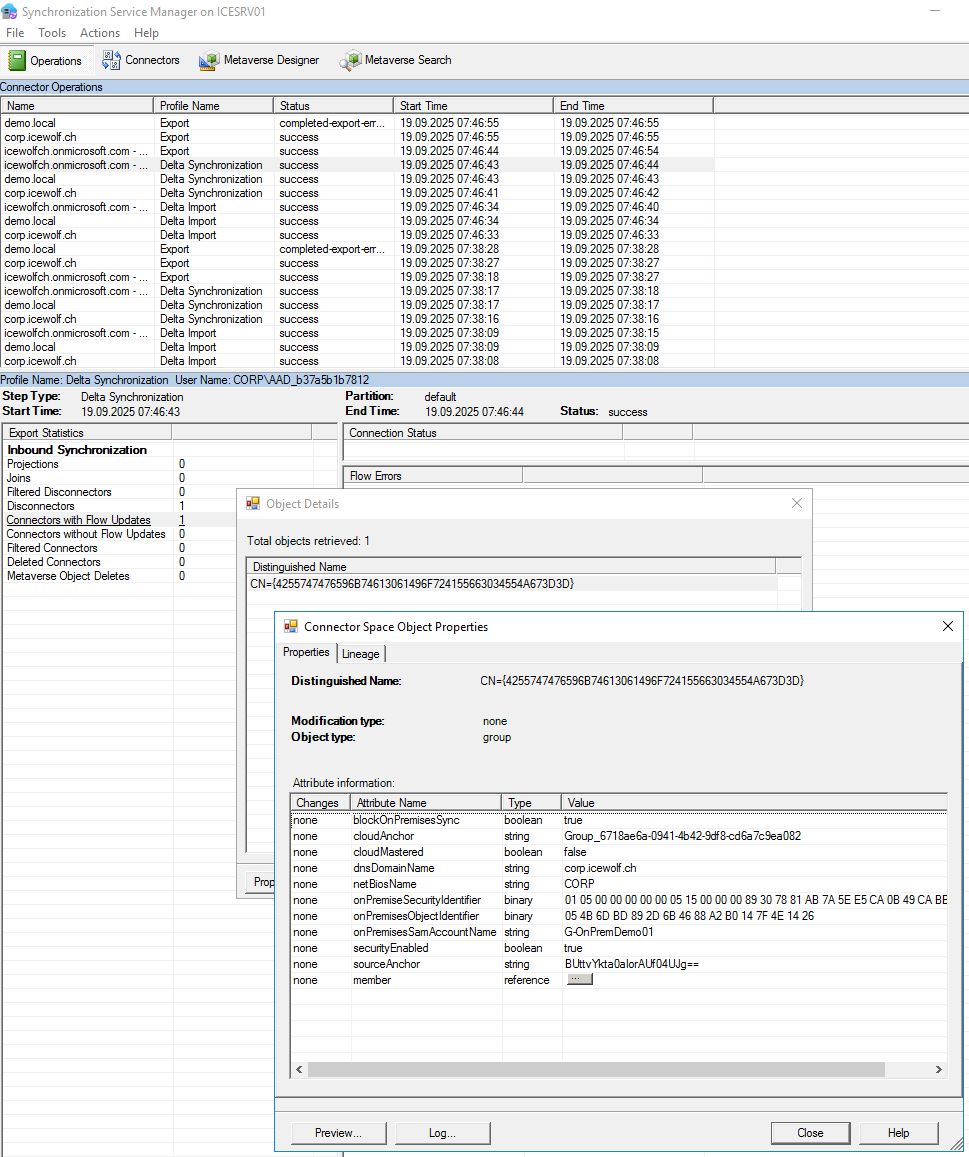
On the “Delta Sync” the “blockOInPremisesSync” fo the Group is set to “true”
I can now edit the Group Name / Display Name
Cloud Sync
In Entra Admin Center under Cloud Sync we change the Groups Scope to the Group “G-OnPremDemo01 Cloud”
Save the Configuration
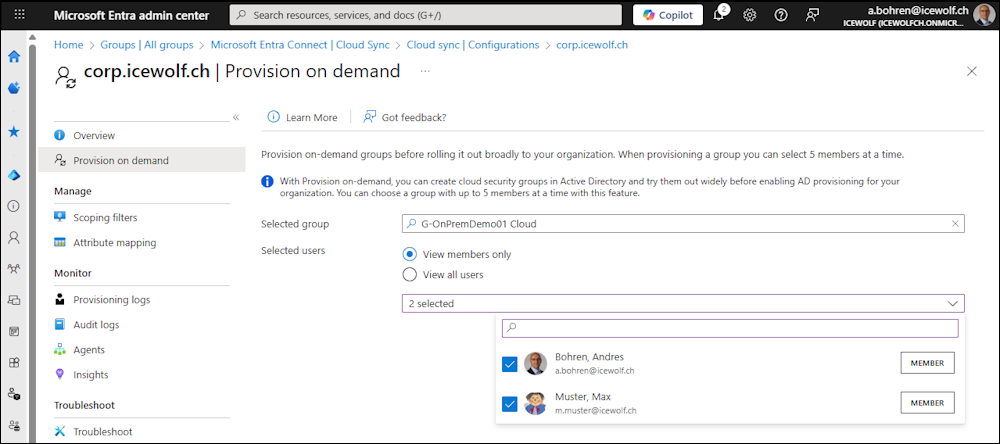
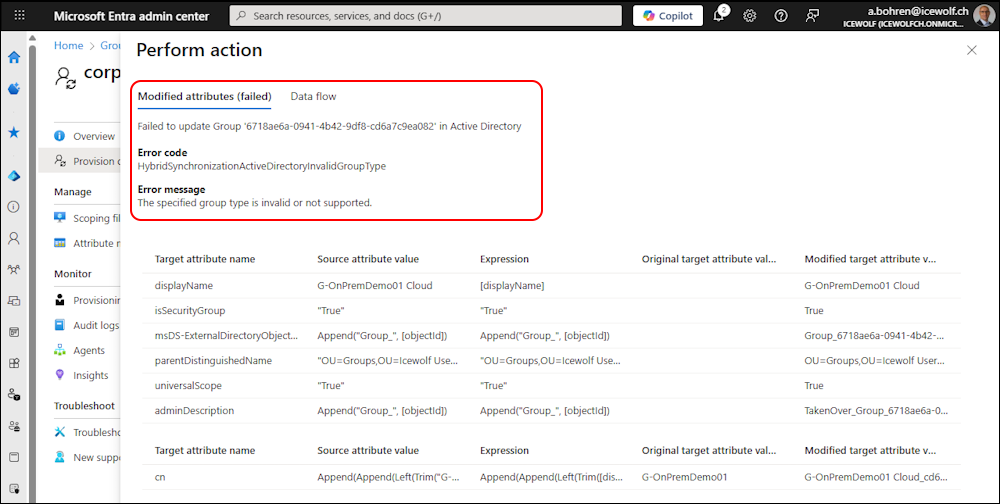
Let’s run a “Provisioning on demand” with the Group “G-OnPremDemo01 Cloud”
That results in an Error. The Group Type is not valid
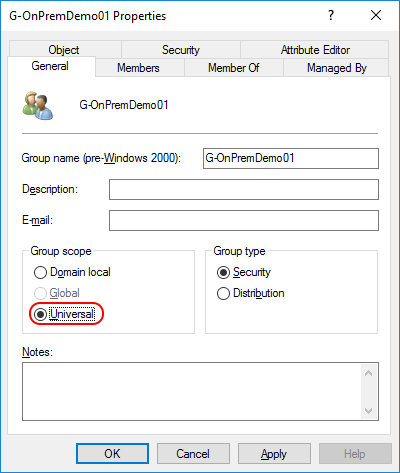
Let’s change the Group Scope in Active Directory to “Universal”
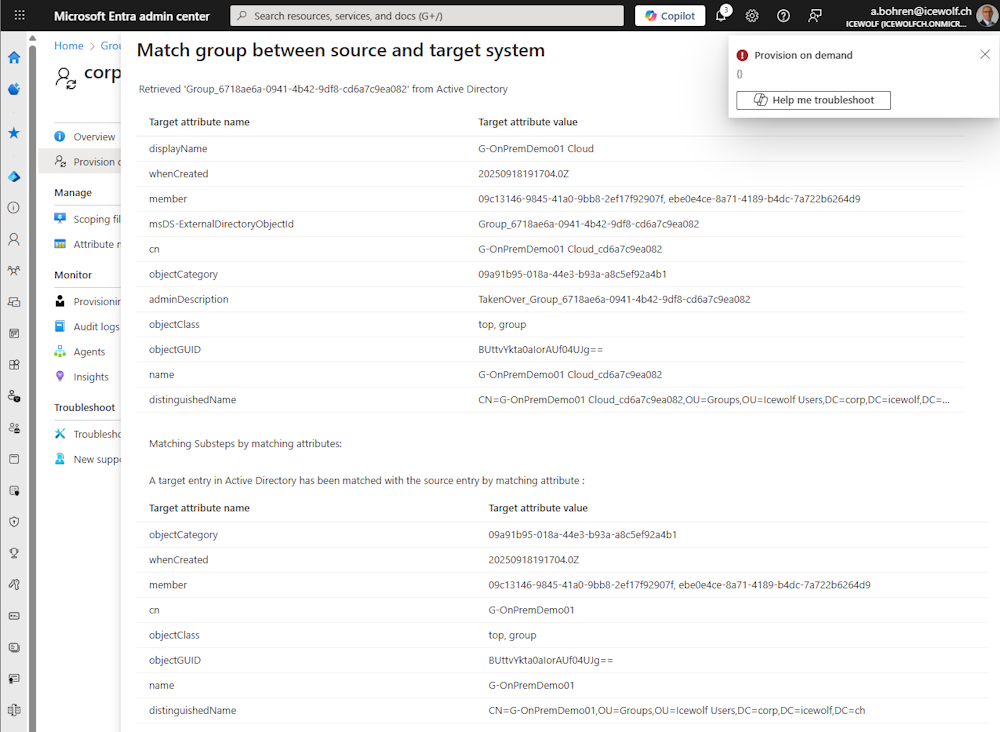
Run the “Provisioning on demand” with the Group “G-OnPremDemo01 Cloud” - this time with sucess.
The red “Message Box” on top right is a bit irritating. As the Output below is “{}” this means - no error happend. At least that’s what i think 😊
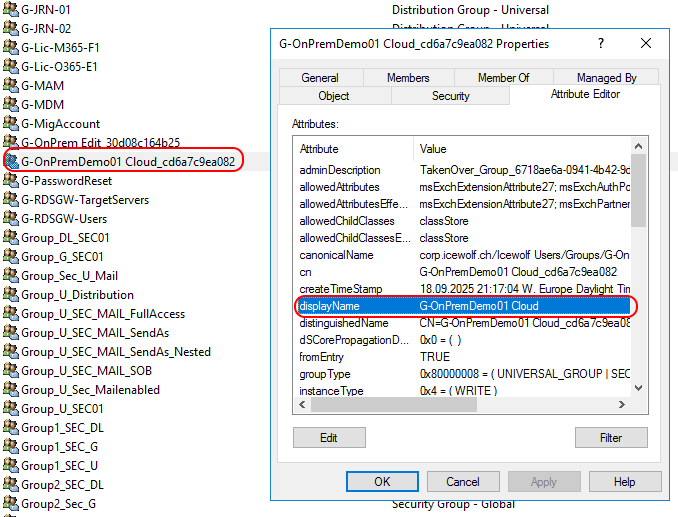
This is the Result on Prem. The Display Name from Entra ID has sucessfully synced back to Active Directory.
Summary
I think this Article gives a good overview on how this Preview Feature actually works. The Limitation of nested Groups and only supporting the Group Scope Universal for Groups Writeback is a bit far from Reality. If you used Groups with AGDLP Principle, you didn’t use the Universal Group Scope. Anyway it’s an interesting Approach and we will see how it develops.
Regards
Andres Bohren