Outlook Error: Something went wrong [4usqa]
![Outlook Error: Something went wrong [4usqa]](https://icewolffile.blob.core.windows.net/$web/thumbnails/ExchangeServer_thumbnail.jpg)
Hi All,
After i solved this Issue, i decided to write this Article to help others solve it too.
Initial situation
My Mailbox is in Exchange Online, but i have Full Access (with Automapping) to a Mailbox OnPrem, that is mapped into my Outlook Profile
About a Month ago, i did get this Error Message in Outlook.
Error
Something went wrong. [4usqa]
Correlation ld: 0f05e4c6-7doa-4e5a-962f-6611 b82fd6e4
Timestamp: 2025-10-22T06:07:14.000Z
DPTI: bbb47eogc0037aadeb4933ca14060b6975dcgc5bg 1 15 If8daOcb
Message: Access denied for the resource.
Tag: 4usqa
Code: 3399614475
I could close the Error Message, but Outlook was not connected to the Mailbox and showed “Need Password”
I could click on the “Need password” and the Mailbox was connected again. After a few Minutes the Error showed again
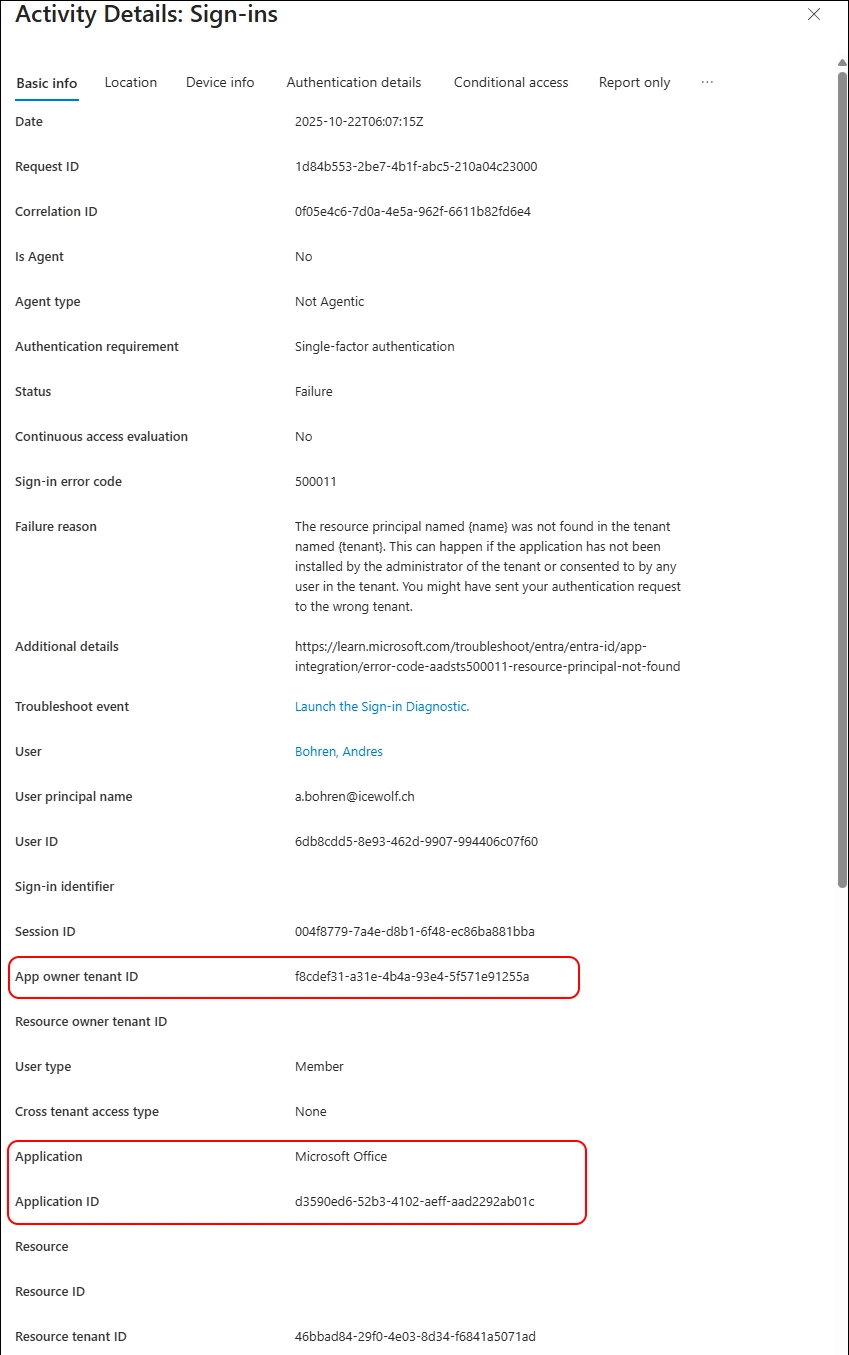
SignIn Logs
I’ve searched for the Correlation Id in the Entra SignIn Logs and found this
Found the CorrelationID in SignIn Logs
App owner tenant ID: f8cdef31-a31e-4b4a-93e4-5f571e91255a
Application: Microsoft Office
Application ID: d3590ed6-52b3-4102-aeff-aad2292ab01c
Results:
App ID seems to be Microsoft Office
d3590ed6-52b3-4102-aeff-aad2292ab01c (Microsoft Office)
Source: https://learn.microsoft.com/de-de/office/dev/add-ins/develop/register-sso-add-in-aad-v2
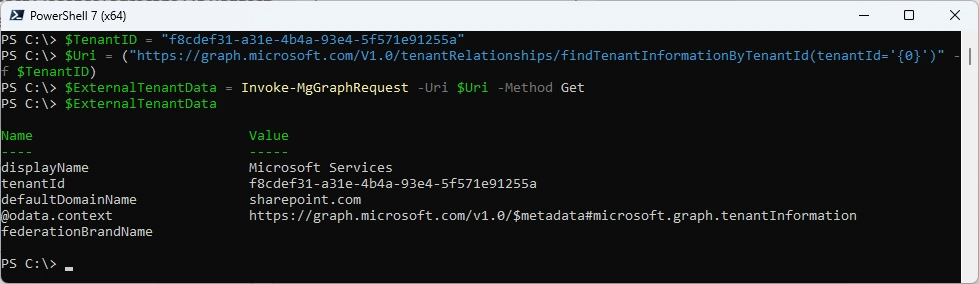
Home Tenant ID seems to be
displayName Microsoft Services
tenantId f8cdef31-a31e-4b4a-93e4-5f571e91255a
defaultDomainName sharepoint.com
I was using this PowerShell Code to get the Name of the TenantID
$TenantID = "f8cdef31-a31e-4b4a-g3e4-5f571eg1255a"
$Uri = ("https://graph.microsoft.com/V1.0/tenantRelationships/findTenantInformationByTenantId(tenantId='{0}')" -f $TenantID)
$ExternalTenantData = Invoke-mgGraphRequest -Uri $Uri -Method "GET"
$ExternalTenantData
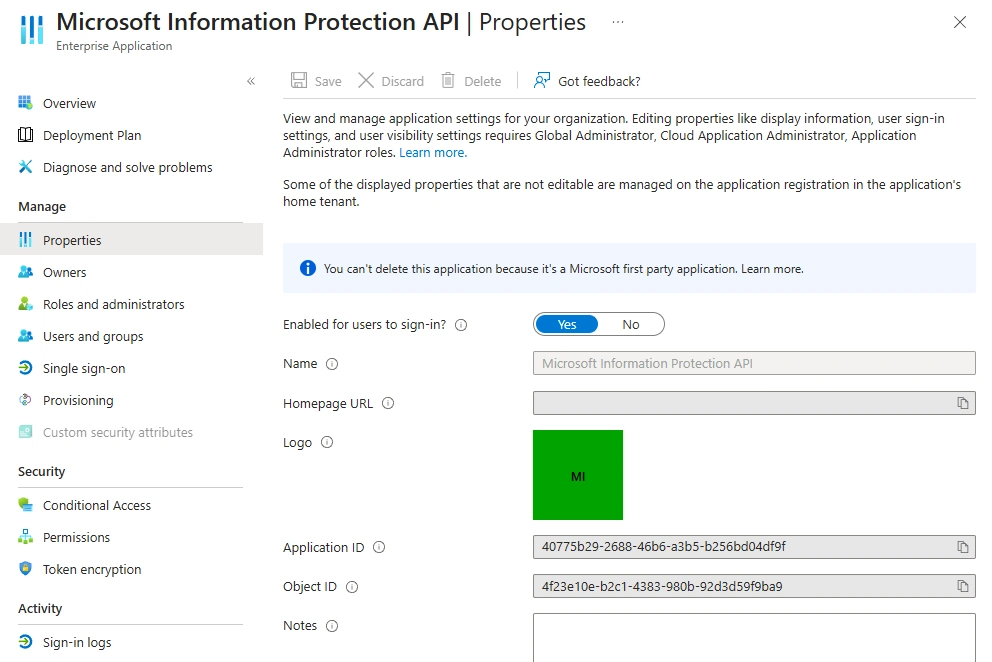
Microsoft Information Protection API
There can be found several Articles like the one below, that suggest to check the Entra Enterprise Application “Microsoft Information Protection API” and set “Enabled for users to sign-in” to “Yes”
In my case the “Enabled for users to sign-in” was already set to “Yes”
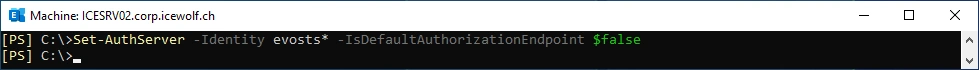
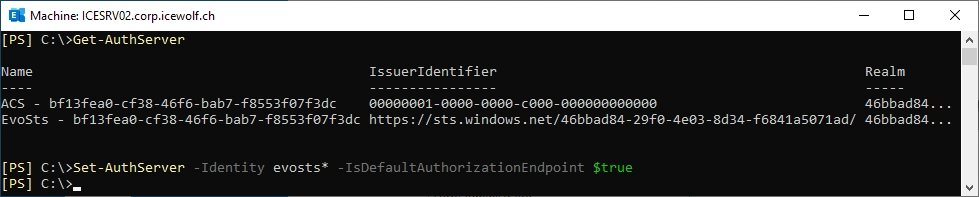
Exchange Auth Server
I played around and figured out, when disabling the “IsDefaultAuthorizationEndpoint” in the EVOSTS* AuthServer the Error Message disappeared
Set-AuthServer -Identity evosts* -IsDefaultAuthorizationEndpoint $false
Exchange Hybrid Wizard
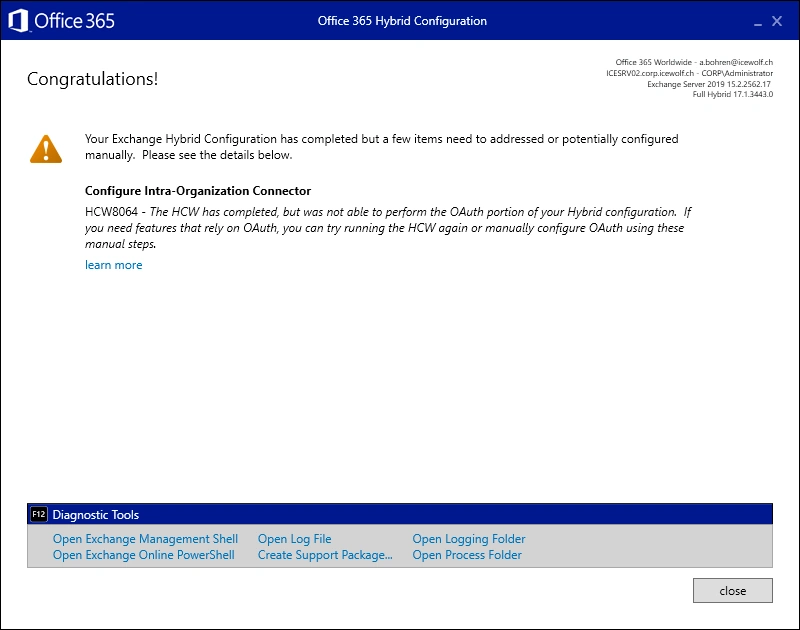
Now i did run the Exchange Hybrid Wizard - it finished with an OAuth Warning
So i ran it again, only with the OAuth Setting
This time it completed successfully - but the Error was still there when enabling IsDefaultAuthorizationEndpoint
Set-AuthServer -Identity evosts* -IsDefaultAuthorizationEndpoint $true
Service Principal Name
This leads me to have a look into the Service Principal Names of the Exchange Online Service Principal
Connect-MgGraph -Scopes Application.Read.All, Application.ReadWrite.All -NoWelcome
Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'" | select -ExpandProperty ServicePrincipalNames
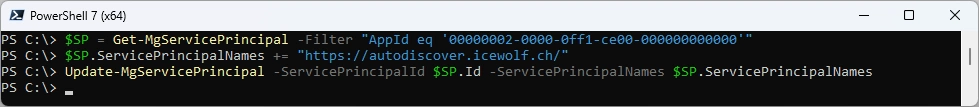
I found that the “Autodiscover” Entry was missing
# ADD ServicePrincipalName
Connect-MgGraph -Scopes Application.Read.All, Application.ReadWrite.All -NoWelcome
$SP = Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'"
$SP.ServicePrincipalNames += "https://autodiscover.icewolf.ch/"
Update-MgServicePrincipal -ServicePrincipalId $SP.Id -ServicePrincipalNames $SP.ServicePrincipalNames
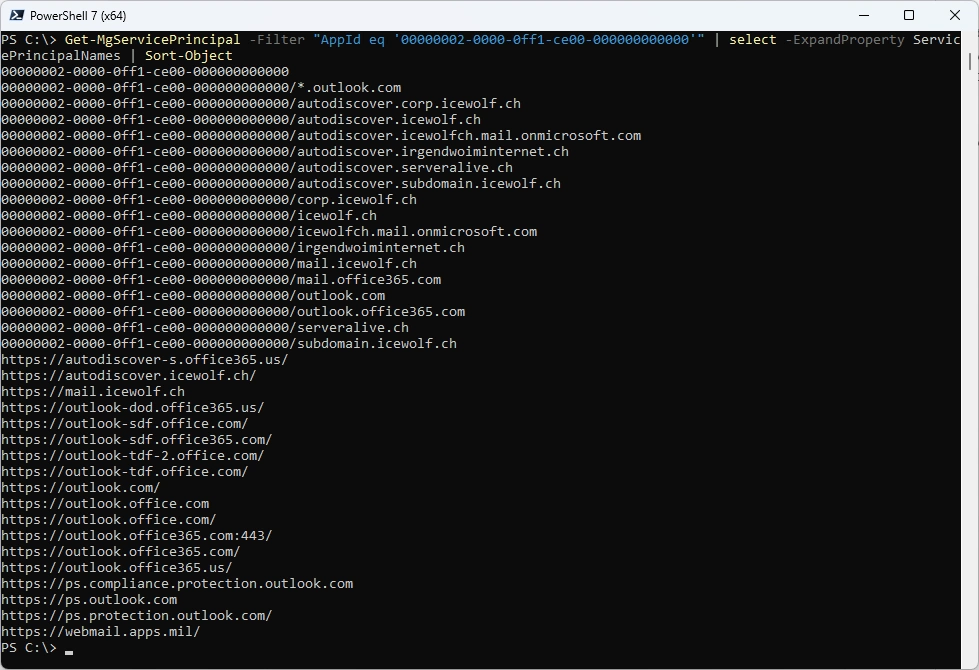
Check the ServicePrincipalNames
Connect-MgGraph -Scopes Application.Read.All, Application.ReadWrite.All -NoWelcome
Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'" | select -ExpandProperty ServicePrincipalNames
Again enabled IsDefaultAuthorizationEndpoint on the evosts* AuthServer - the Issue was solved 😎
Get-AuthServer
Set-AuthServer -Identity evosts* -IsDefaultAuthorizationEndpoint $true
In case you need to remove a Service Principal Name (SPN) here is the code
# REMOVE ServicePrincipalName
Connect-MgGraph -Scopes Application.Read.All, Application.ReadWrite.All -NoWelcome
$SP = Get-MgServicePrincipal -Filter "AppId eq '00000002-0000-0ff1-ce00-000000000000'"
$SPN = $SP.ServicePrincipalNames | where {$_ -ne "https://autodiscover.icewolf.ch/"}
Update-MgServicePrincipal -ServicePrincipalId $SP.Id -ServicePrincipalNames $SPN
Summary
I would say, i have some skills to Troubleshoot an Issue. I was able to find the CorrelationID in the Entra SignIn Logs. But the leap from there to the Solution with the ServicePrincipalNames was more of a lucky coincidence, while poking around in the dark. The fun part is, it worked for several months without any issue - so there must have some Change in M365 - Entra, Exchange Online or even the Outlook Client. Anyway - hope this helps someone else to fix this issue and save the day. If so, you might consider to use the “Buy me a coffee” link on this Website.
Regards
Andres Bohren