Exchange Server 2013/2016/2019 Security Updates May 2022
Hi All,
Yesterday at the Microsoft Patchday, the Exchange Server 2013/2016/2019 Security Updates May 2022 have been released.
Released: May 2022 Exchange Server Security Updates
Security Update For Exchange Server 2016 CU23 (KB5014261)
Microsoft Exchange Server Elevation of Privilege Vulnerability
There is also a new format of the Security Update. The .exe File is a self-extracting, auto-elevating installer (.exe), which works best for manual installations.
New Exchange Server Security Update and Hotfix Packaging
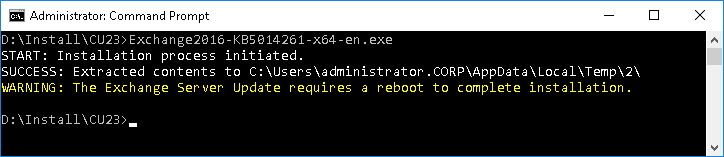
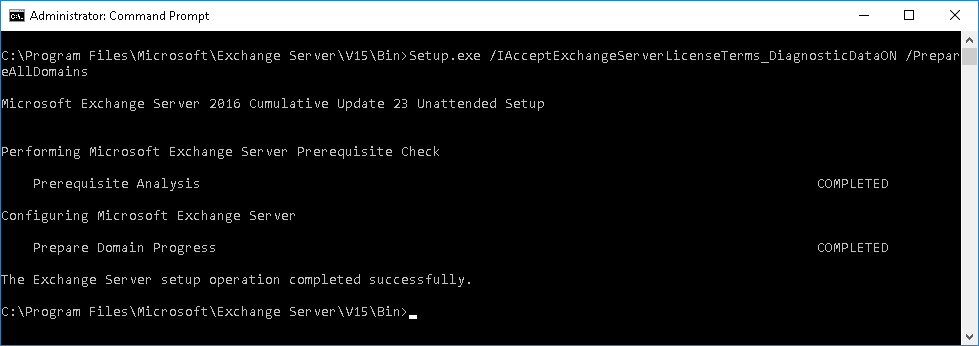
After the Setup is installed on all Servers you have to run "PrepareAllDomains" as an Enterprise Admin.
cd C:\Program Files\Microsoft\Exchange Server\V15\Bin
Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataON /PrepareAllDomains
Regards
Andres Bohren


