Swiss Domain Security Report Q3 2022

Hi All,
In 2015 i wanted to know how many SMTP Servers used STARTTLS, SPF, DKIM, DMARC. I’ve programmed a Webspider with PowerShell and collected about 100'000 Domains. Then made another Script that queried those domains and made SMTP Connect to find out if STARTTLS was in the ELHO Response. The Result was a Report of about 100'000 Domains from the .ch Top Level Domain.
The Results from 2015:
- About 90% of the Domains used MX
- About 75% of the SMTP Servers offered STARTTLS
- About 28% of the Domains with MX had an SPF Record
- About 1% or less DKIM and DMARC was barely present
In 2022 i have extracted the Open Data of Switch DNS Zone Data for the .ch Zone and wrote a Blog Article how i imported it into a SQL Database.
I’ve written a PowerShell Script “Get-Mailprotection” and published it on GitHub and on the PowerShell Gallery.
The Script will extracts Information for a Domain like:
- DNS Zone Signed (DNSSEC)
- CAA (Certification Authority Authorization)
- MX (MailExchanger)
- STARTTLS
- SPF (Sender Policy Framework)
- DKIM (DomainKeys Identified Mail)
- DMARC (Domain-based Message Authentication, Reporting and Conformance)
- DANE (DNS-based Authentication of Named Entities)
- BIMI (Brand Indicators for Message Identification)
- MTA-STS (SMTP MTA Strict Transport Security)
- MTA-STS Web (https://mta-sts.domain.tld/.well-known/mta-sts.txt)
- TLS-RPT (TLS Reporting)
Instead of only the sample of 100'000 Domains from 2015 i have then scanned all the 2.4 Mio .ch Domains. That took me about 2 Months (September/October 2022).
Note
I am a private Person and this is just a Hobby Project. Due some other priorities in my Life, it took longer than anticipated to publish this Report. But i still believe it can be useful as an Overview of the Mail- and Domain Security in Switzerland.
Here are the Results:
Overview
My main Focus on this Project was related to Mailsecurity - but there are other aspects i did NOT consider like:
- HTTP/HTTPS of Website
- HTTPS TLS Version used
- HTTP Strict Transport Security Cheat Sheet (HSTS)
- HTTP Security Header
Regarding Mailsecurity there is still a huge opportunity to improve and make the Internet more Secure.
.ch Domains
- 2'393'997 .ch Domains (August 2022) https://www.nic.ch/statistics/domains/
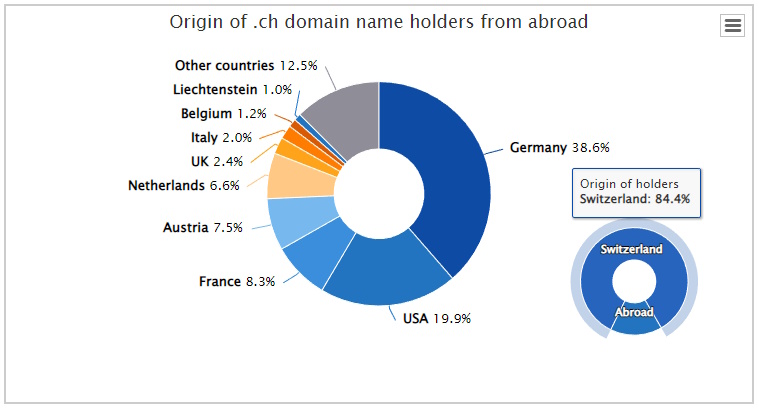
- 84.4% of the Domain Holders are located in Switzerland https://www.nic.ch/statistics/countries/
Top .ch Domain Holders outside Switzerland
- 38.6% Germany
- 19.9% USA
- 8.3% France
- 7.5 % Austria
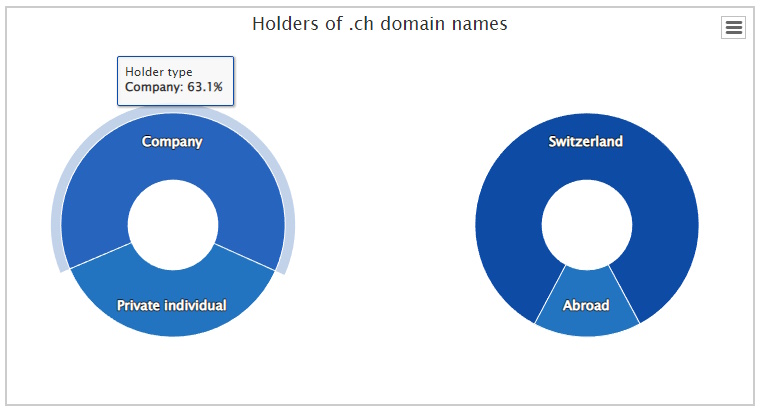
.ch Domain Holders (Company / private Individual)
- 63.1% (about 1'510'612) of the Domains are owned by a Company
- 36.9% (about 883'384) of the Domains are owned by a private Individual
- An overview regarding Security the top 1'000 .ch Domains is maintained by Switch https://www.hardenize.com/dashboards/ch-resilience/
DNS Zones
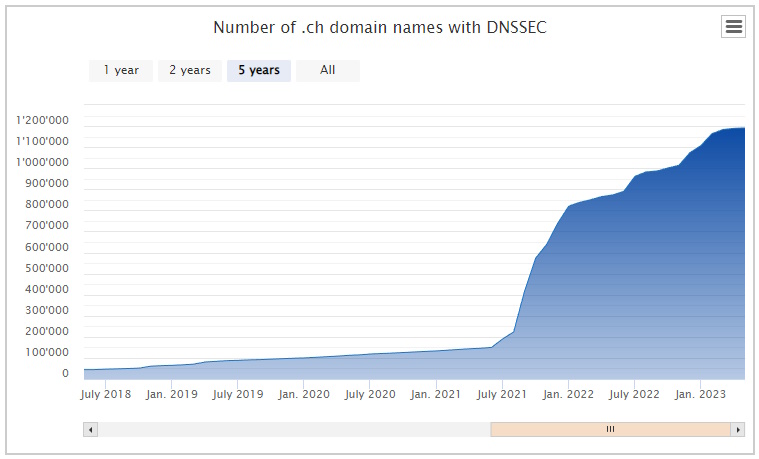
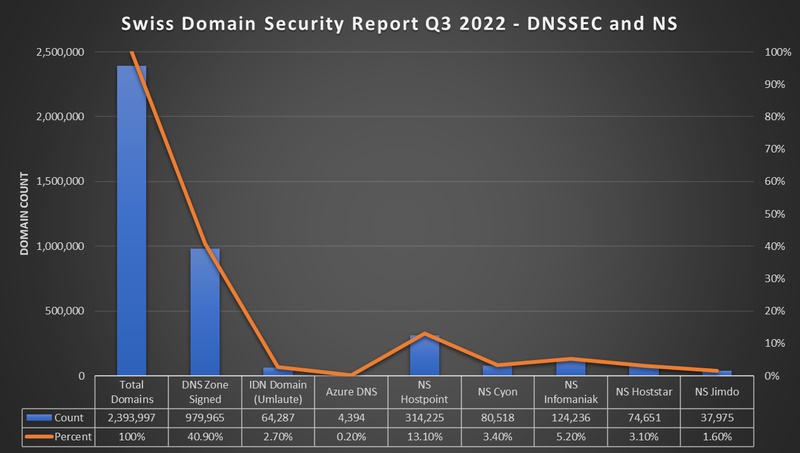
- 40% (979'965) of the DNS Zone Signed (DNSSEC) https://www.nic.ch/statistics/dnssec/
- with a huge bump since summer 2021
- 13.4% (314'225) of the NS Records point to Hostpoint
- 5.2% (124'236) of the NS Records point to Infomaniak
- 3.4% (80'218) of the NS Records point to Cyon
- 3.1% (74'651) of the NS Records point to Hoststar
- 1.6% (74'651) of the NS Records point to Jimdo
- 0.2% (4'394) of the NS Records point to Azure DNS
- 2.7% (4'394) are internationalized domain name (IDN) using Punycode
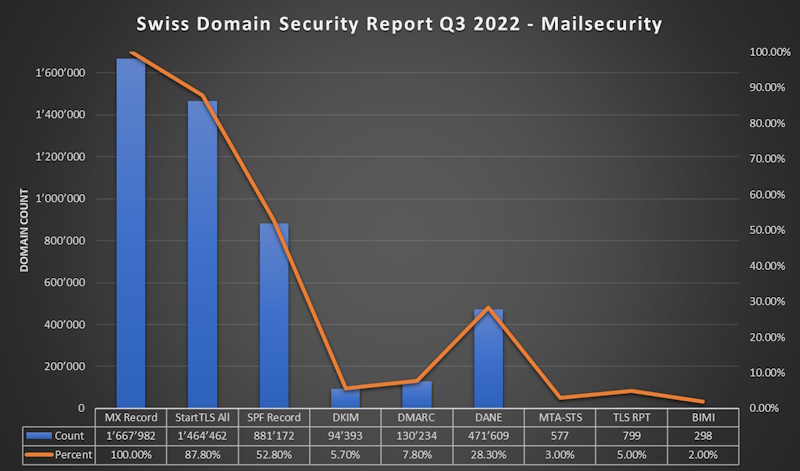
MX (Mail Exchange)
- MX Record defined here rfc1035
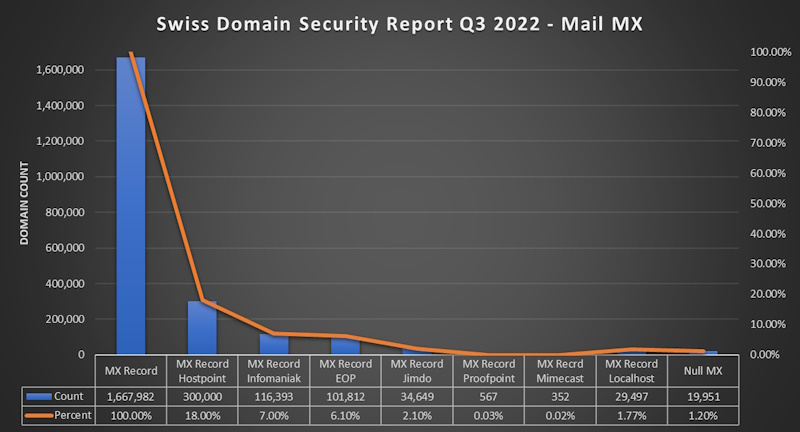
- 70% (1'700'000)of all Domains have a MX Record
- 18% (300'000) of Domains with MX point to Hostpoint
- 7% (116'393) of Domains with MX point to Infomaniak
- 6.1% (101'812) of Domains with MX point to Exchange Online
- 2.1% (34'649) of Domains with MX point to Jimdo
- 0.03% (567) of Domains with MX point to Proofpoint
- 0.02% (352) of Domains with MX point to Mimecast
- 1.20% (19'951) of Domains use “Null MX” rfc7505
- 1.77% (29'497) of Domains with MX point localhost 😂 - WTF?
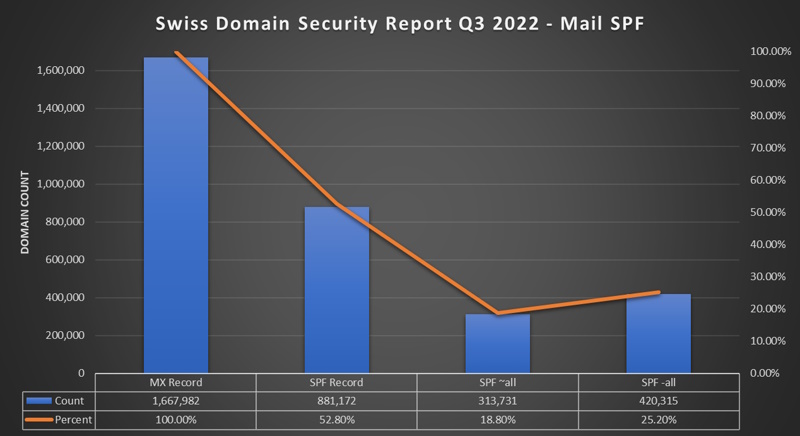
SPF (Sender Policy Framework)
- SPF exists since 2003 with Updates 2006 and 2014 rfc7208
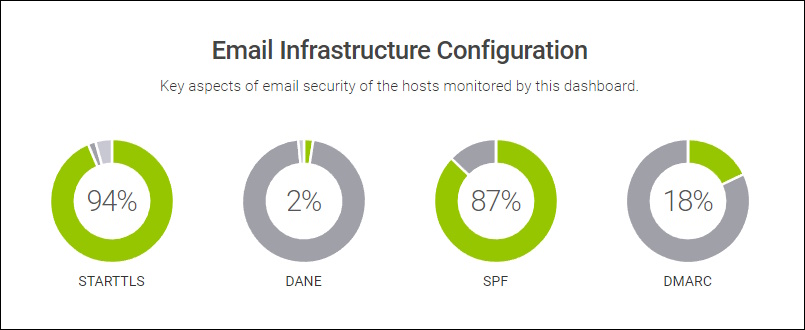
- 52.8% of Domains with MX have a SPF Record
- 25.2% of Domains with MX have “SPF -all” (about half of the SPF Records)
- 18.8% of Domains with MX have “SPF ~all”
- 1.2% (19'951) of Domains with MX have a NULL MX (most of them with “v=spf1 -all”)
- did found a few Domains that have multiple SPF Records (not supported)
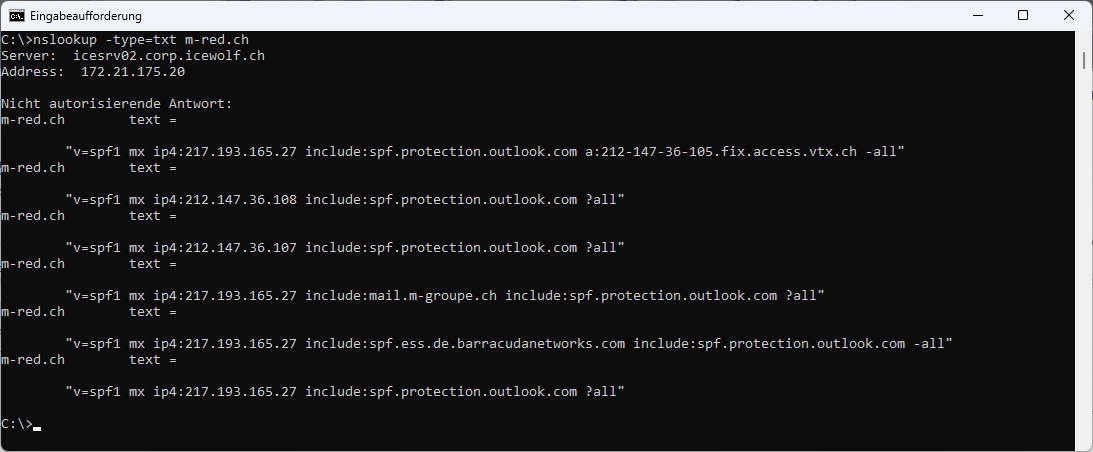
Bad Example: nslookup -type=txt m-red.ch

DKIM (DomainKeys Identified Mail)
It is defined in rfc6376 from 2011 with updates in rfc8301 and rfc8463.
Note: due the fact that the Selector can be anything it’s hard to determine DKIM Records
- 5.7% (94,393) of Domains with MX have a high chance of having a DKIM Record
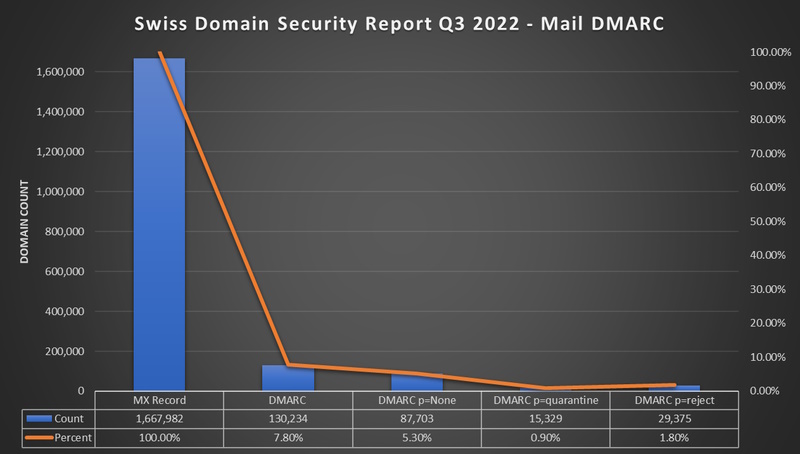
DMARC (Domain-based Message Authentication, Reporting and Conformance)
- DMARC Exists since 2015 defined in rfc7489
- 7.8% (130'234) of Domains with MX have a DMARC Record
- 5.3% (87'703) p=none
- 0.9% (15'329) p=quarantine
- 1.8% (29'375) p=reject
- 2.50% (42'134) have a rua defined
Top RUA Domains
- tophost.ch 10'733
- amenic.ch 3'876
- swisscenter.com 2'683
- emaildefense.proofpoint.com 1'136
- mailinblue.com 1134
- rep.dmarcanalyzer.com 596
- rua.dmp.cisco.com 583
- dmarc.postmarkapp.com 549
- vali.email 333
- ag.eu.dmarcadvisor.com 279
- itsrv.tech 242
- yourdomain.com 238
- mxtoolbox.dmarc-report.com 224
- ag.eu.dmarcian.com 206
- rua.agari.com 199
- kesako.ne 190
- mydo.space 164
- vali.email 156
- akomodix.ch 143
- talus.ch 128
- gmail.com 128
- immerda.ch 116
- megatraffic.de 114
- dmarc.barracudanetworks.com 103
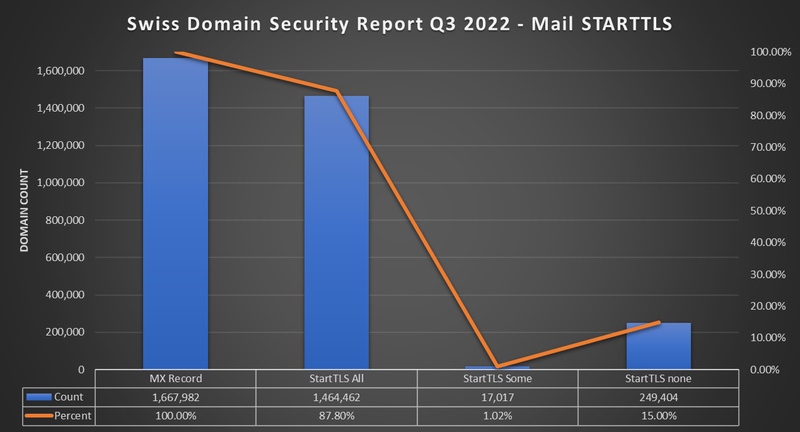
StartTLS
- 87.8% (1'464'462) of Domains with MX have STARTTLS support on all Mailservers
- 1% (17'017) of the Domains with MX have STARTTLS support on some Mailservers
TLS-RPT (SMTP TLS Reporting)
- Exists since 2018 rfc8461
- 0.05% (799) of the Domains with MX support TLS-RPT
MTA-STS (SMTP MTA Strict Transport Security)
- Exists since 2018 rfc8461
- 0.03% (577) of the Domains with MX support MTA-STS
CAA (Certification Authority Authorization)
DANE (DNS-based Authentication of Named Entities)
- Exists since 2015 rfc8461
- Requires DNSSEC
- I’ve explained how DANE works in one of my Blog Articles
- 28.3% (471'609) of the Domains with MX have a DANE Record
- 25.69% (428'546) use “3 1 1” (Hash of Servercertificate without Certificate Chain / Hash of Public Key and algorithm / SHA-256 hash)
M365 Tenant
- 6.4% (153'148) of all .ch Domains have M365 Tenant
- 8.3% (12'757) of Domains with an M365 Tenant have DKIM enabled
- 63% (96'959) of Domains with an M365 Point the MX to EOP (*protection.outlook.com)
- 111'884 unique Tenants with .ch Domains
- About 10% of Company owned Domains use M365 (1'510'612 Company owned Domains / 153'148 Domains with M365 Tenant )
BIMI (Brand Indicators for Message Identification)
- Exists since 2021 but is still under development IETF BIMI Draft
- 0.02% (298) of all .ch Domains Support BIMI / only 14 with a Certificate
Summary
Let’s wrap it up
- It is amazing that over 40% of the DNS Zones already support DNSSEC.
- STARTTLS has improved from about 75% to 87%. That’s impressive - the goal should be 100%
- SPF has improved from 28% to 50%. Still a long way to go and “-all” should be standard
- DKIM is about 5.7% - that’s way to low and schould be standard anyway.
- DMARC has improved from about 1% to 8%. Most of it with “p=none” - Still a long way to go and “p=reject” should be standard.
- DANE is about 28.3% - surprising high due to the fact it’s quite complex to set up and it has a DNSSEC Requirement
As you can see - there is still a huge “space for improvement” for Email Security in Switzerland.
Let’s make Email better and implement those well known Techniques better to improve the Mailsecurity in Switzerland.
That means you, as an Mailserver Administrator, you as a Provider, you as a CISO, you as a Business Representive… Take action and help to improve the situation and secure the Mail related DNS Settings.
I would like to hear about your actions on Twitter with the Hashtag #SwissDomainSecurityReport 😍
My personal Learnings
I’ve made some learnings along the way
- Efficient i/o handling in PowerShell (system.IO.StreamReader / system.IO.StreamWriter)
- Learned about a new DNS Record like CAA
- SQL Indexes are important 😂
- I have learned how to use PowerShell 7 and run a Scriptblock with the -paralell Parameter. Shout out to Fabrice Reiser who helped me here.
- How to write a Report like this
Regards
Andres Bohren