Deploy MTA-STS with PS.MTA-STS PowerShell Module

Hi All,
I’ve explained how “Mail Transfer Agent Strict Transport Security (MTA-STS)” works in this Article
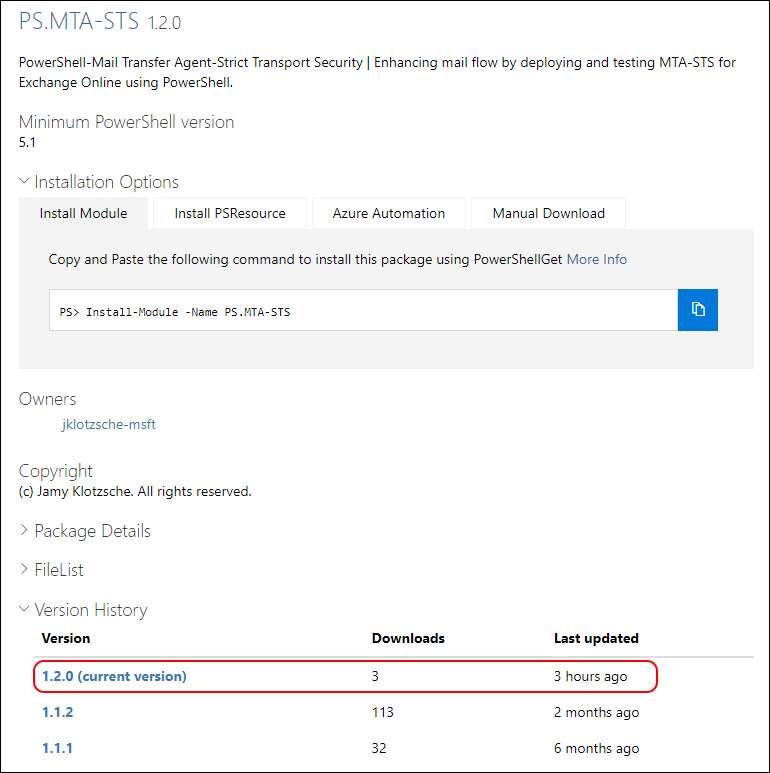
PS.MTA-STS
A Month ago, the PS.MTA-STS PowerShell Module was announced on the Exchange Team Blog
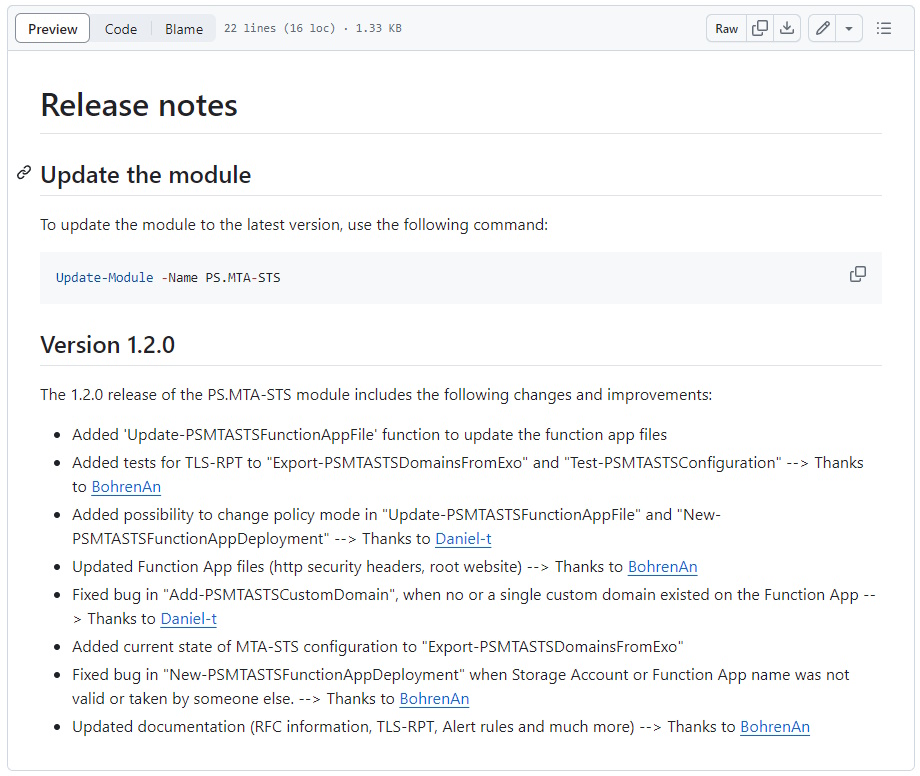
Today a new Version has been released
- PowerShell Gallery PS.MTA-STS 1.2.0
I’ve tested the Module back then and contacted Jamy Klotzsche and worked with him to improve the Module on GitHub PS.MTA-STS
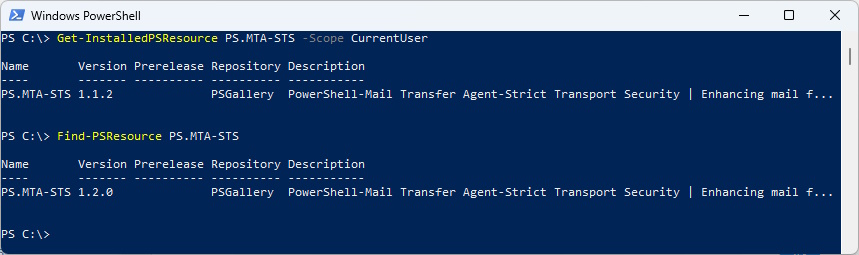
Get-InstalledPSResource PS.MTA-STS -Scope CurrentUser
Find-PSResource PS.MTA-STS
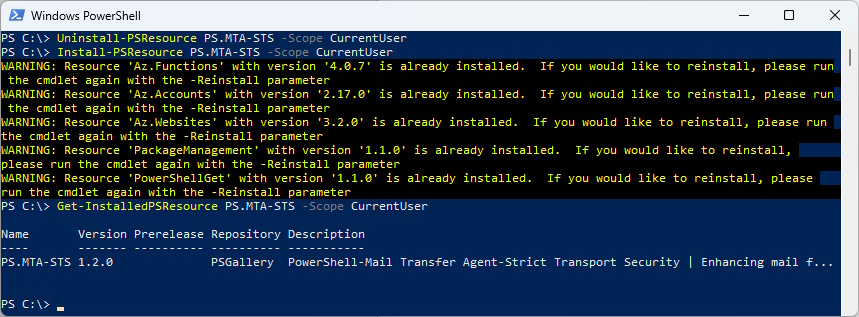
Uninstall the old Module and install the new PowerShell Module
Uninstall-PSResource PS.MTA-STS -Scope CurrentUser
Install-PSResource PS.MTA-STS -Scope CurrentUser
Get-InstalledPSResource PS.MTA-STS -Scope CurrentUser
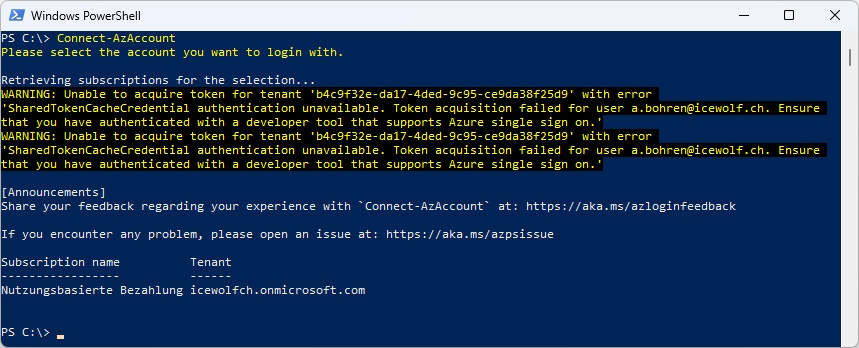
It’s best to connect to Azure first
Connect-AzAccount
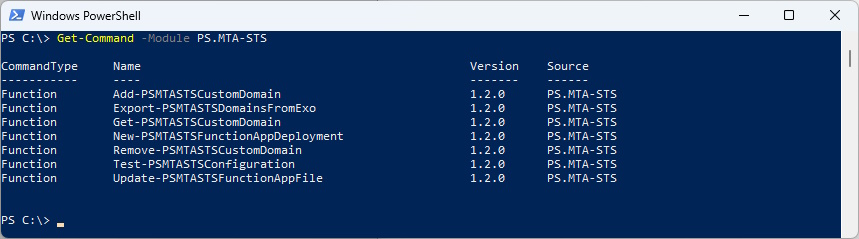
List the commands from the PowerShell Moduel
Get-Command -Module PS.MTA-STS
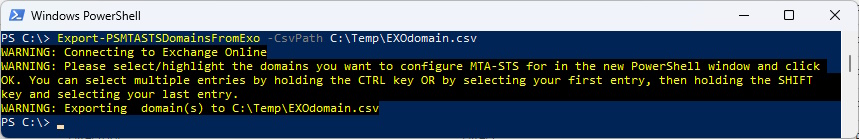
You can select and export the Accepted Domains from Exchange Online to a CSV File
Export-PSMTASTSDomainFromExo -CsvPath C:\Temp\ExoDomain.csv
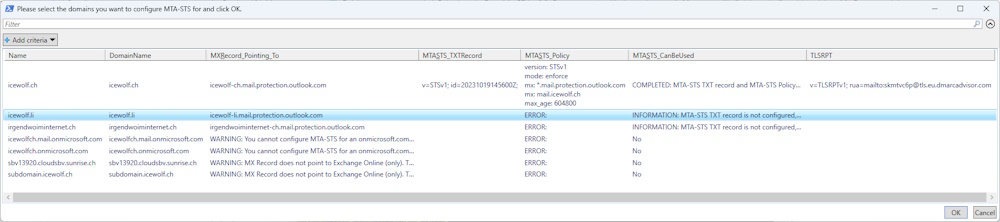
The Overview will be shown in a Grid View - the marked rows will be exported to the CSV File
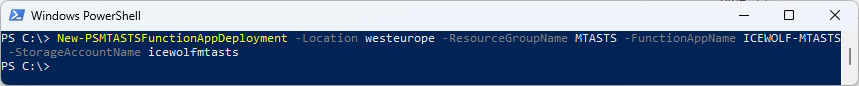
Now it’s time to deploy the Azure Function
Note: The FunctionApp needs to be unique worldwide as the URL will be “FunctionAppName.azurewebsites.net”
Note; The StorageAccount needs to be unique worldwide as the URL will be “StorageAccountName.blob.core.windows.net”
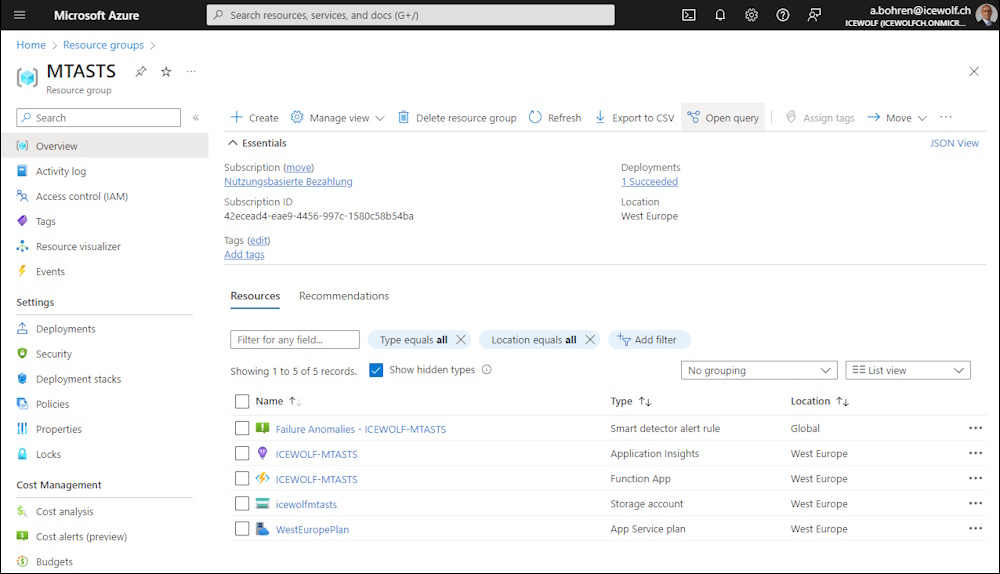
It takes a while, until all the Azure Resources have been deployed
New-PSMTASTSFunctionAppDeployment -Location westeurope -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS -StorageAccountName icewolfmtasts
These are the Azure Resources that have been deployed
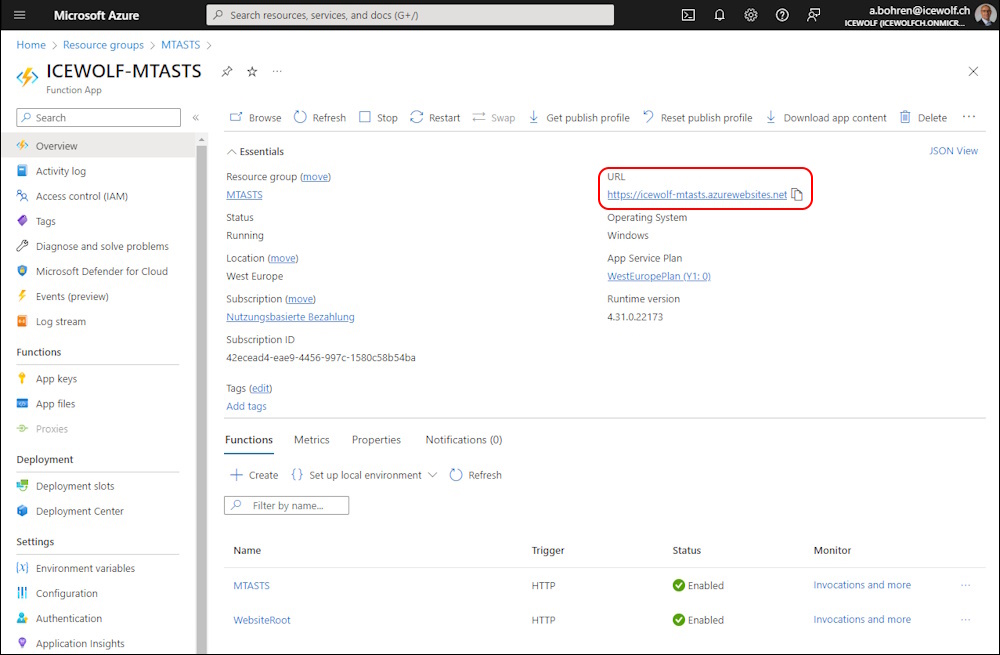
On the Overview of the Azure Function app you can find the URL
The Function App contains a Function for “" (Root Website) that has the Link to the MTA-STS Policy
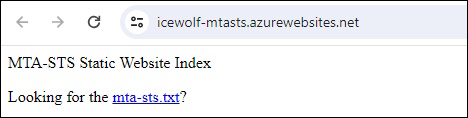
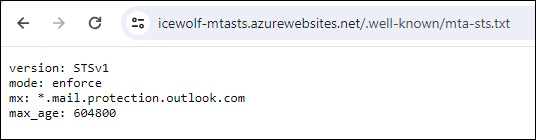
If you click on the Link you will get the MTA-STS Policy
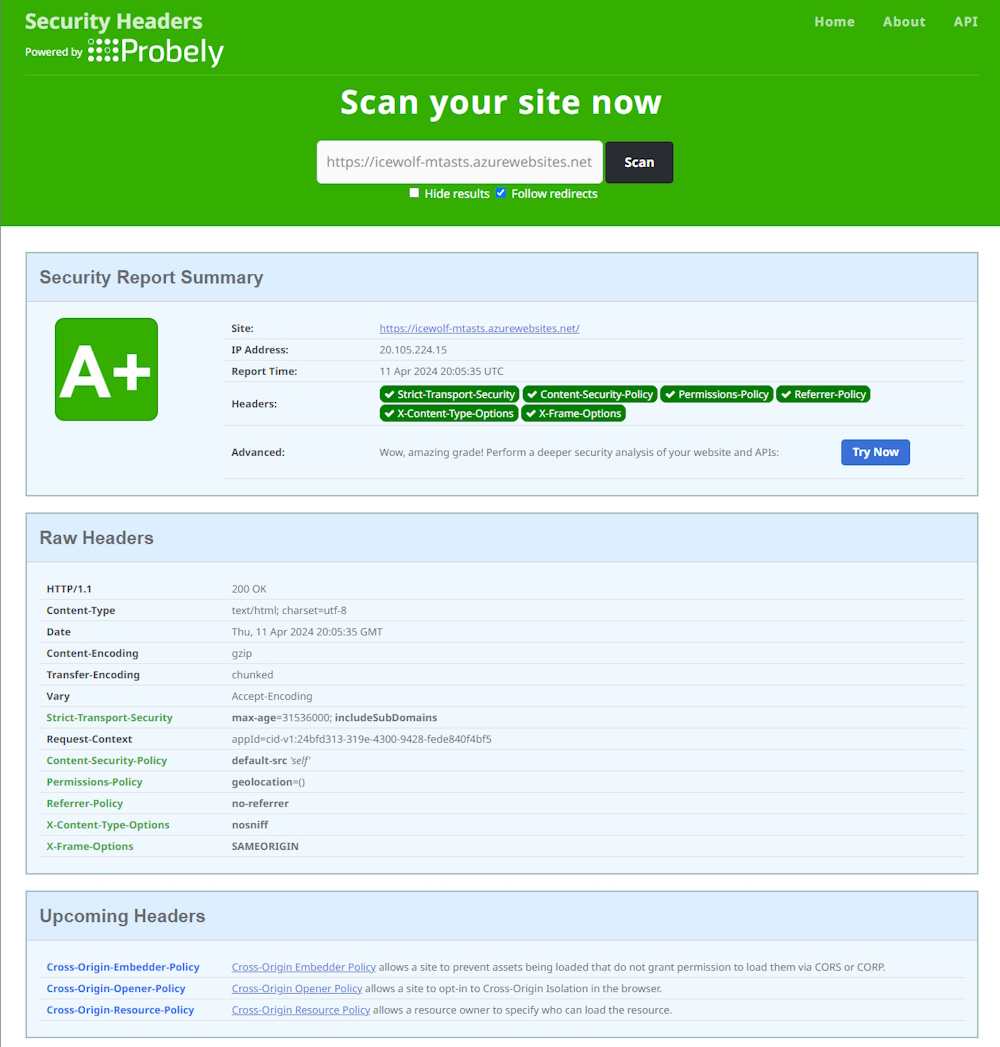
The Websites do now include HTTP Security Headers
https://icewolf-mtasts.azurewebsites.net/
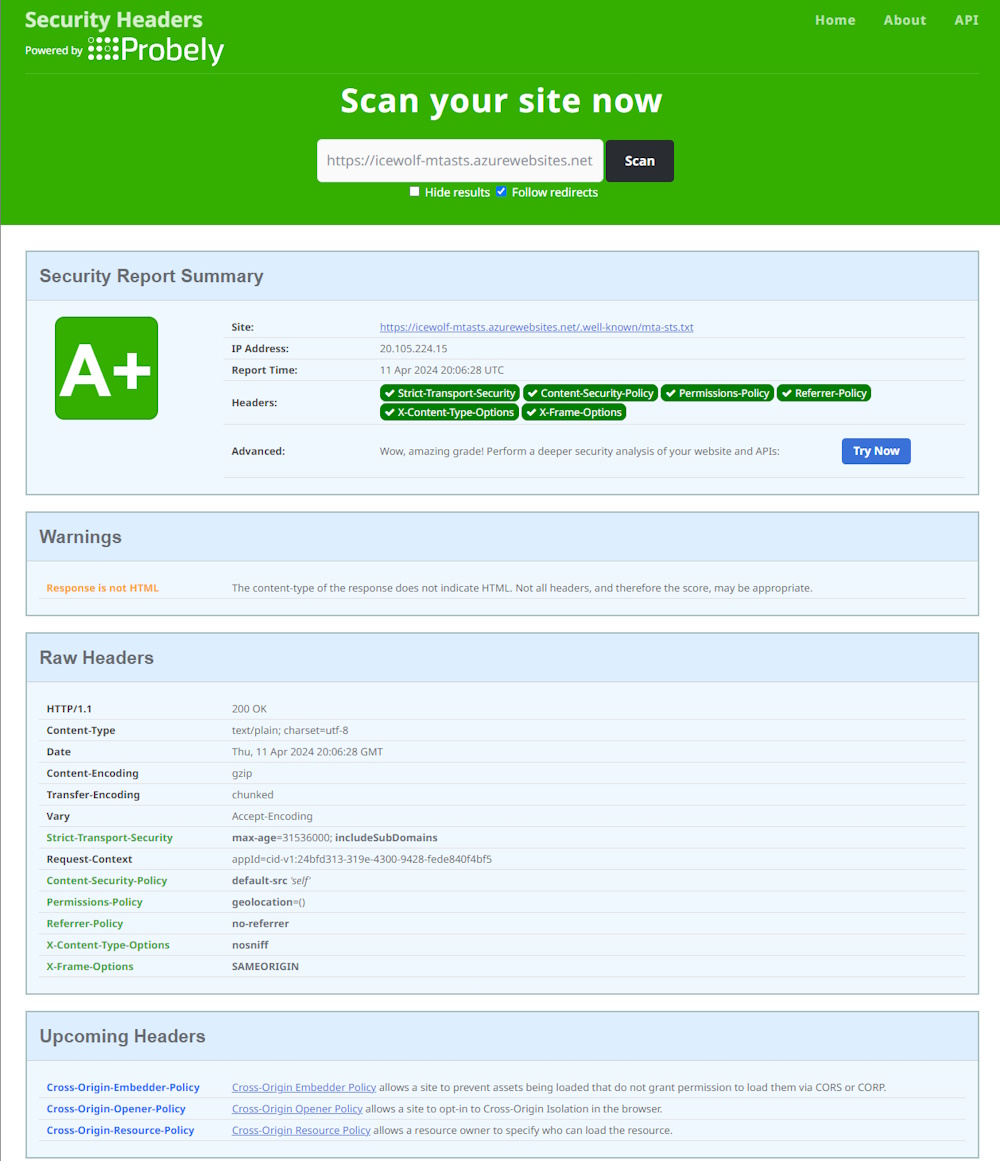
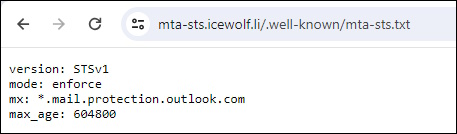
Note: when you use the full URL with mta-sts.txt you get a warning that it’s not HTML
https://icewolf-mtasts.azurewebsites.net/.well-known/mta-sts.txt
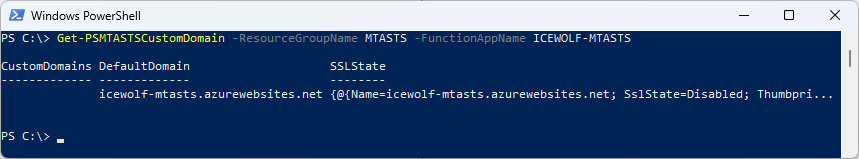
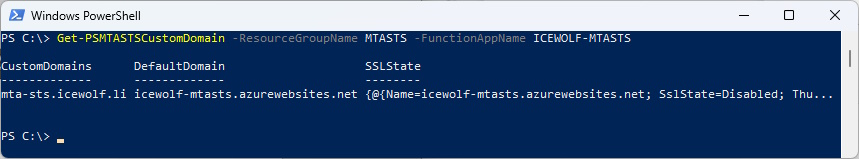
List custom domains of the Azure Function App
Get-PSMTASTSCustomDomain -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS
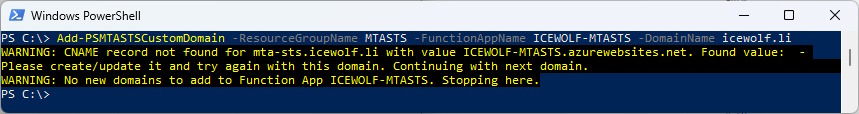
Now we try to add the cutom domain. You will get a warning, because the Certificate can not be issued, as long the DNS Name does not point to the Azure Function App
Add-PSMTASTSCustomDomain -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS -DomainName icewolf.li
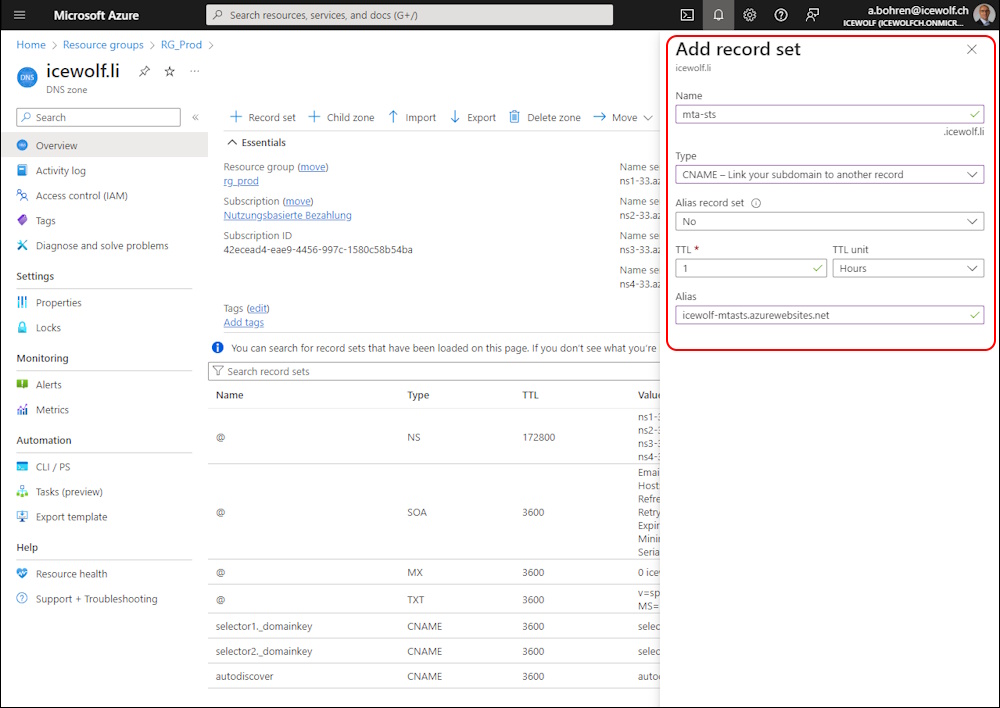
Adding CNAME DNS Record “mta-sts.domain.tld” that points to the Azure Function App
This time it works
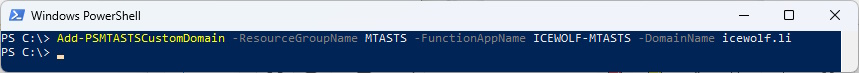
Add-PSMTASTSCustomDomain -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS -DomainName icewolf.li
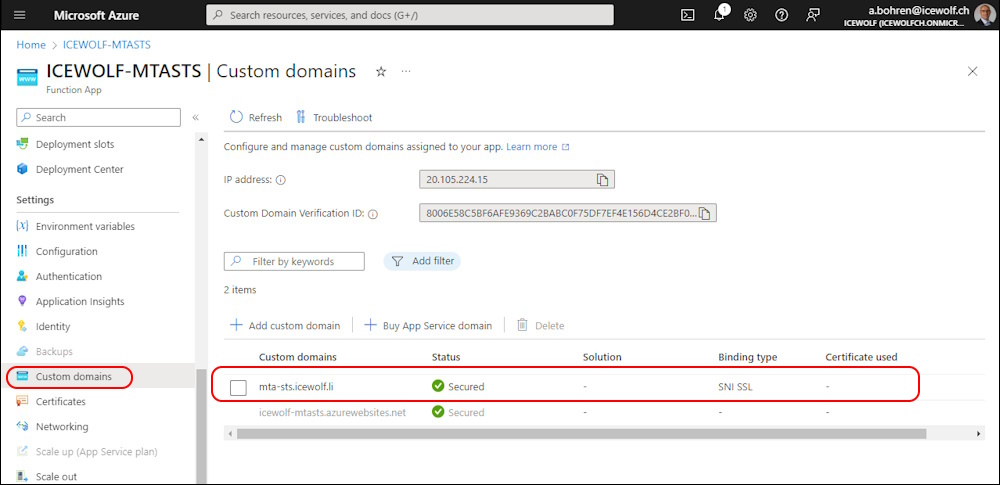
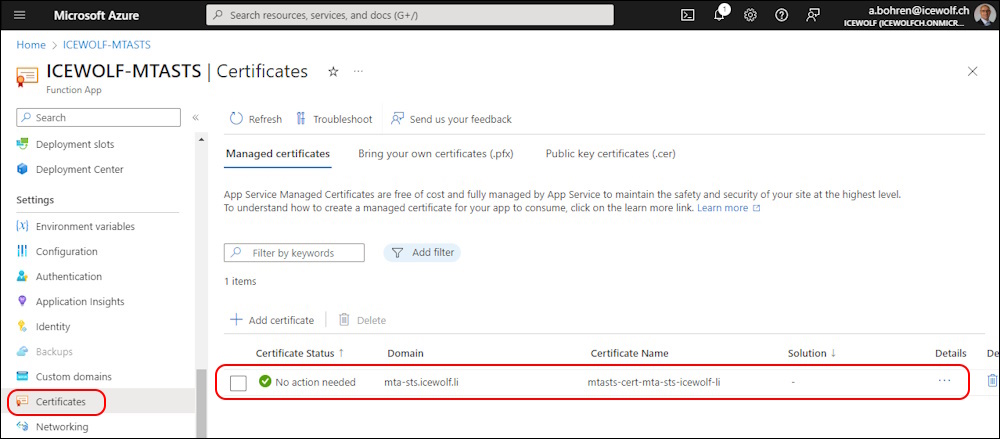
Now you can see the custom domain on the Azure Function App “mta-sts.domain.tld”
Also the Certificate for “mta-sts.domain.tld” has been deployed
Now we can see that there is a custom Domain listed
Get-PSMTASTSCustomDomain -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS
Works without Certificate warning in the Browser
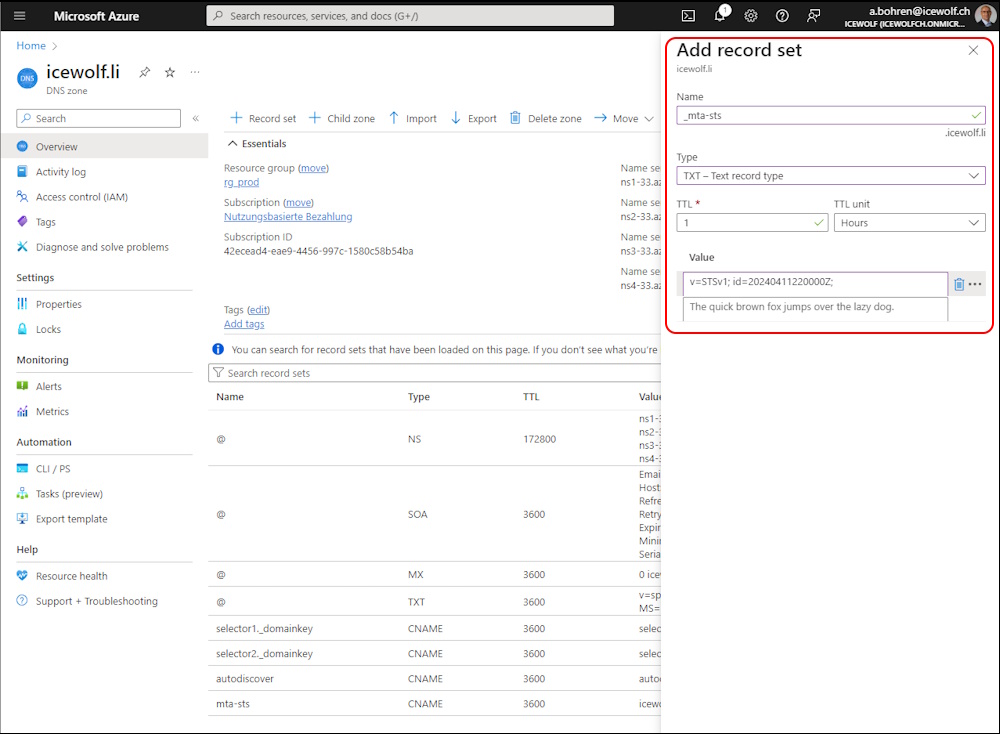
It’s time to enable the _mta-sts.domain.tld TXT Record
v=STSv1; id=20240411220000Z;
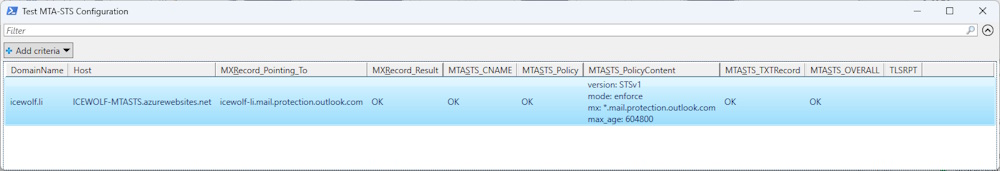
We can test the Configuration against the Exported CSV from “Export-PSMTASTSDomainFromExo”
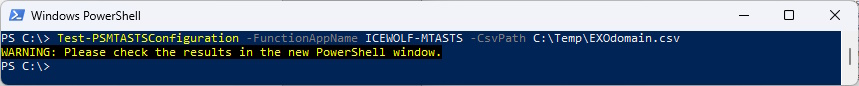
Test-PSMTASTSConfiguration -FunctionAppName ICEWOLF-MTASTS -CsvPath C:\Temp\EXOdomain.csv
The Result will be shown in a Grid View
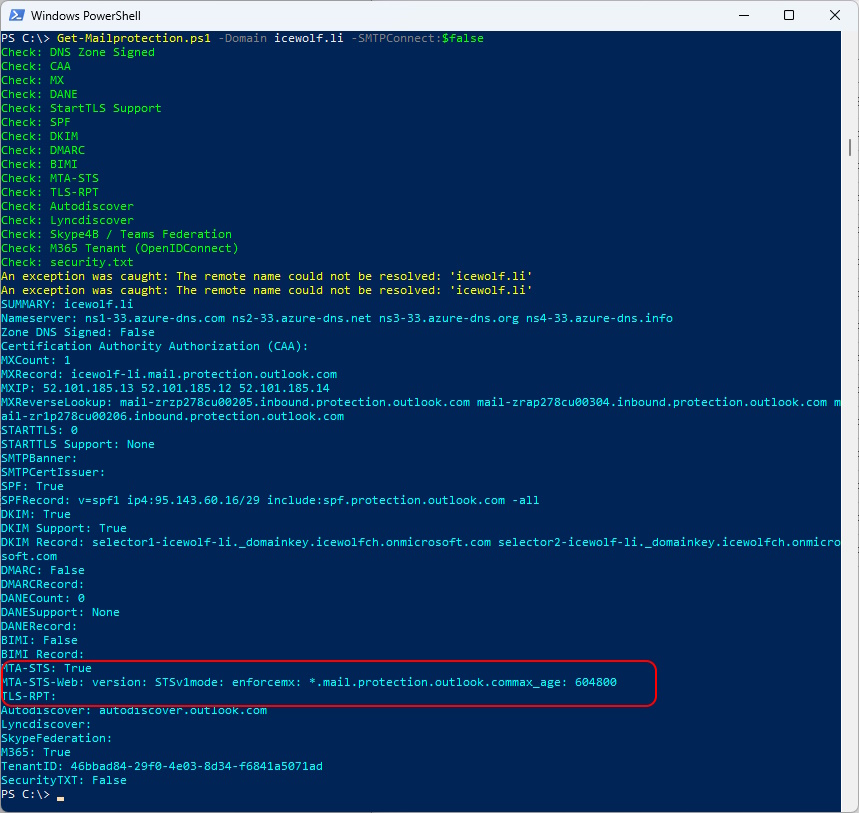
We can check also with my Get-Mailprotection Script
Get-Mailprotection.ps1 -Domain icewolf.li -SMTPConnect:$false
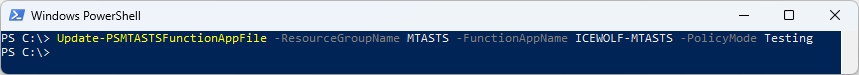
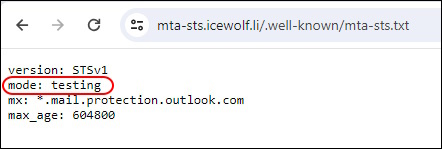
If you want to change the PolicyMode you can use the following Command
Update-PSMTASTSFunctionAppFile -ResourceGroupName MTASTS -FunctionAppName ICEWOLF-MTASTS -PolicyMode Testing
As you can see the mode has changed
Summary
I am proud to work with Jamy and bring MTA-STS for Exchange Online to the next level and hope to increase the MTA-STS coverage for Exchange Online.
Regards
Andres Bohren