Secure Exchange Online when using CMT or 3rd Party Mailgateway

Hi All,
In my professional Life, i have architected and implemented many Exchange Hybrid Organizations.
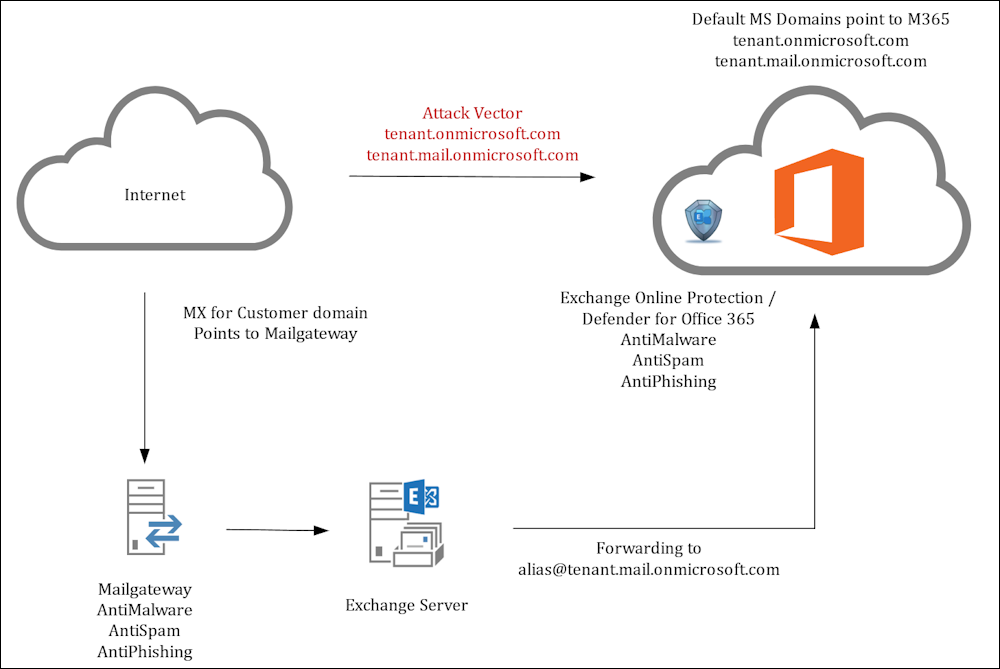
Most of the Time the MX Records still point to the OnPrem Mailgateway or a 3rd Party Service for AntiMalware, Antispam, AntiPhishing. These Systems have well designed Rules for preventing Malware and unwanted Mails.
But customers forget, that with Exchange Online by default comes two MX Records to your Tenant, where someone potentially can bypass all these checks from the OnPrem Mailgateway and deliver Mails directly to Exchange Online Protection (EOP).
Default MX Records for a Tenant
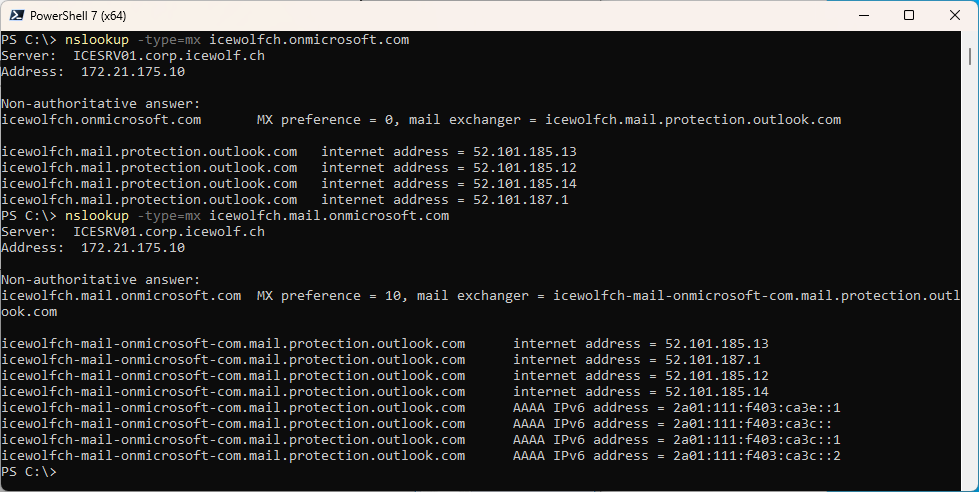
You can check this for your own Tenant
When you check Microsoft 365 URLs and IP address ranges (ID 10), then you see that these are the IP’s for Exchange Online Protection (EOP). From the Internet the Port 25 is open and can receive email.
nslookup -type=mx tenant.onmicrosoft.com
nslookup -type=mx tenant.main.onmicrosoft.com
As an Attacker you only need to send to that MX, and the Message will be delivered to the Exchange Online Mailbox or via Hybrid Mailflow to the OnPrem Mailbox.
Centralized Mail Transport (CMT)
Now to the Outbound Connector of Exchange Online.
I see still a lot of Organizations that use Centralized Mail Transport (CMT). Sometimes because they have invested recently in a new Mailgateway or have other specialities like Routing to other Appliances for Mail Signature/Encryption like SEPPMail or Kiteworks (ex Totemo).
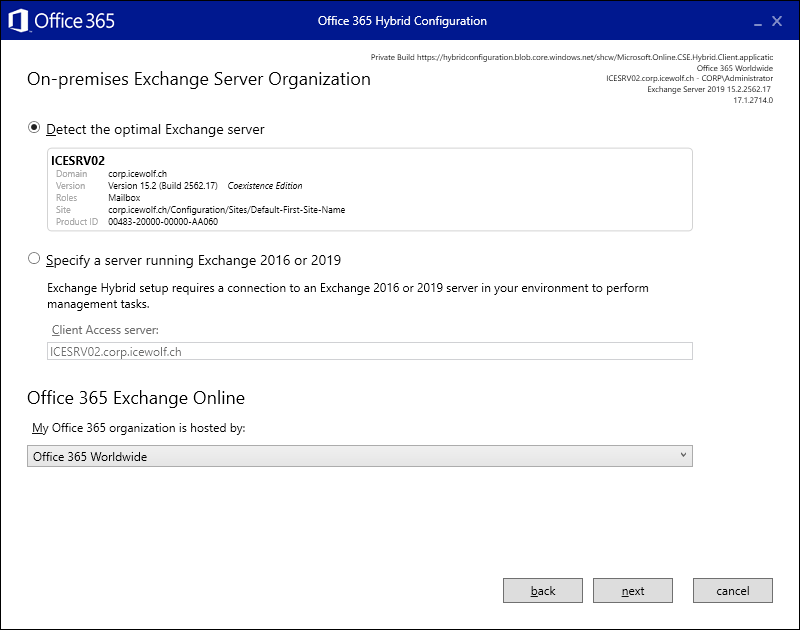
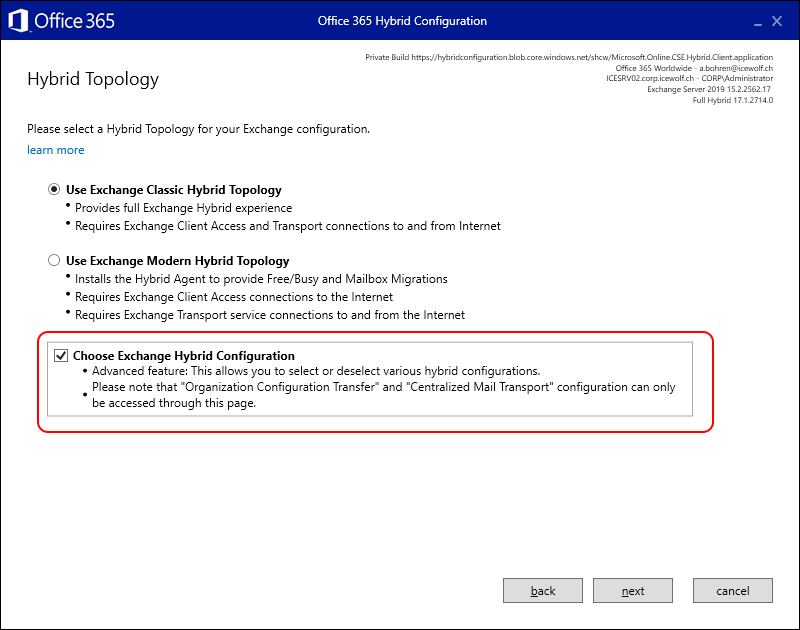
If that is the Case, you probably have run the Hybrid Configuration Wizard with the following Options
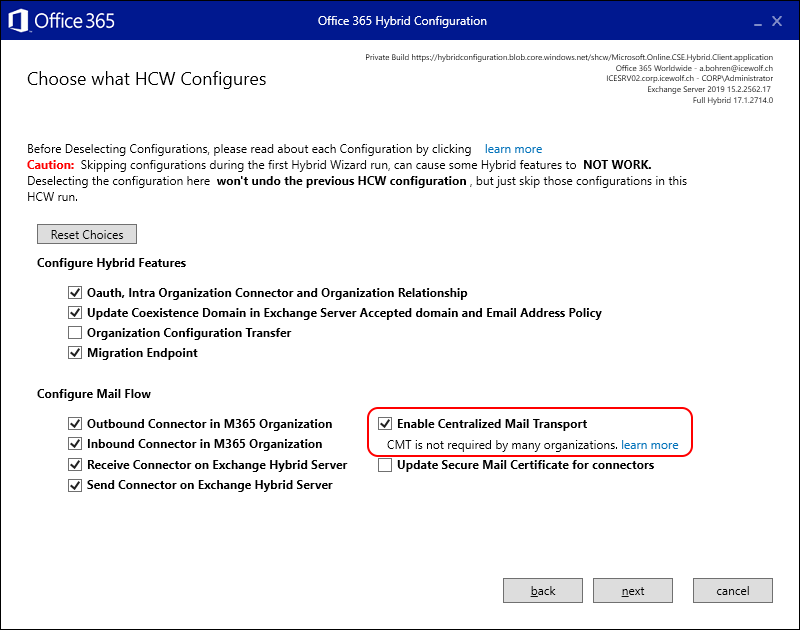
You need to select “Choose Exchange Hybrid Configuration” when you want enable Centralized Mail Transport (every time you run Hybrid Configuration Wizard)
And select “Enalbe Centralized Mail Transport”
Be aware that the Centralized Mail Transport has some Limitations that are burried deep into the Exchange Team Blog
Scenarios not covered by CMT:
- Messages originating from Exchange on-premises
- Messages sent between two Exchange Online mailboxes (more later in the article)
- Messages forwarded by Exchange Online (more on this later, too)
- Messages that trigger a transport rule redirecting it via Criteria Based Routing (CBR) through a specific Outbound Connector; CBR has preference over CMT
This means:
Even when Centralized Mail Transport has been enabled, not all Messages are routed via OnPrem Exchange.
Therefore it’s recommended to add the SPF Record
include:spf.protection.outlook.com
And configure DKIM in Exchange Online
- Enable DKIM in Exchange Online (updated)
- How to set the DMARC Record for <\tenant>.onmicrosoft.com Address
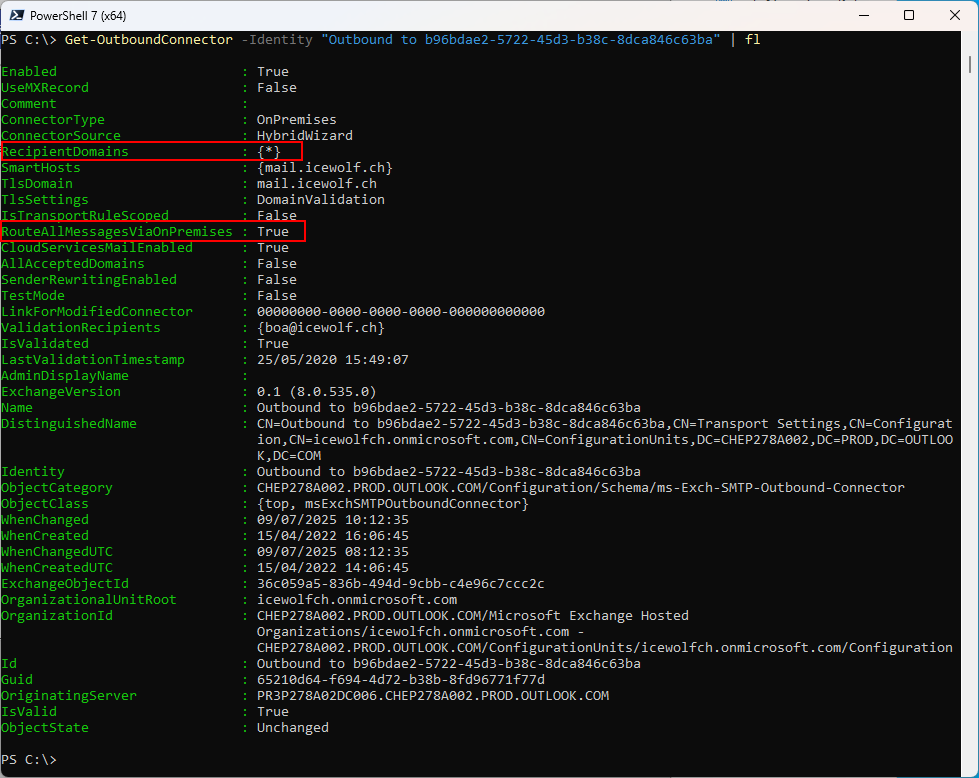
Check Outbound Connector
When you check your Hybrid Outbound Connector you can see, that the Recipient Domains are set to “*” and RouteAllMessagesViaOnPremise is set to “True”. That’s all that Centralized Mail Transport really does 😊
Get-OutboundConnector -Identity "Outbound to b96bdae2-5722-45d3-b38c-8dca846c63ba" | fl
Block Attack Vector
There is a Guidance from Microsoft how you can prevent this
Option 1: Inbound Connector with Certificate
You create an Inbound Connector that requires a Certificate for all Sender Domains. This does not affect your Hybrid Mail Flow.
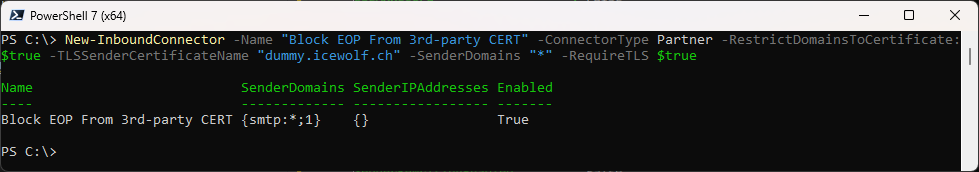
New-InboundConnector -Name "Block EOP From 3rd-party CERT" -ConnectorType Partner -RestrictDomainsToCertificate:$true -TLSSenderCertificateName "dummy.icewolf.ch" -SenderDomains "*" -RequireTLS $true
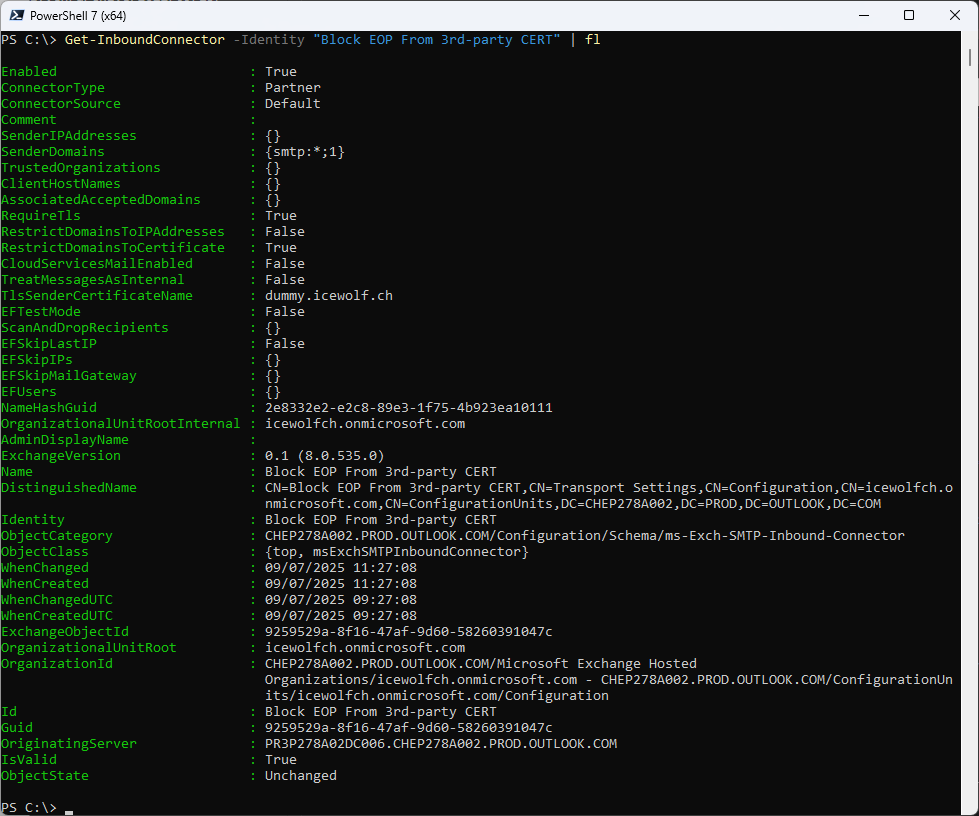
Details of the Inbound Connectpr
Get-InboundConnector -Identity "Block EOP From 3rd-party CERT" | fl
Option 2: Inbound Connector with IP
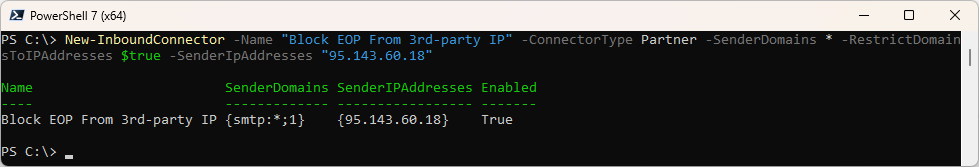
You create an Inbound Connector that requires a Certificate for all Sender Domains.
New-InboundConnector -Name "Block EOP From 3rd-party IP" -ConnectorType Partner -SenderDomains * -RestrictDomainsToIPAddresses $true -SenderIpAddresses <#static list of on-premises IPs or IP ranges of the third-party service>
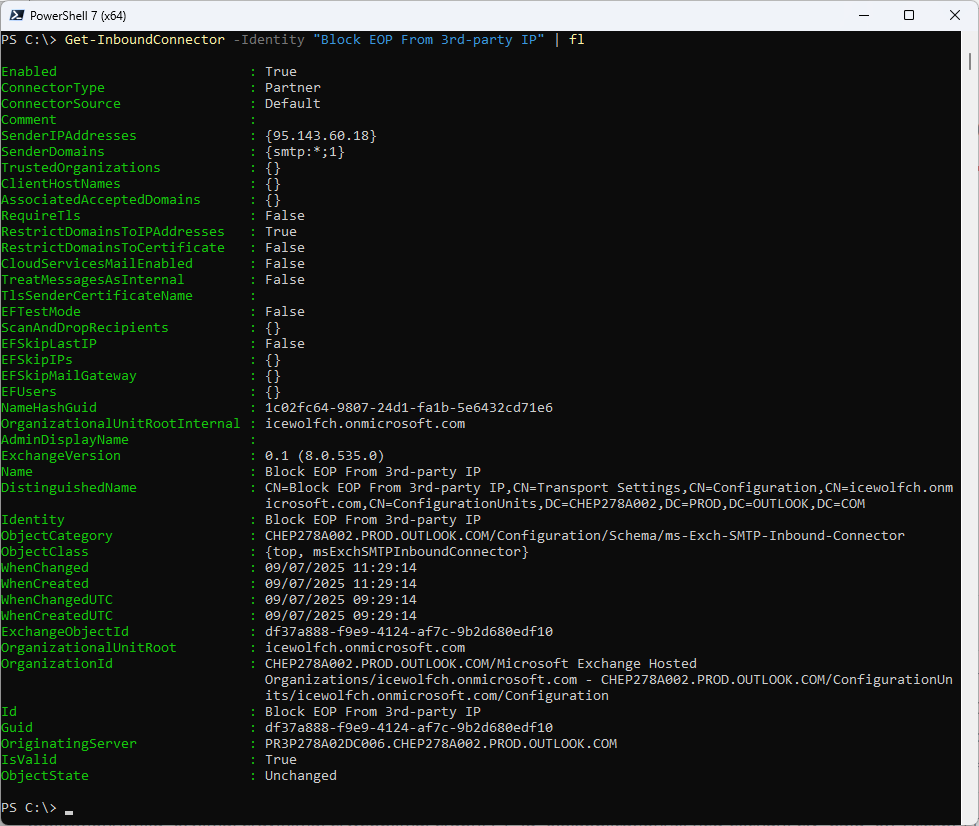
Details of the Inbound Connectpr
Get-InboundConnector -Identity "Block EOP From 3rd-party IP" | fl
The Hybrid Inbound Connector should not be affected, as a Certificate Based Connector has predence over IP Based Connectors.
Note: If you want to move your MX to Exchange Online, don’t forget to disable or delete the Block Connector.
Additional Recommendations
Even if you have blocked the Attack Vector from the Internet. I would still recommend setting the “Standard” Settings in Exchange Online Protection (EOP) and Microsoft Dfender for Office 365 (MDO).
Summary
Now you know how to block this Attack Vector and can secure your Exchange Online Environment.
Regards
Andres Bohren