Entra Verified ID Enable Facecheck

Hi All,
I have already written a few Articles about Entra Verified ID
- Microsoft Entra Verified ID
- Verified ID Advanced Setup
- Entra Verifiable credentials Admin API with PowerShell
Overview
Today we want to dig deeper into Face Check.
Prerequisits:
- Microsoft Entra Verified ID setup completed before using Face Check
- Azure Subscription / Resource Group
- User that sets up Face Check has Contributor role for the Azure subscription / Resource Group
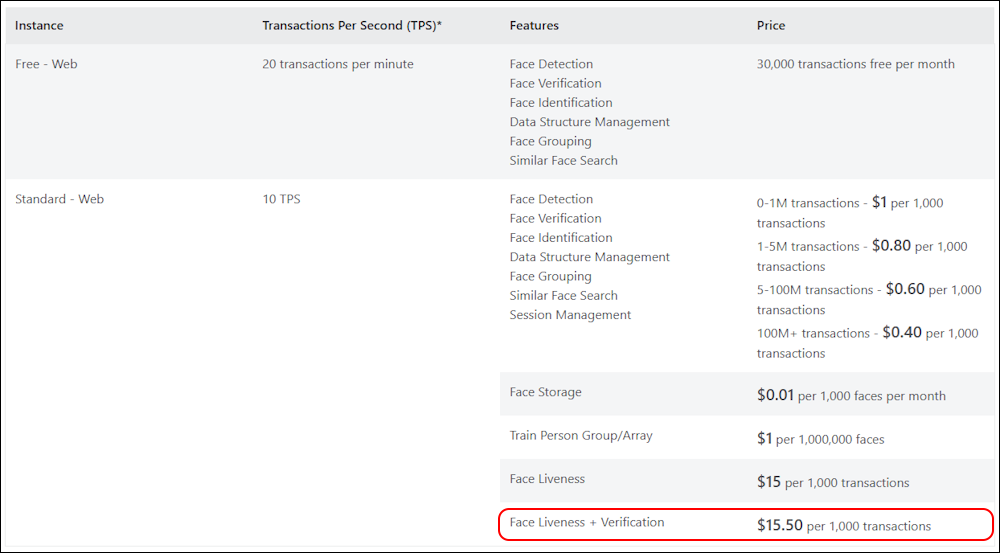
Costs:
The Cost of Verified ID Transaction is 0.25$ per Transaction
That is more that the Face API pricing
Entra Admin Center
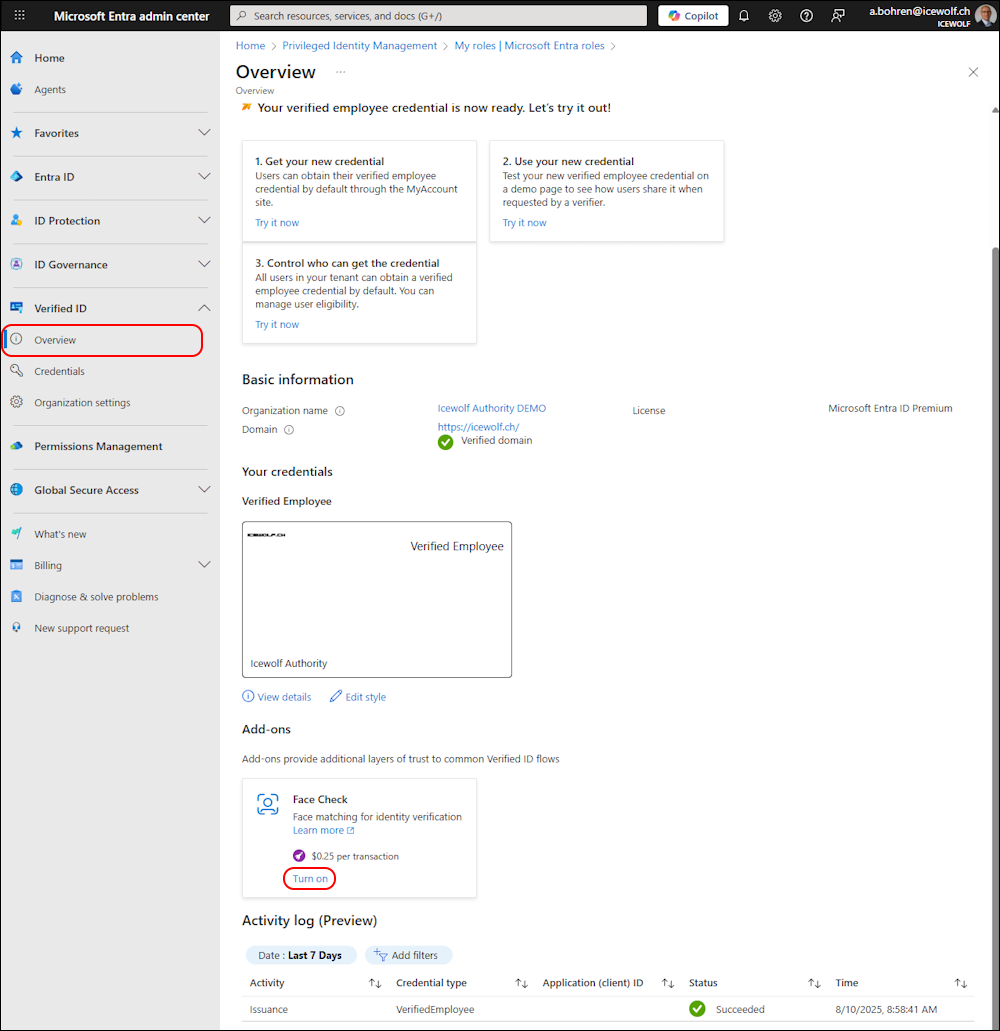
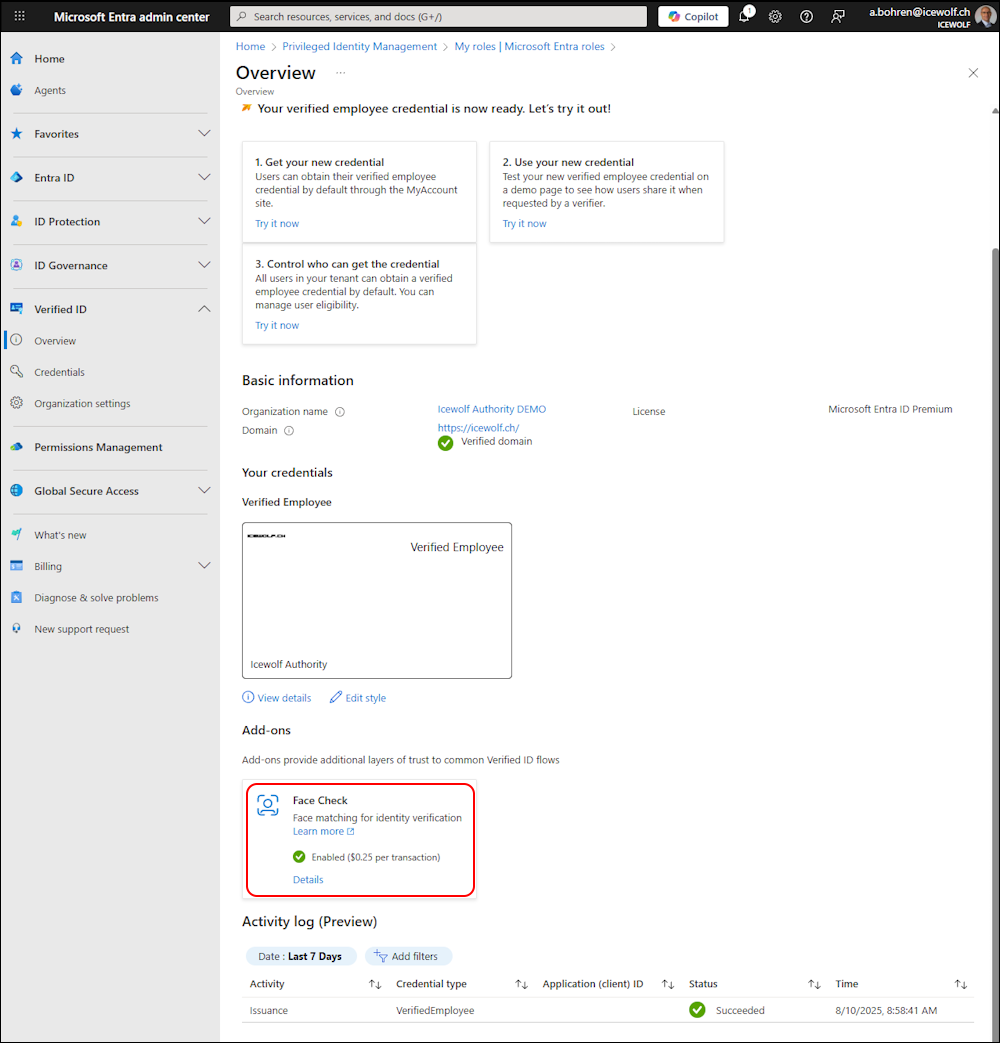
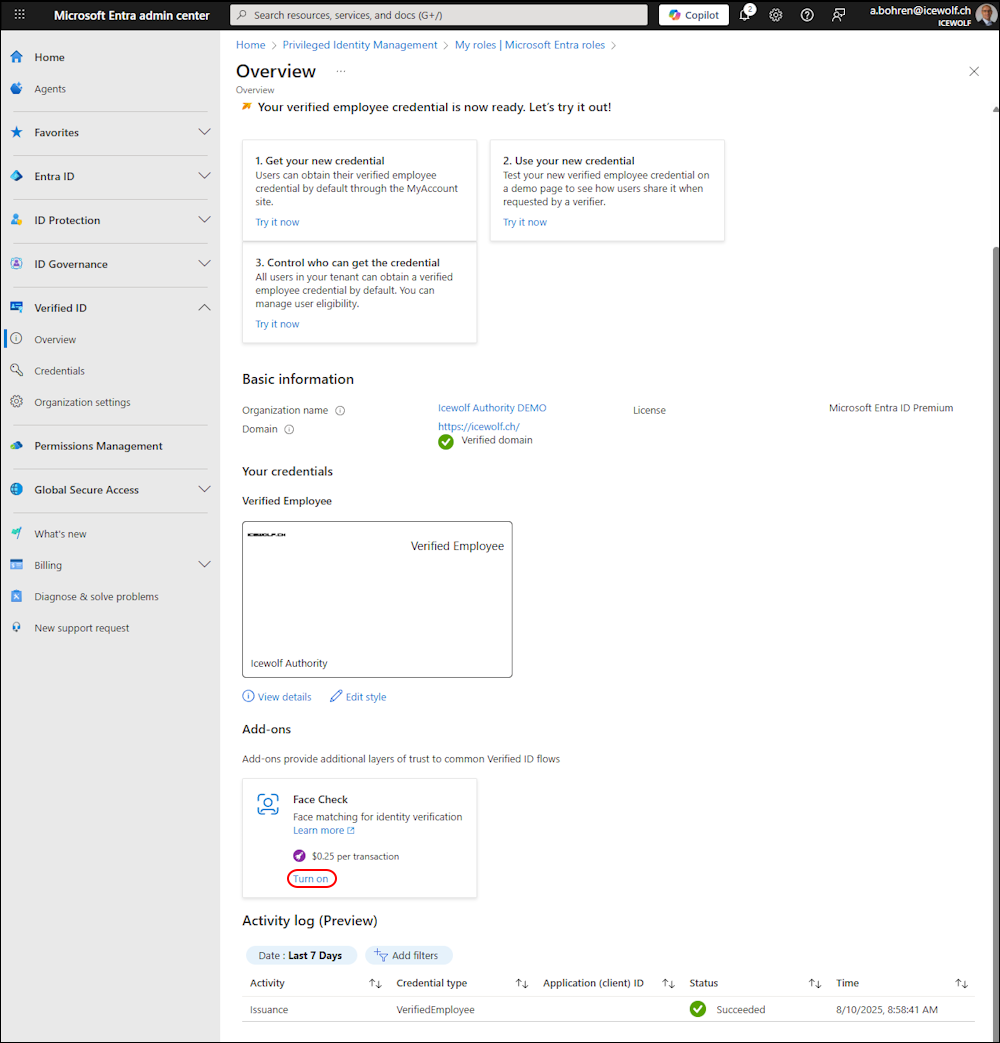
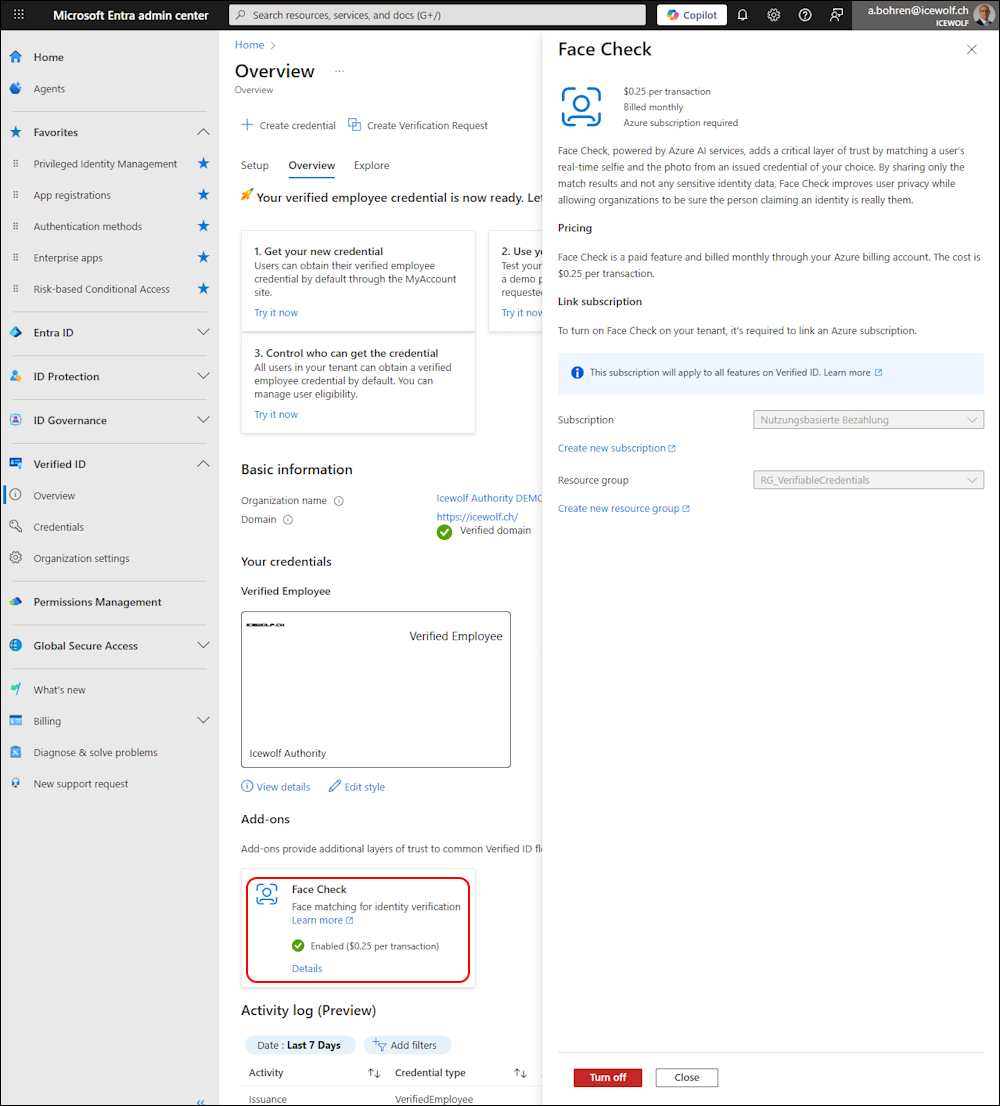
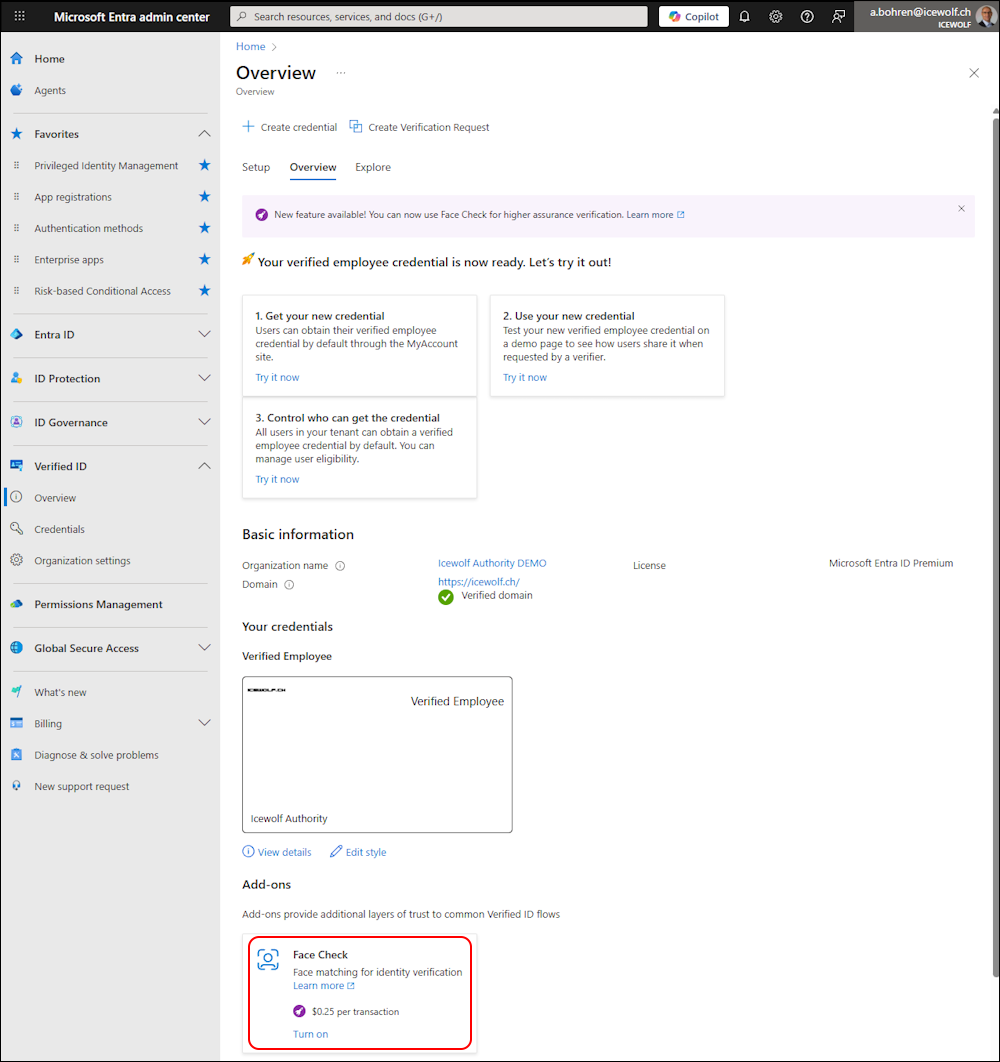
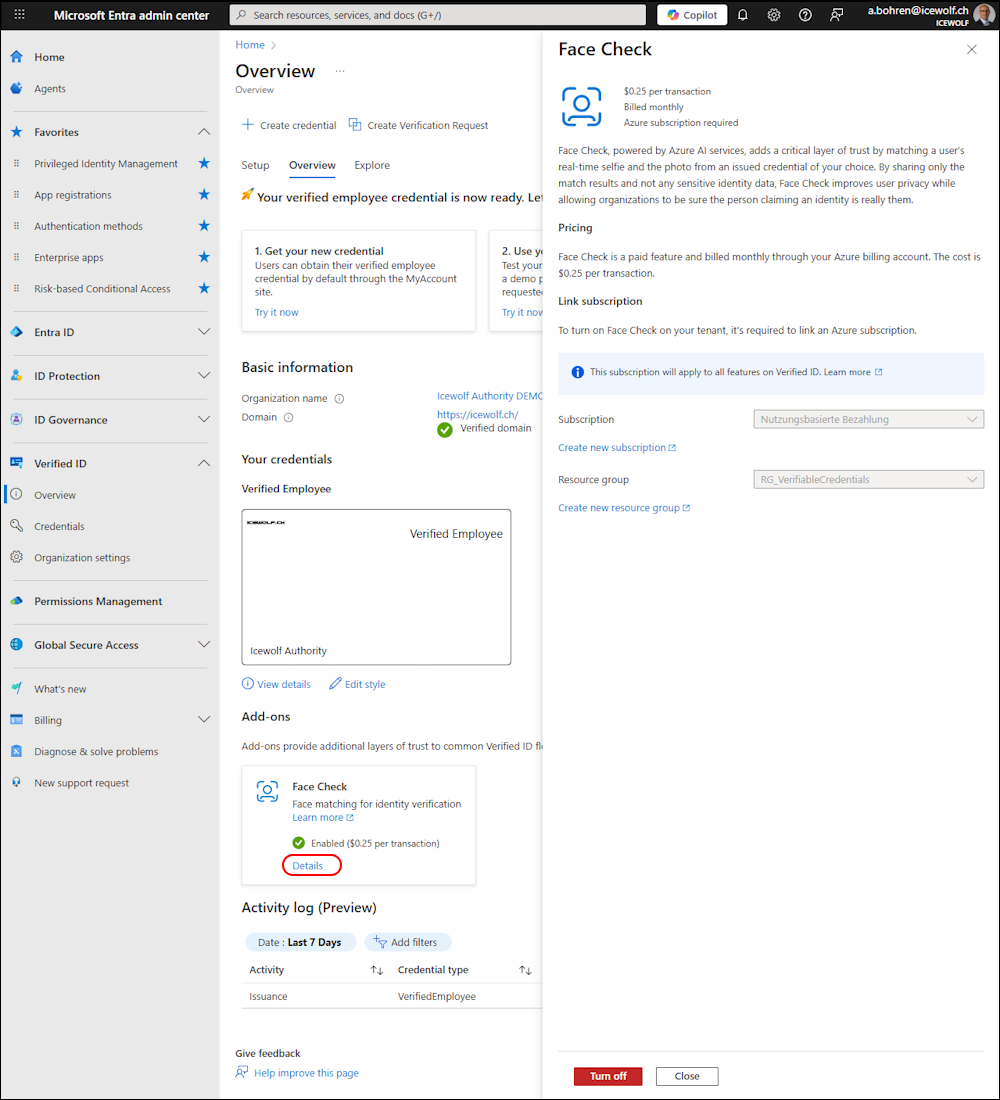
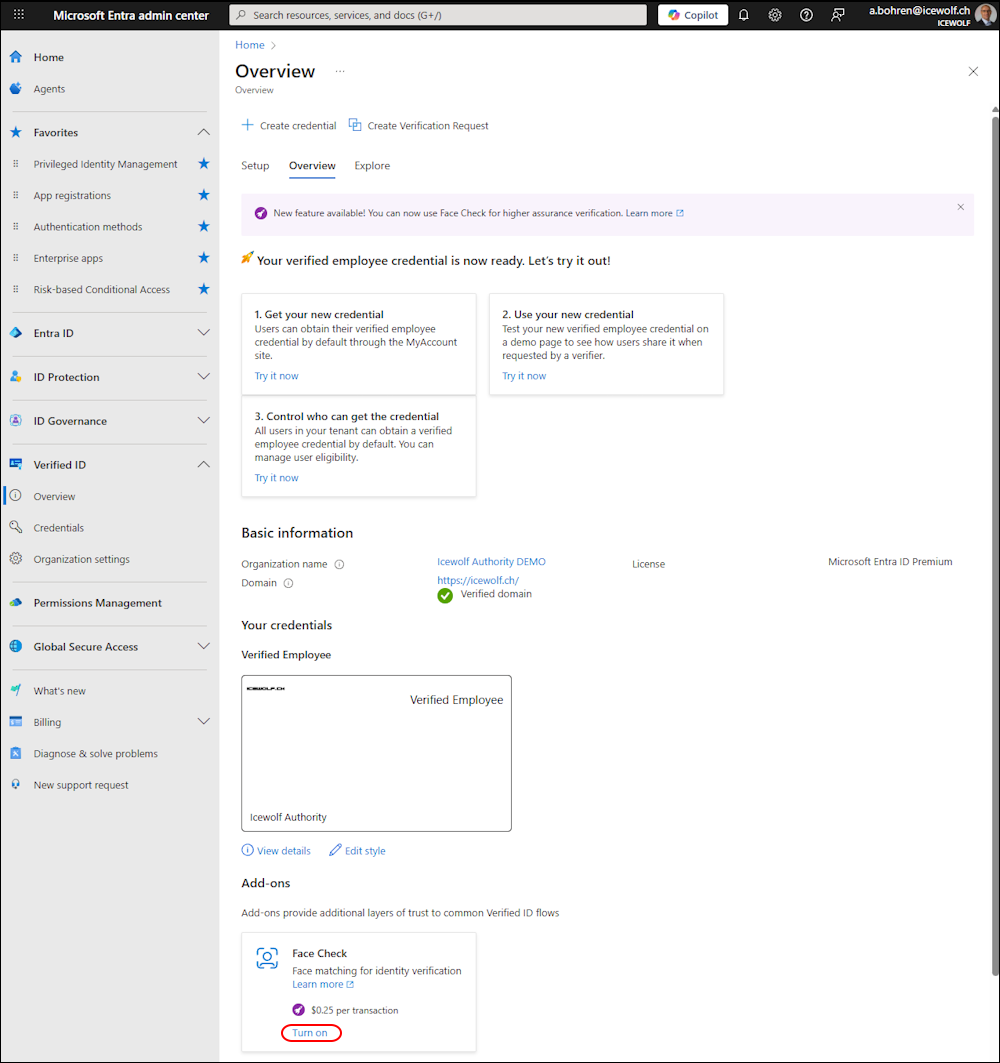
I’ve been logged in as “Global Administrator” and on the Entra Admin Center under “Verified ID”.
As you can see, it is turned of and we can turn Face Check on.
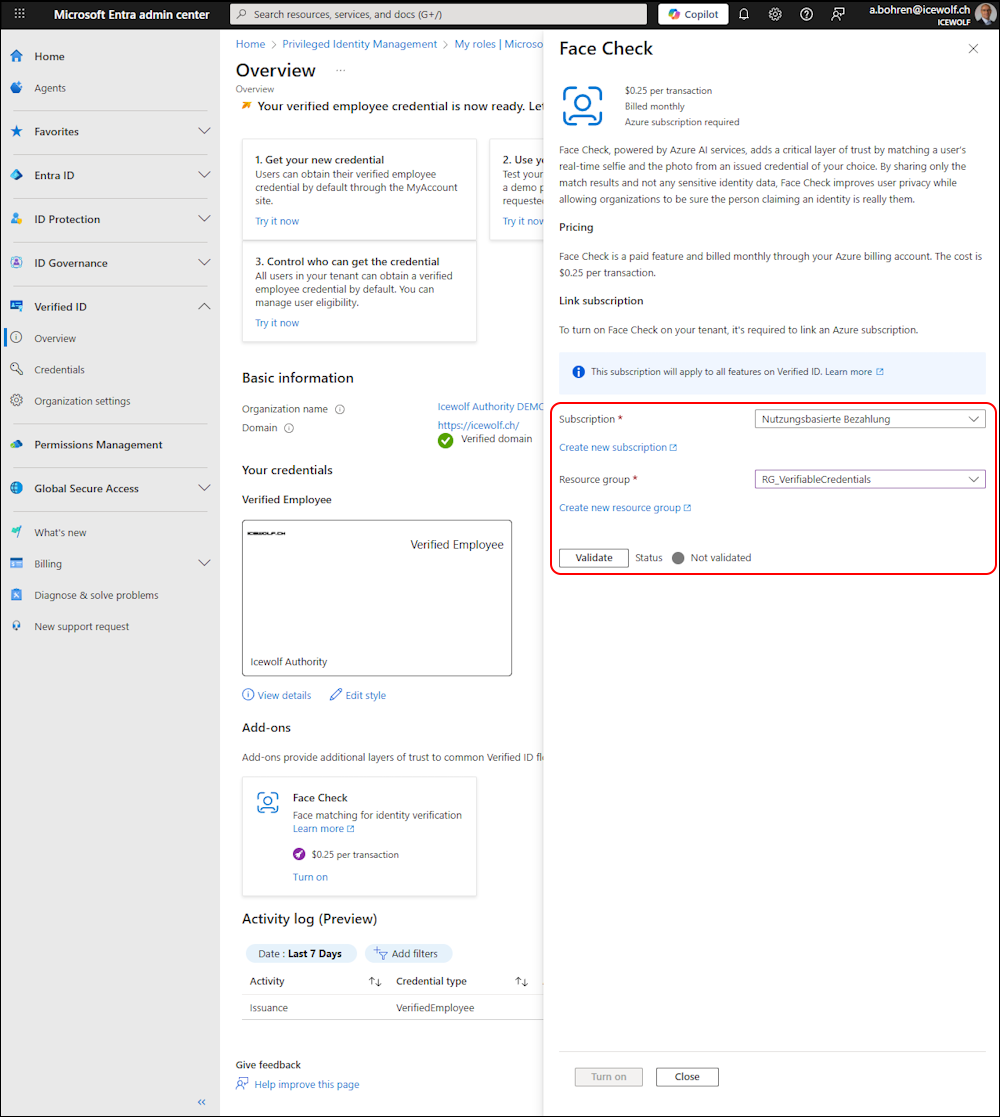
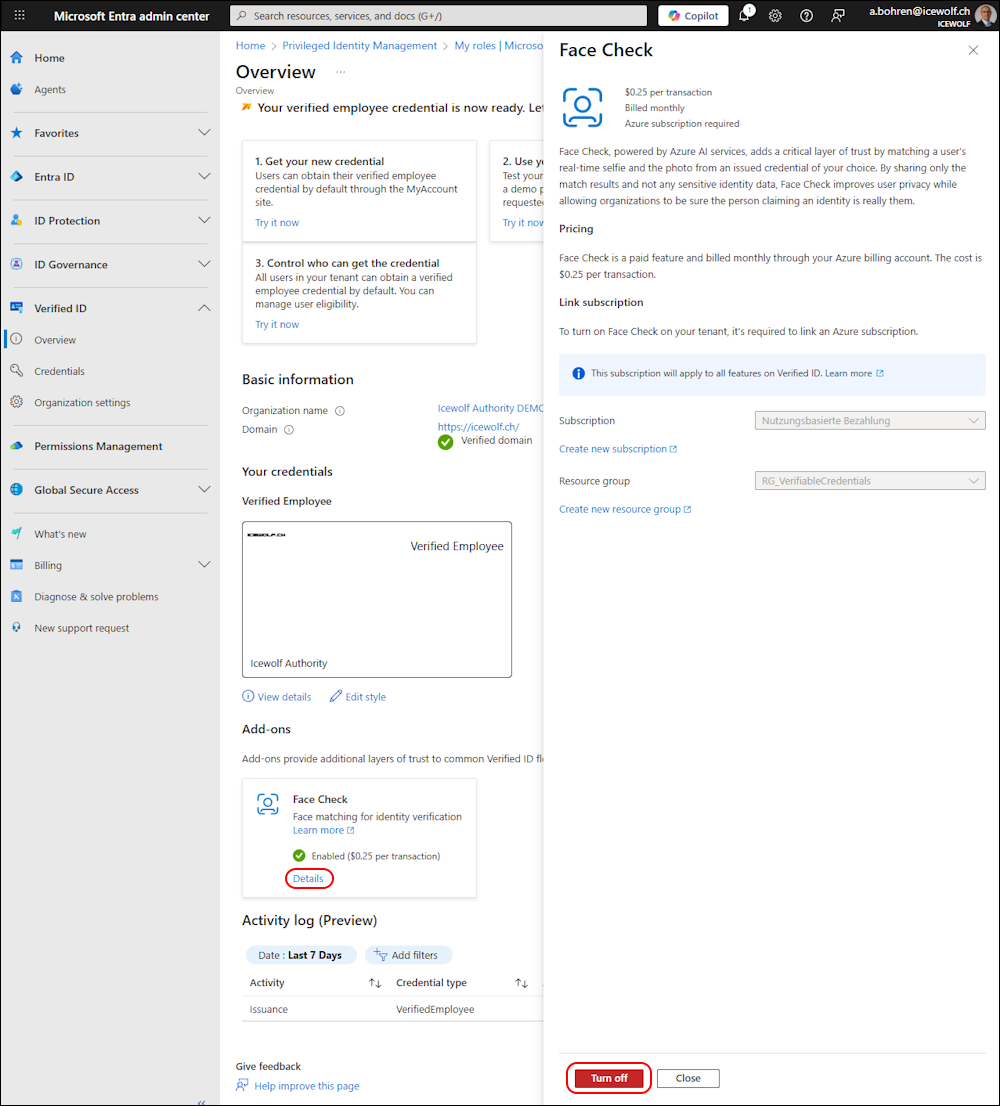
If you click on “Turn on” you need to select a Subscription and a Resource Group.
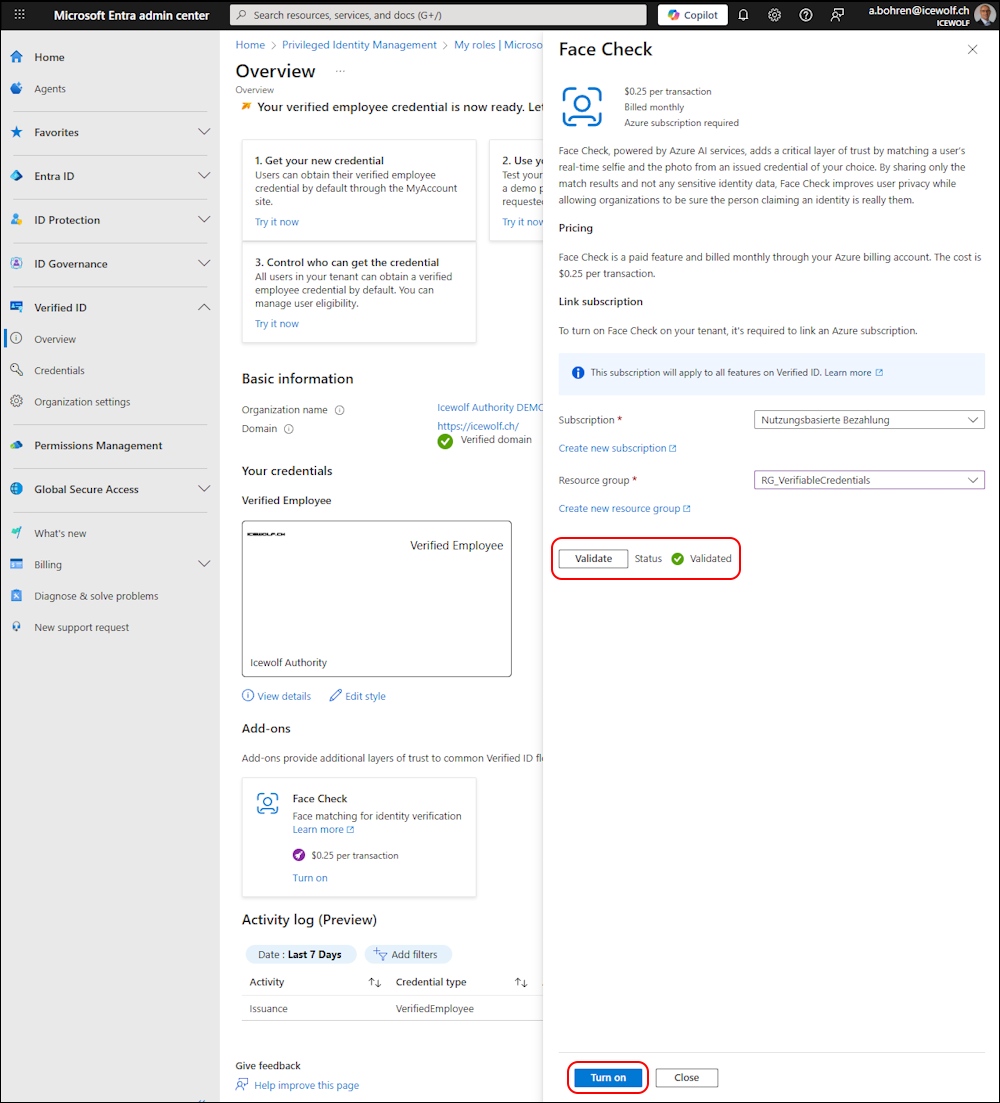
Now you can Validate - if validation is sucessful “Turn on” to Enable Face Check
In the Overview we can see it’s now enabled
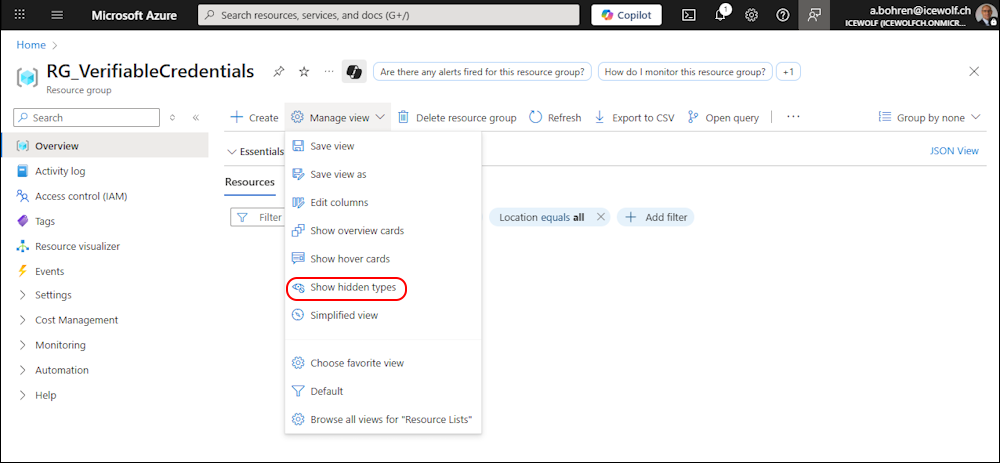
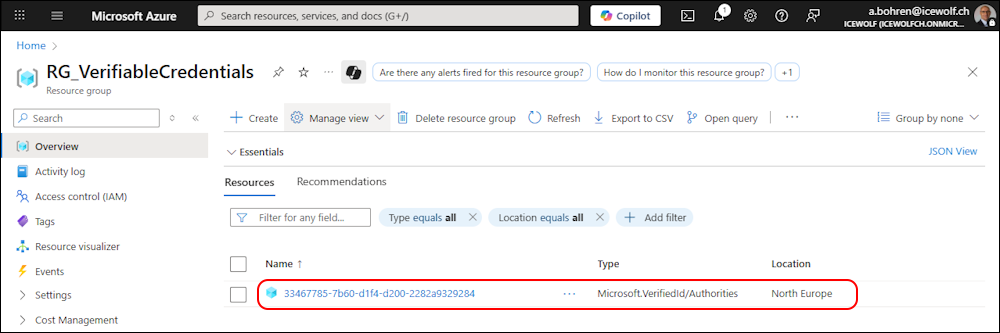
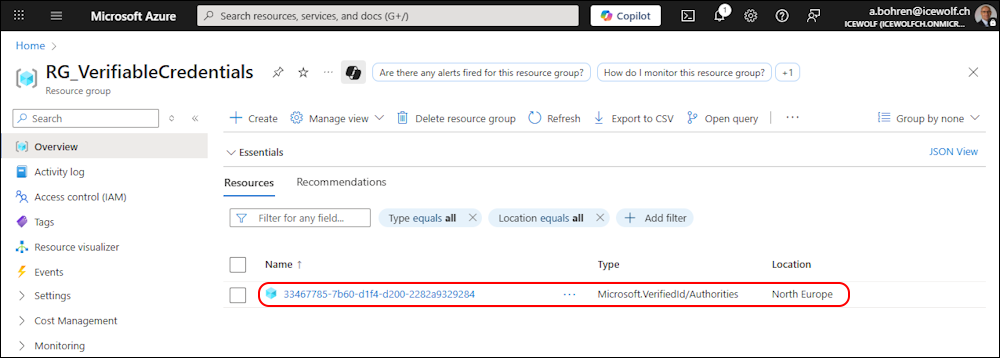
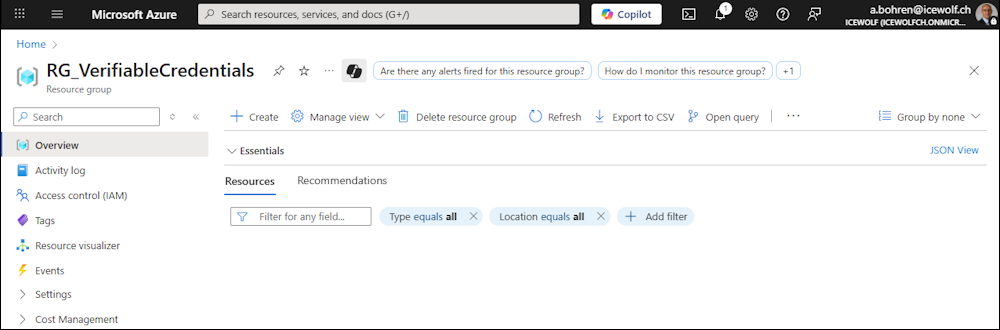
In the Azure Portal in the Resource Grooup we need to enable “Show hidden types”
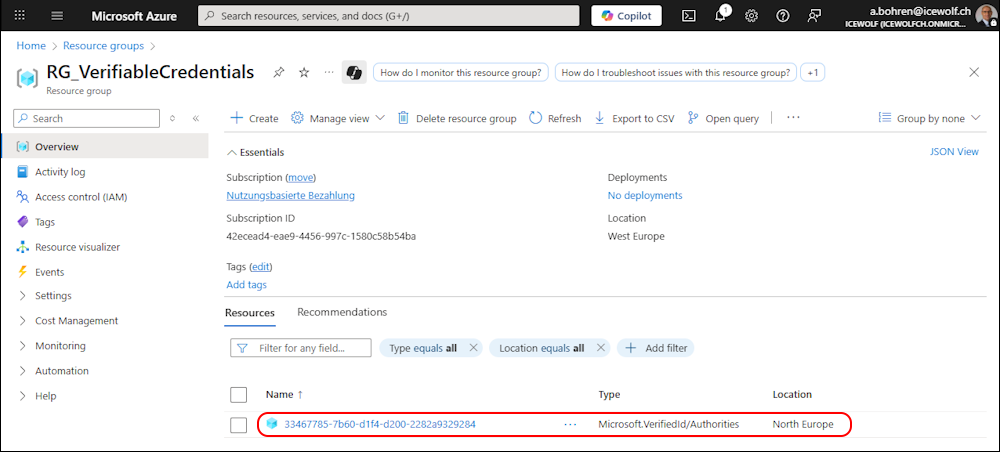
Now we can see an Object with the Authority ID - i think that’s just an Object that is used for adding the Cost.
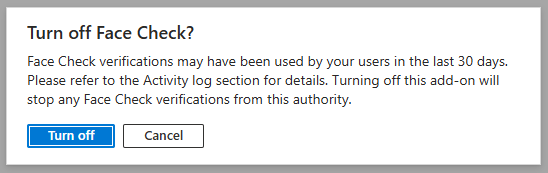
If you click on “Details” you can also “Turn off” Face check
It will ask again
Face check is disabled again
PowerShell
I have an Entra Application that has Delegated permissions to the “Verifiable Credentials Service Admin 6a8b4b39-c021-437c-b060-5a14a3fd65f3” and the “full_access” Permission.
For Delegated Permissions you need one of the following Entra Roles
- Global Administrator
- Authentication policy administrator
- Global Reader
###############################################################################
# PSMSALNet (Delegate Permission WAM)
###############################################################################
#Install-Module PSMSALNet
#Import-Module PSMSALNet
$TenantId = "46bbad84-29f0-4e03-8d34-f6841a5071ad"
$AppID = "da2e568b-3058-48f5-9684-a0116a86656e" # IcewolfVerifiedCredential
$CustomResource = "6a8b4b39-c021-437c-b060-5a14a3fd65f3"
$RedirectURI = "ms-appx-web://microsoft.aad.brokerplugin/$AppID"
$Token = Get-EntraToken -WAMFlow -ClientId $AppID -TenantId $TenantId -RedirectUri $RedirectURI -Resource Custom -CustomResource $CustomResource -Permissions "full_access"
$AccessToken = $token.AccessToken
#View AccessToken
Get-JWTDetails -token $AccessToken
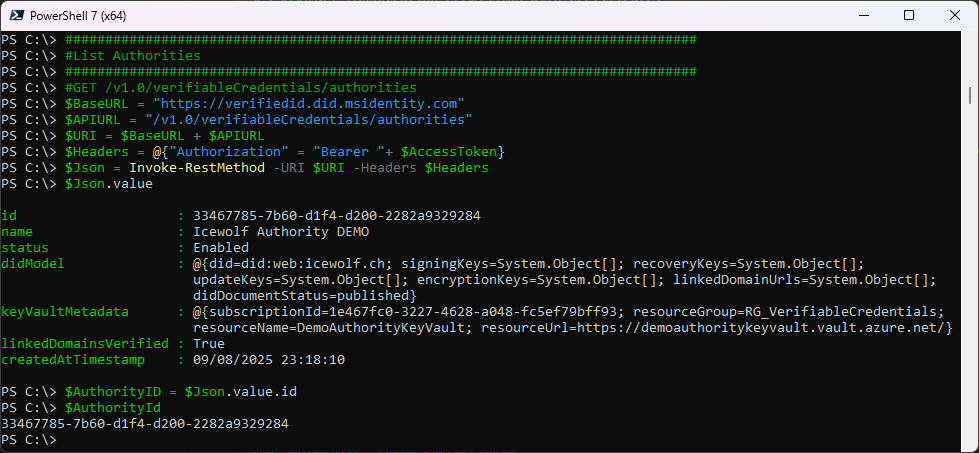
Let’s list the Verified Authorities
###############################################################################
#List Authorities
###############################################################################
#GET /v1.0/verifiableCredentials/authorities
$BaseURL = "https://verifiedid.did.msidentity.com"
$APIURL = "/v1.0/verifiableCredentials/authorities"
$URI = $BaseURL + $APIURL
$Headers = @{"Authorization" = "Bearer "+ $AccessToken}
$Json = Invoke-RestMethod -URI $URI -Headers $Headers
$Json.value
$AuthorityID = $Json.value.id
$AuthorityId
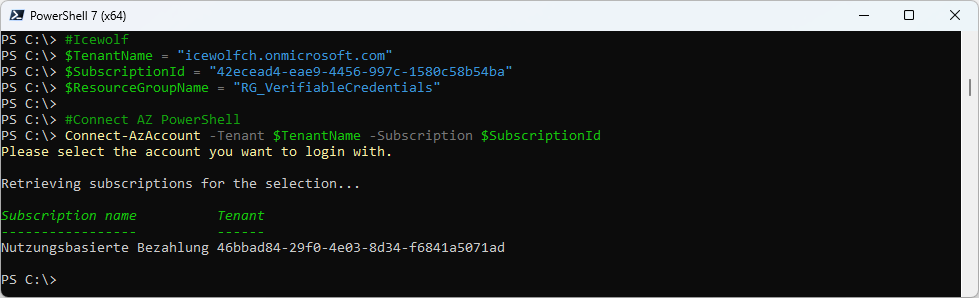
Login with AZ PowerShell
###############################################################################
# AZ PowerShell
###############################################################################
#Serveralive
$TenantName = "serveralive.onmicrosoft.com"
$SubscriptionId = "176d5a47-5c8c-4b9d-929c-3e2a1cb9d180"
$ResourceGroupName = "VerifiedID"
#Icewolf
$TenantName = "icewolfch.onmicrosoft.com"
$SubscriptionId = "42ecead4-eae9-4456-997c-1580c58b54ba"
$ResourceGroupName = "RG_VerifiableCredentials"
#Connect AZ PowerShell
Connect-AzAccount -Tenant $TenantName -Subscription $SubscriptionId
Check if the Microsoft.VerifiedId Resource Provider is installed
#Get AZ Resource Provider
Get-AzResourceProvider -ProviderNamespace Microsoft.VerifiedId
#Register AZ Resource Provider
Register-AzResourceProvider -ProviderNamespace Microsoft.VerifiedId
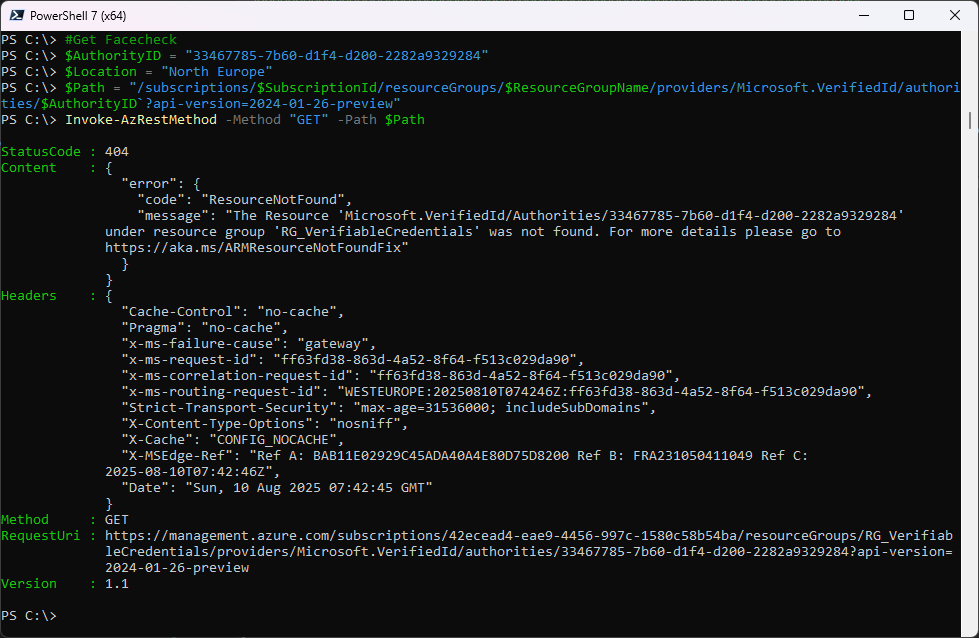
Let’s check if Face Check is enabled - you can see the 404 Resource not found in the Return Values
#Get Facecheck
$AuthorityID = "33467785-7b60-d1f4-d200-2282a9329284"
$Location = "North Europe"
$Path = "/subscriptions/$SubscriptionId/resourceGroups/$ResourceGroupName/providers/Microsoft.VerifiedId/authorities/$AuthorityID`?api-version=2024-01-26-preview"
Invoke-AzRestMethod -Method "GET" -Path $Path
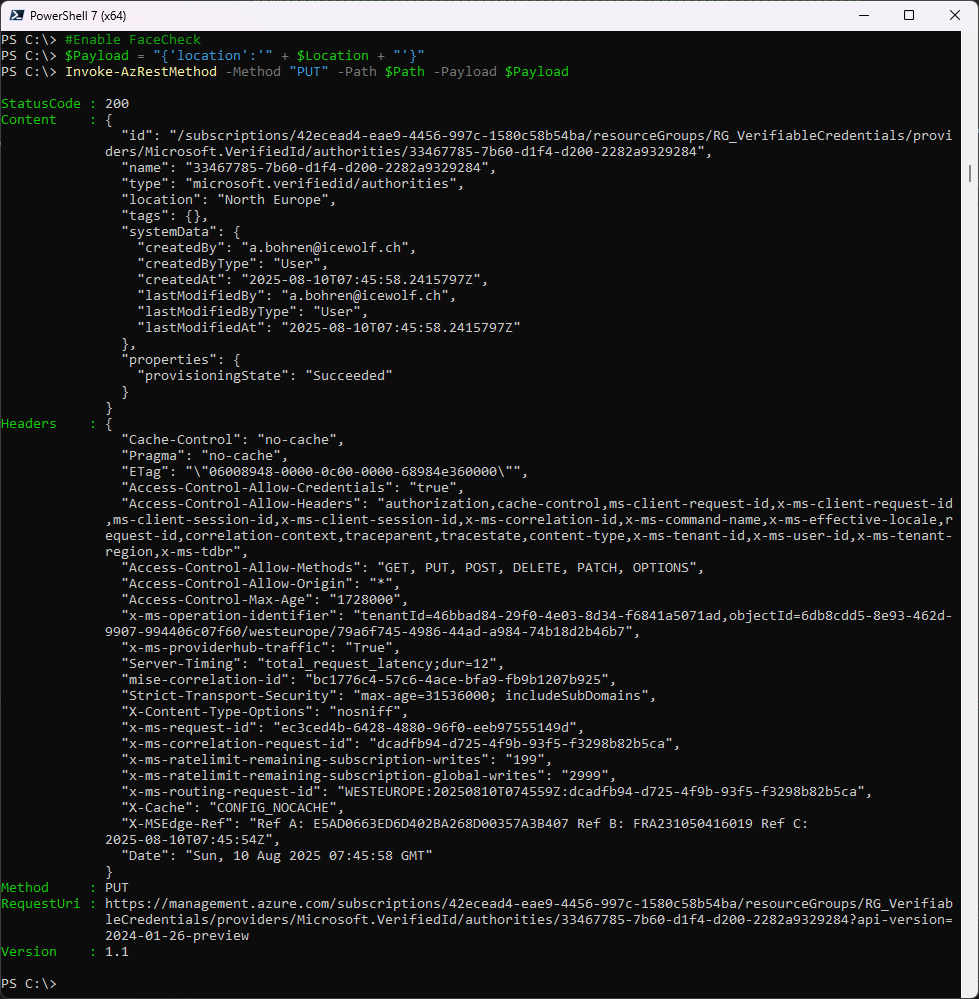
Let’s enable Face Check with a PUT
#Enable FaceCheck
$Payload = "{'location':'" + $Location + "'}"
Invoke-AzRestMethod -Method "PUT" -Path $Path -Payload $Payload
As you can see in the Entra Admin Center Face Check has been enabled
And the Object has been created in the Azure Resource Group
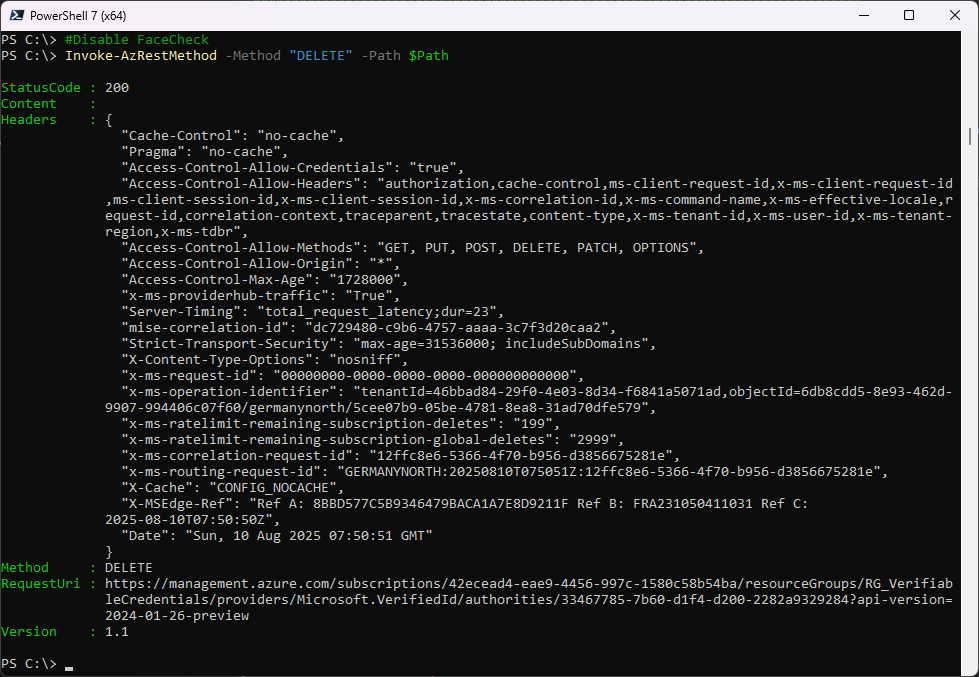
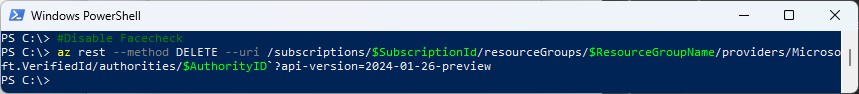
Let’s disable Face Check with a DELETE Method
#Disable FaceCheck
Invoke-AzRestMethod -Method "DELETE" -Path $Path
Face Check has been disabled in the Entra Admin Center
The Resource has been deleted in the Azure Resource Group
AZ CLI
You can also use the AZ CLI to enable Face Check
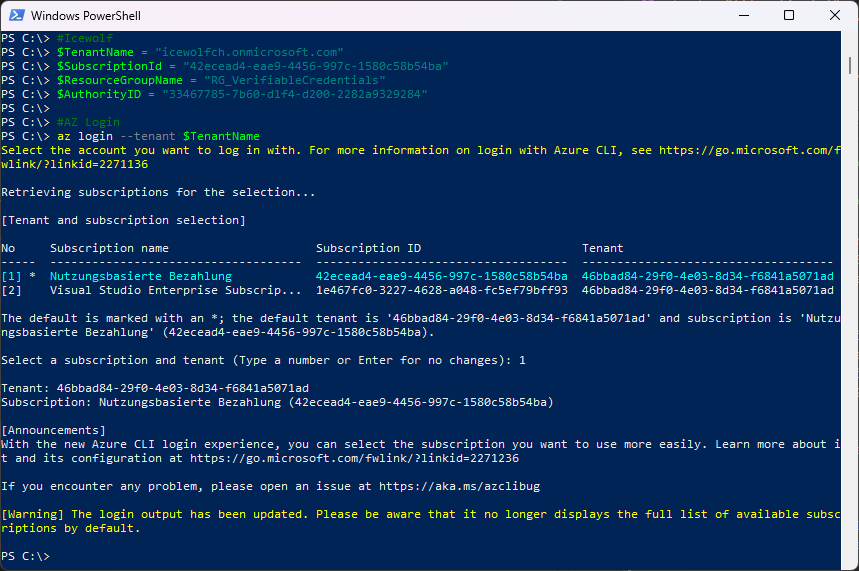
Let’s login with AZ CLI
###############################################################################
# AZ CLI
###############################################################################
#Serveralive
$TenantName = "serveralive.onmicrosoft.com"
$SubscriptionId = "176d5a47-5c8c-4b9d-929c-3e2a1cb9d180"
$ResourceGroupName = "VerifiedID"
$AuthorityID = "33467785-7b60-d1f4-d200-2282a9329284"
#Icewolf
$TenantName = "icewolfch.onmicrosoft.com"
$SubscriptionId = "42ecead4-eae9-4456-997c-1580c58b54ba"
$ResourceGroupName = "RG_VerifiableCredentials"
$AuthorityID = "33467785-7b60-d1f4-d200-2282a9329284"
#AZ Login
az login --tenant $TenantName
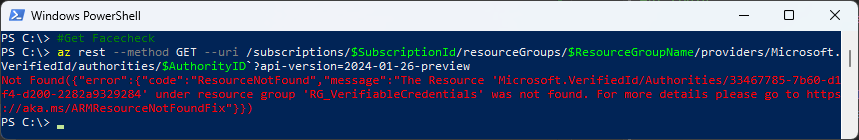
Get Facecheck - you get a ResourceNotFound error
#Get Facecheck
az rest --method GET --uri /subscriptions/$SubscriptionId/resourceGroups/$ResourceGroupName/providers/Microsoft.VerifiedId/authorities/$AuthorityID`?api-version=2024-01-26-preview
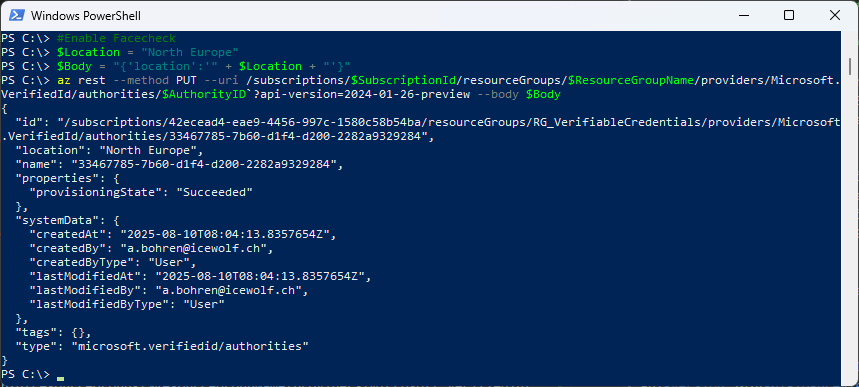
Let’s enable Face Check
#Enable Facecheck
$Location = "North Europe"
$Body = "{'location':'" + $Location + "'}"
az rest --method PUT --uri /subscriptions/$SubscriptionId/resourceGroups/$ResourceGroupName/providers/Microsoft.VerifiedId/authorities/$AuthorityID`?api-version=2024-01-26-preview --body $Body
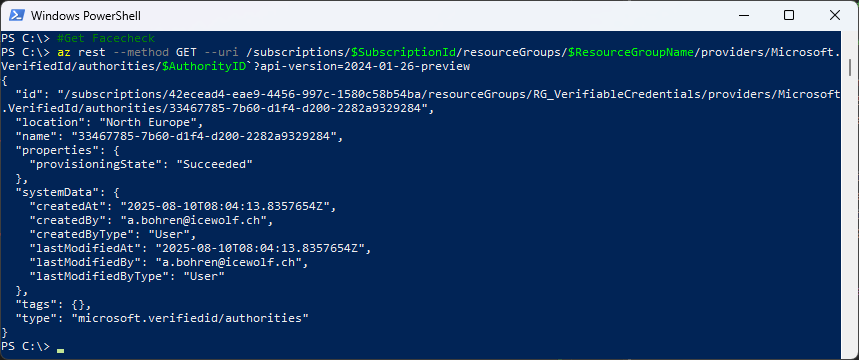
Again Get Facecheck - this time we get the resource
#Get Facecheck
az rest --method GET --uri /subscriptions/$SubscriptionId/resourceGroups/$ResourceGroupName/providers/Microsoft.VerifiedId/authorities/$AuthorityID`?api-version=2024-01-26-preview
Face Check is enabled in Entra Admin Center
The Object is created in Azure Resource Group
Let’s disable Face Check
#Disable Facecheck
az rest --method DELETE --uri /subscriptions/$SubscriptionId/resourceGroups/$ResourceGroupName/providers/Microsoft.VerifiedId/authorities/$AuthorityID`?api-version=2024-01-26-preview
Face Check is disabled in Entra Admin Center
No Resource in Azure Resource Group
Test with Sample App
Microsoft has provided an App for testing Face Check
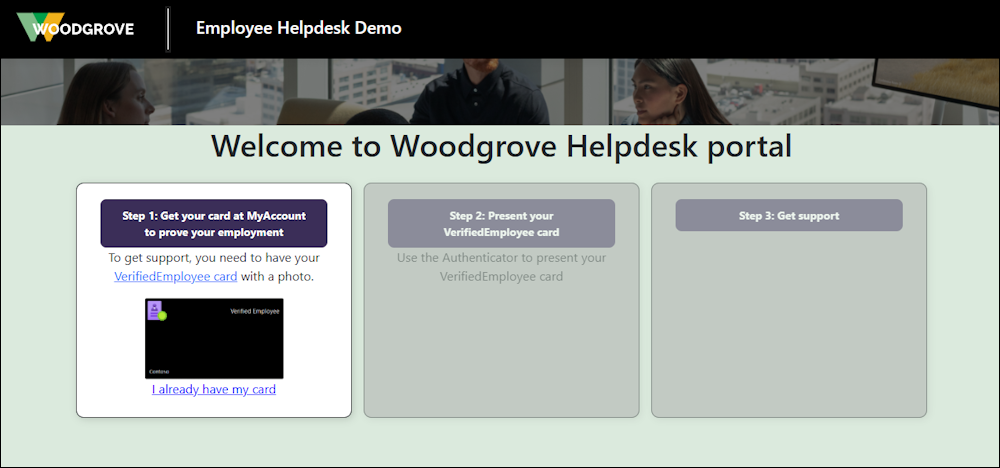
https://woodgrovehelpdesk.azurewebsites.net/
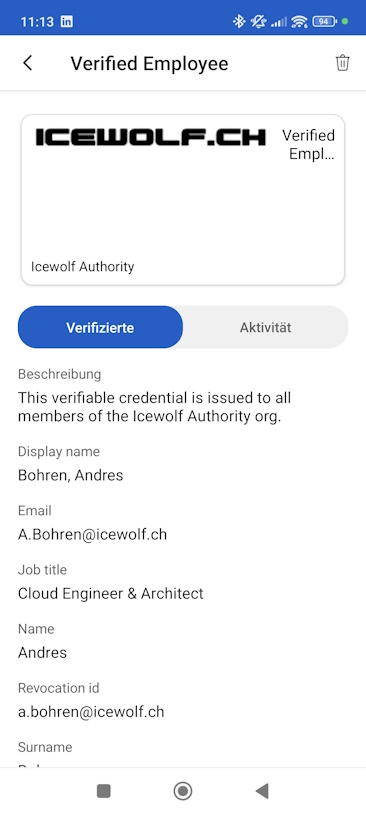
I have already issued a Verified ID in my Authenticator App under My Account. So i click on “I already have my card”
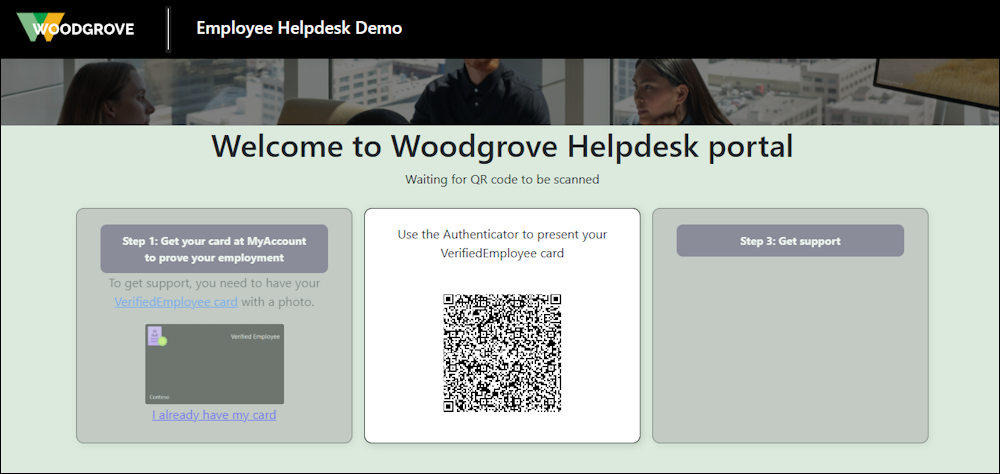
A QR Code is generated
I scan that with the Authenticator App
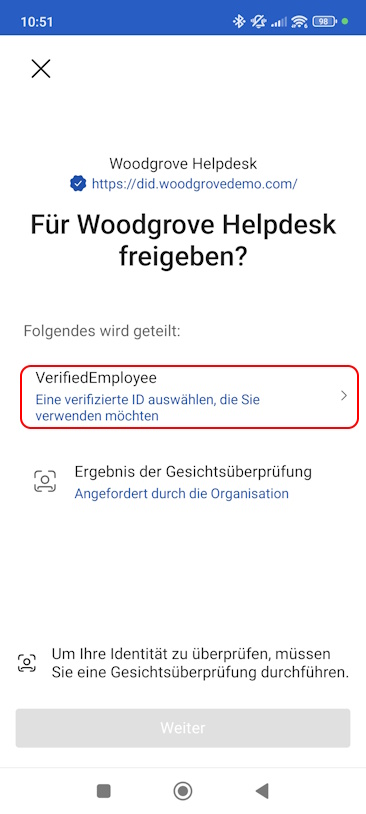
I have to select my Verified Id
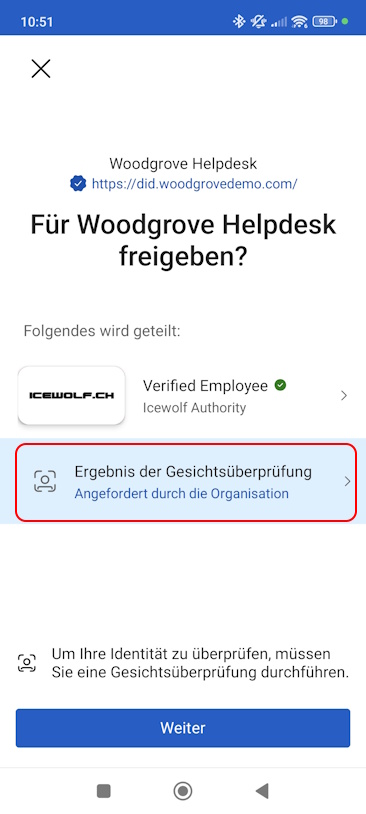
Select Verified ID
Run Face Check
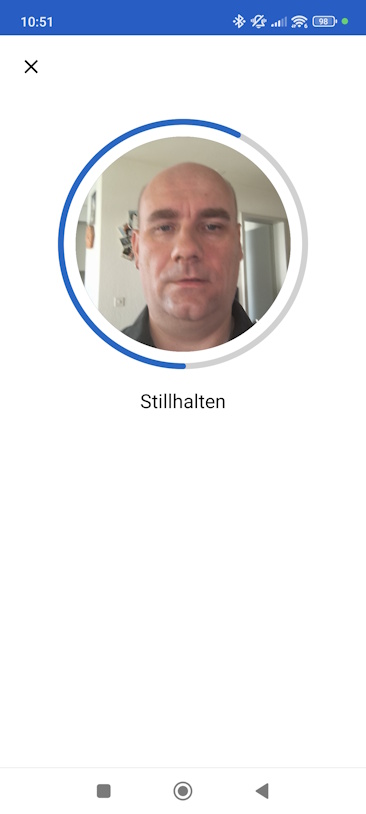
You need to look into the Front Camera of your Mobile Phone
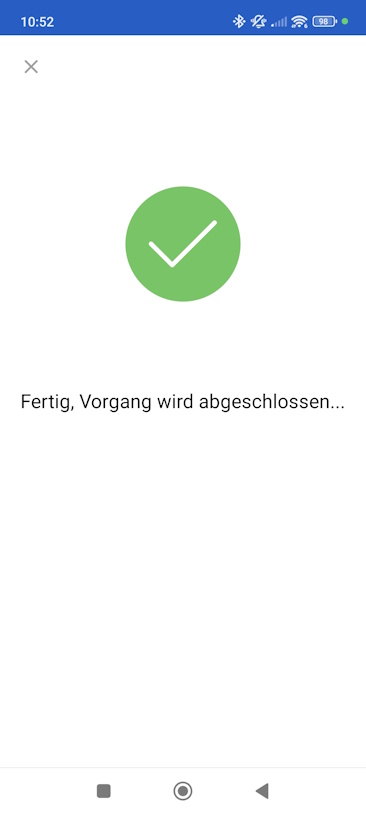
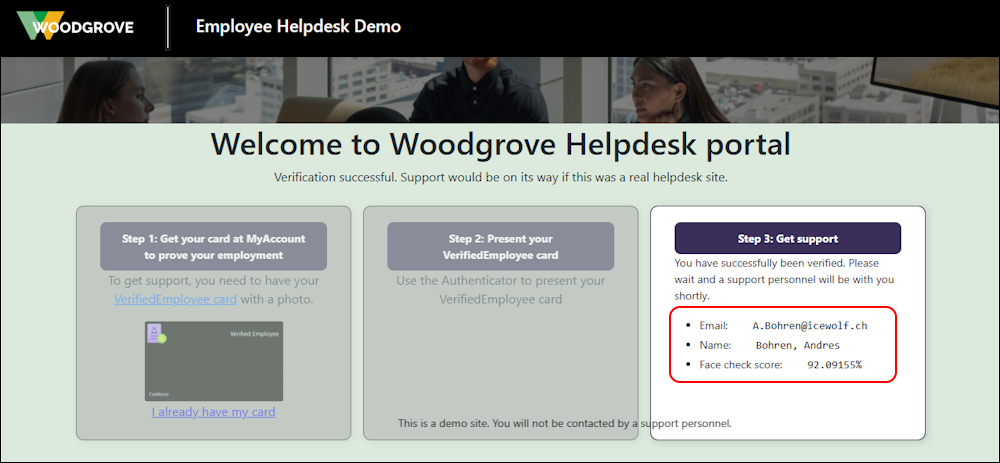
Face Check successful
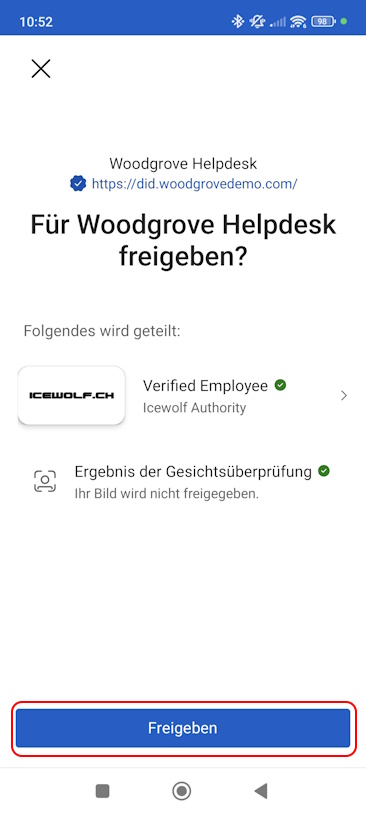
Now we can send that Information
On the Website i can now see some of the Information of my Verified ID and the Face Check Score of about 92%
Additional Tests
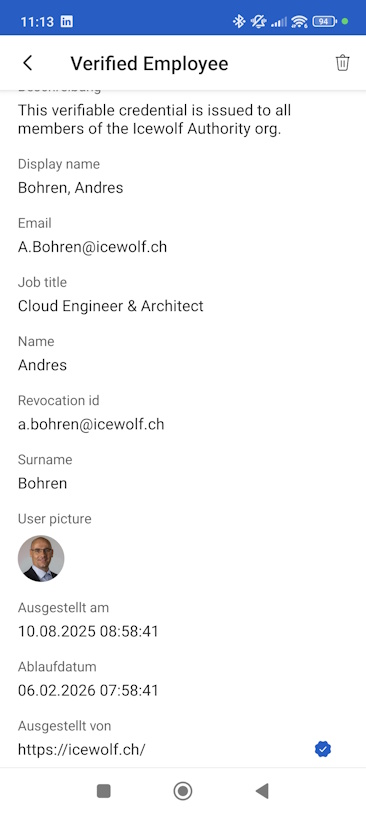
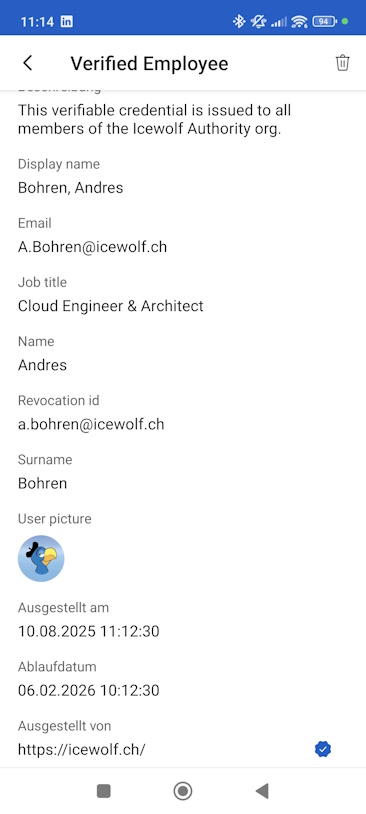
As you can see the Picture is part of the Verified ID. It is generated with the Profile Picture at the Time the Verified ID is issued
I did change my Profile Picture - issued another Verified ID and tried Face Check - that did obviously not match
Summary
I’ve shown you how to enable / disable Face Check for Verified ID in three diffrent ways:
- Entra Admin Center
- AZ PowerShell
- AZ CLI
As you can see the Check for Face ID is executed against the Picture in the Verified Id. The Picture is taken from the Users Profile Picture at the Time of issuance of the Verified ID. Make sure you have control over the Profile Picture - otherwise the Face Check will fail.
Regards
Andres Bohren