Install Exchange 2019 on Windows Server 2022

Hi All,
Recently Microsoft has published the - Exchange Server Roadmap Update on the Exchange Team Blog.
Changes to support Exchange Server Subscription Edition
- Removal of support for co-existence with Exchange 2013
- Support for new product keys (Hybrid servers which will continue to receive a free license and product key via the Hybrid Configuration Wizard)
- Support for Windows Server 2025 - CU15 will introduce support for Windows Server 2025 (when the OS reaches GA later this year)
Upgrading to Exchange Server SE from Previous Versions
- In-place upgrade (From Exchange 2019)
- Legacy upgrade (Classic Swing Upgrade to new Exchange Infrastructure)
Install Exchange 2019 on Windows Server 2022
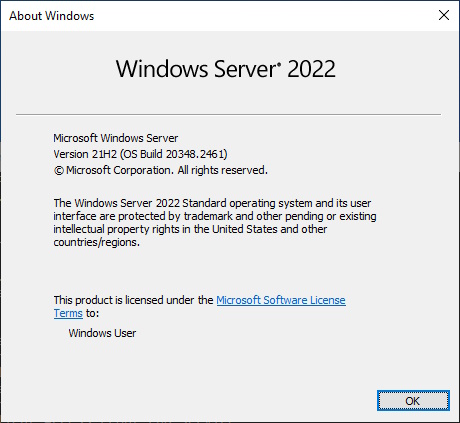
Time to move on and prepare. Until now in the Production only a single Exchange 2016 Server exists. The Mainsteam Support for Windows Server 2019 has ended on 9 Jan 2024 i decidet to go with Windows Server 2022.
I’ve downloaded Windows Server 2022 Evaluation Version of the ISO for and installed it
With the following command i changed the version with my Product Key
dism /online /set-edition:serverstandard /productkey:XXXXX-XXXXX-XXXXX-XXXXX-XXXXX /accepteula
Make sure, you have all the Updates for the Operation System installed before proceeding
Excange 2019 Prerequisites
The Exchange Server prerequisites are well documented
- .NET Framework 4.8.1
- Visual C++ Redistributable Package for Visual Studio 2012
- Visual C++ Redistributable Package for Visual Studio 2013
- Microsoft Unified Communications Managed API 4.0, Core Runtime 64-bit
- URL-Rewrite
Install .NET Framework 4.8.1
Visual C++ Redistributable 2012
Visual C++ Redistributable 2013
Unified Communications Managed API 4.0
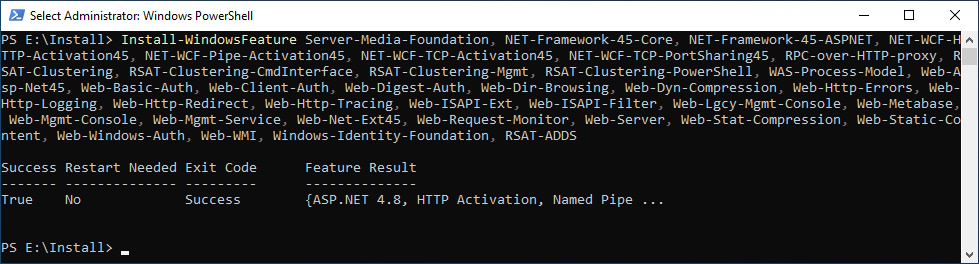
Windows Features
Install-WindowsFeature Server-Media-Foundation, NET-Framework-45-Core, NET-Framework-45-ASPNET, NET-WCF-HTTP-Activation45, NET-WCF-Pipe-Activation45, NET-WCF-TCP-Activation45, NET-WCF-TCP-PortSharing45, RPC-over-HTTP-proxy, RSAT-Clustering, RSAT-Clustering-CmdInterface, RSAT-Clustering-Mgmt, RSAT-Clustering-PowerShell, WAS-Process-Model, Web-Asp-Net45, Web-Basic-Auth, Web-Client-Auth, Web-Digest-Auth, Web-Dir-Browsing, Web-Dyn-Compression, Web-Http-Errors, Web-Http-Logging, Web-Http-Redirect, Web-Http-Tracing, Web-ISAPI-Ext, Web-ISAPI-Filter, Web-Lgcy-Mgmt-Console, Web-Metabase, Web-Mgmt-Console, Web-Mgmt-Service, Web-Net-Ext45, Web-Request-Monitor, Web-Server, Web-Stat-Compression, Web-Static-Content, Web-Windows-Auth, Web-WMI, Windows-Identity-Foundation, RSAT-ADDS
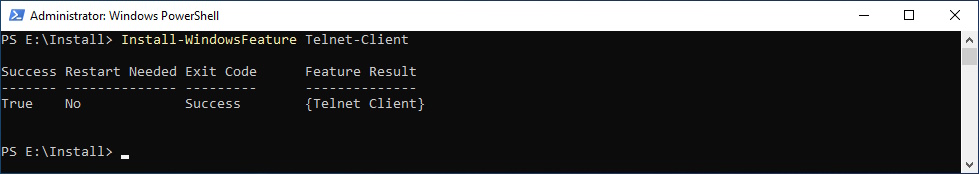
It’s always nice to have the Telnet Client on a Exchange Server
Install-WindowsFeature Telnet-Client
Now that IIS installed we can install URL Rewrite
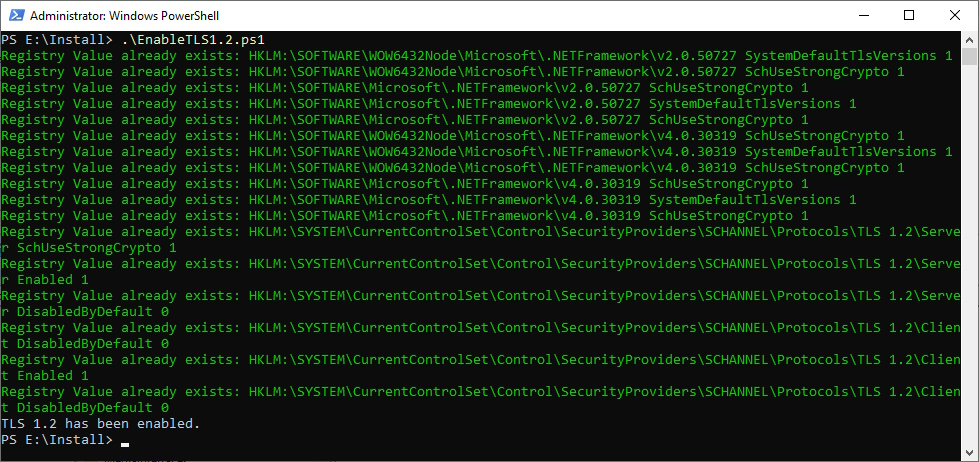
Make sure the TLS Settings are set to TLS 1.2
- Github EnableTLS1.2.ps1
###############################################################################
# Enable TLS 1.2
###############################################################################
<#
Transport Layer Security (TLS) best practices with the .NET Framework
https://learn.microsoft.com/en-us/dotnet/framework/network-programming/tls
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727]
"SystemDefaultTlsVersions"=dword:00000001
"SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319]
"SystemDefaultTlsVersions"=dword:00000001
"SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v2.0.50727]
"SystemDefaultTlsVersions"=dword:00000001
"SchUseStrongCrypto"=dword:00000001
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\.NETFramework\v4.0.30319]
"SystemDefaultTlsVersions"=dword:00000001
"SchUseStrongCrypto"=dword:00000001
[HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server]
"Enabled"==dword:00000001
"DisabledByDefault"=dword:00000000
[HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client]
"Enabled"==dword:00000001
"DisabledByDefault"=dword:00000000
#>
$RegKey = "HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v2.0.50727"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
}
$Property = "SystemDefaultTlsVersions"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SchUseStrongCrypto"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$RegKey = "HKLM:\SOFTWARE\Microsoft\.NETFramework\v2.0.50727"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SystemDefaultTlsVersions"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SchUseStrongCrypto"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$RegKey = "HKLM:\SOFTWARE\WOW6432Node\Microsoft\.NETFramework\v4.0.30319"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SystemDefaultTlsVersions"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SchUseStrongCrypto"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$RegKey = "HKLM:\SOFTWARE\Microsoft\.NETFramework\v4.0.30319"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SystemDefaultTlsVersions"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "SchUseStrongCrypto"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$RegKey = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Server"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "Enabled"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "DisabledByDefault"
$PropertyValue = "0"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$RegKey = "HKLM:\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.2\Client"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "Enabled"
$PropertyValue = "1"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
$Property = "DisabledByDefault"
$PropertyValue = "0"
$Item = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($Item.$Property -ne $PropertyValue)
{
Write-Host "Create Registry Value: $RegKey $Property $PropertyValue" -ForegroundColor Yellow
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'DWord' -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey $Property $PropertyValue" -ForegroundColor Green
}
Write-Host 'TLS 1.2 has been enabled.'
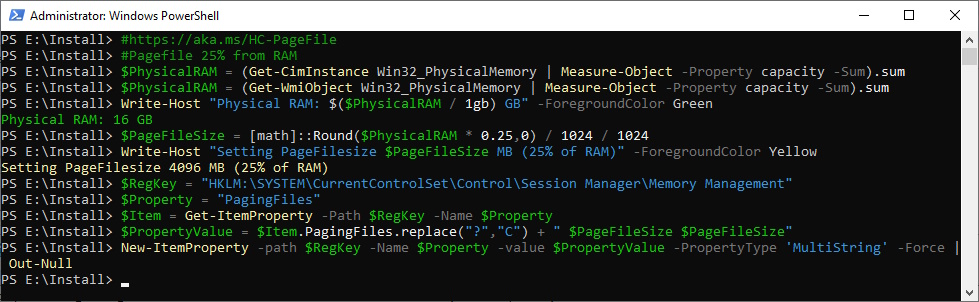
Set Pagefile to 25% of Physical RAM
Note: It’s recommended to have 128 GB of RAM for a Production Server
Pagefile
###############################################################################
#https://aka.ms/HC-PageFile
#Pagefile 25% from RAM
###############################################################################
$PhysicalRAM = (Get-CimInstance Win32_PhysicalMemory | Measure-Object -Property capacity -Sum).sum
$PhysicalRAM = (Get-WmiObject Win32_PhysicalMemory | Measure-Object -Property capacity -Sum).sum
Write-Host "Physical RAM: $($PhysicalRAM / 1gb) GB" -ForegroundColor Green
$PageFileSize = [math]::Round($PhysicalRAM * 0.25,0) / 1024 / 1024
Write-Host "Setting PageFilesize $PageFileSize MB (25% of RAM)" -ForegroundColor Yellow
$RegKey = "HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management"
$Property = "PagingFiles"
$Item = Get-ItemProperty -Path $RegKey -Name $Property
$PropertyValue = $Item.PagingFiles.replace("?","C") + " $PageFileSize $PageFileSize"
New-ItemProperty -path $RegKey -Name $Property -value $PropertyValue -PropertyType 'MultiString' -Force | Out-Null
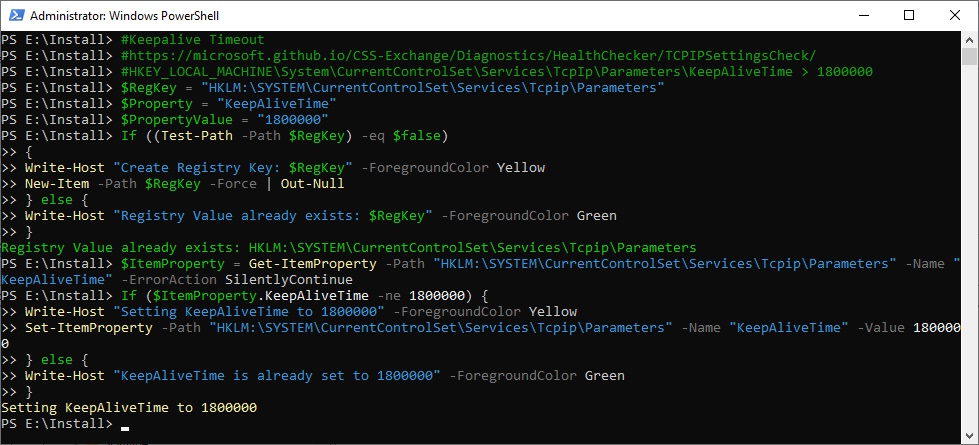
Keepalive Timeout
Set Keepalive TCP Timeout
###############################################################################
#Keepalive TCP Timeout
#https://microsoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/TCPIPSettingsCheck/
#HKEY_LOCAL_MACHINE\System\CurrentControlSet\Services\TcpIp\Parameters\KeepAliveTime > 1800000
###############################################################################
$RegKey = "HKLM:\SYSTEM\CurrentControlSet\Services\Tcpip\Parameters"
$Property = "KeepAliveTime"
$PropertyValue = "1800000"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey" -ForegroundColor Green
}
$ItemProperty = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($ItemProperty.KeepAliveTime -ne 1800000) {
Write-Host "Setting $Property to $PropertyValue" -ForegroundColor Yellow
Set-ItemProperty -Path $RegKey -Name $Property -Value $PropertyValue
} else {
Write-Host "$Property is already set to $PropertyValue" -ForegroundColor Green
}
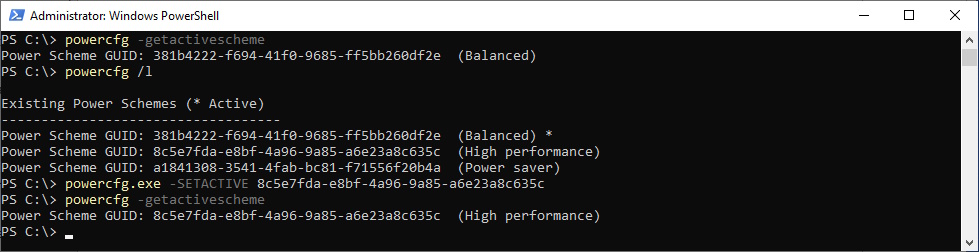
Power Plan
Set Power Plan to “High performance”
###############################################################################
# Set Power Plan to "High performance"
###############################################################################
powercfg -getactivescheme
powercfg /l
powercfg.exe -SETACTIVE 8c5e7fda-e8bf-4a96-9a85-a6e23a8c635c
powercfg -getactivescheme
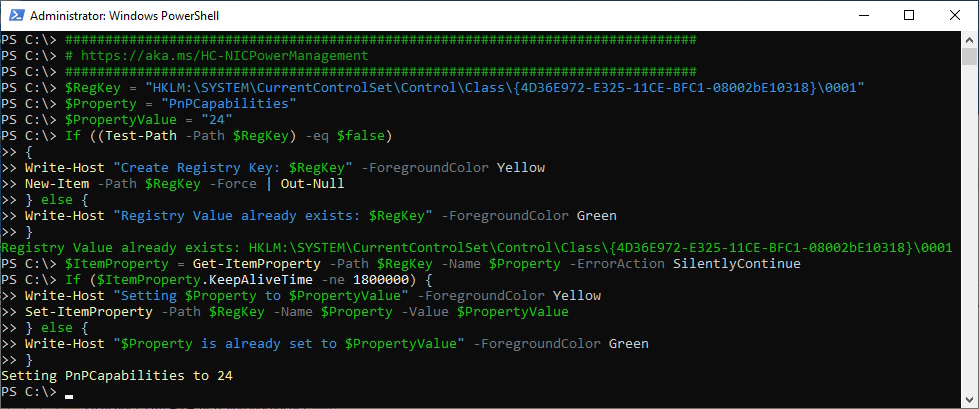
NIC PowerManagement
Disable NIC PowerManagement
###############################################################################
# https://aka.ms/HC-NICPowerManagement
###############################################################################
$RegKey = "HKLM:\SYSTEM\CurrentControlSet\Control\Class\{4D36E972-E325-11CE-BFC1-08002bE10318}\0001"
$Property = "PnPCapabilities"
$PropertyValue = "24"
If ((Test-Path -Path $RegKey) -eq $false)
{
Write-Host "Create Registry Key: $RegKey" -ForegroundColor Yellow
New-Item -Path $RegKey -Force | Out-Null
} else {
Write-Host "Registry Value already exists: $RegKey" -ForegroundColor Green
}
$ItemProperty = Get-ItemProperty -Path $RegKey -Name $Property -ErrorAction SilentlyContinue
If ($ItemProperty.KeepAliveTime -ne 1800000) {
Write-Host "Setting $Property to $PropertyValue" -ForegroundColor Yellow
Set-ItemProperty -Path $RegKey -Name $Property -Value $PropertyValue
} else {
Write-Host "$Property is already set to $PropertyValue" -ForegroundColor Green
}
Pending Reboot
Check for Pending Reboot
- GitHub Script Check-PendingReboot.ps1
.\Check-PendingReboot.ps1
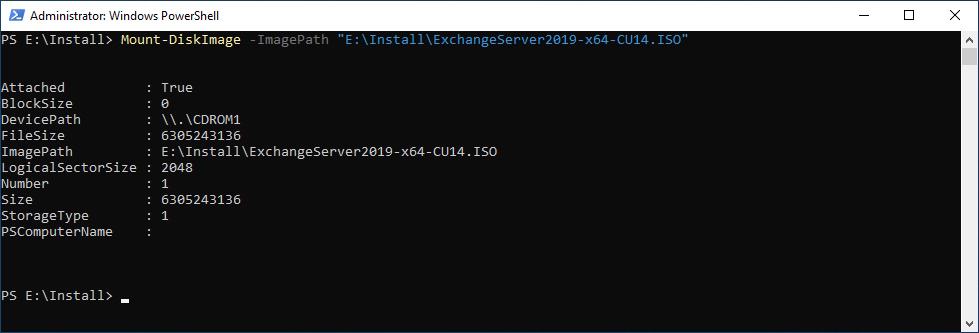
Mount ISO
Mount-DiskImage -ImagePath "E:\Install\ExchangeServer2019-x64-CU14.ISO"
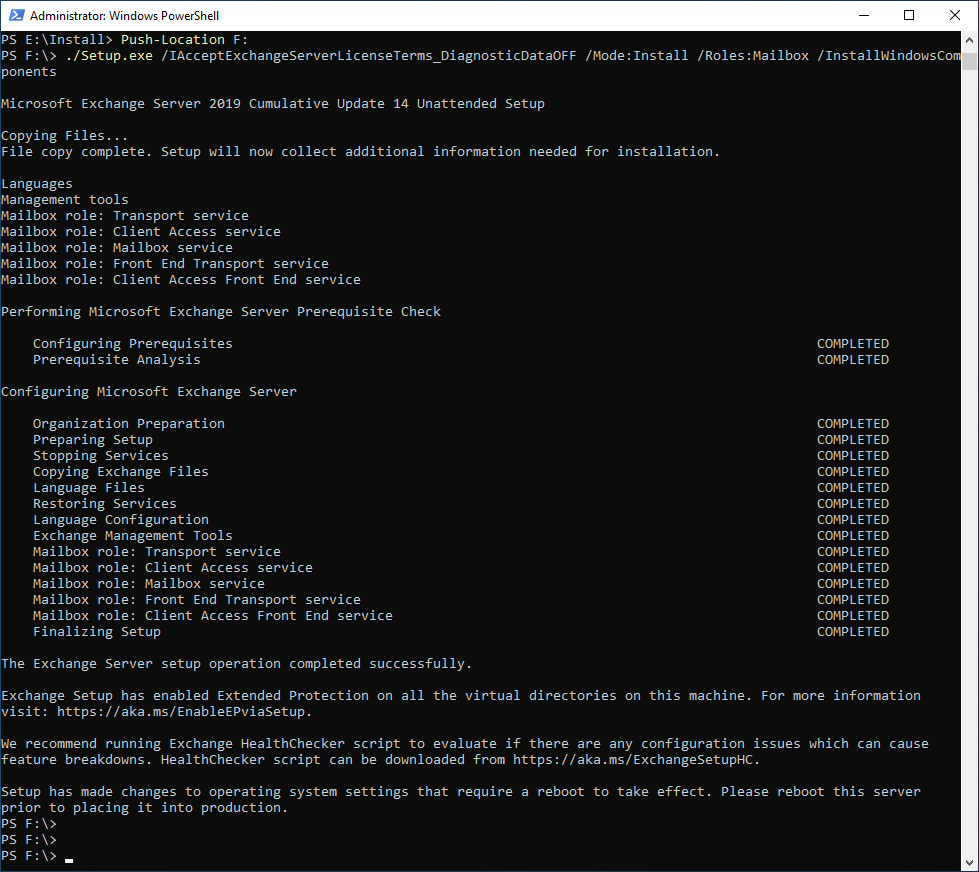
Install latest Exchange 2019 CU
Time to install the latest Exchange Server 2019 Cumulative Update (CU)
#Change Directory
Push-Location F:
#Install Exchange
./Setup.exe /IAcceptExchangeServerLicenseTerms_DiagnosticDataOFF /Mode:Install /Roles:Mailbox /InstallWindowsComponents
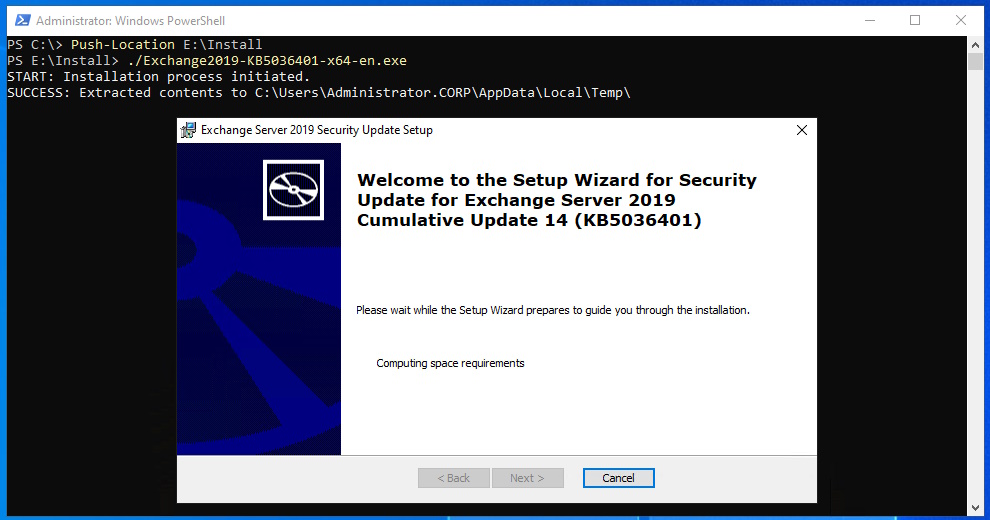
Install latest Exchange Server Security Update
After a Reboot we need to install the latest Security Update
#Security Update
Push-Location E:\Install
./Exchange2019-KB5036401-x64-en.exe
Public Certificate
Install PowerShell Module to request “Let’s Encrypt Certificates”
###############################################################################
#Exchange Public Certificate with Let's Encrypt
###############################################################################
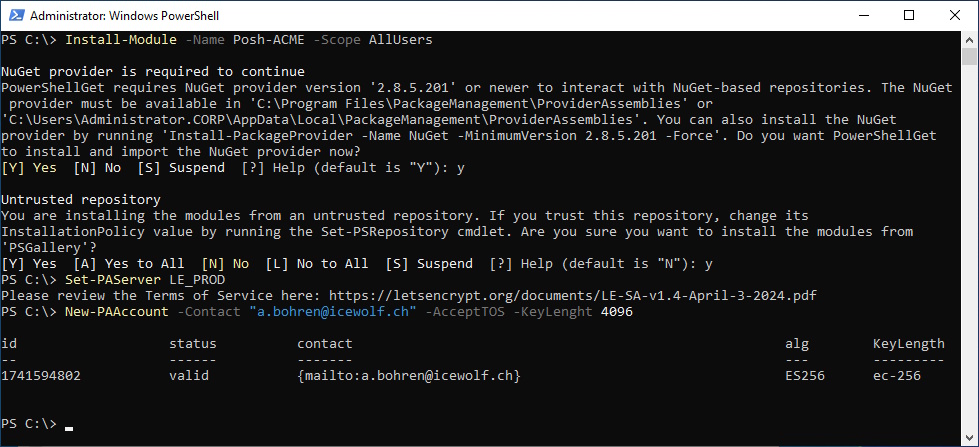
Install-Module -Name Posh-ACME -Scope AllUsers
Set-PAServer LE_PROD
New-PAAccount -Contact "a.bohren@icewolf.ch" -AcceptTOS -KeyLenght 4096
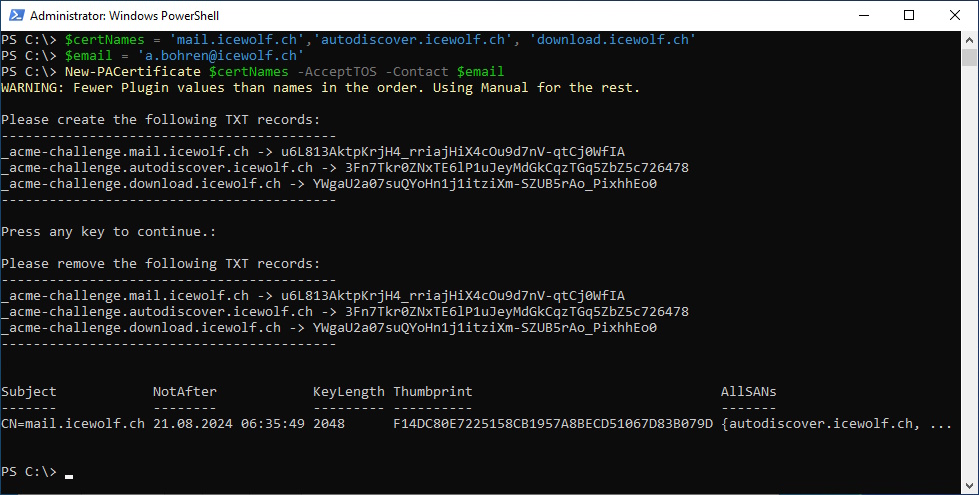
Request “Let’s Encrypt Certificate”
$certNames = 'mail.serveralive.ch','autodiscover.serveralive.ch', 'download.serveralive.ch'
$certNames = 'mail.icewolf.ch','autodiscover.icewolf.ch', 'download.icewolf.ch'
$email = 'a.bohren@icewolf.ch'
New-PACertificate $certNames -AcceptTOS -Contact $email
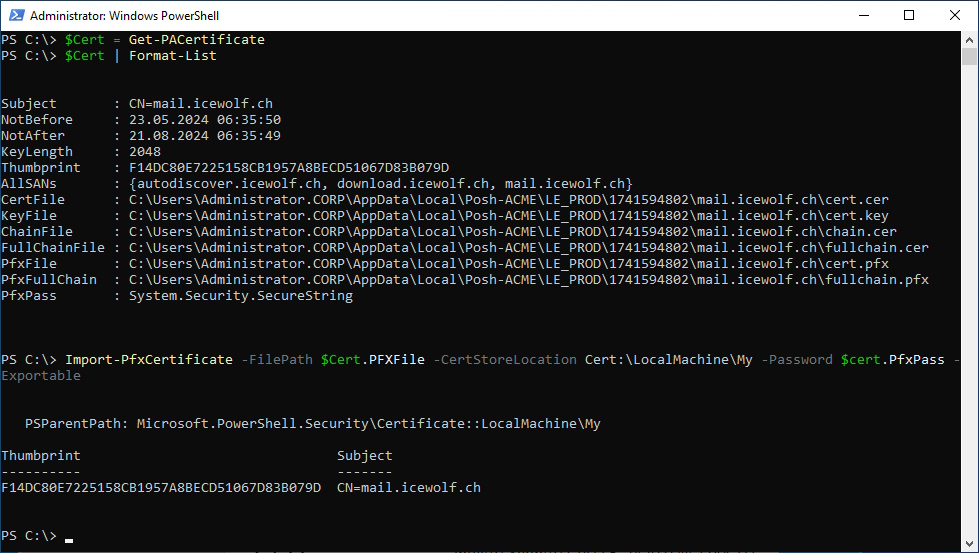
Import Certificate to LocalMachine Cert Store
#Import Certificate
$Cert = Get-PACertificate
$Cert | Format-List
Import-PfxCertificate -FilePath $Cert.PFXFile -CertStoreLocation Cert:\LocalMachine\My -Password $cert.PfxPass -Exportable
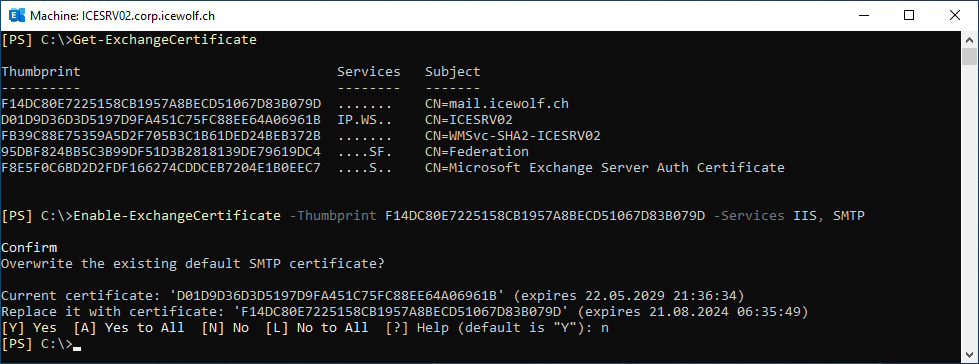
Start Exchange Management Shell and Enable Certificate for IIS and SMTP
#Exchange Certificate
Get-ExchangeCertificate
Enable-ExchangeCertificate -Thumbprint $Thumbprint -Services SMTP,IIS
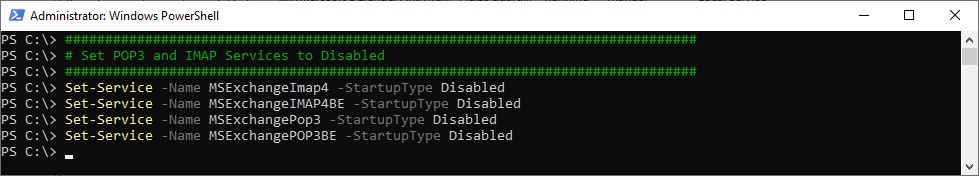
Disable POP3 and IMAP Services
Disable POP3 and IMAP Services (most Companys do not require them anyways - but make sure you don’t use it)
###############################################################################
# Set POP3 and IMAP Services to Disabled
###############################################################################
Set-Service -Name MSExchangeImap4 -StartupType Disabled
Set-Service -Name MSExchangeIMAP4BE -StartupType Disabled
Set-Service -Name MSExchangePop3 -StartupType Disabled
Set-Service -Name MSExchangePOP3BE -StartupType Disabled
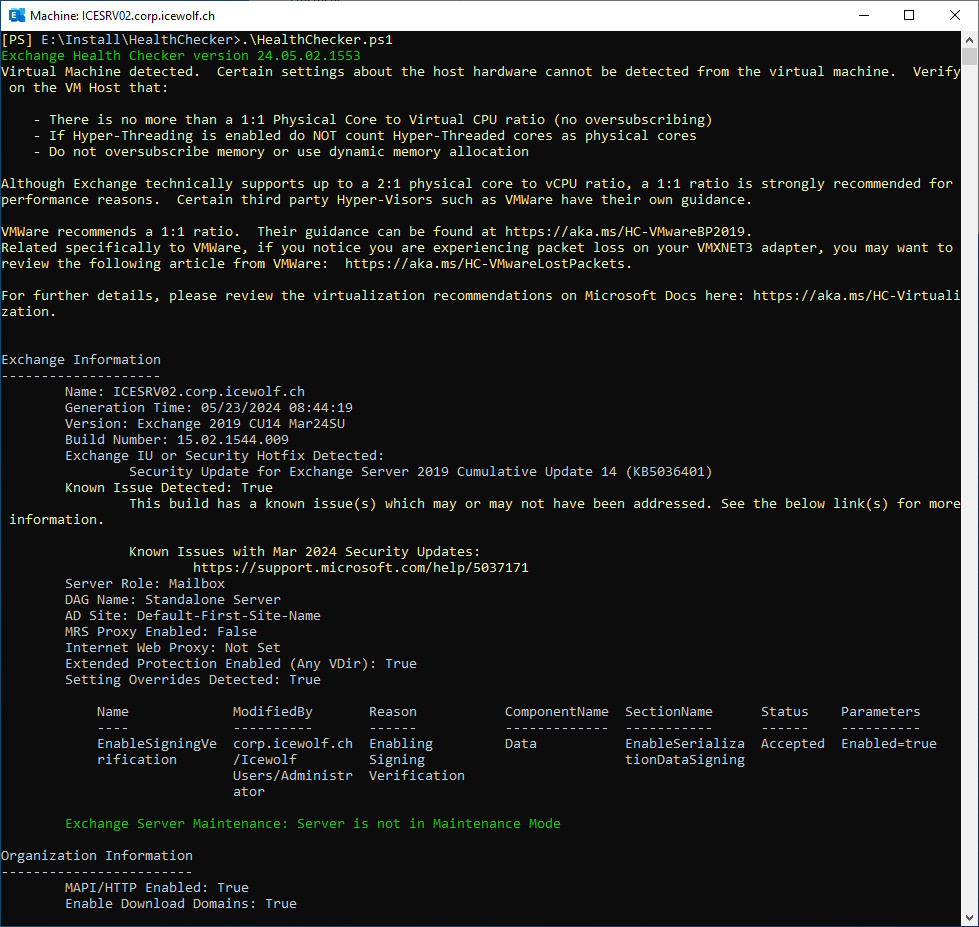
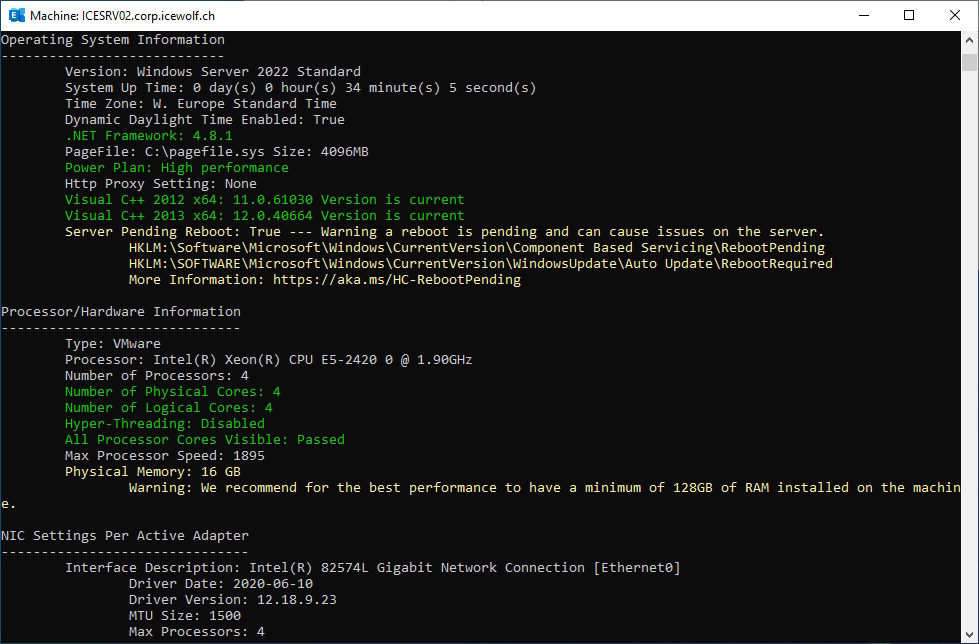
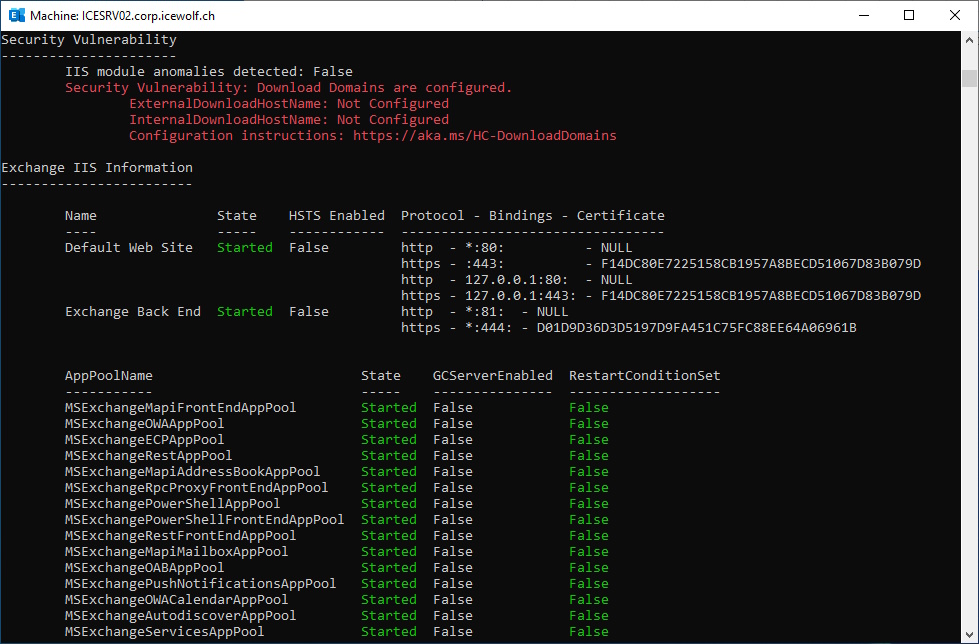
HealthChecker
Run Exchange HealthChecker
###############################################################################
# Health Checker
###############################################################################
#https://microsoft.github.io/CSS-Exchange/Diagnostics/HealthChecker/
#https://github.com/microsoft/CSS-Exchange/releases/latest/download/HealthChecker.ps1
.\HealthChecker.ps1
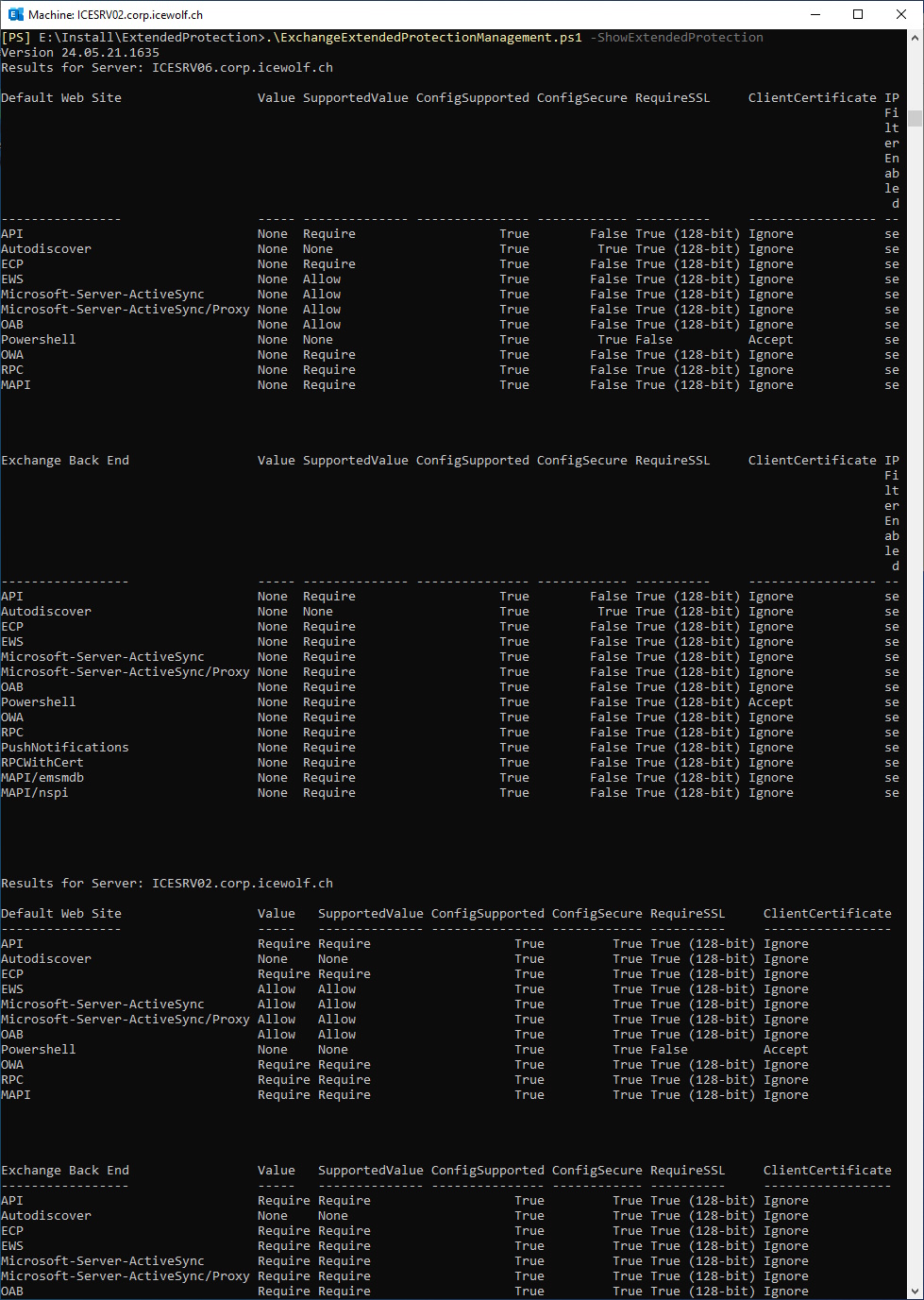
Extended Protection
Review Exchange Extended Protection
###############################################################################
# ExchangeExtendedProtectionManagement
###############################################################################
#https://microsoft.github.io/CSS-Exchange/Security/ExchangeExtendedProtectionManagement/
#https://github.com/microsoft/CSS-Exchange/releases/latest/download/ExchangeExtendedProtectionManagement.ps1
.\ExchangeExtendedProtectionManagement.ps1 -ShowExtendedProtection
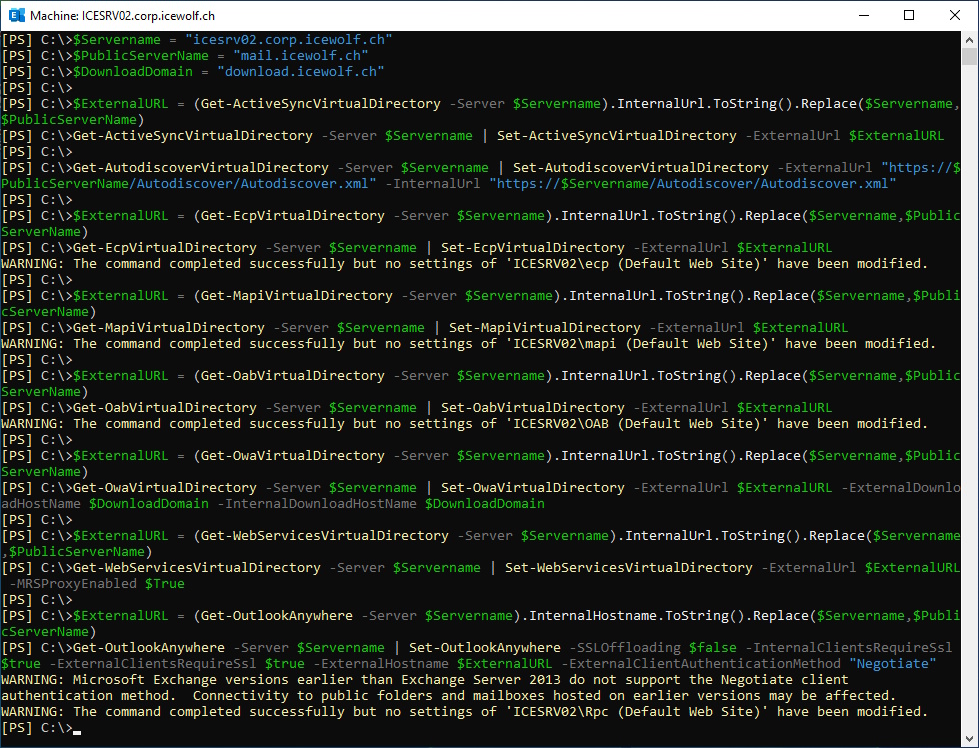
Set External URL
Set ExternalURL of Virtual Directories
###############################################################################
# Set ExternalURL of Virtual Directories
###############################################################################
$Servername = "icesrv02.corp.icewolf.ch"
$PublicServerName = "mail.icewolf.ch"
$DownloadDomain = "download.icewolf.ch"
$ExternalURL = (Get-ActiveSyncVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-ActiveSyncVirtualDirectory -Server $Servername | Set-ActiveSyncVirtualDirectory -ExternalUrl $ExternalURL
Get-AutodiscoverVirtualDirectory -Server $Servername | Set-AutodiscoverVirtualDirectory -ExternalUrl "https://$PublicServerName/Autodiscover/Autodiscover.xml" -InternalUrl "https://$Servername/Autodiscover/Autodiscover.xml"
$ExternalURL = (Get-EcpVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-EcpVirtualDirectory -Server $Servername | Set-EcpVirtualDirectory -ExternalUrl $ExternalURL
$ExternalURL = (Get-MapiVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-MapiVirtualDirectory -Server $Servername | Set-MapiVirtualDirectory -ExternalUrl $ExternalURL
$ExternalURL = (Get-OabVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-OabVirtualDirectory -Server $Servername | Set-OabVirtualDirectory -ExternalUrl $ExternalURL
$ExternalURL = (Get-OwaVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-OwaVirtualDirectory -Server $Servername | Set-OwaVirtualDirectory -ExternalUrl $ExternalURL -ExternalDownloadHostName $DownloadDomain -InternalDownloadHostName $DownloadDomain
$ExternalURL = (Get-WebServicesVirtualDirectory -Server $Servername).InternalUrl.ToString().Replace($Servername,$PublicServerName)
Get-WebServicesVirtualDirectory -Server $Servername | Set-WebServicesVirtualDirectory -ExternalUrl $ExternalURL -MRSProxyEnabled $True
$ExternalURL = (Get-OutlookAnywhere -Server $Servername).InternalHostname.ToString().Replace($Servername,$PublicServerName)
Get-OutlookAnywhere -Server $Servername | Set-OutlookAnywhere -SSLOffloading $false -InternalClientsRequireSsl $true -ExternalClientsRequireSsl $true -ExternalHostname $ExternalURL -ExternalClientAuthenticationMethod "Negotiate"
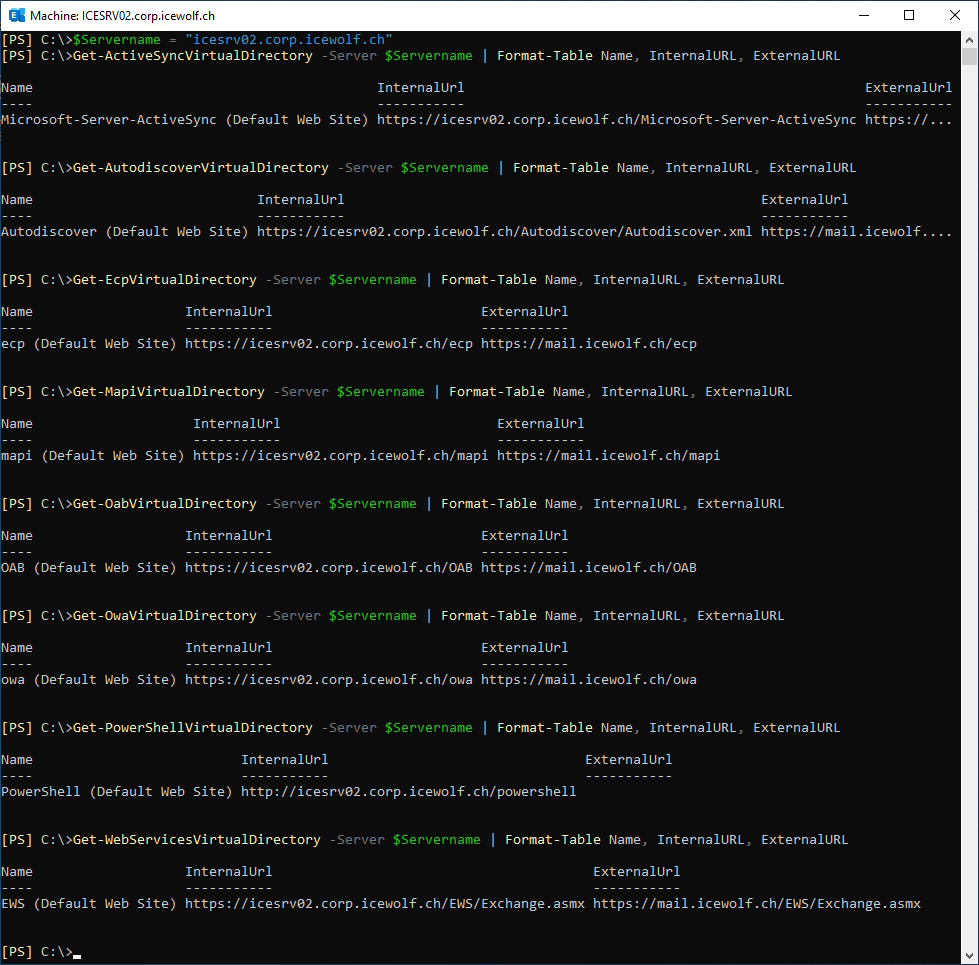
###############################################################################
# Review URL's of Virtual Directories
###############################################################################
$Servername = "icesrv02.corp.icewolf.ch"
Get-ActiveSyncVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-AutodiscoverVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-EcpVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-MapiVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-OabVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-OwaVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-PowerShellVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
Get-WebServicesVirtualDirectory -Server $Servername | Format-Table Name, InternalURL, ExternalURL
License Server
Open Microsoft Edge and browse to https://aka.ms/hybridwizard
There are multiple reasons, why the Hybrid Wizard might not start
- Unable To Install or Launch Exchange HCW
- Exchange Hybrid Configuration Wizard (HCW) > InternetOptions: Downloads > File Downloads > Enable
- Office 365 Hybrid Configuration Wizard can’t start
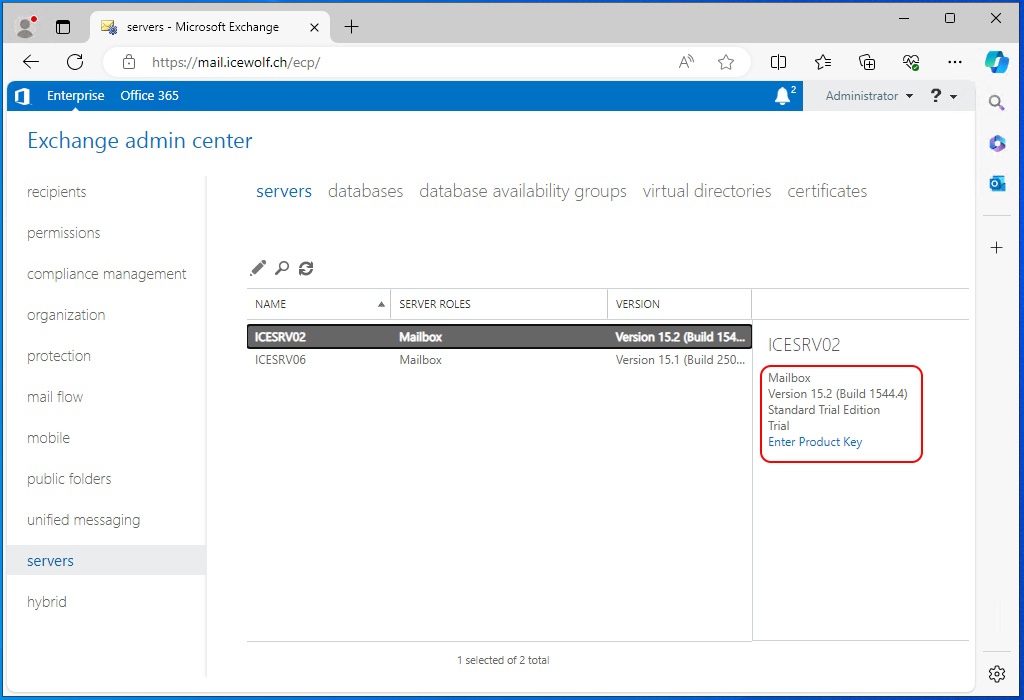
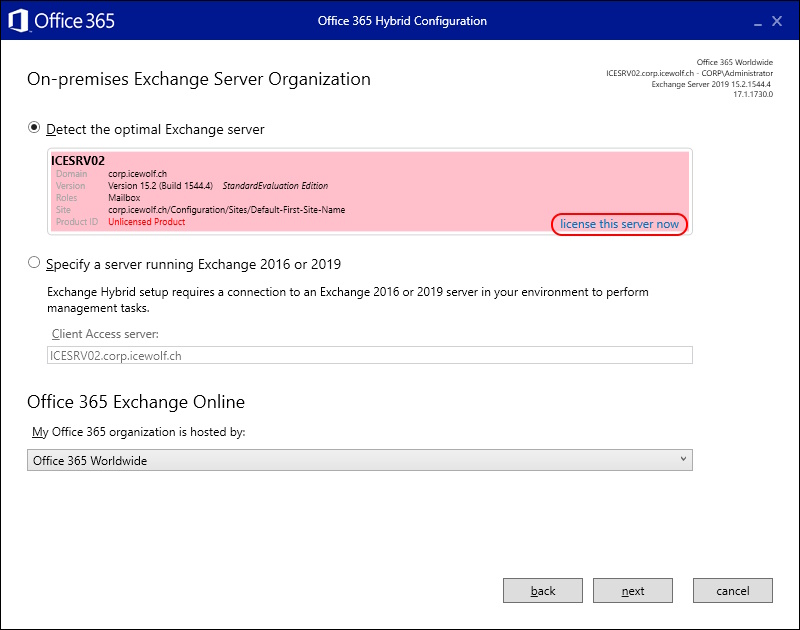
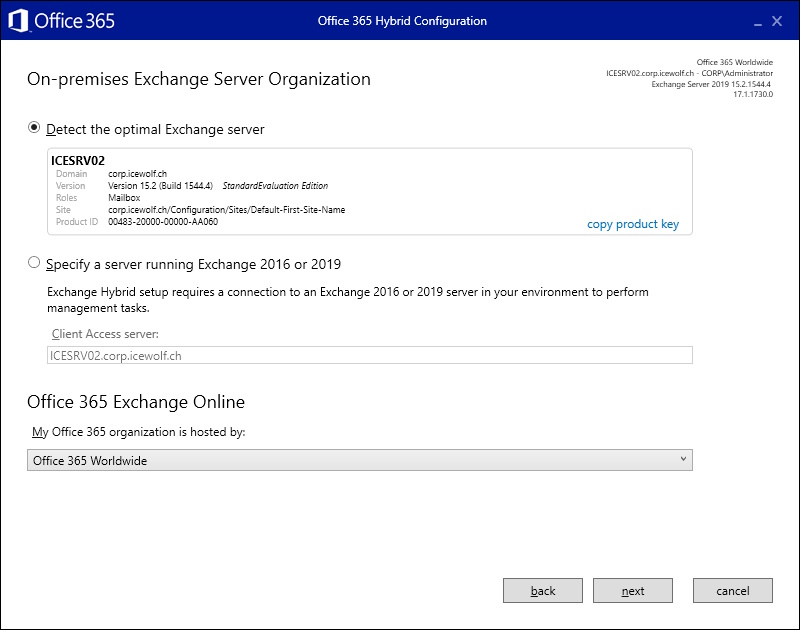
Select “license this server now”
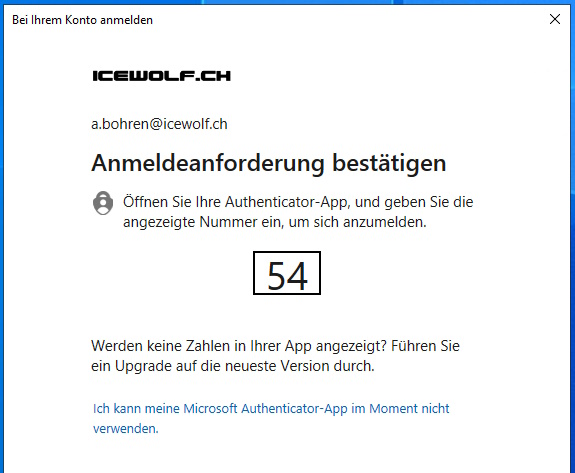
Sign in with your “Exchange Administrator” Role
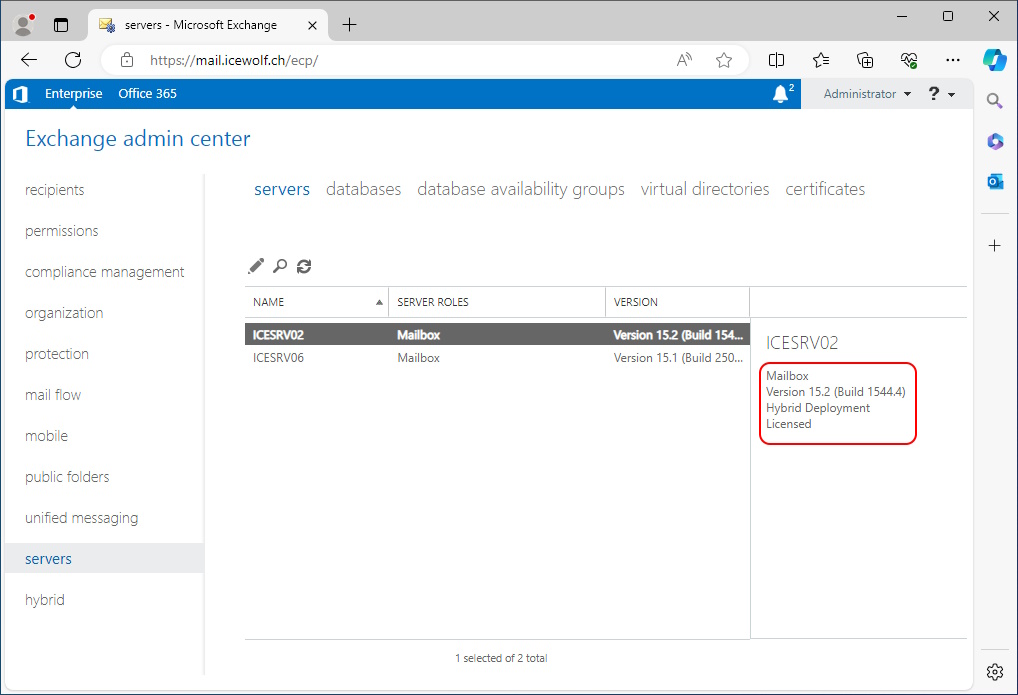
The Server has now an assiged License and you can even copy the License Key
The Exchange Server is now licensed
There might be other Takss to integrate it with your Environement:
- Backup Solution
- Monitoring Solution
- Antivirus Solution
- CMDB
Regards
Andres Bohren