Swiss Domain Security Report Q3 2025

Hi All,
I’ve published a new Swiss Domain Security Report Q3 2025 to rise awareness about the available Security technologies around Domains and Mailsecurity. It shows the adoption of diffrent technologies for the whole .ch TLD (Top Level Domain).
Hope you enjoy it and learn something. Let’s improve the Security in Switzerland!
Note: I am a private person and this is just a hobby project. But i believe this Report can be useful as an Overview of the Mail- and Domain Security in Switzerland.
Older Reports
Changes
The .ch and .li Domain data can be optained with a DNS Zone Transfer.
After that, you have to clean the Zone Data. I’ve written a PowerShell Script to do that.
###############################################################################
# Fix Tab in .ch Zone File
# 30.08.2022 Andres Bohren / https://blog.icewolf.ch
# 07.11.2024 Andres Bohren Export Unique Domains
###############################################################################
$INfile = "D:\CHDomain2025\ch.txt"
$OUTfile = "D:\CHDomain2025\ch_psedit.txt"
$UniqueDomains = "D:\CHDomain2025\ch_uniquedomains.txt"
$reader = new-object system.IO.StreamReader($INfile)
$writer = new-object system.IO.StreamWriter($OUTfile, 0)
$writer2 = new-object system.IO.StreamWriter($UniqueDomains, 0)
$Start = Get-Date
$Int = 0
#Header for Unique Domain
$writer2.WriteLine("Domain")
while ($line = $reader.ReadLine())
{
# do your thing
$Int = $Int + 1
$Line = $Line.Replace("`t`t`t","`t")
$Line = $Line.Replace("`t`t","`t")
$Line = $Line.Replace(".ch. 3600",".ch.`t3600")
$Line = $Line.Replace(".ch. 3600",".ch.`t3600")
$Line = $Line.Replace("3600 IN RRSIG","3600`tIN`tRRSIG")
$Line = $Line.Replace("3600 IN DS","3600`tIN`tDS")
$Line = $Line.Replace("3600 IN NS","3600`tIN`tNS")
$Line = $Line.Replace("3600 IN","3600`tIN")
$Line = $Line.Replace("IN`tDS ","IN`tDS`t")
$Line = $Line.Replace("IN`tNS ","IN`tNS`t")
$Line = $Line.Replace("IN RRSIG","IN`tRRSIG")
$Line = $Line.Replace("IN DS","IN`tDS")
$Line = $Line.Replace("IN NS","IN`tNS")
$Line = $Line.Replace("IN`tDS ","IN`tDS`t")
$Line = $Line.Replace(".ch. 900 IN NSEC3",".ch.`t900`tIN`tNSEC3")
$Line = $Line.Replace(".ch. 900 IN RRSIG",".ch.`t900`tIN`tRRSIG")
$Line = $Line.Replace("IN`tNSEC3 ","IN`tNSEC3`t")
$Line = $Line.Replace("IN`tRRSIG ","IN`tRRSIG`t")
$Line = $Line.Replace(".ch. 900 IN",".ch.`t900`tIN")
$Line = $Line.Replace("IN`tRRSIG DS","IN`tRRSIG`tDS")
$Writer.WriteLine("$Line")
$Domain = $Line.Split("`t")[0]
$Domain = $Domain.Substring(0,$Domain.Length -1)
If ($Domain -ne $CompareDomain)
{
$CompareDomain = $Domain
$Writer2.WriteLine("$Domain")
}
If ($Int%10000 -eq 0)
{
Write-Host "Domain: $Domain [$int]"
}
}
$End = Get-Date
$Timespan = New-TimeSpan -Start $Start -End $End
$Timespan
Write-Host "Lines processed: $INT" -ForegroundColor Green
$reader.close()
$writer.Close()
$writer2.Close()
I wanted to move the Data Gathering process to the Azure Cloud.
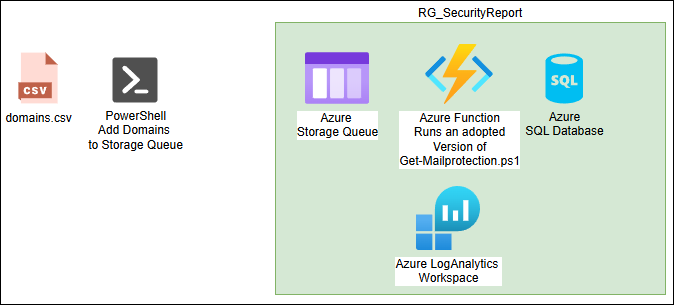
- Figured out how to use Azure Function to run the Query’s from my PowerShell Module and store the Result in an Azure SQL Database. And using the Storage Queue as a Trigger to invoke the Azure Function.
- So i’ve learned how to Use Azure Storage Queue with PowerShell
- Written a PowerShell Script to write the Domains into the Storage Queue
These are the Azure Resources used for the Report
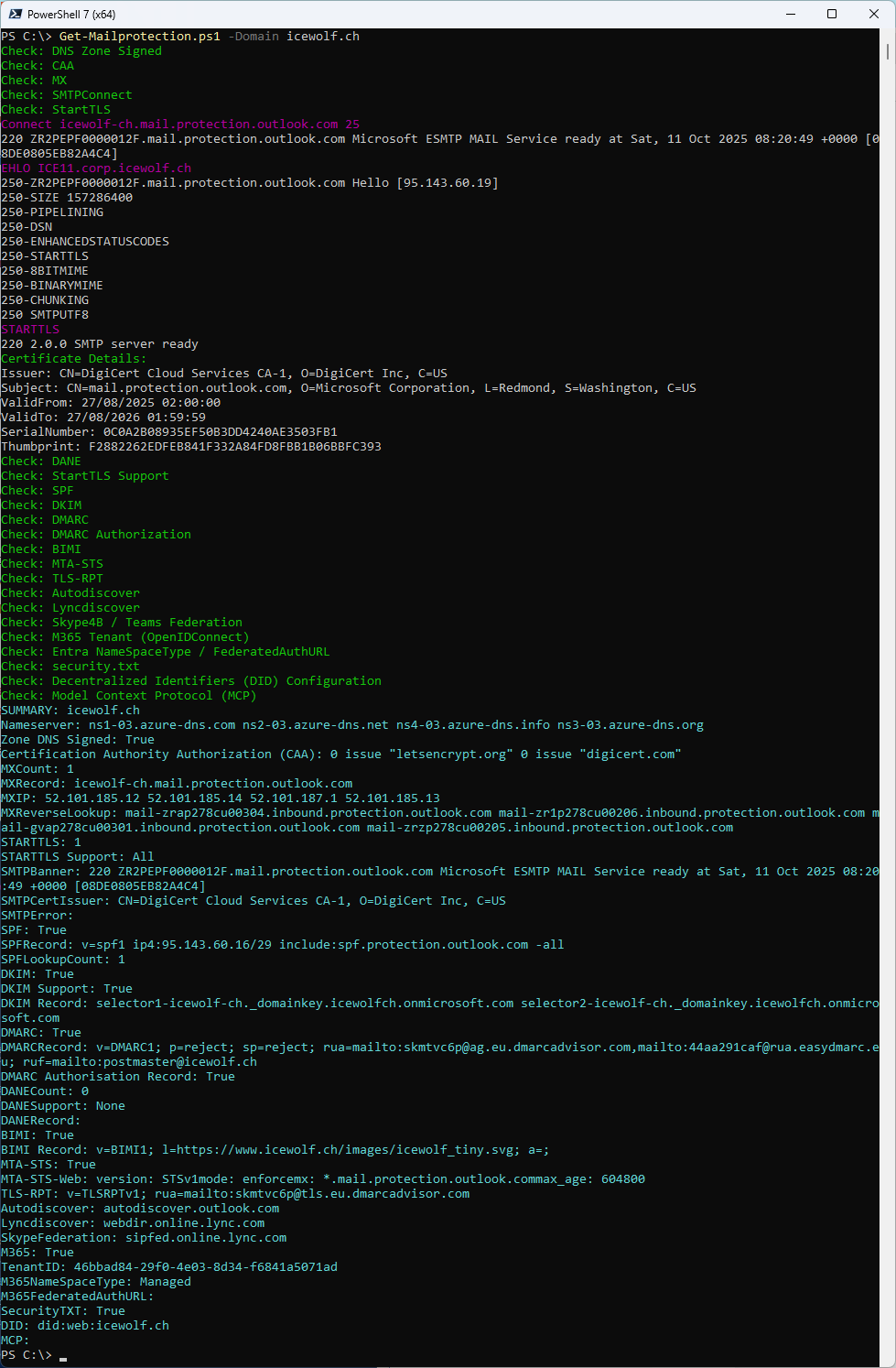
I’ve written a PowerShell Script “Get-Mailprotection” and published it on GitHub and on the PowerShell Gallery.
The Script will extracts Information for a Domain like:
- DNS Zone Signed (DNSSEC)
- CAA (Certification Authority Authorization)
- MX (MailExchanger)
- STARTTLS
- SMTPBanner
- SMTP Certificate Issuer
- SMTP Error
- SPF (Sender Policy Framework)
- DKIM (DomainKeys Identified Mail) > Only for M365 Tenants
- DMARC (Domain-based Message Authentication, Reporting and Conformance)
- DANE (DNS-based Authentication of Named Entities)
- BIMI (Brand Indicators for Message Identification)
- MTA-STS (SMTP MTA Strict Transport Security)
- MTA-STS Web (https://mta-sts.domain.tld/.well-known/mta-sts.txt)
- TLS-RPT (TLS Reporting)
- Autodiscover
- Lyncdiscover
- Skype4B / Teams Federation
- M365 Tenant
- SecurityTXT
- (NEW) M365NameSpaceType (Federated / Managed)
- (NEW) M365FederatedAuthURL (ADFS or 3rd Party Auth URI)
- (NEW Experimental) Decentralized Identifiers (DID)
- (NEW Experimental) Model Context Protocol (MCP)
I had to rewrite the DNS Querys from Resolve-DnsName to DNS over HTTPs (DoH), because Resolve-DNS does not work on Azure Function.
Challenges
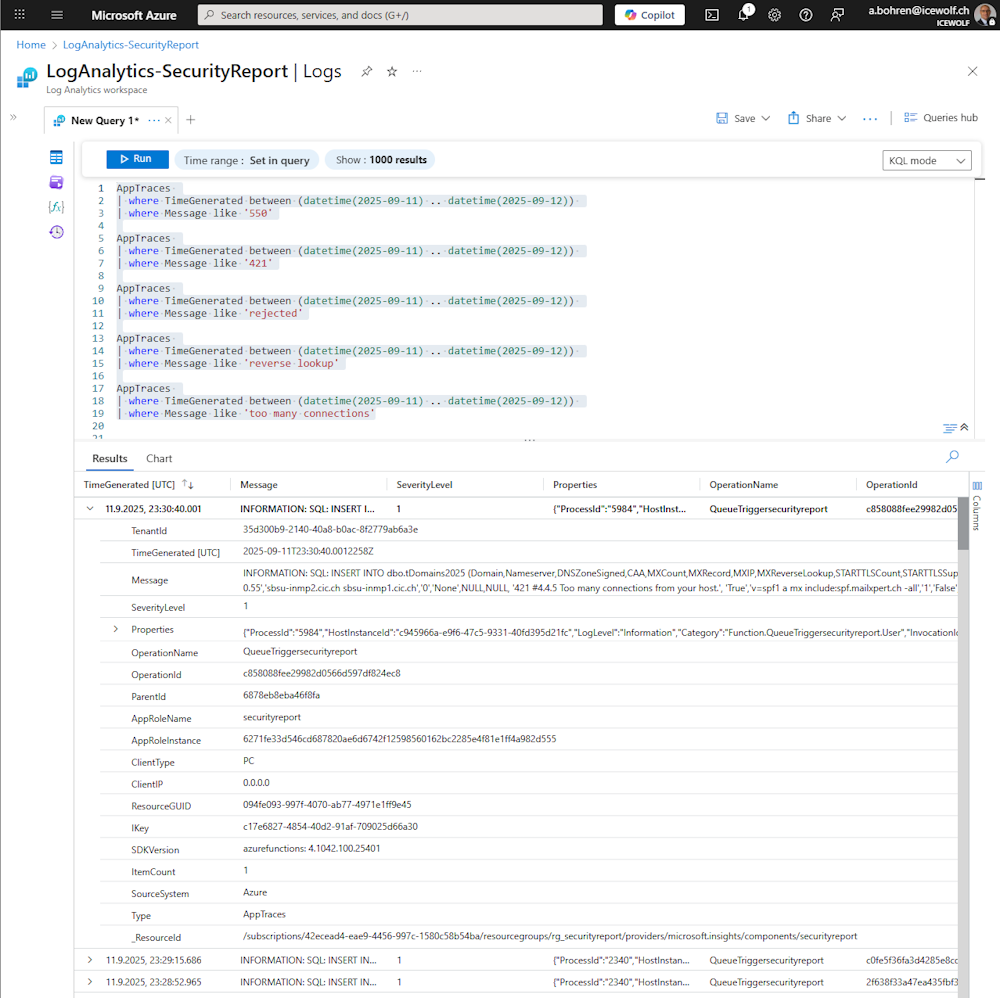
I needed to learn how to Trace an Azure Function
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like '550'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like '421'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'rejected'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'reverse lookup'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'too many connections'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'Connection rate limit exceeded'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'Service not available'
AppTraces
| where TimeGenerated between (datetime(2025-09-11) .. datetime(2025-09-12))
| where Message like 'Too many open connections'
Soon learned that some of the Mailservers rejected the SMTP Connections with various reasons. That lead to adding SMTPError so i would be able to Process these Entrys later from another Machine.
- 550 98.64.192.172 is blacklisted - https://lookup.abusix.com/search?q=98.64.192.172
- 550 This email from IP has been rejected
- 521 Blocked because reverse lookup failed
- 554 Service not available
- 421 Failure to determine Reverse DNS for your IP
- 421 4.4.5 too many connections
- 421 4.3.2 Connection rate limit exceeded
- 421 4.3.2 Too many open connections
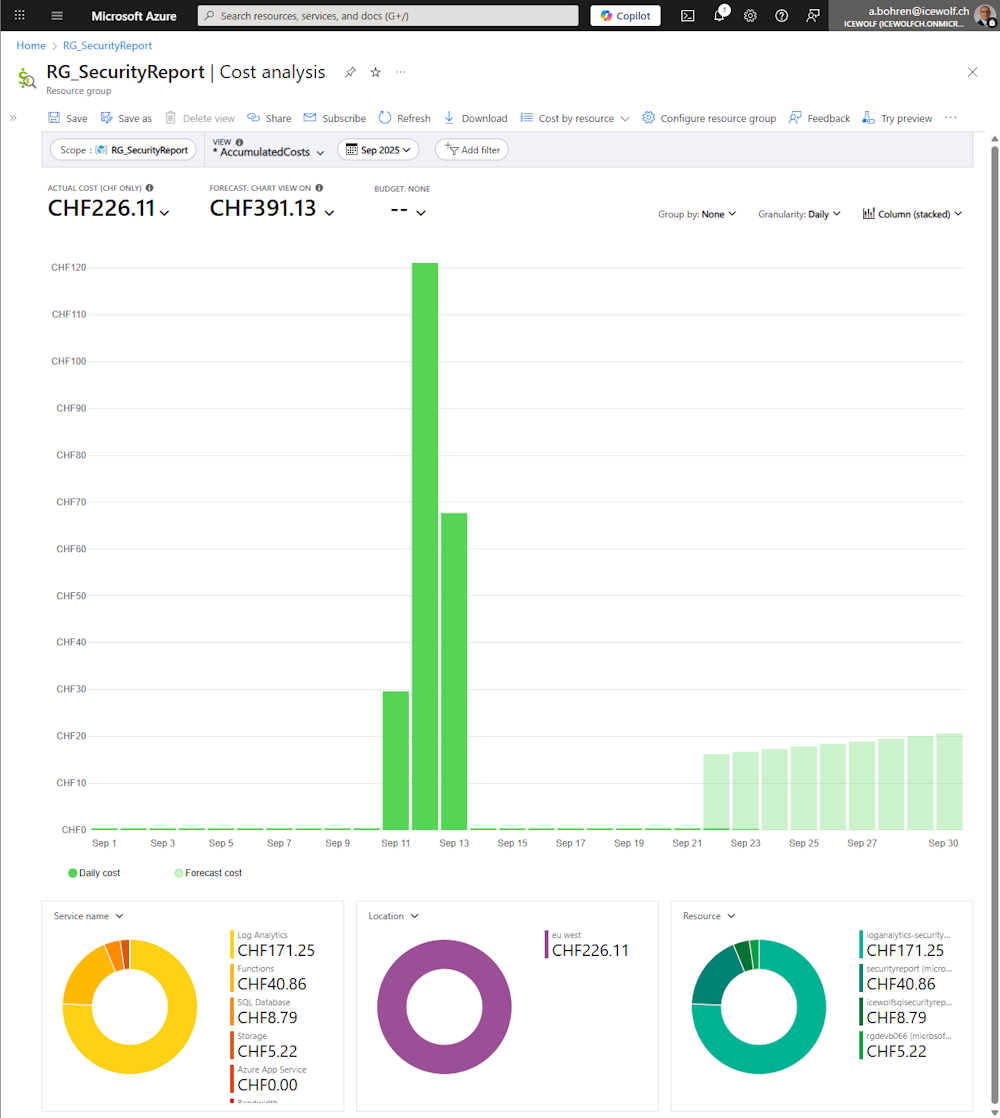
Costs
I was unsure, how much cost this would generate on Azure. As you can see, it ended up at a cost of 226 CHF.
The actual Azure Function, Azure Storage Queue and the SQL Database was only about 55 CHF.
The biggest cost block was Log Analytics, even i did already cut down the messages to a minimum. Next Time i will do a run of about 100'000 Domain to make sure everything works fine and then Disable Application Insights with the Code below.
#Disable Application Insights
Get-AzFunctionAppSetting -Name "SecurityReport" -ResourceGroupName "RG_SecurityReport"
Update-AzFunctionAppSetting -Name "SecurityReport" -ResourceGroupName "RG_SecurityReport" -AppSetting @{"APPLICATIONINSIGHTS_CONNECTION_STRING" = $null}
If you like this Report and want to support it, feel free to BuyMeACoffee
Outcome
I was impressed by the Outcome. The almost 2.7 Million .ch Domain Names where processed in like three days. Only having to reprocess about 400'000 Domains because the SMTP Errors - wich took me about 10 Days running on my VM with PowerShell 7 and the -Parallel Parameter
$ArrayDomains | ForEach-Object -ThrottleLimit 10 -Parallel {
#Code goes here
}
Timeline
- 10.09.2025: Getting .ch Zone Data
- 11-13.09.2025: Processing the Domains with Azure Fuction
- 24.09-05.10.2025 Reprocessing the Domains with SMTPErrors on my OnPrem VM
- 06-12.10.2025: Analysis and Report
Overview
My main Focus on this Project was related to Domain and Mailsecurity - but there are other aspects i did NOT consider like:
- HTTP/HTTPS of Website
- HTTPS TLS Version used
- HTTP Strict Transport Security Cheat Sheet (HSTS)
- HTTP Security Header
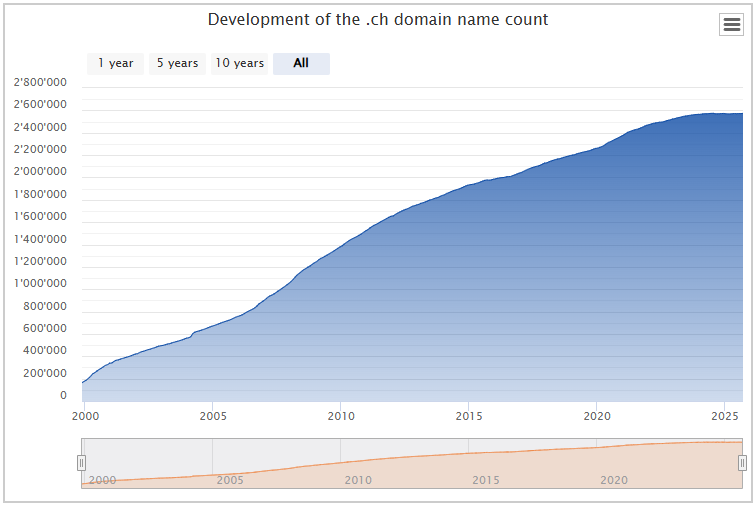
.ch Domains
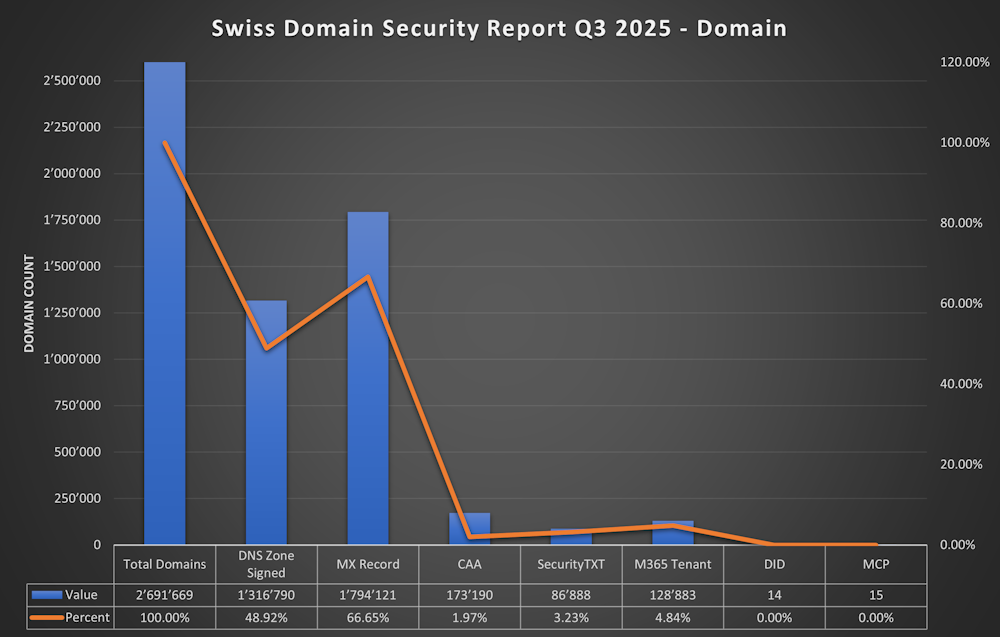
- 2'691'669 .ch Domains (September 2025) https://www.nic.ch/statistics/domains/
- 175'226 Domains more than September 2023
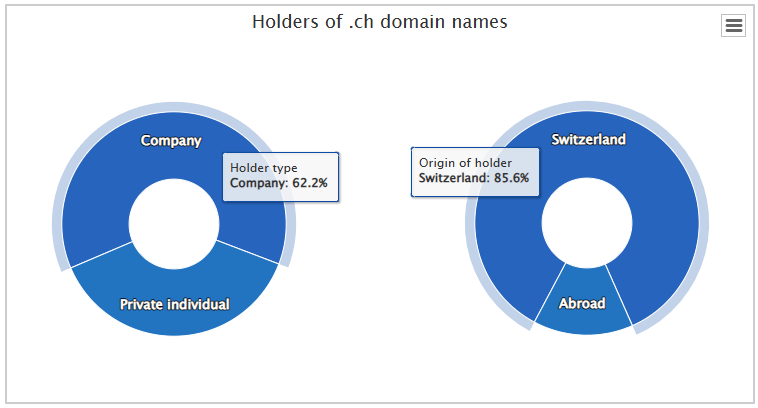
.ch Domain Holders (Company / private Individual)
- 62.2% (about 1'674'218) of the Domains are owned by a Company
- 37.8% (about 1'017'450) of the Domains are owned by a private Individual
- 85.6% (about 2'304'068) of the Domain Holders are located in Switzerland
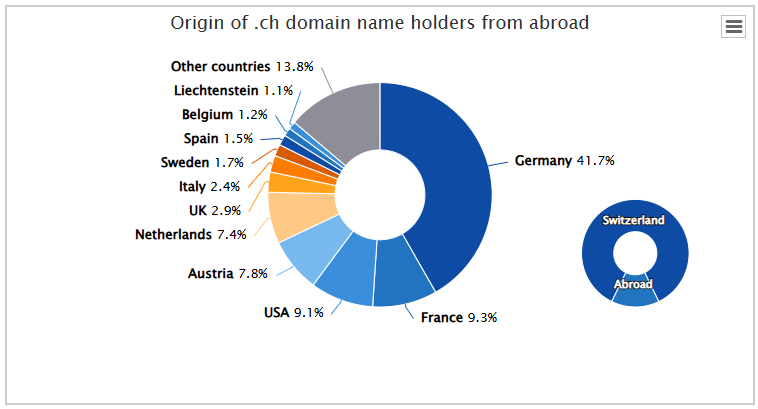
Top .ch Domain Holders outside Switzerland Countries of Origin
- 41.7% Germany
- 9.3% France
- 9.1% USA
- 7.8% Austria
Hardenize
An overview about Security the top 1'000 .ch Domains is maintained by Switch
These are probably big companies with professional IT and Security Teams. So these Results do not represent the whole Market.
Switch DNS Resilience Dashboard
Check out also this Dashboard from Switch
Domain Security Overview
DNSSEC
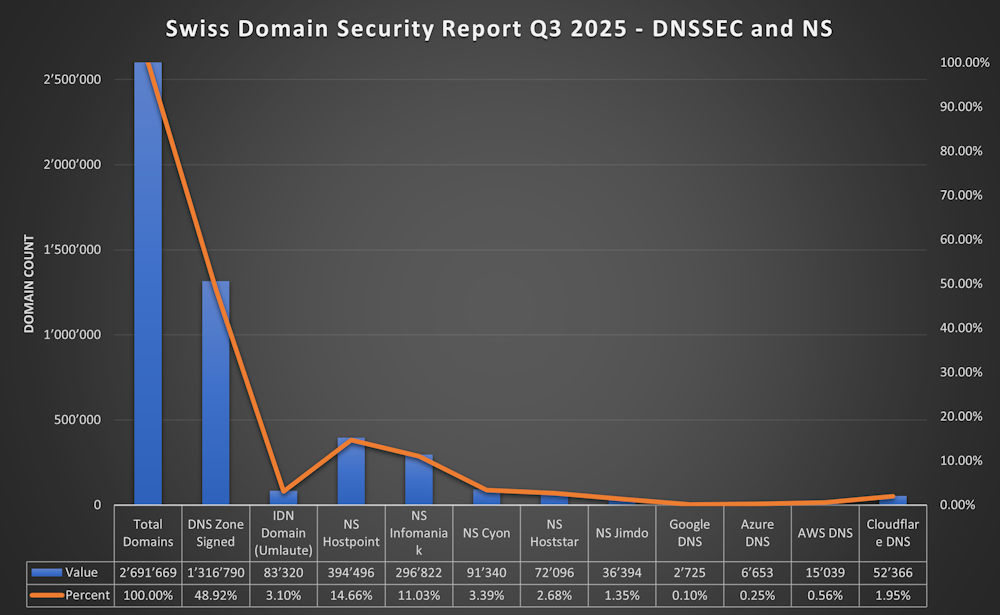
- 48.92% (1'316'790) of the .ch DNS Zones Signed (DNSSEC) https://www.nic.ch/statistics/dnssec/
- 100'449 DNSSEC Domains more than September 2023
MX Record
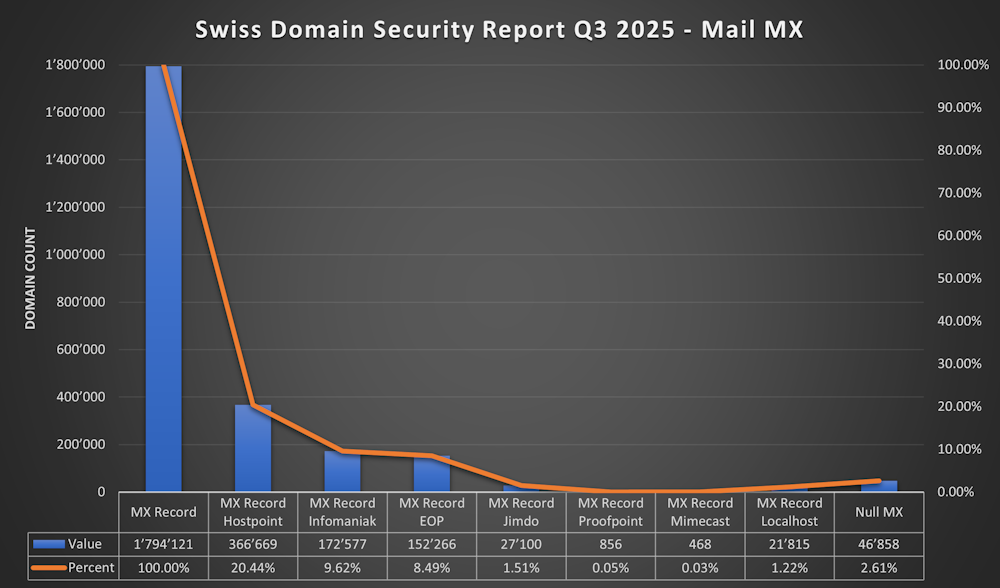
- 66.65% (1'794'121) of all .ch Domains have a MX Record
- 13'519 more than September 2023 (but then it was about 70% of all Domains)
CAA (Certification Authority Authorization)
- CAA exists since 2019 rfc8659
- 1.97% (173'190) of all .ch Domains support CAA
- 138'891 Domains more than September 2023
SecurityTXT
I have checked for Security.txt on https://domain.tld/security.txt (old) and https://domain.tld/.well-known/security.txt (new)
- Exists since April 2022 rfc9116 More Info: https://securitytxt.org/
- 3.23% (86'888) of all .ch Domains have a SecurityTXT
- 32'194 less than in September 2023
M365 Tenant
- 4.84% (128'883) of all .ch Domains have a M365 Tenant
- 16'065 less than in September 2023
Decentralized Identifiers (DID)
- First time i have checked for DID
- Only 14 Domains have a DID published
Model Context Protocol (MCP)
- First time i have checked for MCP
- Looking for
- Only 15 Domains have a MCP published
DNSSEC and Nameserver
DNSSEC
- 48.92% (1'316'790) of the DNS Zone Signed (DNSSEC) https://www.nic.ch/statistics/dnssec/
- 100'449 DNSSEC Domains more than September 2023
Internationalized domain name (IDN)
- 3.10% (83'320) are Internationalized domain name (IDN) using Punycode
Nameserver
- 14.66% (394'496) of the NS Records point to Hostpoint
- 11.03% (296'822) of the NS Records point to Infomaniak
- 3.93% (91'340) of the NS Records point to Cyon
- 2.68% (72'096) of the NS Records point to Hoststar
- 1.35% (36'394) of the NS Records point to Jimdo
- 0.10% (2’725) of the NS Records point to Google DNS
- 0.25% (6'653) of the NS Records point to Azure DNS
- 0.56% (15'039) of the NS Records point to AWS DNS
- 1.95% (52'366) of the NS Records point to Cloudflare DNS
Mailsecurity Overview
MX (Mail Exchange)
- MX Record exists since 1987 defined here rfc1035
- 66.65% (1'794'121) of all .ch Domains have a MX Record
- 20.44% (366'669) of .ch Domains with MX point to Hostpoint
- 9.62% (172'577) of .ch Domains with MX point to Infomaniak
- 8.49% (152'266) of .ch Domains with MX point to Exchange Online
- 1.51% (27'100) of .ch Domains with MX point to Jimdo
- 0.05% (856) of .ch Domains with MX point to Proofpoint
- 0.03% (468) of .ch Domains with MX point to Mimecast
- 2.61% (46'858) of .ch Domains use “Null MX” rfc7505 (sadly not supportet by Exchange Server or Exchange Online)
- 1.22% (21'815) of .ch Domains with MX point localhost 😂 - (Mostly parked Domains)
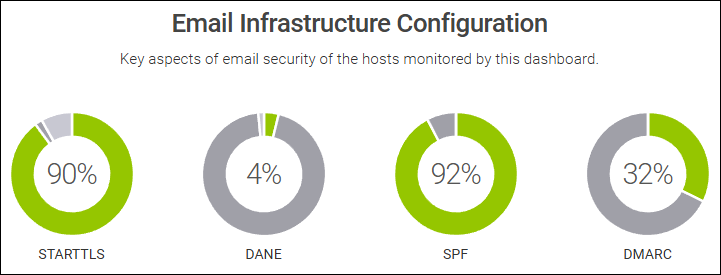
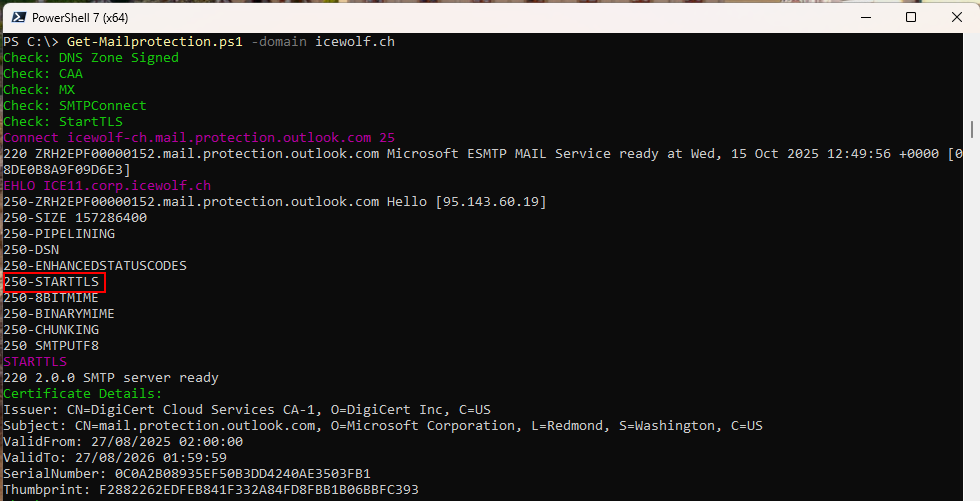
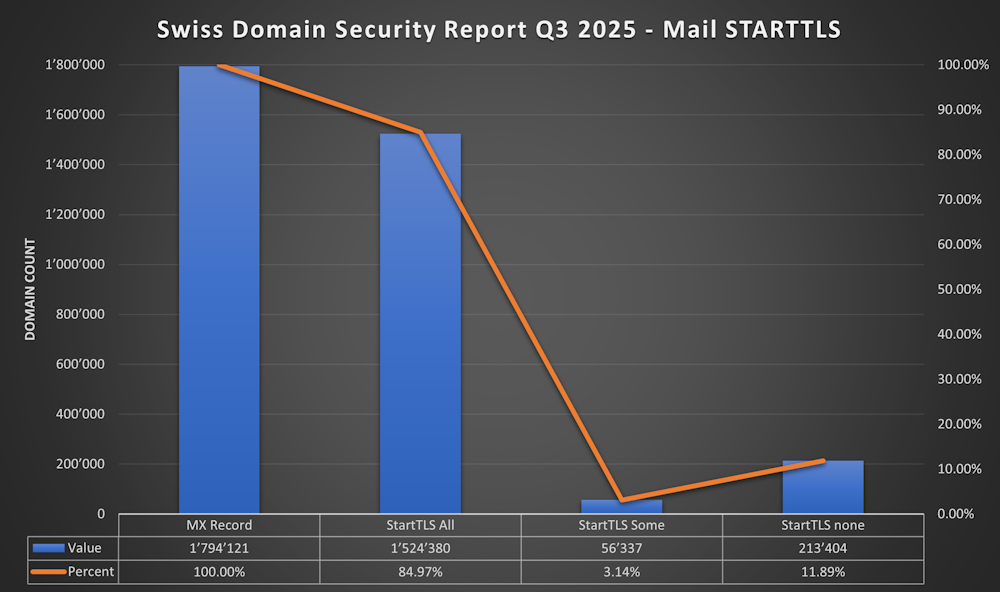
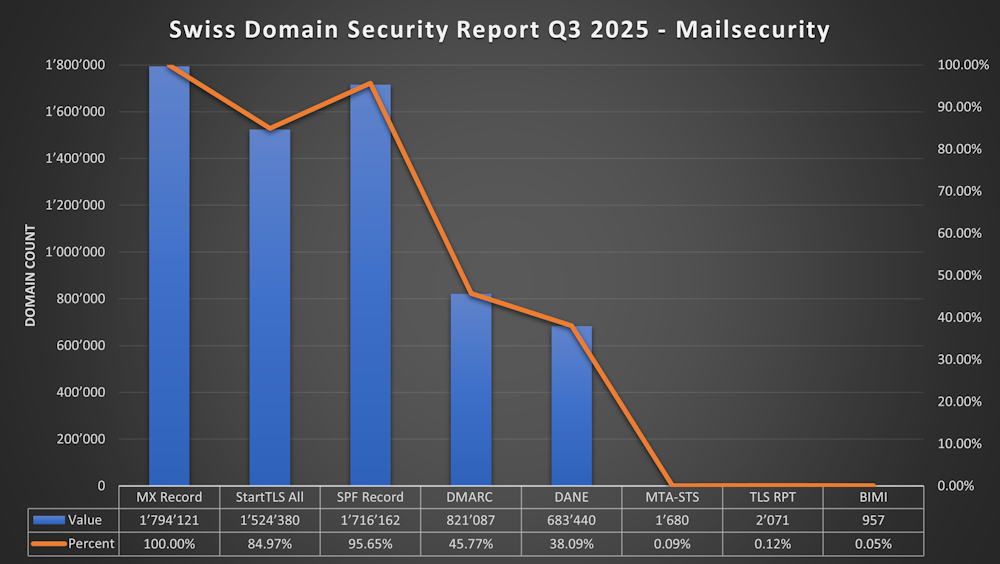
STARTTLS
I’ve connected to every MX Record on Port 25 and checked for a “STARTTLS” Response to a EHLO command
- If they returned “STARTTLS” it was counted.
- If a Domain has multiple MX, i’ve checked every Mailserver for “STARTTLS”. If all MX Records supported STARTTLS then this will be counted as “STARTTLS All”.
- 84.97% (1'524'380) of all .ch Domains with MX - all Mailservers supported STARTTLS
- 3.14% (56’337) of all .ch Domains with MX - some Mailservers supported STARTTLS
- 11.89% (213’404) of all .ch Domains with MX - none Mailservers supported STARTTLS
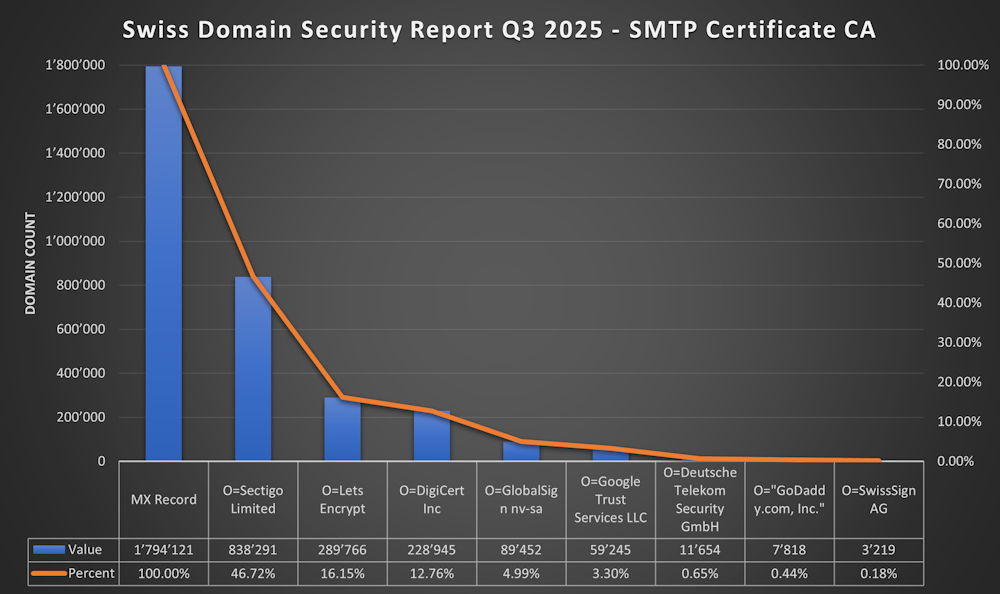
SMTP Certificate Issuer
When STARTTLS was available i’ve checked the Certificate Details and stored the Certificate Issuer (Certificate Authority that issued the Certificate)
Results of SMTP Certificate Issuer (CA)
The Report is based on the O=(Organization) Attribute of the CA Certificate
- 46.72% (838'291) O=Sectigo Limited
- 16.15% (289'766) O=Lets Encrypt
- 12.76% (228'945) O=DigiCert Inc
- 4.99% (89'452) O=GlobalSign nv-sa
- 3.30% (59'245) O=Google Trust Services LLC
- 0.65% (11'645) O=Deutsche Telekom Security GmbH
- 0.44% (16'477) O=“GoDaddy.com, Inc.”
- 0.18% (3'219) O=SwissSign AG
It’s quite Impressive that Let’s Encrypt CA is used for more than 16% on SMTP.
I’ve written an Article how to Automate Exchange Certificate renewal with Let’s Encrypt
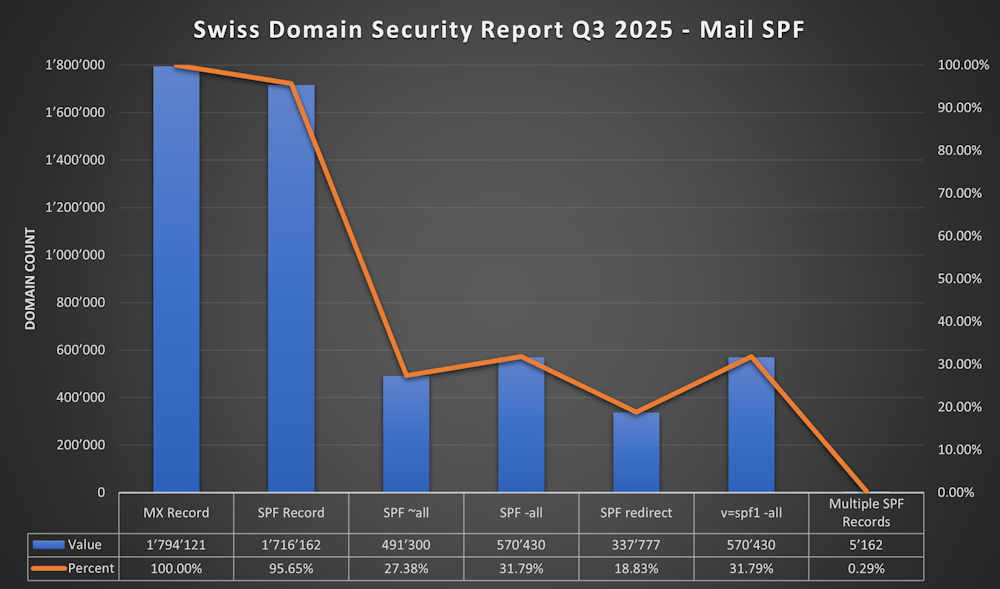
SPF (Sender Policy Framework)
- SPF exists since 2003 with Updates 2006 and 2014 rfc7208
- 95.65% (1'716'162) of .ch Domains with MX have a SPF Record
- In September 2023 it was only about 78%
- 27.38% (491'300) of .ch Domains with MX have “SPF -all”
- 31.79.82% (570'430) of .ch Domains with MX have “SPF ~all”
- 18.38% (377'777) of .ch Domains with MX have a SPF Redirect
- 31.79% (570'430) of .ch Domains with MX have (v=spf1 -all)
- 0.29% (5'162) of .ch Domains with MX have Multiple SPF Records
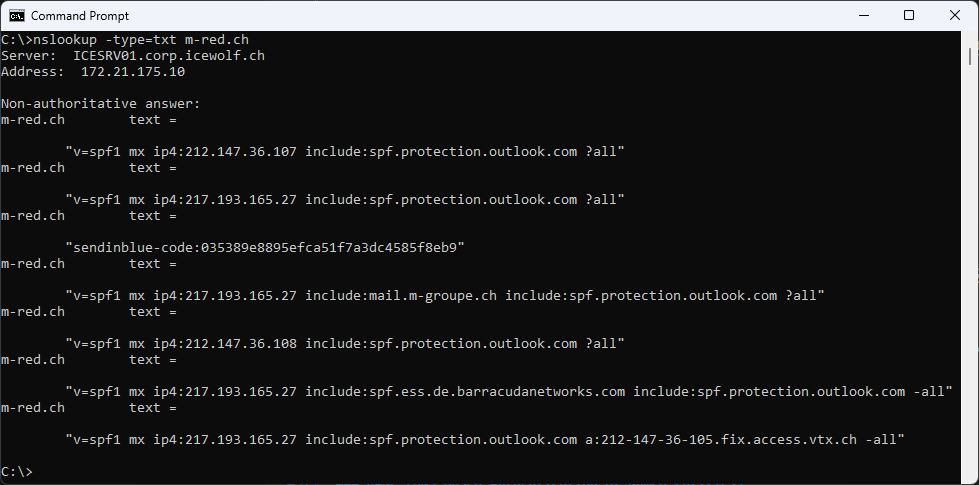
Bad Example: nslookup -type=txt m-red.ch (does not work like that)
DKIM (DomainKeys Identified Mail)
Note: due the fact that the Selector can be anything it’s impossible to determine DKIM Records. But can look at the DMARC Numbers - because DMARC is based on SPF and DKIM.
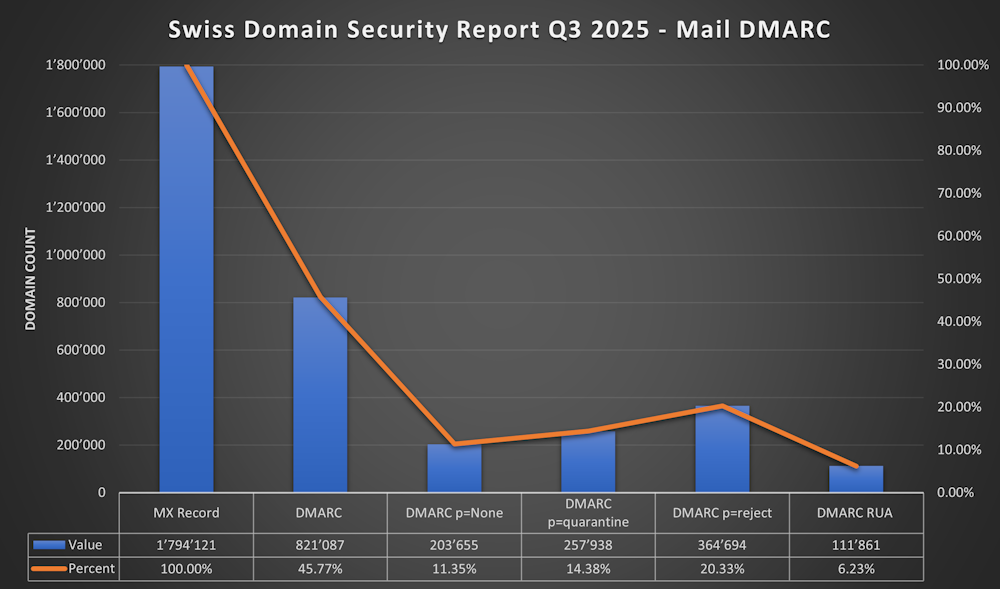
DMARC (Domain-based Message Authentication, Reporting and Conformance)
- DMARC Exists since 2015 defined in rfc7489
- 45.77% (821'087) of Domains with MX have a DMARC Record
- In September 2023 it was only 11.26%
- 11.35% (203'655) p=none
- 14.38% (257'938) p=quarantine
- 20.33% (364'694) p=reject
- 6.23% (111'861) have a rua defined
It shure helped that Exchange Online sends now DMARC Aggregate Reports
As only about 6% have a rua i guess the Monitoring about DMARC is not great. I recommend one of the below:
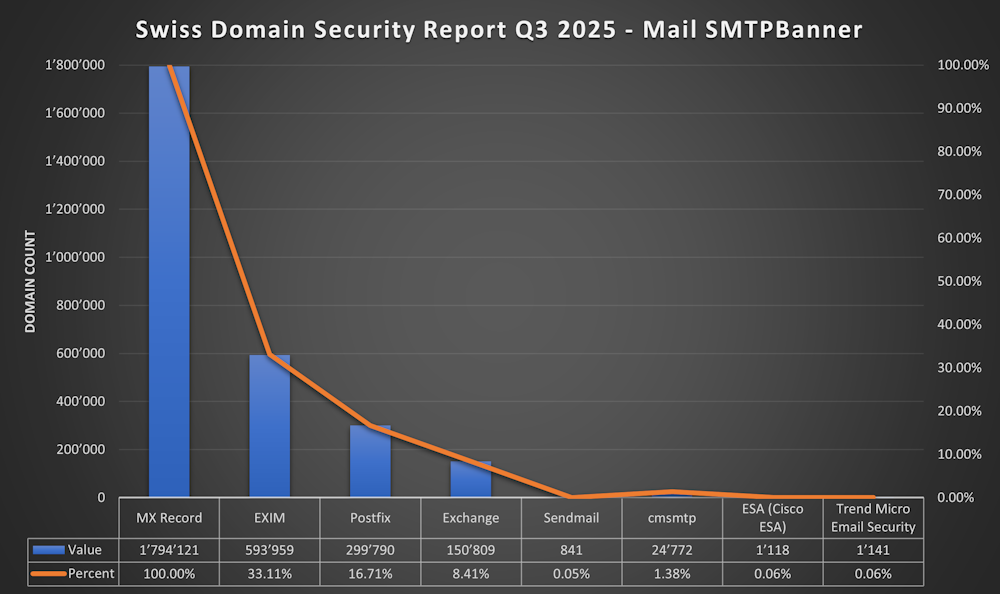
SMTP Banner
It’s clear that not all Mailservers will show the Software or even Version in the SMTP Banner. But a lot of Mailserver still do that and it’s interesting to see witch are the most used Mailservers.
SMTPBanner Results
- 33.11% (593’959) EXIM
- 16.71% (299’790) Postfix
- 8.41% (150’809) Exchange/Exchange Online
- 0.05% (841) Sendmail
- 1.38% (24'772) cmsmtp
- 0.06% (1'118) ESA (Cisco Email Security Appliance aka Ironport)
- 0.06% (1'141) Trend Micro Email Security
It’s impressive to see, that almost half of the Mailservers run with EXIM or Postfix.
Mailsecurity Overall
STARTTLS Overviev
Beeing able to Transmit E-Mails over a secure TLS Connection is crucial when it comes to Confidentiality. It’s great to see, that this Number is at about 85%.
SPF / DKIM / DMARC
When it comes to protect your Domain from Spoofing SPF, DKIM and DMARC are the tools at hand. It’s great to see that SPF is at about 95% and DMARC has increased from 11% to 45% in two years.
It’s likely that the new Requirements for DMARC from Google, Yahoo and Microsoft had a massive influence.
- New Gmail protections for a safer, less spammy inbox
- More Secure, Less Spam: Enforcing Email Standards for a Better Experience
- Strengthening Email Ecosystem: Outlook’s New Requirements for High‐Volume Senders
DANE (DNS-based Authentication of Named Entities)
- Exists since 2015 rfc7673
- Requires DNSSEC
- I’ve explained how DANE works in one of my Blog Articles
- 38.09% (683’440) of the Domains with MX have a DANE Record
- 35.09% (629’593) use “3 1 1” (Hash of Servercertificate without Certificate Chain / Hash of Public Key and algorithm / SHA-256 hash)
- 148'065 more than September 2023
MTA-STS (SMTP MTA Strict Transport Security)
- Exists since 2018 rfc8461
- 0.09% (1'680) of the Domains with MX support MTA-STS
- 840 more than September 2023
TLSRPT (SMTP TLS Reporting)
- Exists since 2018 rfc8461
- 0.12% (2071) of the Domains with MX support TLS-RPT
- 1441 more than September 2023
BIMI (Brand Indicators for Message Identification)
-
Exists since 2021 but is still under development IETF BIMI Draft
-
0.05% (957) of all .ch Domains with MX Support BIMI / only 99 with a Certificate
-
659 more than September 2023
-
Sadly not supported by Microsoft
More Resources:
You can try to Vote for one of these two Suggestions in the Microsoft Feedback Portal
M365 Tenant Details
I work a lot with Microsoft M365 and Exchange Online so i did an extra Statistic here
- 6.43% (173'190) of all .ch Domains have a M365 Tenant
- 4.79% (128’883) if you count only unique TenantID’s
- 48.13% (83’349) of Domains with an M365 Point the MX to EOP (*protection.outlook.com or *.mx.microsoft)
- 22.45% (38’883) of Domains with an M365 Tenant have DKIM enabled (way to low)
Summary Mailsecurity
Let’s wrap it up
- SecurityTXT is at 3.23% and has been decreased. I would like to see an Increase here
- It is amazing that DNSSEC is about 49%. Maybe time to move your DNS to Azure since Azure DNS finally supports DNSSEC (Preview)
- STARTTLS is between 85% and 89%. That’s impressive - but there are still about 11% that does not support STARTTLS - the goal should be 100%
- It’s impressive to see that over 16% of the Mailservers use “Let’s Encrypt” Certificates. I’ve written an Article how to Automate Exchange Certificate renewal with Let’s Encrypt
- SPF has improved from 78% to 95%. Sadly only 31% have “-all” what should be standard (in my opinion)
- And we still have over 5'000 Domains that have multiple SPF Records 🫣
- DKIM is hard to detect via DNS. Should be Standard on every M365 Tenant - as Microsoft makes this very easy Enable DKIM in Exchange Online
- DMARC has improved from 11% to 45%. Thats very impressive. Only 11% are still on with “p=none” - great to see that.
- RUA is still very low - i guess the Monitoring of DMARC Reports can be massively improved
- DANE has improved from 30% to 38% - surprising high due to the fact it’s quite complex to set up and it has a DNSSEC Requirement. It’s a high Number due to to Fact that only 49% of the Domains are protected with DNSSEC. Good thing that Exchange Online supports DANE
- MTA-STS/TLS-RPT is surprising low at 0.09 / 0.12% as it’s less complex than DANE. Did you know there is a PowerShell Module that helps you deploy MTA-STS on a Azure Function PS.MTA-STS
- BIMI still very low at 0.05% and VMC Certificates (0.01%) have high costs and require registered Trademarks and Logos. It will stay like that until Microsoft is supporting BIMI
- CAA Support is still very low at almost 2%. I would like to see that more Companys adopt CAA DNS Certification Authority Authorization
Call to Action
Let’s make Email better and implement those well known Techniques to improve the Domain and Mailsecurity in Switzerland.
That means you, as an Mailserver Administrator, you as a Provider, you as a CISO, you as a Business Representive… Take action and help to improve the Security in Switzerland…
I would like to hear about your actions on X, LinkedIn or BlueSky with the Hashtag #SwissDomainSecurityReport 😍
Regards
Andres Bohren