Security Update for Microsoft Office Web Apps Server 2013 (KB3118360)
Hallo zusammen,
Letzte Woche hat Microsoft wieder mal ein Update für Office Web Apps Server 2013 veröffentlicht.
Hallo zusammen,
Letzte Woche hat Microsoft wieder mal ein Update für Office Web Apps Server 2013 veröffentlicht.
Hallo zusammen,
Vor ein paar Tagen habe ich Secure Score Preview auf Office 365 entdeckt.
Hallo zusammen,
Kürzlich habe ich die Konsole von Symantec Mail Security für Microsoft Exchange Server kontrolliert und gesehen, dass eine neue Version verfügbar ist.
Hallo zusammen,
Kürzlich habe ich mal wieder die Meldungen in Backup Exec 15 angeschaut und festgestellt, dass ein Update verfügbar ist.
Hallo zusammen,
In den folgenden Screenshots zeige ich euch wie man Multi-Faktor Authentification (MFA) in Office 365 aktiviert und wie es für den Benutzer aussieht.
Hallo zusammen,
Am 20. September 2016 wurde das Cumulative Update 14 für Exchange 2013 veröffentlicht.
Hallo zusammen,
Windows Server 2016 RTM wurde am 26. September weltweit gelaunched.
Hallo zusammen,
Gestern habe ich ein Mail von Microsoft Learning erhalten. Mir wurde zu der neuen Zertifizierung "Microsoft Certified Solution Expert: Productivity" gratuliert.
Hallo zusammen,
Im Juni 2009 hat das Energie Wasser Bern (EWB) beschlossen im Gemeindegebiet Bern ein flächendeckendes Glasfasernetz zu realisieren.
Hallo zusammen,
Ich habe mich mal mit dem Office 2016 Deployment Tool auseinander gesetzt. Zuerst muss man aber mal die verschiedenen Versionen und Kanäle verstehen.
Hallo zusammen,
Vor ein paar Tagen wurde im untenstehenden Blog Artikel aufgezeigt, was bei übrlappenden Accounts von AzureAD und Microsoft Account (beide mit derselben Emailadresse registriert) geplant ist und wie man das Lösen kann.
Hallo zusammen,
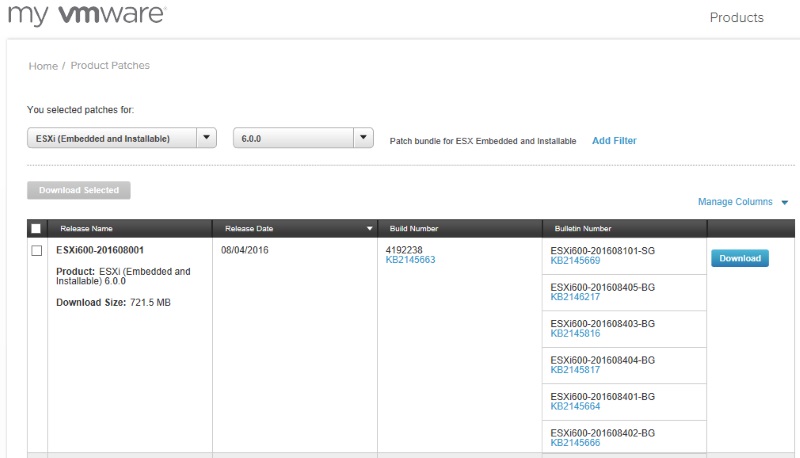
Hallo zusammen,
Auf meinem Samsung Galaxy S6 erhalte ich regelmässig Android Updates. In den folgenden Screenshots sieht man, das Security Update von August, welche ich am 29.08.2016 erhalten und installiert habe.
Hallo zusammen,
Ein neues Security Update für Office Web Apps Server 2013 ist verfügbar.
Hallo zusammen,
Seit ein paar Monaten ist SQL 2016 auf dem Markt. Dazu gibt es eine gute über sicht auf dem nachfolgenden Blog
Hallo zusammen,
Als ich den nachfolgenden Artikel gelesen habe wurde ich extrem neugierig. Das .NET Core Framework auf Linux? Nun ja, mit Windows 10 und Windows Server 2016 kommt ja auch die Bash auf Windows.
Hallo zusammen,
Diese Woche wurde für Exchange 2010 SP3 das Update Rollup 15 veröffentlicht
Hallo zusammen,
Diese Woche wurde ein Security Update für Exchange 2013 CU13 veröffentlicht
Hallo zusammen,
Kürzlich bin ich über die Liste und die Liste der Emoticons von Skype und deren Tastaturkürzel gefunden.
Hallo zusammen,
Ich habe mich mal mit Modern Authentication in Office 365 befasst. Modern Authentication benutzt im Hintergrund ADAL.